SaaS discovery beyond what your IDP controls
See every application your employees use, how access was granted, and whether it aligns with policy, even when it bypasses your IDP.
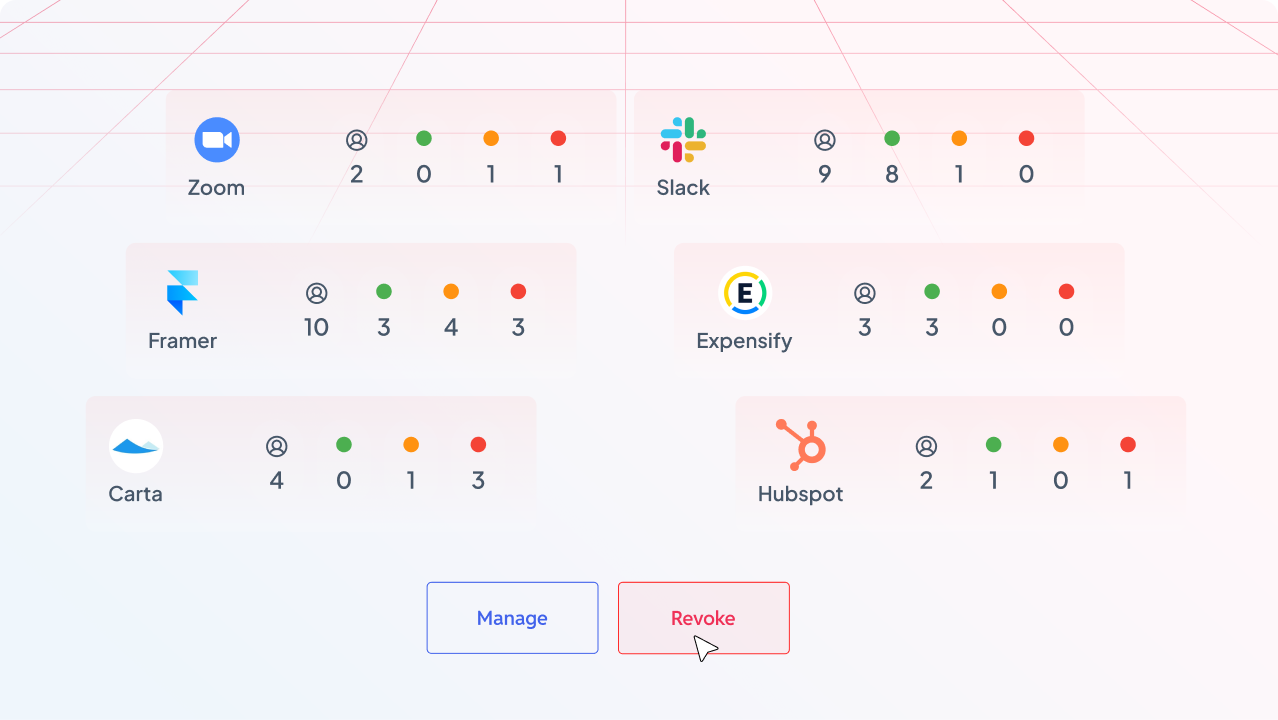
Visibility where traditional identity tools go blind
Most identity tools only show what they control. YeshID shows what actually exists.By observing real sign-in behavior, OAuth grants, and unmanaged access paths, YeshID exposes shadow applications without requiring every app to be onboarded or enforced through SSO first.
Get a DemoDiscover applications employees actually use
YeshID identifies SaaS applications employees sign into through Google and Microsoft login flows, OAuth consent screens, direct app invites, and background integrations. You see the applications that exist in practice, not just the ones formally onboarded to your IDP.
Full visibility into OAuth, tokens, and non-human access
Shadow IT extends beyond users. YeshID surfaces OAuth grants, service accounts, bot tokens, and embedded integrations associated with each application, including the scopes granted and the data they can access.
Risk context instead of flat inventories
YeshID evaluates discovered applications based on access sensitivity, scope breadth, and data exposure. Rather than a long list of tools, you get clear signal about which applications introduce real risk and which ones are low impact.
Govern shadow apps without blocking teams
Discovery does not force immediate enforcement. YeshID lets you flag applications for review, require approval for future access, restrict OAuth scopes, or formally onboard apps into managed workflows without disrupting existing work.
Continuous discovery that keeps up with change
SaaS usage evolves constantly. YeshID continuously monitors sign-ins and access grants so new applications, integrations, and tokens are surfaced as they appear, not months later during audits.
“No solution really sat between manually managing all of my SaaS and Okta until YeshID came along. Not sure how I could manage my org without it”


