Agentic AI for IAM, Built for Trust
Why AI Agents in IAM Are a Security Breakthrough (and a Security Risk) — and How YeshID Makes Them Trustworthy
Identity and Access Management (IAM) is where enterprise AI gets real.
An AI agent that can answer “why does this person have access?” and then actually fix it—remove an over-privileged role, expire time-bound access, or open the right approval workflow—removes hours of manual work from every joiner/mover/leaver and every audit. It also touches the most sensitive control plane in the company.
That’s why “generic AI assistants” are a non-starter for IAM. The hard problem isn’t whether an LLM can write a nice response. The hard problem is whether an agent can safely operate with:
- untrusted inputs (Slack messages, tickets, email),
- sensitive identity data (entitlements, group membership, access history), and
- the ability to change access.
This is exactly the failure mode security researchers are worried about: prompt injection.
Prompt injection is the reason “AI + IAM” needs new architecture
Prompt injection is a fundamental, unsolved weakness in LLMs: untrusted strings that get into an agent’s context can cause it to ignore developer instructions and take unauthorized actions.
Meta’s “Email-Bot” example illustrates the risk clearly: if an attacker can get a malicious instruction into an email, and the agent reads it, the agent can be hijacked into exfiltrating private data or taking unwanted actions.
Now translate that to IAM:
- The “email” becomes a Slack message, a ticket, or a request form.
- The “private inbox” becomes your directory, entitlements, audit logs, and policies.
- The “send email tool” becomes “add user to group,” “grant role,” “create service principal,” or “rotate keys.”
In IAM, the agent isn’t just summarizing. It’s holding the keys to the kingdom.
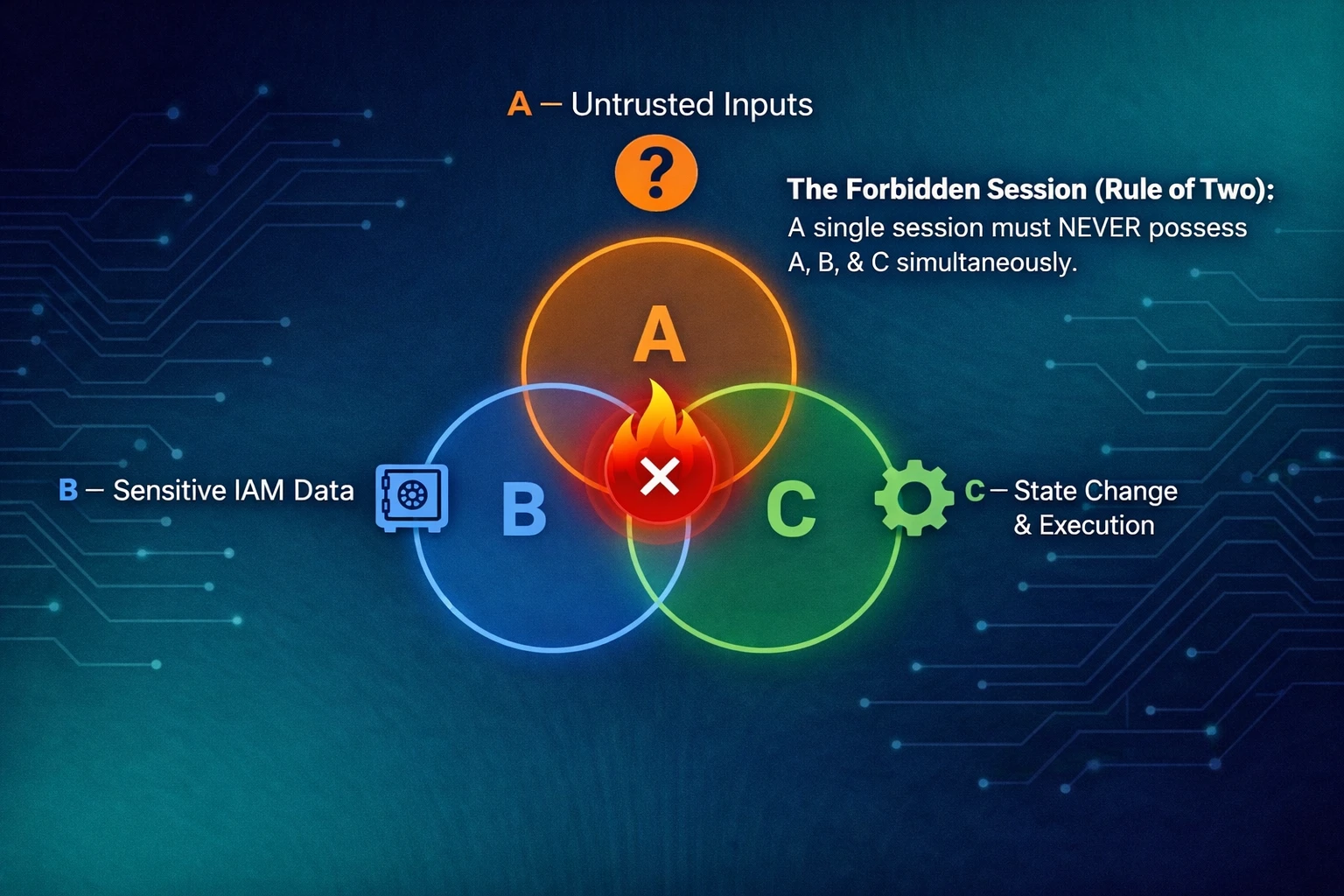
The practical framework: Agents Rule of Two
Meta’s proposed framework (inspired by Chromium policy thinking and the “lethal trifecta” concept) is simple and intentionally practical: until we can reliably detect and refuse prompt injection, an agent should satisfy no more than two of three properties within a single session.
Those three properties are:
- [A] Process untrustworthy inputs
- [B] Access sensitive systems or private data
- [C] Change state or communicate externally
If you need all three to complete a request, the guidance is explicit: don’t let the agent run autonomously without a new session boundary and supervision (human approval or another reliable validation method).
Why this matters more in IAM than almost anywhere else
Most “AI agent” demos outside security involve low-stakes failures: wrong travel suggestions, a missed calendar detail, a sloppy summary.
In IAM, the worst-case failure is catastrophic: privilege escalation, persistence via new credentials, or automated lateral movement—triggered by nothing more than a cleverly crafted request.
So the Rule of Two becomes a design constraint, not a theoretical guideline. It forces you to engineer away the exploit chain: A → B → C.
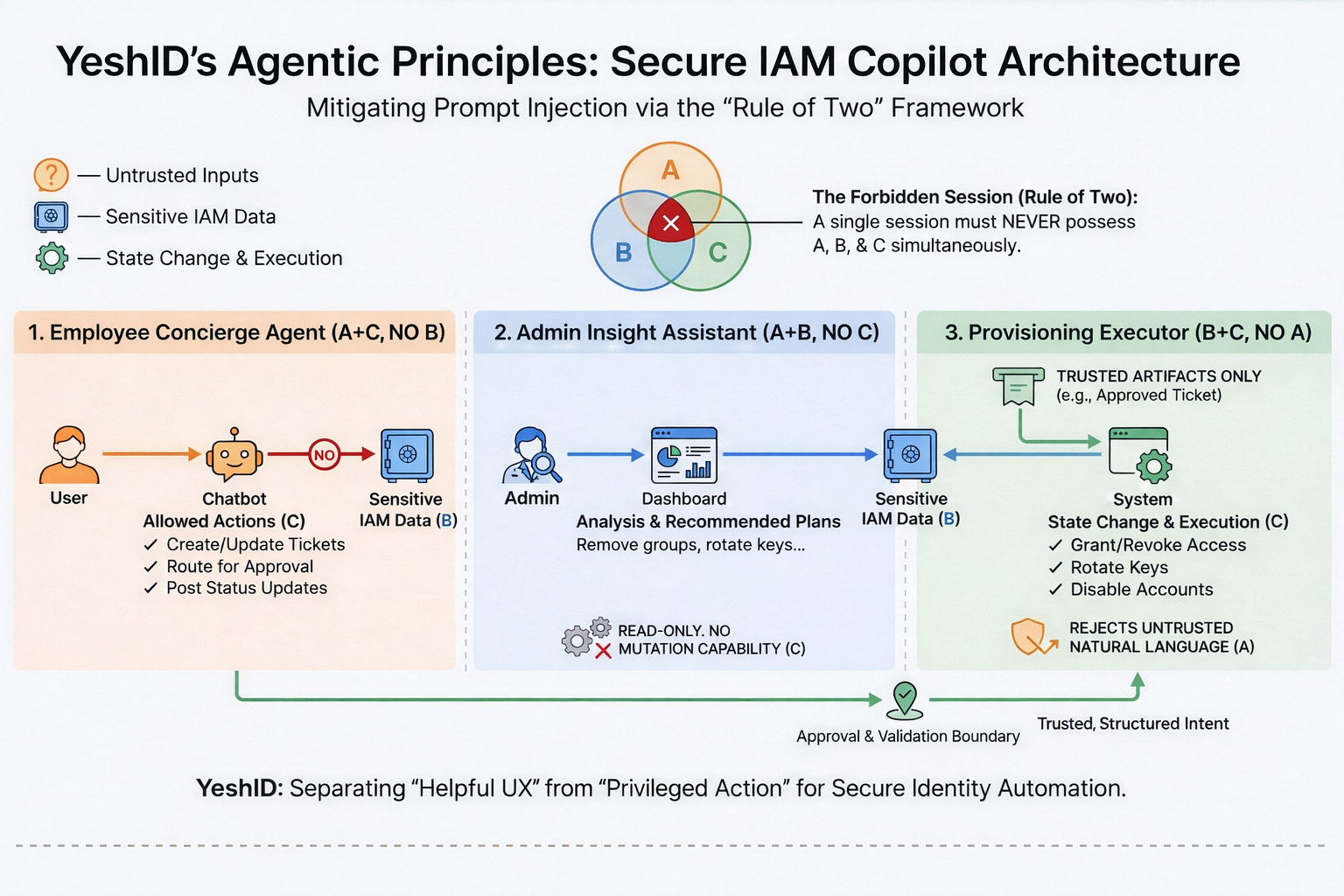
What an IAM agent looks like when it respects Rule of Two
A useful way to think about an “IAM Copilot” is not as one agent, but as three operating modes (or three cooperating agents), each deliberately missing one of the “dangerous” powers.
1) Employee concierge: (A + C), not B
This is the employee-facing helper in Slack/Teams or a portal.
- It can read untrusted requests (“please give me X”) and messy context (A).
- It can communicate and coordinate: open tickets, ask follow-ups, route to approvers, post status (C).
- It cannot query sensitive IAM data broadly (no B).
This is how you get fast employee UX without turning “chat” into “privilege grant.”
YeshID already supports access requests directly in Slack or Teams, including in-line approvals and time-based access that expires automatically.
2) Admin insight agent: (A + B), not C
This is the “answer the hard question” mode for admins and security teams.
- It can read incident notes/tickets (A).
- It can consult sensitive identity and access data (B).
- It cannot take action (no C).
This is a powerful safety posture: prompt injection might distort reasoning, but it can’t immediately translate into an automated entitlement change.
3) Provisioning executor: (B + C), not A
This is the “do it” engine.
- It can read directory/app state (B).
- It can change access (C).
- It only accepts trusted, structured inputs (no A): approved workflows, policy decisions, validated change plans.
This pattern matches the core Rule of Two idea: you can build incredibly capable systems, but you must prevent any single session from being simultaneously exposed to untrusted inputs, sensitive access, and autonomous action.
Where YeshID is different: we built the infrastructure layer that makes “governed agentic IAM” real
A question we hear often is: “Isn’t everyone just adding a chatbot?”
YeshID’s answer is: the model is not the product. The product is the authoritative IAM control plane that makes safe automation possible.
YeshID is built as “an authoritative IAM infrastructure layer” with a continuously updated source of truth for identities, applications, policies, roles, entitlements, and access changes. And YeshID extends your IdP with visibility, policy, and automation across every human, app, and non-human identity.
That foundation is what enables Rae.
Meet Rae: an IAM-native agent, not a generic assistant
Rae is YeshID’s agentic AI purpose-built for IAM—described as “a senior IAM engineer embedded directly into YeshID.” The key is what Rae is built on:
- Authoritative context (not best guesses): Rae operates on up-to-date identity and policy data from the system of record.
- Explainability anchored to real controls: Rae is designed to explain reasoning and “points back to the underlying data and policies.”
- Governed actions: Rae can take actions within guardrails defined by policies and approvals, and actions are intended to be auditable and explainable.
In other words: Rae isn’t useful because it can chat. Rae is useful because it can operate safely inside a governed IAM system.
What Rae does for employees and admins (in practice)
For employees: fast access without security theater
Employees want one thing: get access quickly, with clarity.
With YeshID, employees can request access in Slack/Teams; managers approve in-line; time-based access is supported and expires automatically.
That’s the employee experience layer. Rae adds the intelligence layer: explain what access means, detect risky patterns, and keep the process aligned to policy—without turning every request into an ad hoc admin intervention.
For admins and security teams: turn IAM from “dashboard work” into decisions and action
Rae is described as doing four things that map directly to modern IAM pain:
- Answer IAM questions in context (and explain why) Examples include: why a user has access, which policies grant an entitlement, and what the impact is if a role is compromised.
- Detect risk and drift proactively Rae looks for unsanctioned apps, over-privileged users/roles, policy drift/misconfiguration, and dormant/risky identities—then explains what changed and what to do.
- Take governed IAM actions Rae can flag/quarantine risky access, open workflows for review, provision/deprovision access, and enforce policy standards—within the guardrails defined in YeshID.
- Turn IAM into a security signal Rae correlates identity data with security signals so investigations can be grounded in “who had access to what, when, and why.”
This is the core shift: IAM becomes an operational system, not a set of spreadsheets and alerts.
Why this is a defensible technical wedge
Most companies trying to add AI into IAM start at the UI layer: “chat with your directory.” That’s easy to demo and hard to trust.
The durable wedge is deeper:
1) Authoritative identity context becomes the agent’s “ground truth”
YeshID’s positioning is explicit: continuously updated source of truth across identities, apps, policies, roles, entitlements, and access changes. That means the AI is not improvising. It’s operating on governed data.
2) Governed action is the only path from insight → outcome
The Rule of Two teaches a practical lesson: if you want agents to take action safely, you must design the system so the agent doesn’t combine untrusted inputs + sensitive access + autonomous action in one session.
YeshID’s Rae is described as being “built for environments where trust, auditability, and explainability matter,” and capable of governed actions aligned to YeshID controls.
3) Real-world IAM requires depth: apps, directories, workflows, and lifecycle automation
YeshID’s platform emphasizes lifecycle management, automation from source-of-truth systems, and provisioning/deprovisioning across apps (SCIM, REST, and even manual). That integration depth is what turns an agent from “answering questions” into “operating the system.”
The bigger point: AI agents will reshape IAM—but only the governed ones will ship
Agentic AI is moving toward plug-and-play tool calling, which increases both capability and risk. Meta’s framework is a reminder that the only safe path is architectural: constrain what an agent can do in one session, require supervision when needed, and build defense in depth (including least privilege).
YeshID’s bet is that the winning IAM agent won’t be the one with the cleverest prompt. It’ll be the one built on:
- authoritative identity context,
- clear policy,
- governed action,
- and auditability from day one.
That’s what makes Rae—and YeshID’s approach to agentic IAM—structurally different.
