AI for IAM admins: stop bolting chat onto dashboards—build a real colleague
I’m Alex, CTO of YeshID. I spend a lot of time with IAM admins, security teams, and CTOs who are trying to keep organizations safe while the identity surface area keeps expanding: more apps, more identities, more automation, more exceptions, and more ways for access to silently drift into dangerous states.
That’s why I’m skeptical of a big chunk of “AI-native IAM” messaging in the market. Too often it means: a chat box on top of the same dashboards you already have.
AI isn’t the problem. The layer it’s applied to is.
The real opportunity is not making IAM easier to query. It’s making IAM easier to operate by giving admins something they rarely get: a true colleague—a senior, deeply technical IAM/Security/SWE partner who can investigate across systems, connect the dots, prioritize what matters, and help you act safely.
That’s what we’re building at YeshID: Rae.
Why dashboards and rules don’t solve the real IAM job
IAM isn’t hard because UIs are bad. It’s hard because the work is cross-system and investigative:
- Access lives across IdP, directory, IGA, cloud IAM, SaaS admin consoles, CI/CD, secrets managers, and logs.
- Entitlements aren’t “one toggle.” They’re chains: group nesting, role inheritance, policy attachments, SCIM mappings, exceptions, break-glass paths, and shadow admin capabilities.
- The cost of mistakes is asymmetric: miss a privilege path and you get breached; remove the wrong access and you take production down.
Dashboards are good at showing what one system believes right now. Rules are good at enforcing known policy deterministically.
But admins spend their time on the work that doesn’t fit neatly into either:
- reconstructing how access happened,
- understanding blast radius and toxic combinations,
- diagnosing drift and broken provisioning,
- validating offboarding completeness,
- and executing changes without outages.
That’s not a “UI problem.” It’s an insight problem.
The AI trap in IAM
There’s a pattern I keep seeing:
- “Ask AI” summarizes what’s already on the screen.
- It demos well.
- It doesn’t change outcomes.
A quick litmus test:
- If the job is deterministic and auditable (“if X then Y”), a rule/workflow is the right tool.
- If the job requires reconstructing causal chains across systems, dealing with missing context, and making tradeoffs under risk, AI can be transformative.
IAM needs AI for the second category—the parts that take senior judgment and, most importantly, time.
The bar for a real AI colleague in IAM
If you hired a senior IAM/Security/SWE, they wouldn’t add value by reading dashboards back to you. They’d add value by:
- knowing where to look across systems,
- correlating identity facts with activity and change history,
- spotting second-order effects (“this change breaks deploys”),
- producing a plan with options, risks, and rollback,
- preventing catastrophic mistakes,
- and doing the tedious legwork fast.
That’s the bar we hold Rae to.
Not “answers.” Not “summaries.” Operational insight.
What Rae does (today) with the evidence you can actually see
I don’t have long-form public case studies yet. But I can show screenshots of Rae doing the kinds of work IAM teams feel every day—work that normally takes hours of stitching context together across tools.
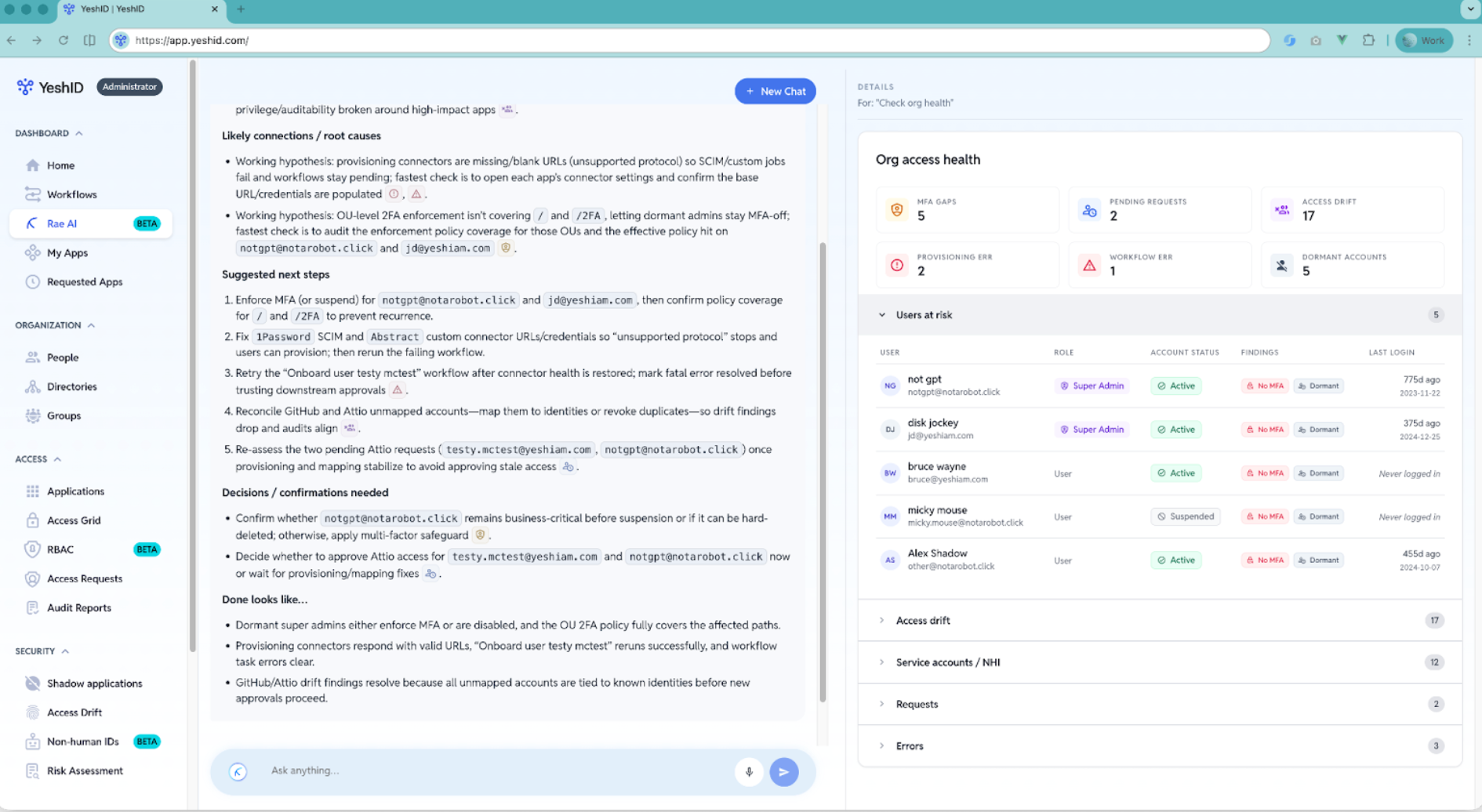
1) Org-wide health synthesis that tells you what matters this week
Instead of another dashboard tile, Rae produces a prioritized view of the identity program’s health and drift—what changed, what’s risky, what’s broken, and what to look at first.
What this is meant to replace is the “I have 20 tabs open and still don’t know where to start” problem.
2) Shadow-IT discovery and access reality, not wishful inventory
Shadow IT isn’t just “apps we don’t like.” It’s unreviewed access paths, unmanaged admin surfaces, and data exposure outside your core controls.
Rae is built to help you identify and reason about:
- what’s actually being used,
- where identities exist outside your expected systems,
- and where access is being granted through side doors.
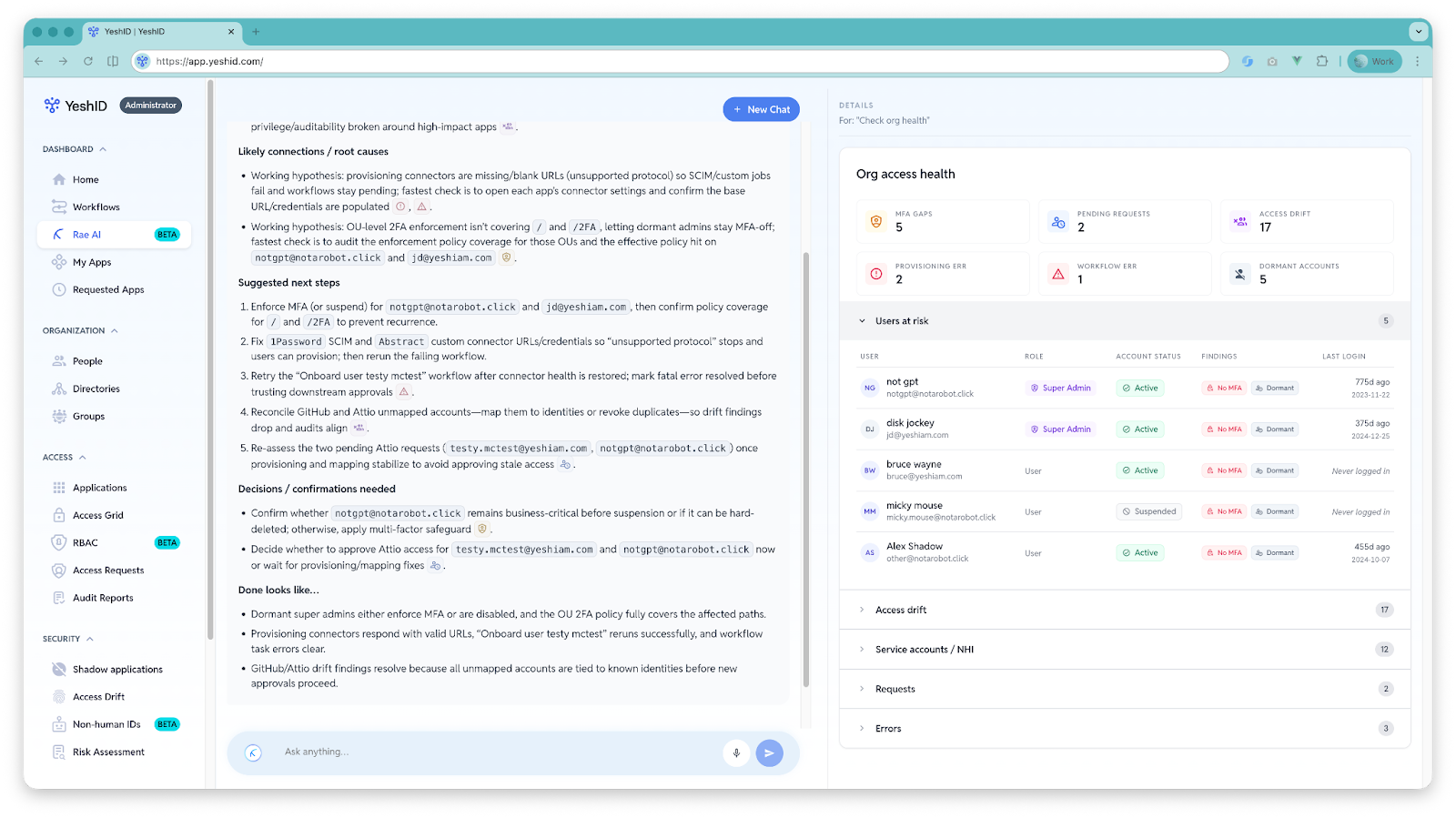
3) Non-human identity analysis (service accounts, tokens, automation, agents)
Non-human identities are now one of the fastest-growing risk surfaces: service principals, API tokens, CI identities, integrations, ephemeral workloads, and long-lived credentials.
Rae helps you answer questions like:
- Which non-human identities exist, and where?
- Which ones are over-privileged relative to their observed use?
- Which ones are stale, orphaned, or quietly “immortal”?
- Where are the credential and trust boundaries actually weak?
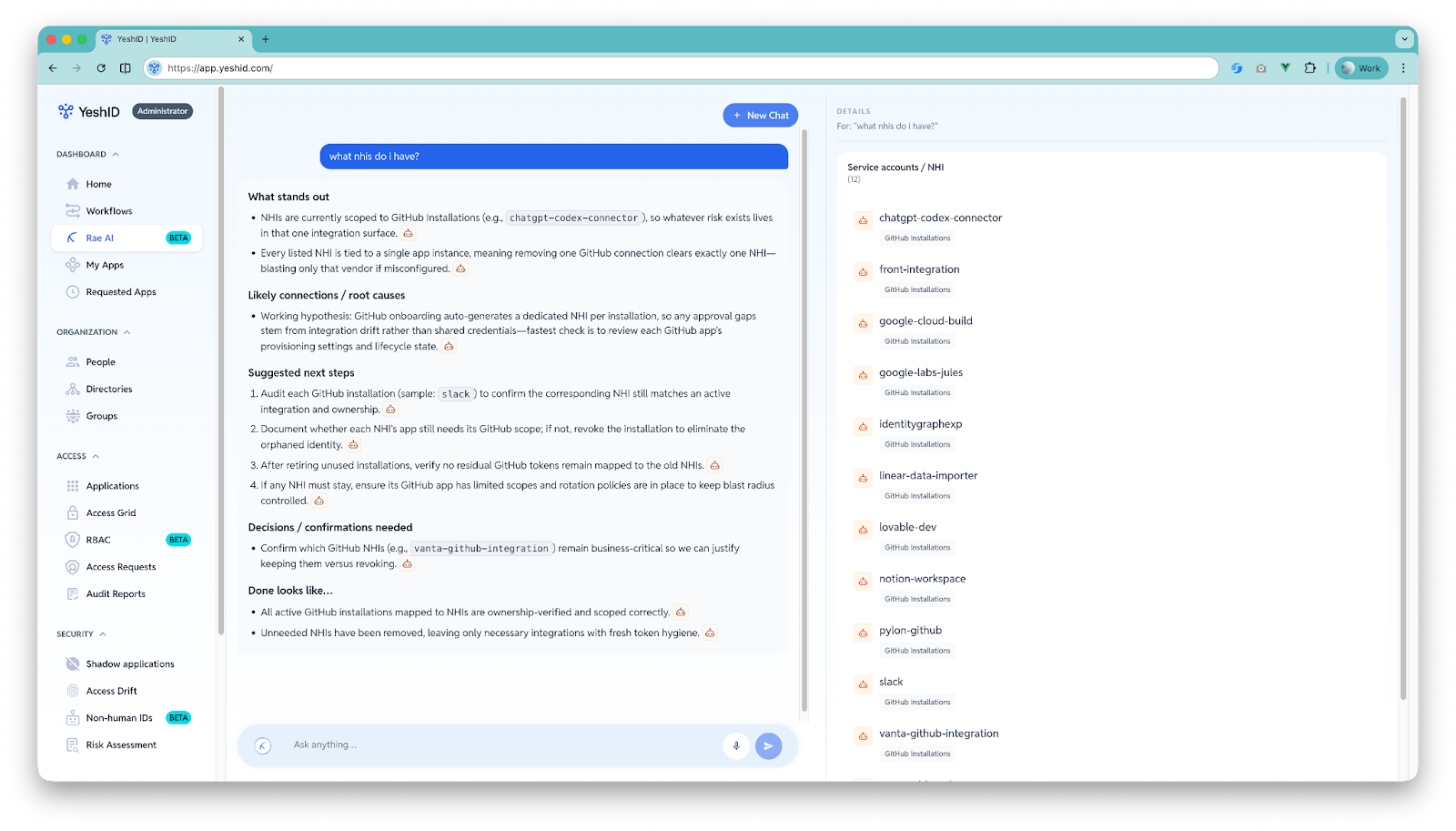
4) Workflow building that turns insight into repeatable operations
In IAM, one-off investigations don’t compound unless they become repeatable workflows: approvals, validations, structured work items, execution steps, documentation.
Rae helps you take “here’s what we found” and convert it into “here’s how we handle this every time.”
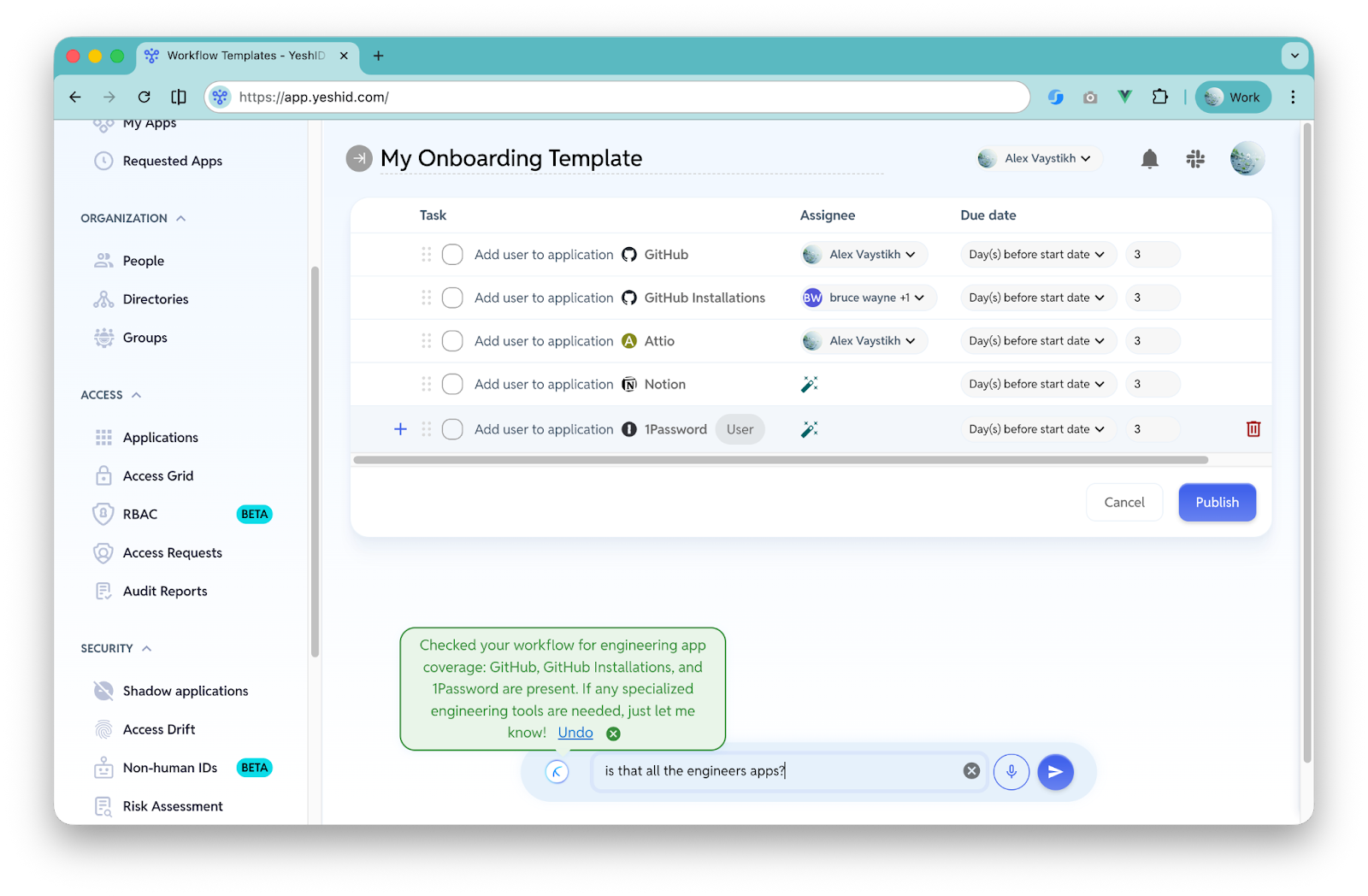
5) Integration building with code for the long tail (especially non‑SCIM apps)
Every IAM team hits the same wall: the long tail of apps that don’t support SCIM cleanly (or at all), plus internal tools and custom platforms.
Rae can write integration code to connect those systems—making it practical to:
- automate provisioning/deprovisioning,
- reconcile entitlements,
- perform targeted access changes,
- and reduce the backlog of “we’ll integrate it someday.”
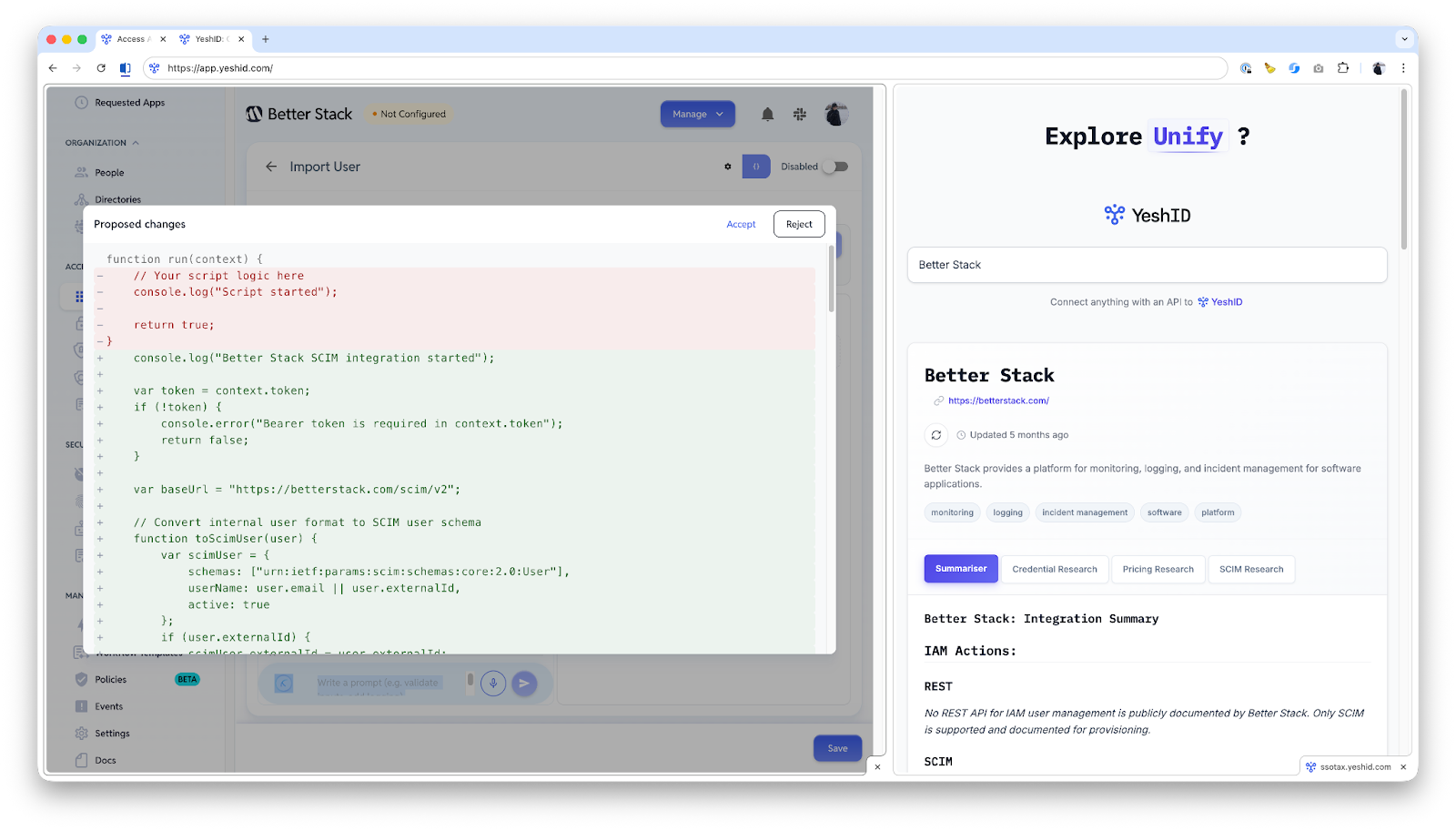
This is not “AI for vibes.” It’s engineering leverage applied directly to the most stubborn part of IAM operations.
“Acts” without autopilot
IAM is too high-stakes for “just let the agent do it.”
A real colleague doesn’t blindly execute. They:
- investigate,
- propose,
- highlight risks and dependencies,
- and help operationalize safely through controlled workflows and review.
Rae is designed to take work off the admin’s plate without taking away responsibility—and to reduce the most expensive failure mode in IAM: a fast, confident mistake.
How to evaluate “AI-native” IAM in 5 questions
Here’s a practical filter:
- Does it create new understanding, or just rephrase existing screens?
- Can it explain “how did this access happen?” with a traceable chain of evidence?
- Does it prioritize what matters, or just generate more output?
- Can it operationalize (workflows, validations, structured execution), not just answer?
- Does it reduce the long-tail integration tax—or does it assume perfect connectors and SCIM everywhere?
If the product can’t do those things, “AI-native” is likely just UI polish.
The point of Rae
Rae is built to be the colleague IAM teams have always needed: deeply technical, cross-system, tireless about investigation, and practical about turning findings into action.
Not to replace how you think—but to give you time back to do what no AI can do for you: decide what matters for your organization, set the tradeoffs, and drive the program forward.
