From Zero to Secure in 5 Minutes: The Fastest Way to Deploy YeshID

Most companies spend months trying to automate everything. But here’s the truth: if you’re a mid-sized company, full automation is a myth—unless every single one of your apps supports SCIM (and you’re paying for the enterprise tier). Spoiler: they don’t.
That’s why the fastest way to secure your environment isn’t automation. It’s orchestration.
Start by making your core identity workflows—onboarding, offboarding, and access requests—repeatable, visible, and auditable. Then you can optimize the hell out of them.
And with YeshID, you can do that in under 5 minutes.
Step-by-Step: Secure in 5 Minutes Flat
Here’s how you get going—fast.
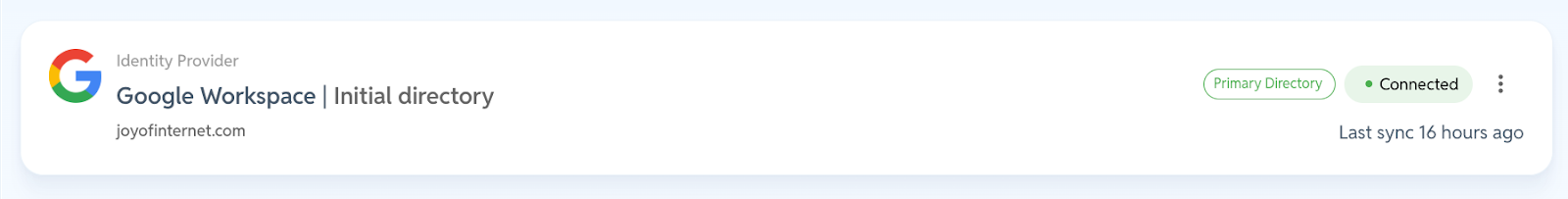
1. Connect your directory (30 seconds)
Choose Google Workspace or Microsoft 365. One click. Grant permissions.
Boom—you now have full visibility into your users, and (bonus!) a list of apps they’re logging into.
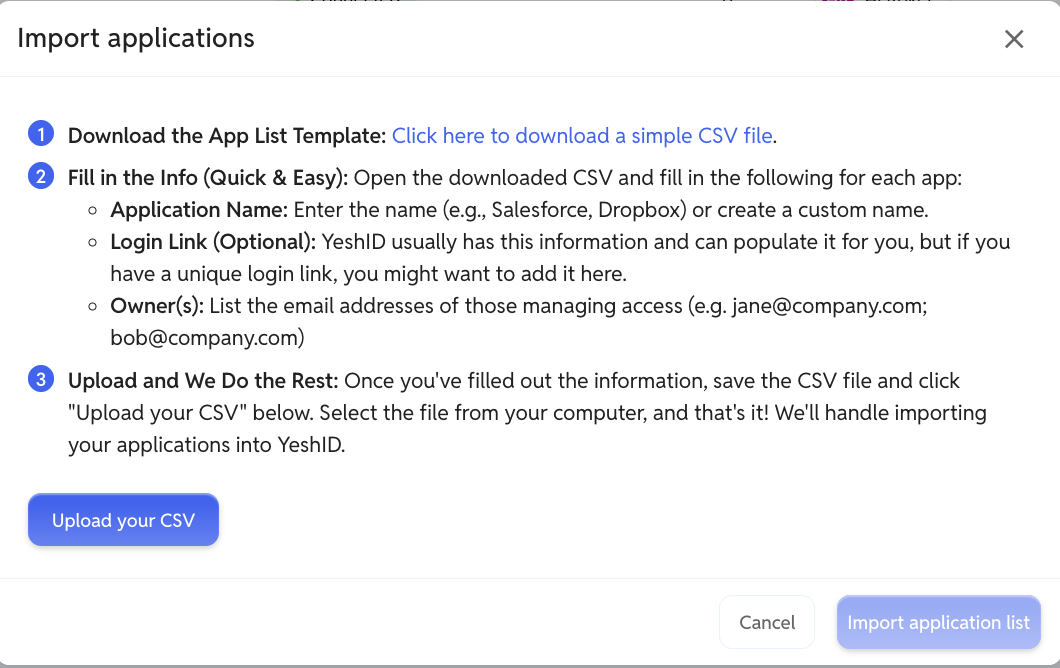
2. Upload your app list (30 seconds)
Grab that Notion doc, spreadsheet, or finance tracker listing the SaaS apps you're paying for.
Drag. Drop. Done.
3. Turn your onboarding checklist into a workflow (30 seconds)
Paste your onboarding steps into our AI agent.
We’ll build an orchestrated onboarding flow that actually runs, not just sits in a doc no one follows.
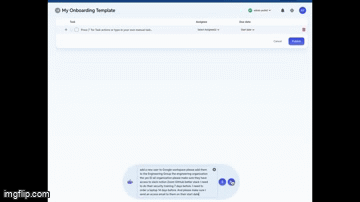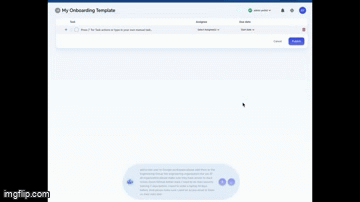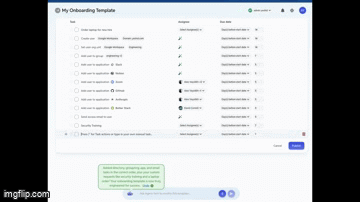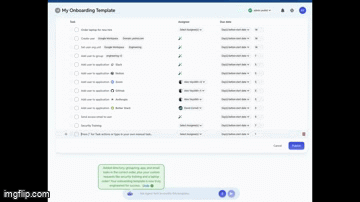
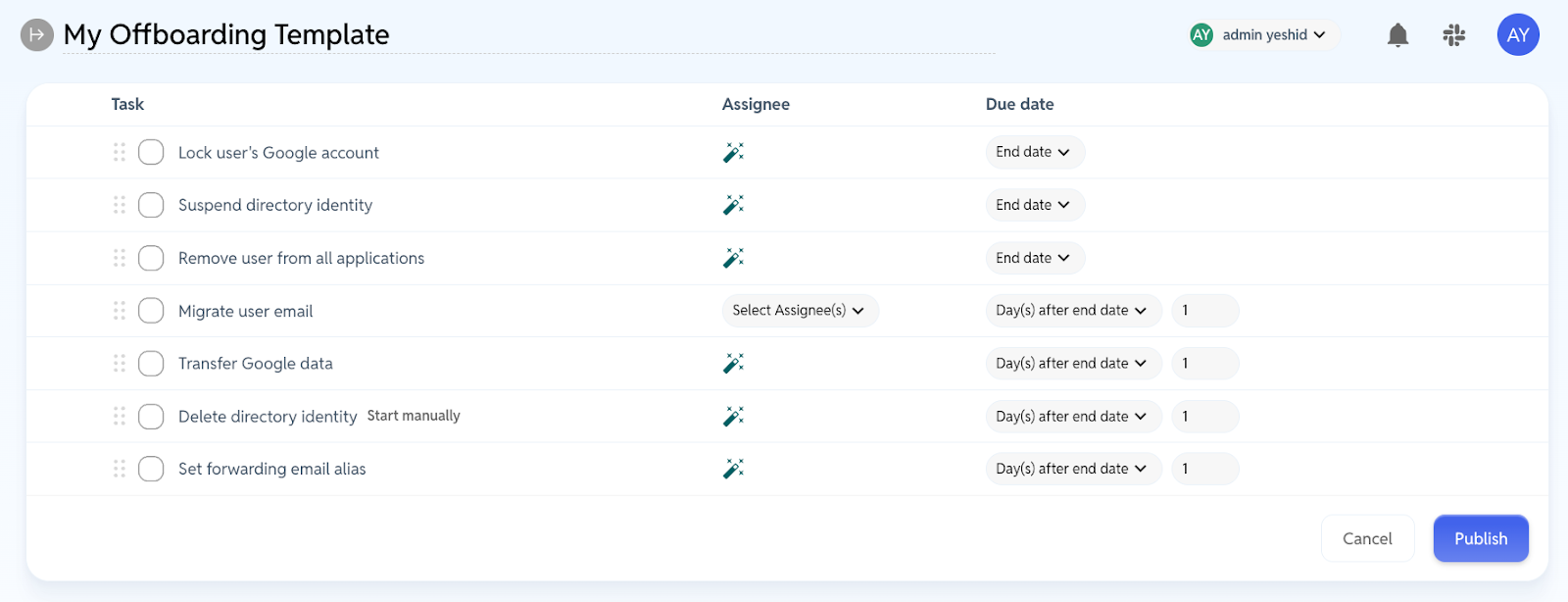
4. Create your offboarding template (30 seconds)
Use ours or customize your own. Either way, you now have a standard, repeatable way to lock things down when someone leaves.
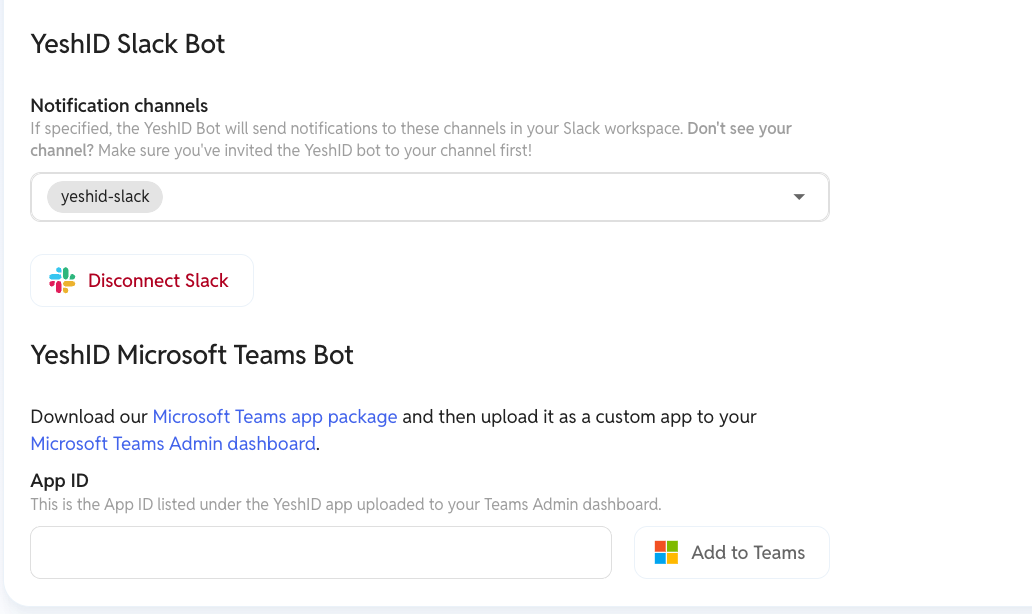
5. Install the Slack (or Teams) app (1 min)
Employees can now request access the right way, every time.
It’s auditable, consistent, and—yes—compliant (hello, SOC 2 and ISO 27001).
Congratulations, you now have:
✅ All your apps in one place
✅ A consistent onboarding & offboarding process
✅ Logging and visibility
✅ A real access request system (no more “Hey can I get access to X?” in Slack)
This is the foundation. It’s what gets you secure—and keeps your auditors happy.
What About All the Existing Access?
Ah, the fun part: figuring out who already has access to what.
YeshID helps you speed that up too:
- API support? Use our AI-powered integrator to pull in live access lists.
- No API? Upload CSVs—we’ll parse and standardize them with our LLM tools.
- No time? Delegate to the app owner. They can manually confirm who should have access.
TL;DR
Don’t wait six months to get value. In five minutes, you can go from zero to secure:
- Connect your directory
- Upload your app list
- Build repeatable workflows
- Add access request flows
- Start running your org like a real security team
Automation is a journey. But orchestration? That starts today. Try YeshID free → and stop duct-taping your identity process together.
