Role-based access control you can understand and trust
Define access policies clearly, see who qualifies for them, and enforce access without burying logic in brittle groups or hidden rules.
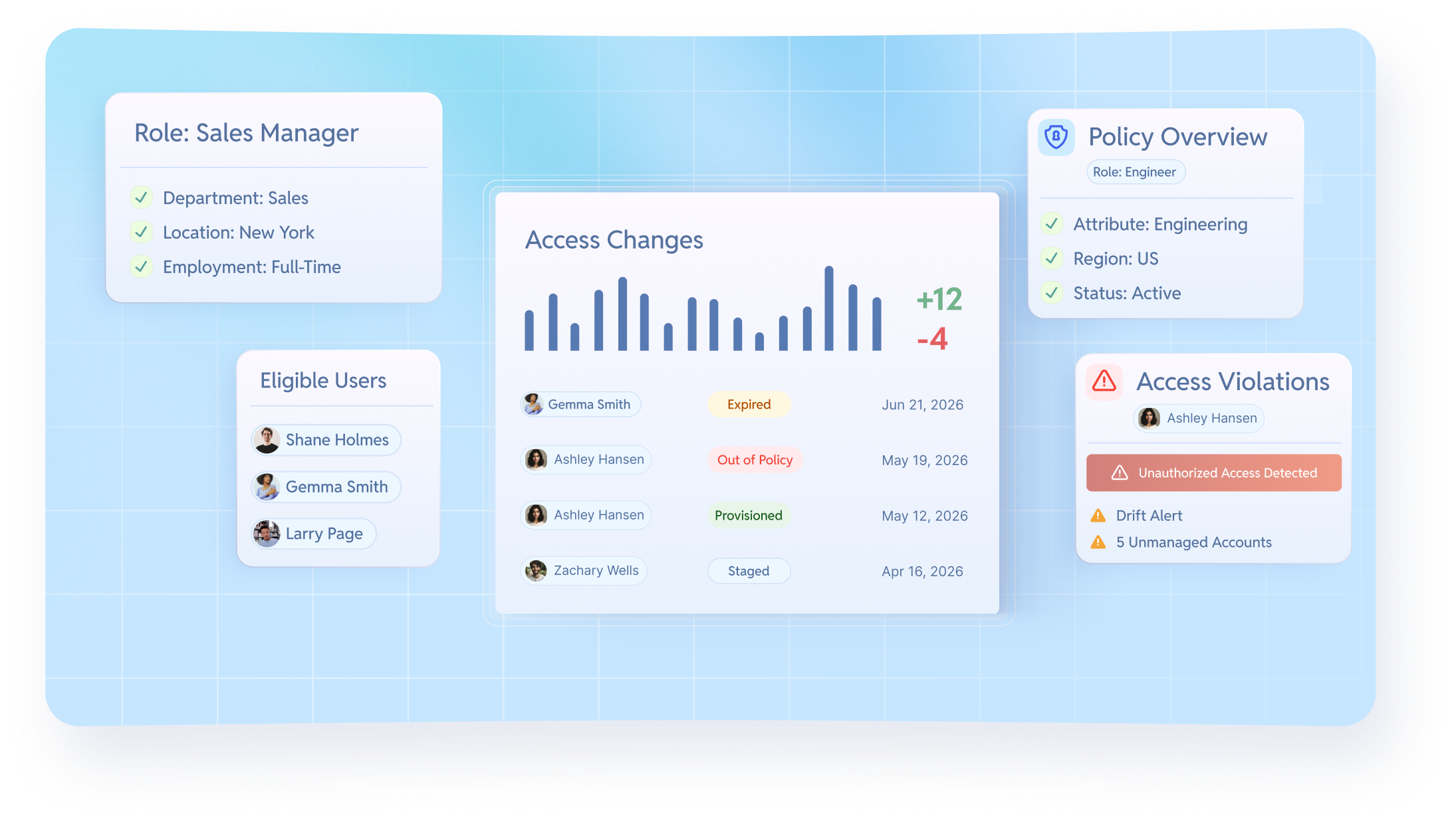
RBAC built for how access really works
YeshID treats RBAC as a living policy system, not a static role directory. Roles are defined based on attributes and intent, evaluated continuously, and enforced across real systems where access actually lives.
Get a DemoRoles defined as policies, not group sprawl
Instead of encoding access logic into opaque groups, YeshID lets you define roles as readable policies. You can see who qualifies, why they qualify, and what access the role is meant to grant.
Dynamic evaluation instead of one-time assignment
Access is evaluated continuously based on user attributes like role, department, location, or employment type. When those attributes change, access adjusts automatically without manual cleanup.
Separation between policy and execution
YeshID separates the definition of a role from how access is provisioned. Policies stay clean and intentional, while provisioning actions can vary by system, integration, or exception.
Drift surfaced, not hidden
When access diverges from policy, YeshID makes it visible. You can see approved exceptions, accidental over-provisioning, and unmanaged access without relying on guesswork or audits to uncover it later.
RBAC that works across modern and messy stacks
Roles are enforced across SaaS apps, directories, APIs, and non-human identities, even when access was granted outside your primary identity provider.
Clear visibility into role impact and change
Every role change is logged and explainable. You can see when a role definition changed, who it affected, what access was granted or removed, and why without reconstructing intent after the fact.
“No solution really sat between manually managing all of my SaaS and Okta until YeshID came along. Not sure how I could manage my org without it”


