Just-in-time access without permanent privilege creep
Grant temporary access across automated and non-automated applications, enforce eligibility through policy, and revoke or de-escalate privileges automatically.
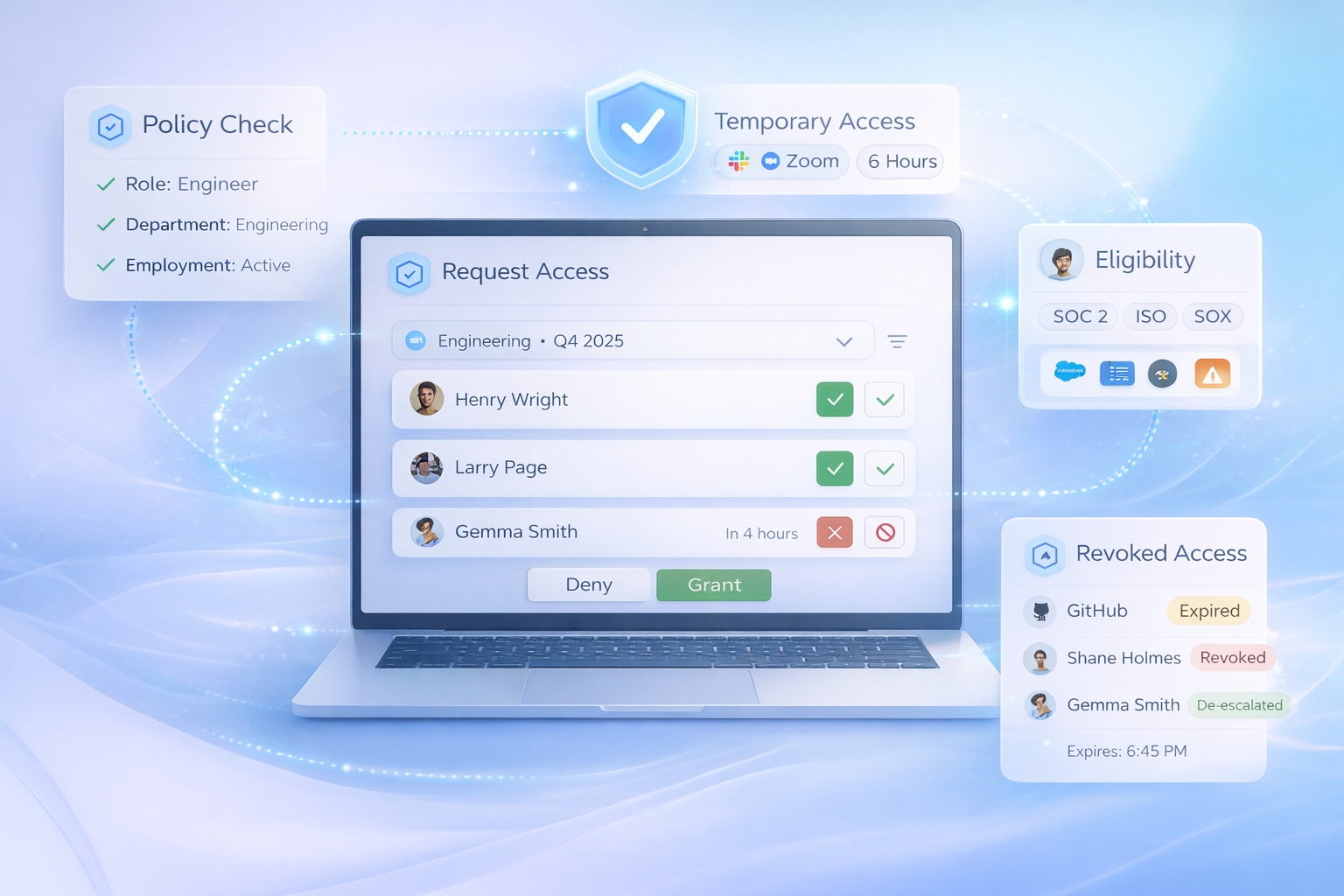
Temporary access treated as a lifecycle event
YeshID treats just-in-time access as a controlled lifecycle event. Temporary access is granted based on policy, enforced across both automated and manual systems, and revoked when conditions change.
Get a DemoPolicy-gated eligibility before access is requested
Users can only request just-in-time access if policy allows it. If a role, attribute, or employment state should never permit access, the request cannot be made.
Time-bound access with automatic revocation or de-escalation
Every just-in-time grant includes a defined duration. When the window expires, YeshID revokes access or reduces privileges back to the approved baseline.
Works across automated and non-automated applications
For applications that support automation, YeshID enforces access changes directly. For systems that do not, YeshID tracks, flags, and governs access so manual gaps do not become invisible risk.
Temporary access without corrupting roles or groups
Just-in-time access is handled separately from baseline roles and groups, preventing short-term needs from permanently altering access models.
Visibility into long-term drift from temporary access
YeshID shows where temporary access is repeatedly granted, whether it was properly removed, and where “temporary” access has effectively become permanent drift.
“No solution really sat between manually managing all of my SaaS and Okta until YeshID came along. Not sure how I could manage my org without it”


