What Makes IAM “AI-Native”? A Definition, Maturity Model, and Why Being the IdP Matters

At 9:07 a.m. on a Monday, a new hire is ready to work.
They have a laptop. They have an email address. They have a calendar invite titled “Day 1 Kickoff.”
And then:
- They can’t access the code repo.
- They can’t access the ticketing system.
- They can’t access the data warehouse.
- They can’t access the customer support tool.
- Someone in Slack says, “File an access request.”
By lunch, three people have approved the request, two admins have touched four consoles, and one critical permission is still missing—because the app that actually matters isn’t connected to anything.
Offboarding is worse. You disable the user in the IdP, feel relieved, and move on. But weeks later you discover:
- a lingering app-local admin role
- an API token created “temporarily”
- an OAuth delegation that still lets a third-party app pull data
- an app-to-app connection that keeps syncing content long after the human account is gone
This is the uncomfortable truth: identity and access management (IAM) isn’t a product category; it’s the control plane of the company. And as companies become more software-defined (and now agent-enabled), IAM becomes the bottleneck—or the leverage point.
“AI-native IAM” is the attempt to turn IAM from a queue of tickets into an always-on system that understands access, reasons about risk, executes changes, and proves what happened.
This post defines AI-native IAM precisely, lays out a practical maturity model, and briefly covers an important design choice: why an AI-native IAM product can be meaningfully stronger if it’s also the IdP.
The definition: what “AI-native IAM” actually means
An IAM product is AI-native if AI is essential to its core function, not just a UI feature.
Working definition:
AI-native IAM continuously understands access reality, reasons about policy and risk, and safely executes IAM changes end-to-end—at scale—with verifiable outcomes.
There are four non-negotiables embedded in that sentence:
- Continuously understands access reality Not “what the IdP group says,” but what permissions exist in reality across apps, cloud, data, and infrastructure—including non-human access paths like tokens and delegated OAuth grants.
- Reasons about policy and risk Not “approvals as ceremony,” but decisions grounded in least privilege, role intent, separation-of-duties, sensitivity, and blast radius.
- Safely executes changes end-to-end Not “here’s a recommendation,” but actual provisioning, deprovisioning, right-sizing, exception handling, and remediation—with guardrails.
- Verifiable outcomes Not “we think we removed access,” but “we can prove what changed, why it changed, who approved it, and what the system state is now.”
What AI-native IAM is not
A lot of products will use “AI-native” loosely. The common mislabels:
- “AI in the UI”: summaries, chat search, nicer access request forms Helpful, but not AI-native. The operating model hasn’t changed.
- “LLM-driven tickets”: the LLM writes the request, humans do the work Still a queue. Still brittle. Still slow.
- “Static RBAC + AI suggestions”: role advice with no execution path If roles drift (they do), advice without enforcement is just noise.
AI-native IAM isn’t “talk to IAM.” It’s “IAM that can act responsibly.”
Why AI-native IAM is happening now
Legacy IAM broke for two reasons.
1) The surface area exploded
Modern orgs have:
- hundreds of SaaS apps
- multiple clouds
- data tools with fine-grained permissions
- API tokens, service accounts, and non-human identities
- contractors, vendors, and shared operational accounts
- delegated connections (app-to-app, SaaS-to-SaaS, agent-to-app)
Access isn’t a simple “user → group → app” graph anymore. It’s a living ecosystem.
2) Work is becoming agentic
Agents will take actions in tools: creating resources, responding to incidents, onboarding vendors, running finance workflows.
If agents can do work, they must have access. If they have access, access must be governed. If access must be governed, the governance must be continuous and machine-enforceable.
Periodic reviews and ticket workflows don’t fit that world.
Elevator pitch: why build AI-native IAM
AI-native IAM is the control plane for safe autonomy. It makes access decisions faster and safer by continuously understanding real entitlements (including tokens and delegations), reasoning about least privilege and blast radius, executing changes across the long tail of systems, and producing audit-grade evidence by default. It replaces fragile, manual IAM operations with a governed system that can keep up with constant org change—and with agents doing real work.
If you can build that, you’re not making a better form. You’re changing the operating system.
The foundations: what an AI-native IAM product must be built on
Before you talk about “agents,” you need a substrate that makes safe automation possible.
1) An identity + entitlement graph
You need a unified model of:
- identities (employees, contractors, vendors, service accounts, agents)
- groups and roles (IdP groups, app-local roles, cloud roles)
- entitlements (permissions, scopes, resource-level access)
- resources (projects, repos, datasets, customer accounts)
- relationships (who can grant what, who owns what, what is inherited)
- non-human access paths (API tokens, OAuth grants, delegated connections)
If you don’t have the graph, you don’t have ground truth.
2) An integration fabric (read + write)
“Supports SCIM” is table stakes—and insufficient.
AI-native IAM requires connectors that can:
- read entitlements deeply (app-local roles, permissions, resource scope)
- write changes back (provisioning, deprovisioning, role changes)
- handle the long tail via REST APIs, SDKs, and custom integrations
- detect drift when app configurations change
- inventory and control tokens and delegations where the underlying system exposes them
Without write access, you have analytics. Not governance. Still useful!
3) A policy control plane
Policies must be:
- explicit (not tribal knowledge)
- machine-enforceable
- scoped by risk (what can be automated vs what requires approvals)
- mapped to data sensitivity and operational constraints
Policies become guardrails for autonomy.
4) Provenance and auditability by default
Every decision and action needs an evidence trail:
- inputs (what data was used)
- reasoning artifact (why the system decided)
- approvals (who signed off, under what policy)
- actions (what changed, where)
- verification (did the change actually take effect)
If you can’t prove it, you can’t run it in production.
The advantage of also being the IdP
You can build AI-native IAM without being an IdP. Many organizations will also require it, because they already have one. But it’s worth naming why “AI-native IAM + IdP” can be uniquely powerful when done correctly.
Being the IdP gives you a privileged control point for both authentication and delegation.
What that buys you:
- You’re already in the SSO path. If your product is the system that issues SAML/OIDC assertions, you see what apps are actually being used, by whom, and when—without relying solely on periodic app inventories.
- You get first-class control over “who can access what” at login time. SSO policy, step-up authentication, device posture gates, conditional access—these are enforcement levers that don’t require every app to be perfectly integrated.
- You can treat OAuth and API delegation as a first-class IAM problem. The next generation of access isn’t just “human → app.” It’s:
- app → app connections
- agent → app permissions
- delegated OAuth scopes that quietly expand data access
- long-lived tokens that outlive the human who created them
If your product also acts as the authorization server for OIDC/OAuth (or has deep hooks into it), you can often discover, govern, and revoke those delegations with far more precision.
Important nuance: being the IdP doesn’t magically reveal every third-party OAuth grant that lives inside every SaaS ecosystem. For those, you still need deep connectors. But owning (or deeply integrating with) the IdP gives you a clean enforcement and visibility layer for a large and growing set of access paths—and it reduces blind spots that pure “workflow IAM” tends to miss.
Practically, it’s the difference between:
- “We disabled the account” and
- “We revoked the identity, invalidated active sessions, and removed delegated access paths tied to that identity.”
That’s a big deal in a world of app-to-app sync, automation, and agent permissions.
The maturity model: levels of AI-native IAM
“AI-native” isn’t binary. It’s a gradient. Here’s a practical ladder you can use to classify a product—or your internal state.
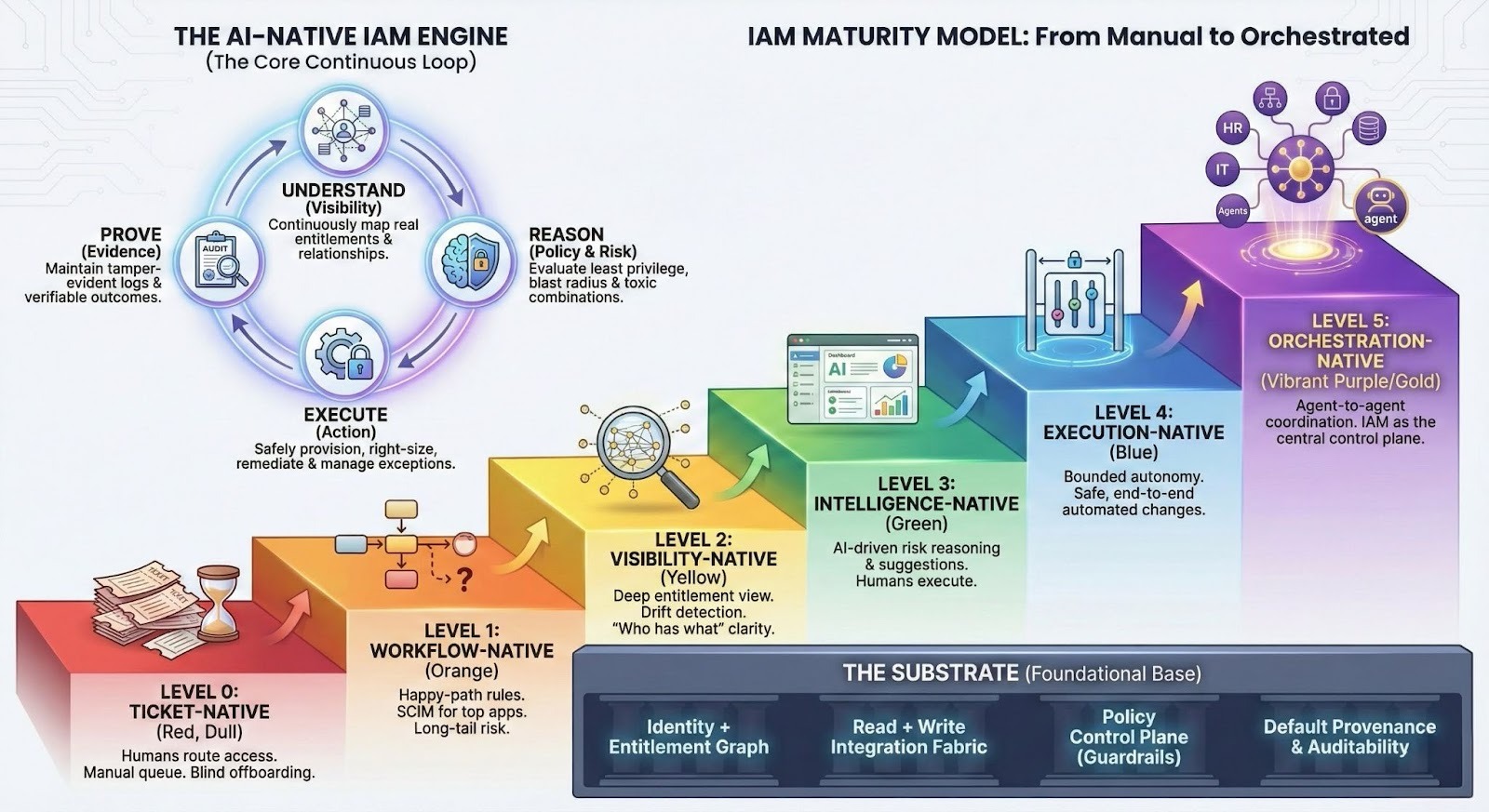
Level 0 — Ticket-native IAM
Operating model: humans route access through tickets and chat.
- Requests are manual.
- Fulfillment is manual in admin consoles.
- Offboarding is best-effort.
- Evidence is assembled during audits (painfully).
Tell-tale sentence: “We disabled the account, but we’re not sure what else still has access.”
Level 1 — Workflow-native IAM
Operating model: rules automate the happy path.
- Joiner/mover/leaver workflows exist.
- Some SCIM provisioning works for top apps.
- Exceptions still require humans.
- RBAC exists, but drifts over time.
What improves: speed and consistency—until reality deviates.
Common failure: the “long tail” of apps stays unmanaged, and that’s where risk accumulates.
Level 2 — Visibility-native IAM
Operating model: entitlement coverage becomes real.
- Deep visibility into app-local roles and resource-level permissions.
- A unified “who has access to what and how.”
- Drift detection: reality vs intended state.
- Visibility expands beyond “accounts and groups” into delegated access paths where possible (tokens, OAuth grants, app-to-app connections).
Key unlock: You can finally govern what you can actually see.
Litmus test: Can you answer this reliably: “Show me every path by which Alex—or Alex’s automations—can reach Customer Data X.”
Level 3 — Intelligence-native IAM
Operating model: AI improves decisions; humans still execute most changes.
AI meaningfully helps with:
- role mining and role suggestions (RBAC hygiene)
- risk-based access reviews (prioritize what matters)
- toxic combinations and separation-of-duties conflicts
- blast radius analysis (what compromise would expose)
- flagging risky delegations (over-broad OAuth scopes, stale tokens, suspicious app-to-app access)
Humans remain the primary operators for remediation and enforcement.
Litmus test: Does AI reduce decision time and review fatigue measurably—or just summarize dashboards?
Level 4 — Execution-native IAM
Operating model: AI executes within guardrails.
The system can perform end-to-end operations safely:
- provisioning/deprovisioning across apps (including non-SCIM via APIs/custom)
- just-in-time access with expiration
- permission right-sizing (least privilege applied where safe)
- automated remediation for certain classes of risk
- exception handling with compensating controls
- revoking delegated access where the system has authority (tokens, sessions, OAuth grants, app-to-app connections)
But it’s not “hands-off.” It’s bounded autonomy:
- approvals required for high-risk actions
- least-privileged agent identity
- change previews and rollback
- tamper-evident logs
Outcome: IAM starts behaving like an always-on team, not a queue.
Level 5 — Orchestration-native IAM (agent-to-agent IAM)
Operating model: IAM becomes a coordinator across systems and owners.
At this level, IAM is no longer a single system acting in isolation. It can coordinate across:
- HR (employment status, org changes)
- IT (device posture, endpoint health)
- security tooling (SIEM/SOAR, detection context)
- data governance (sensitivity, residency, policy constraints)
- application owners (approval and ownership boundaries)
- finance/procurement (vendor onboarding and renewals)
- agent ecosystems (agent identity, delegated permissions, agent-to-app scopes)
Work becomes a structured flow:
Intent → policy evaluation → negotiation → approvals → execution → evidence
Humans stay in the loop for:
- policy changes
- new trust boundaries
- high-risk access
- exceptions that exceed guardrails
Distinctive capability: The product can coordinate multi-step outcomes across multiple owners while remaining auditable and safe.
A quick glossary for the concepts that matter
- Entitlements: the concrete permissions granted inside systems (roles, scopes, resource access), not just group membership.
- Blast radius: what an identity can reach if it’s compromised—directly and indirectly (via escalation paths and delegated access).
- Toxic combinations / SoD: permission pairings that create fraud or high-risk capability when held by the same identity.
- JIT access: permissions granted temporarily for a task, with automatic expiration and logging.
- Delegations: non-human access paths such as OAuth grants, app-to-app connections, and tokens that allow one system to act on behalf of another.
How to evaluate an “AI-native IAM” claim in practice
If you want to classify a product (or your own setup), ask these questions.
Coverage and visibility
- Can it show app-local entitlements and resource-level permissions, not just IdP groups?
- What percentage of apps are integrated for read?
- What percentage are integrated for write (the ability to enforce changes)?
- Can it inventory and reason about tokens and delegated access paths (OAuth grants, app-to-app connections) where those systems expose them?
Decision quality
- Can it explain why access was granted or denied in policy terms?
- Can it quantify risk using blast radius, sensitivity, privilege tiering, and toxic combos?
- Does it understand context (role, team, project, device posture, data sensitivity)?
- Does it recognize that “the user” might be acting through automation, delegation, or an agent?
Execution and safety
- Can it remove access everywhere on offboarding, including app-local admin paths?
- Does it support JIT + expiration + break-glass workflows?
- Can it revoke sessions/tokens/delegations where applicable?
- Does it preview changes and support rollback?
Governance and evidence
- Can you reconstruct an access decision end-to-end months later?
- Are logs tamper-evident and audit-ready?
- Can you prove “policy was enforced,” not just “someone clicked approve”?
If the answers are mostly “no,” it may still be valuable software—but it’s not AI-native IAM.
Three mini-stories that reveal the level immediately
1) Offboarding: “disabled” vs “deprovisioned”
- Ticket/workflow-native: IdP disabled, maybe SCIM deprovisioned in some apps; app-local roles linger.
- Visibility-native: you can see all entitlements; you know what must be removed.
- Execution-native: entitlements are actually removed everywhere, tokens revoked, suspicious delegations flagged, verification recorded.
- Orchestration-native: downstream owners are looped in automatically (transfer ownership, rotate credentials, reassign on-call, revoke agent scopes), and evidence is packaged automatically.
2) Access reviews: spreadsheets vs continuous governance
- Legacy: quarterly spreadsheet of “users in groups,” reviewed with rubber-stamp approvals.
- AI-native: continuous risk-based review:
- focus on high-risk permissions and anomalies
- auto-expire stale exceptions
- propose and execute right-sizing where safe
- treat delegated access (OAuth grants, app-to-app connections) as reviewable access too
- generate evidence without manual compilation
3) Incident response: panic vs containment
- Legacy: scramble to understand what the compromised identity can access.
- AI-native: blast radius is computed immediately:
- prioritize what to revoke first (including delegations)
- enforce step-up auth/JIT where needed
- contain lateral movement paths
- record exactly what was changed and why
In each case, the difference isn’t a better interface. It’s a different operating system.
Common traps and “AI-native” theater
Watch for these patterns:
- Chat-first, integration-last If the product can’t write changes back across systems, it can’t enforce governance.
- Recommendations without remediation “Here’s a risk” is only useful if the system can reduce it safely.
- Automation that breaks auditability If you can’t reproduce why a decision happened, you can’t trust it.
- RBAC as a one-time project Roles drift. Teams change. Apps change. AI-native IAM treats RBAC as a living system.
- Ignoring delegated access paths Disabling accounts but leaving OAuth grants and tokens untouched is the modern version of “we forgot the shared folder.”
What AI-native IAM unlocks
When IAM becomes continuous, intelligent, and executable, a few things happen:
- Onboarding becomes fast without becoming sloppy Access is granted with least-privilege defaults, not “give them everything and fix it later.”
- Offboarding becomes complete and provable You stop carrying invisible risk for months.
- Standing privilege drops More JIT, fewer permanent admin entitlements.
- Delegated access becomes governable OAuth scopes, app-to-app connections, and agent permissions stop being invisible side channels.
- Audits become a byproduct Evidence is generated continuously, not assembled in a fire drill.
- Agents can do real work safely Because access is governed as a first-class system, not an afterthought.
Closing checklist: if you only remember six things
- Entitlements matter more than identities. Groups are not access. Permissions are access.
- Integration depth is destiny. Read + write coverage across the long tail is what makes governance real.
- Policies must be enforceable, not aspirational. PDFs don’t prevent over-privilege.
- Bounded autonomy beats manual heroics. Automate what’s safe. Escalate what’s risky. Log everything.
- Provenance is part of the product. “We can prove it” is the difference between a demo and production.
- Don’t forget delegation. OAuth grants, tokens, app-to-app connections, and agent scopes are access paths too—and they need governance.
AI-native IAM is not “IAM with chat.” It’s IAM that continuously understands, decides, executes, and proves—so the company can move faster without expanding its blast radius. And if you can combine that with the IdP layer (or integrate so deeply it behaves like one), you get a uniquely strong enforcement point for both human and non-human access in an increasingly automated world.
