Passkey User Experience: Two Steps Forward, One Step Back

At YeshID, we are obsessed with making identity and Access Management (IAM) as simple as possible. One of the technologies we're using is Passkey, built on WebAuthN. Passkey promises to replace passwords and simplify password management without requiring additional software.If you are tired of passwords and have been looking for ways to improve security without sacrificing user experience or increasing support tickets, then you've probably heard of Passkeys. And if you’re like most people, you don’t quite understand Passkeys.In this post, we will explore the current state of Passkey and what it means for security.
A passkey conversation
Passkeys, AKA WebAuthN, is an initiative to get rid of passwords…
- I know you already have a password manager. Passkeys is not a password manager.
- Yes, I know your device suggests strong passwords and saves them, but this is different. Even the server doesn’t have your password, so even if it’s hacked…!
- How do you log in? Uh, you use your device. You can use a fingerprint, FaceID, PIN… or password. It’s easy! As long as you’re using Apple and nothing else… But it will get better someday!
- Where are they saved? Well, Passkeys are saved on your, uh, Passkey wallet. Like iCloud Keychain. Yes, that’s where passwords are saved too, but… It’s not a password manager.
- Not using Apple or mixing? No problem! Chrome… Well, Windows 11… Uh. They don’t sync Passkeys, so you can't use them on other devices yet.
- Yes, I know your passwords are synced across devices and clients, but listen!--
- Lost your device? Well, as I said if it’s Windows, Android, or ChromeOS… Eh. But, hey, if it’s Apple, you can get it back! You just have to use your [sigh] password.
- Did I mention that Apple, Google, Microsoft, and many others support it? Where are you going?? Come back…
Ok, so that didn’t go too well. Let’s try again.
Passwords are bad
Passwords are bad. We all know that. They are weak and guessable; we often reuse them; we get tricked into giving them away; servers can be hacked to expose them. This puts a strain on users and developers.As a Netizen, you were probably told to keep good password hygiene. Create strong passwords, keep them unique, change them every six months, don’t write them down, don’t get malware, and don’t forget to floss.Don’t worry. You are not alone. I don’t know anybody who follows those rules. So, security engineers tried to outsmart human nature with innovation:
- Multi-Factor Authentication (MFA). To overcome passwords being static and reused, engineers added a dynamic password. The most common type of MFA is a one-time password sent via SMS. This gives you Yet Another Reason to never let your phone out of sight. One-Time Passwords (OTP) provide some security against weak passwords–assuming you didn’t reuse it somewhere else without OTP, you weren’t socially engineered to enter that OTP somewhere you shouldn’t and you didn’t forget to floss.
- Sign in with Google/Apple/Facebook. When MyFittnessPal was hacked (I swear, I’ll log my meal tomorrow!) hackers gained access to 150 million cleartext passwords (and my macros!) Hackers quickly tested these passwords against other websites - Gmail, Facebook, LinkedIn, and your employer. We love reusing passwords! To partly close the barn door after the horse left, MyFittnessPal added login with Facebook. Less friction for users and fewer secrets for MFP to hold. Plus, fewer passwords to remember!Sign in with Google/Apple/Facebook is great. Until it isn’t; it isn’t portable and you don’t control it. If whoever you used has a problem with you and blocks you, then everything you are associated with gets blocked, too.
- Password managers. Vendors like Apple, Google, and Microsoft started to embed password management in their products. That accelerated adoption and increased stickiness on the identity frontier. Password manager usage has increased as users got tired of frequent password change policies (and run place to put the sticky notes with cryptic text.) Password managers are great at reducing password reuse but enforcing their use is nearly impossible.
So, passwords are bad, and we've come up with many (more than I listed) ways to overcome their limitations. But, each solution adds its own friction and complexity. And they often are layered on each other, which worsens things.So tech giants Apple, Google, and Microsoft teamed up to yesh an alternative into existence with the promise of better user experience and security. This is Passkey.
Passkey is…
Passkey's mission is simple: replace passwords. Make it impossible to social-engineer the user. Get rid of 2FA OTP. Improve user experience.Here’s the elevator pitch for Passkey:
- During registration, an agent on your device generates a public/private key pair and sends the public key to the server.
- During login, the server sends a challenge to confirm the holder of the private key. The agent on your device confirms the sender (origin) to prevent Phishing and signs the challenge using the private key.
- During both registration and login, the server can ask for user verification. This should trigger the device unlock flow, such as FaceID or fingerprint.
- The public key that was sent to the server does not require special protection. It’s public. The private key is protected by the agent that generated it.
Passkey UXApple introduced Passkeys in recent iOS and macOS releases, and it works very well.
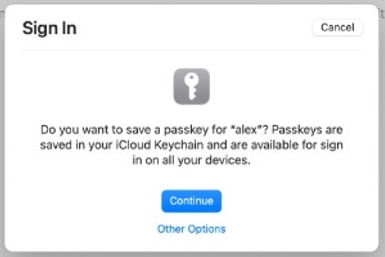
You just press “Continue,” and that’s it.1-click registration and login.If the server needs user-verification then two steps: the continue click put a verification action–click, touch, show your face.Apple syncs the Passkey across all your iCloud devices for a seamless experience.It works the same across all Apple devices, as long as you’re one of the few people using Safari, and not Chrome or Firefox, etc. on macOS. iOS is more consistent: it works on both the default Safari and Chrome for iOS.Google also announced Passkey support, but here things get a bit… Spaghetti Monster.If you’re on Android it takes four steps. Google doesn’t sync it on your Chrome browser so you must always use your phone. Scanning a QRCode with your phone adds more steps and complicates the user experience.(If you watch Google’s Passkey introduction video and go to 12:18 in the video, you will see a popup instructing the user to scan a QRCode. Google edited the video to remove the actual Chrome popup to make it seem easier than it actually is.)
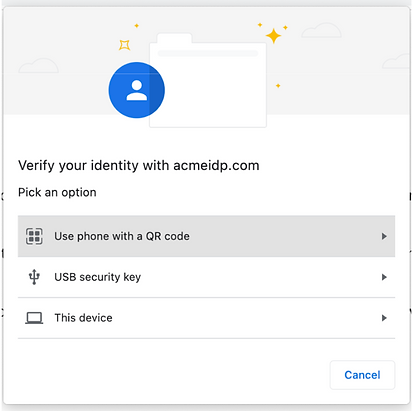
And only if the user chooses the first option (another click), the QRCode is shown:
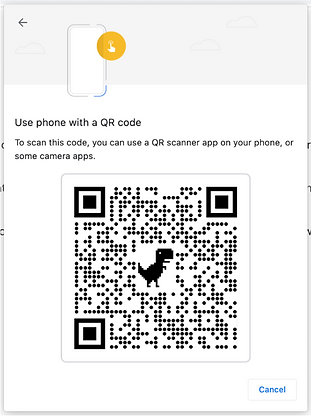
And if that’s not bad enough, I now need to scan the QR code, and I only need 2 more clicks on my phone before I can finally login. Scanning QR codes takes time - not only to do the actual scan but also for the devices to sync. That too was cut from the video. This is significant friction when using a computer.What about identity management? For example, I’d like to be able to have multiple accounts on a given website.Passkey does allow different types of usernames, but the current UX makes it difficult for users to remember which usernames were used where.
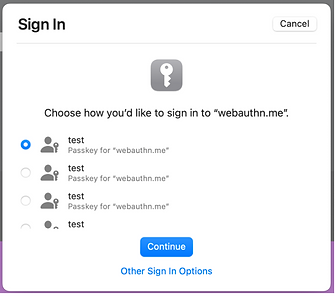
Lastly, users should be able to manage their Passkeys. Currently, only Apple allows managing Passkeys, and even that is buggy – for example, it doesn’t display all the Passkeys created. Chrome (or Microsoft’s Edge) is currently missing this functionality altogether.
So, if you want to experience most of the benefits Passkey has to offer, you are currently better off using Apple ecosystem. You get 1-click registration and login, cross-device sync, and basic management. The rest will have to wait for Chrome’s planned improvements.Passkey is in the early stages. We at YeshID are early adopters and we’re doing our part to make the experience as smooth and secure as possible for both users and IT.Stay tuned for more posts as we continue the journey as we explore Passkey for Employees vs. Consumers, the impact on IT and Security departments, and better flossing techniques.
