Start the New Year on the Right Foot: A 5-Day Challenge for Securing Your Google Workspace

Introduction from YeshID
At YeshID, we're big fans of Google Workspace and have adopted it like many other startups. However, we were not fully aware of all the security features it offers.That's why we reached out to our design partner, Ylan Muller, an expert in Google administration, for guidance on best practices for a Google administrator. Ylan is an IT professional with nine years of experience in managing SaaS applications, including Google Workspace, across industries from financial services to software. She currently runs IT at FireHydrant.Ylan provided us with valuable and easy-to-implement advice, even without a dedicated security or IT team. With Ylan's permission, we've turned her advice into a 5-day New Year's challenge to improve our workplace security. Oh and bonus - you don’t have to purchase any new software to put these good practices in place!We're excited to share Ylan's insights with you.
Introduction to Google Security Basics
Inheriting a Google Workspace environment can be an intimidating experience. While you can address some problems through written policy (don’t send sensitive data outside of the org!), Google Workspace offers ample technical control for locking down the data that matters most to your business.I’ve honed in on the settings I find most important to review over several years of managing Google Workspace environments for companies ranging from 50 to 1050 employees and am here to share them with you! Below you will find a list of settings to review and ideas to implement as you look to lock down your Google organization.Welcome to Day 1!
Day 1: Establishing a Secure Foundation - Review and/or Create Your Organizational Unit and Group Structure
Many settings in Google Workspace can be scoped to either a user group or OU. Ideally, groups and/or OUs should be able to represent your organization structure and any other groupings that would be appropriate for slicing and dicing access and settings. For example, you may want to prevent your finance team from sharing files outside of the organization, but your customer success team may need to. Having your groups and OUs set up properly to start will allow you to more easily scope settings.Groups are also used in Google Cloud Platform - if you or your engineering team plans on utilizing GCP in the future, think about how you would want to handle access. Setting up department and team groups in Google Workspace in advance may save you time when you go to configure IAM.We also recommend:
- Avoiding nesting OUs too deeply. Having many layers of nested OUs will get unmanageable quickly since a user can only be in one OU, but they can be in many groups. For example, the nested OU structure below will result in a lot of overheard if you ever need to change a setting for every user who is allowed to share externally:
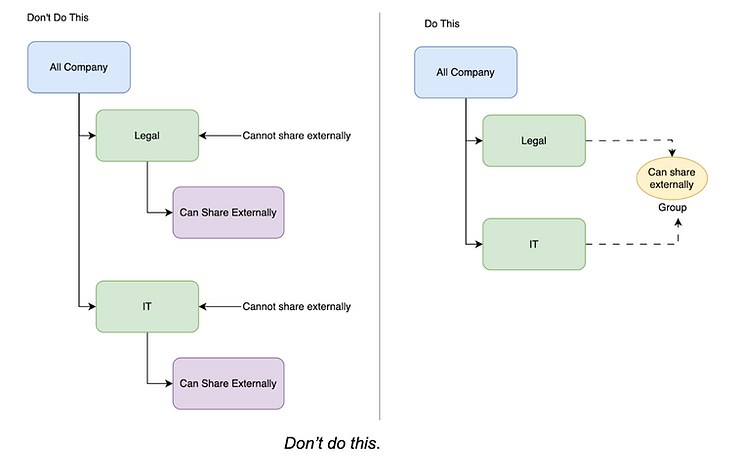
With the newly introduced abilities to apply settings to groups, smaller organizations should consider keeping everyone within a general “Employees” OU while applying settings purely through groups.
- Creating a group for IT as a first-stop for new setting assignments for testing
- Creating a cross-functional group of people in the company, representing all parts of the organization, that can serve as beta testers outside of IT. There is no world in which IT can vet every setting for every use case. Work with this group to collect their feedback about new features or settings you deploy.
If you are on an Enterprise or Education plan you can also construct dynamic groups based on profile attributes to automate memberships.
