IT Department of One

WHOOMP There IT is 2

POV: You're an IT Department of One on a Friday Evening 2

What if you could automate your onboarding and offboarding? 2

Access Request Massage Therapy 2

What if you could automate your onboarding and offboarding?

Access Request Massage Therapy

WHOOMP There IT is

POV: You're an IT Department of One on a Friday Evening
Product Demos
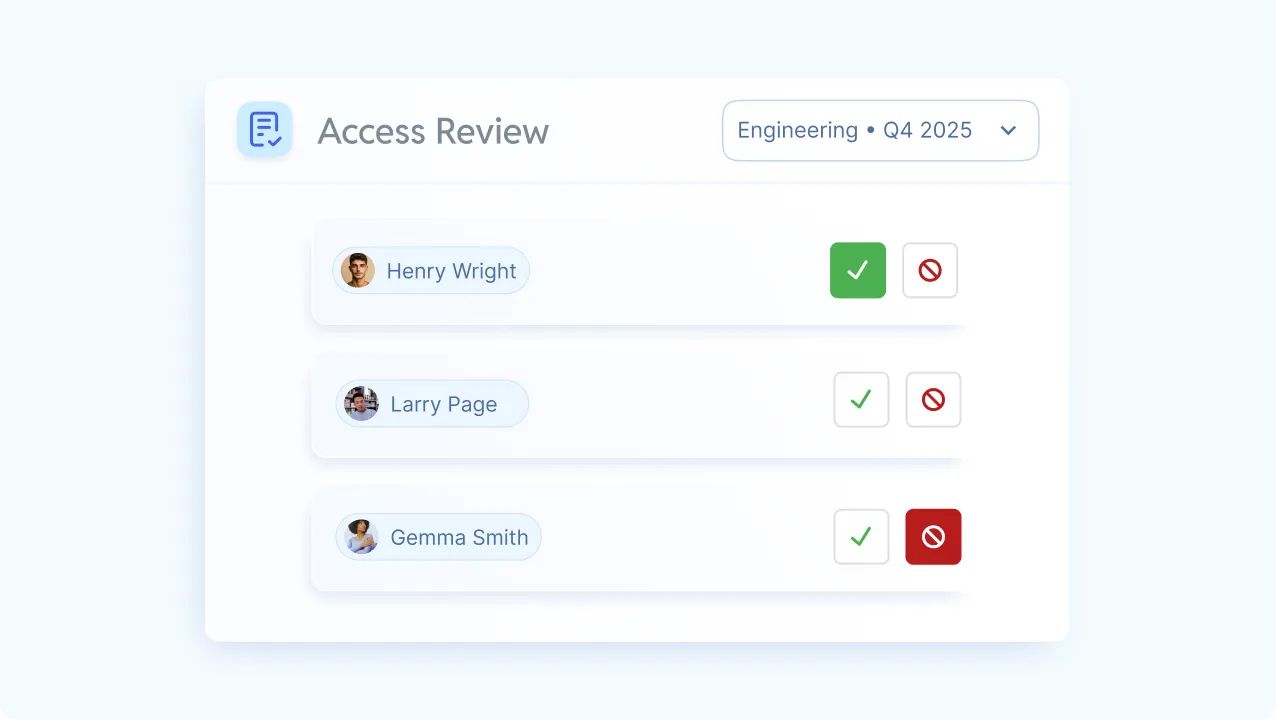
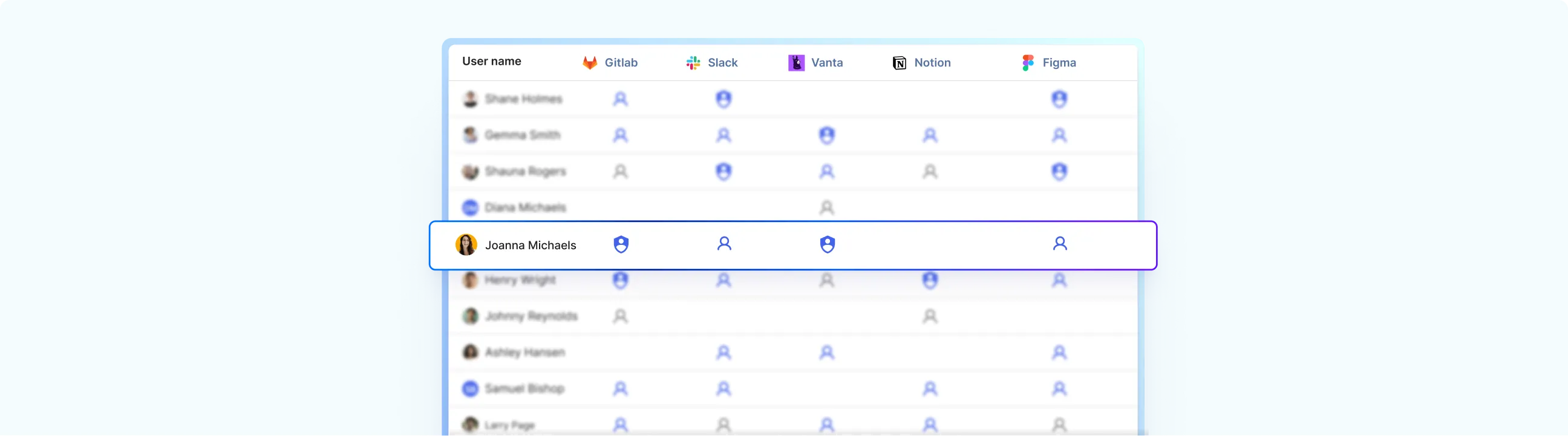
Structured Access Reviews

Structured access reviews
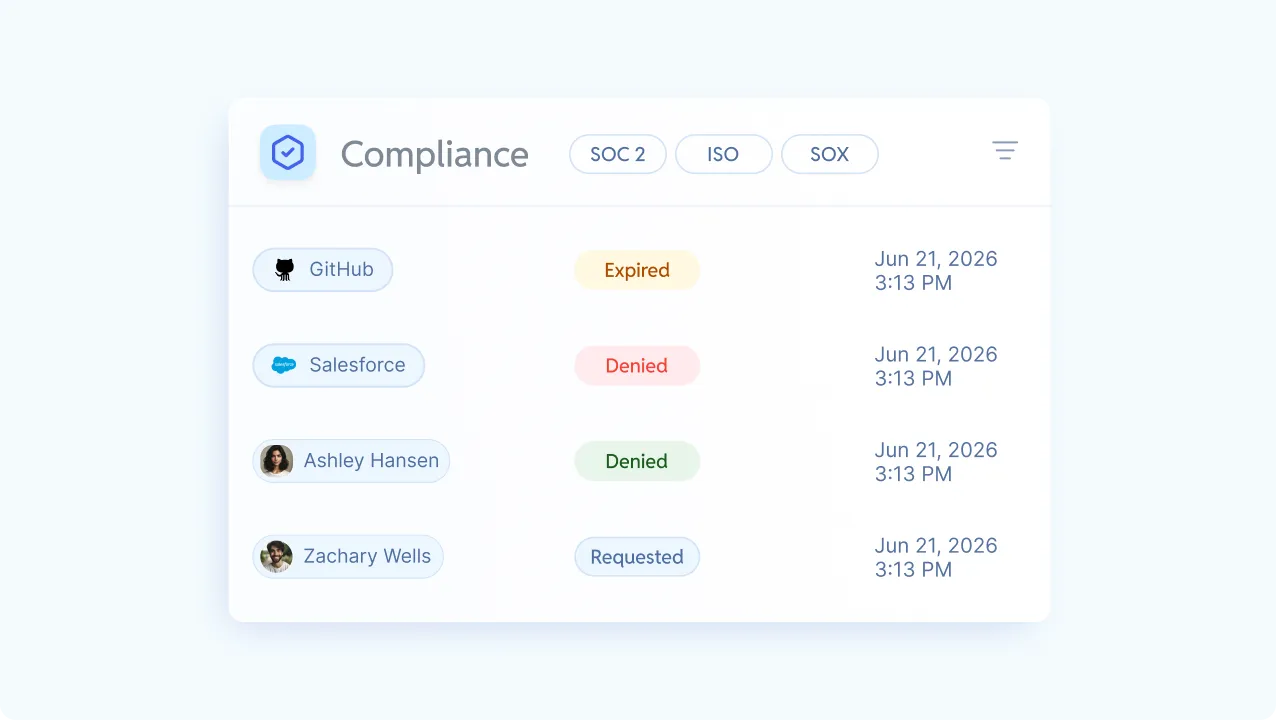
Audit-ready logs from day one
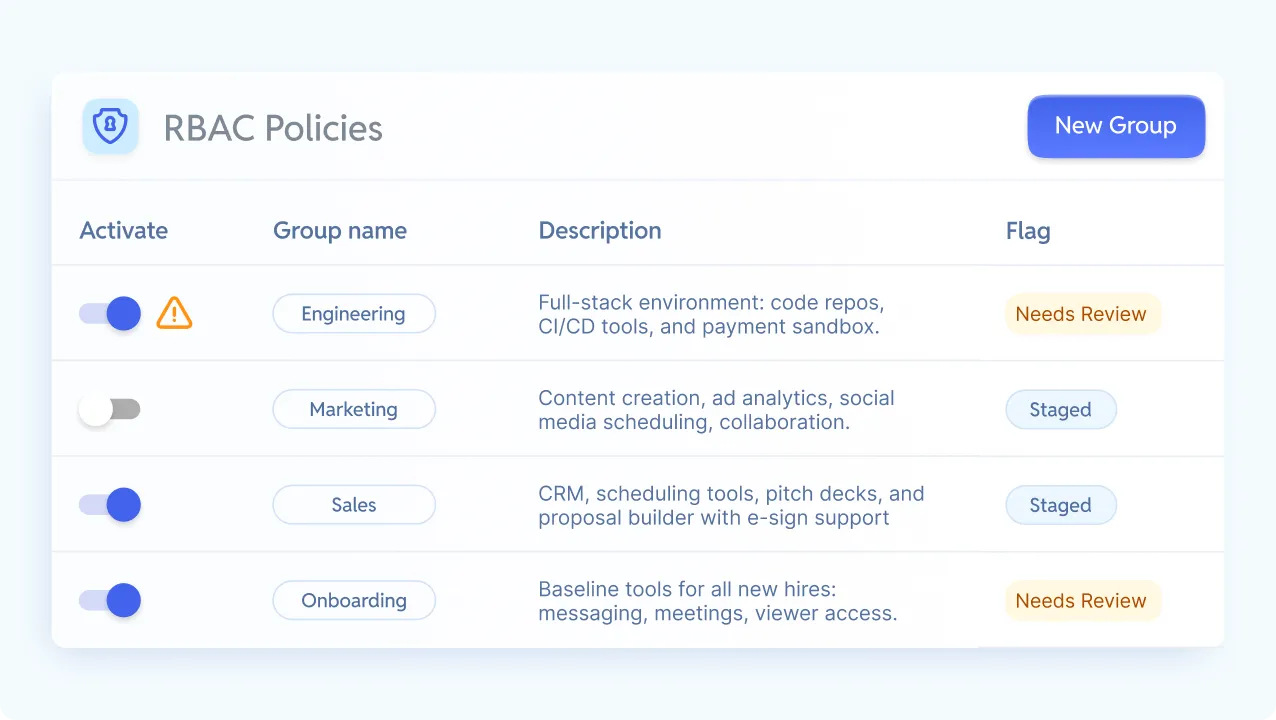
A practical, modern take on RBAC
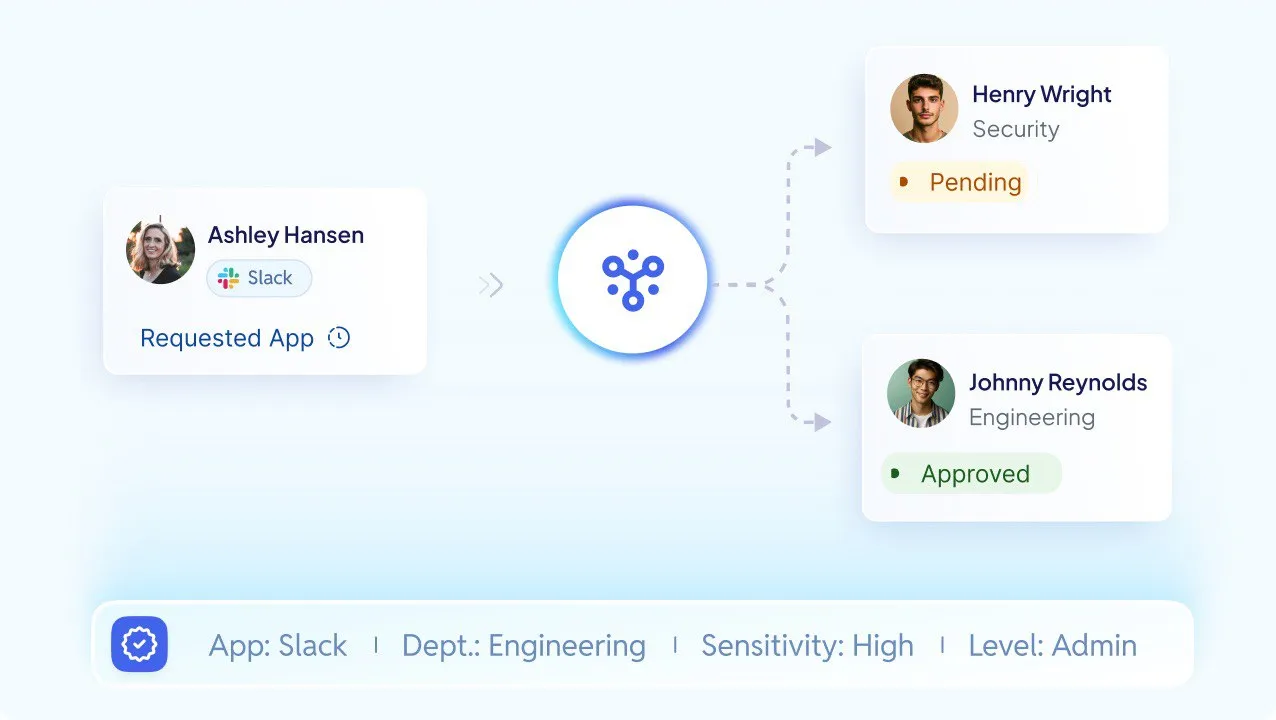
Rules enforced automatically
Full Identity and app inventory
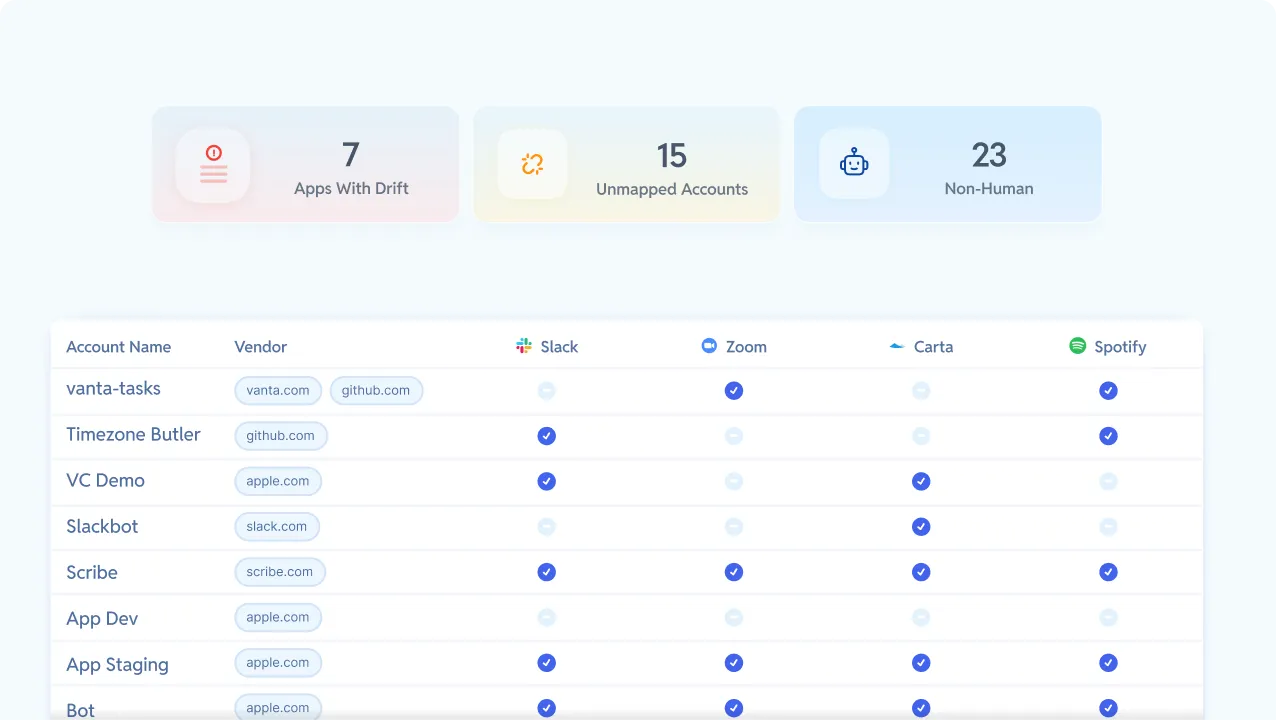
Drift and identity security report
ShadowIT and OAuth visibility

One login page for your users
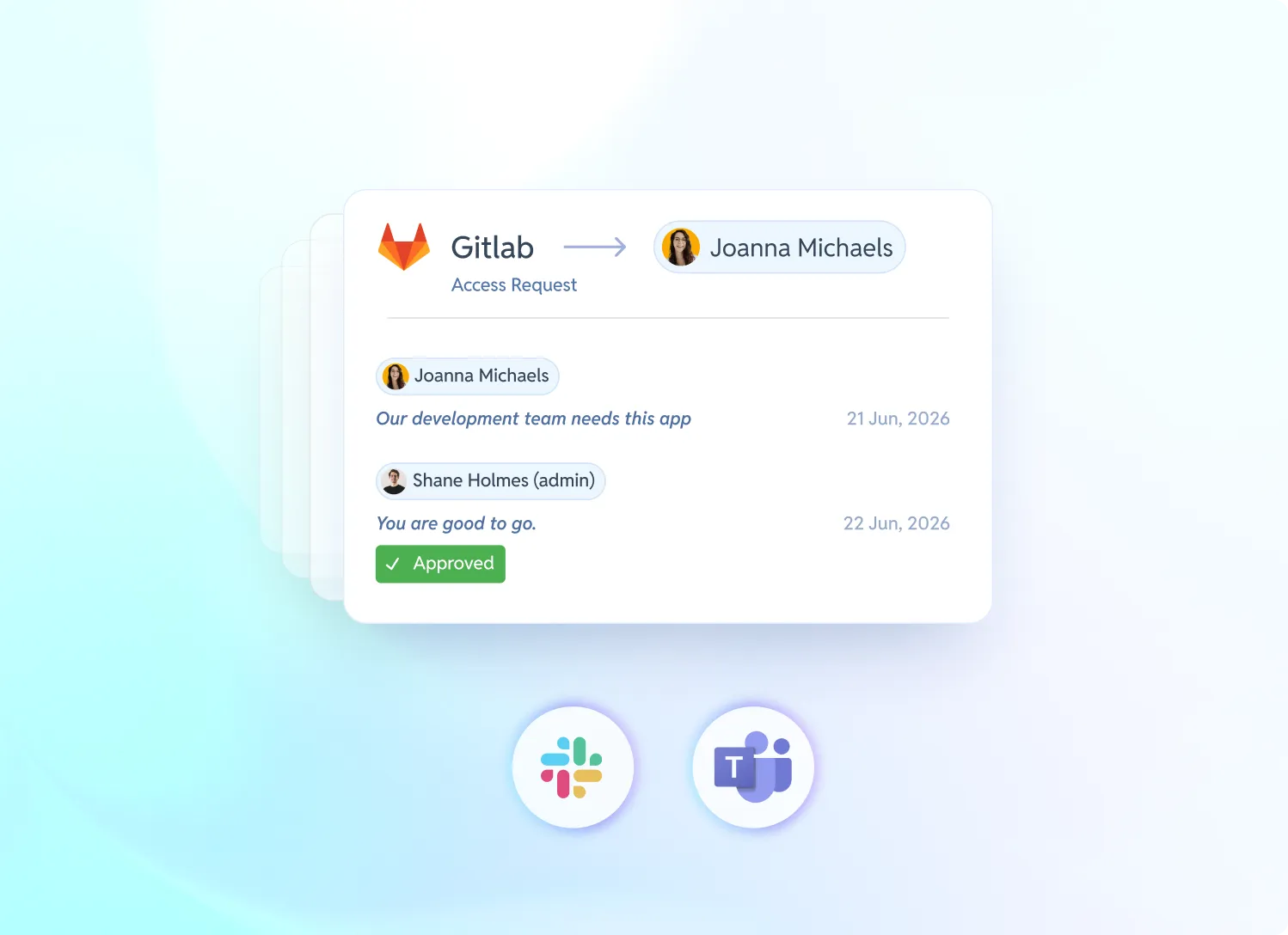
Access requests directly in slack or teams
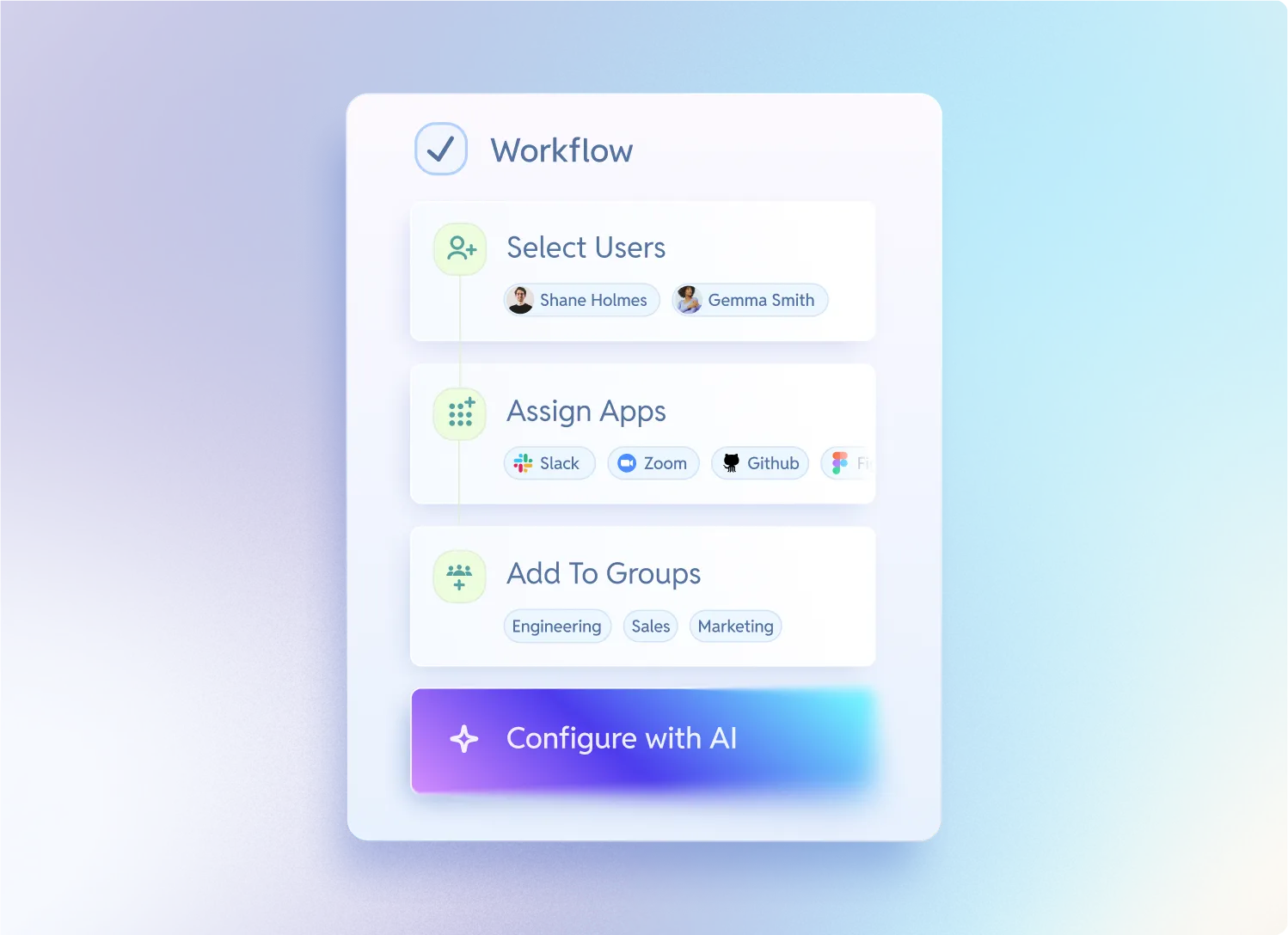
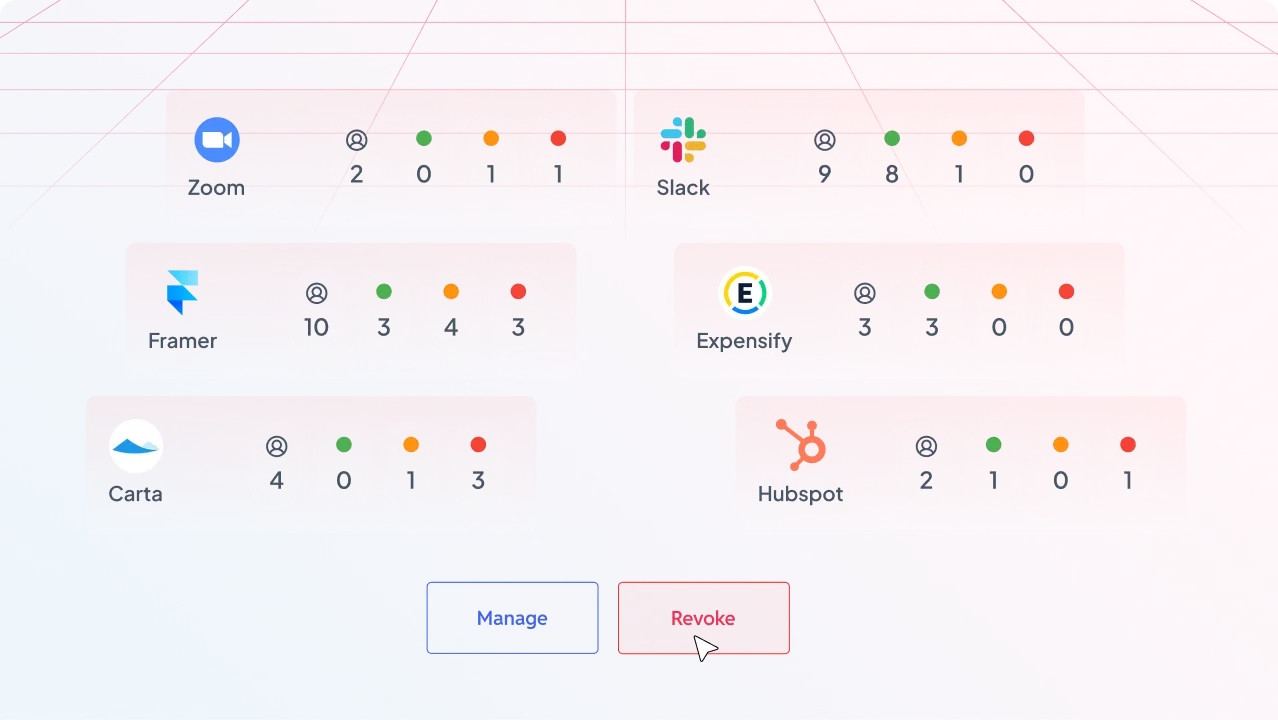
Provisioning across every app you use
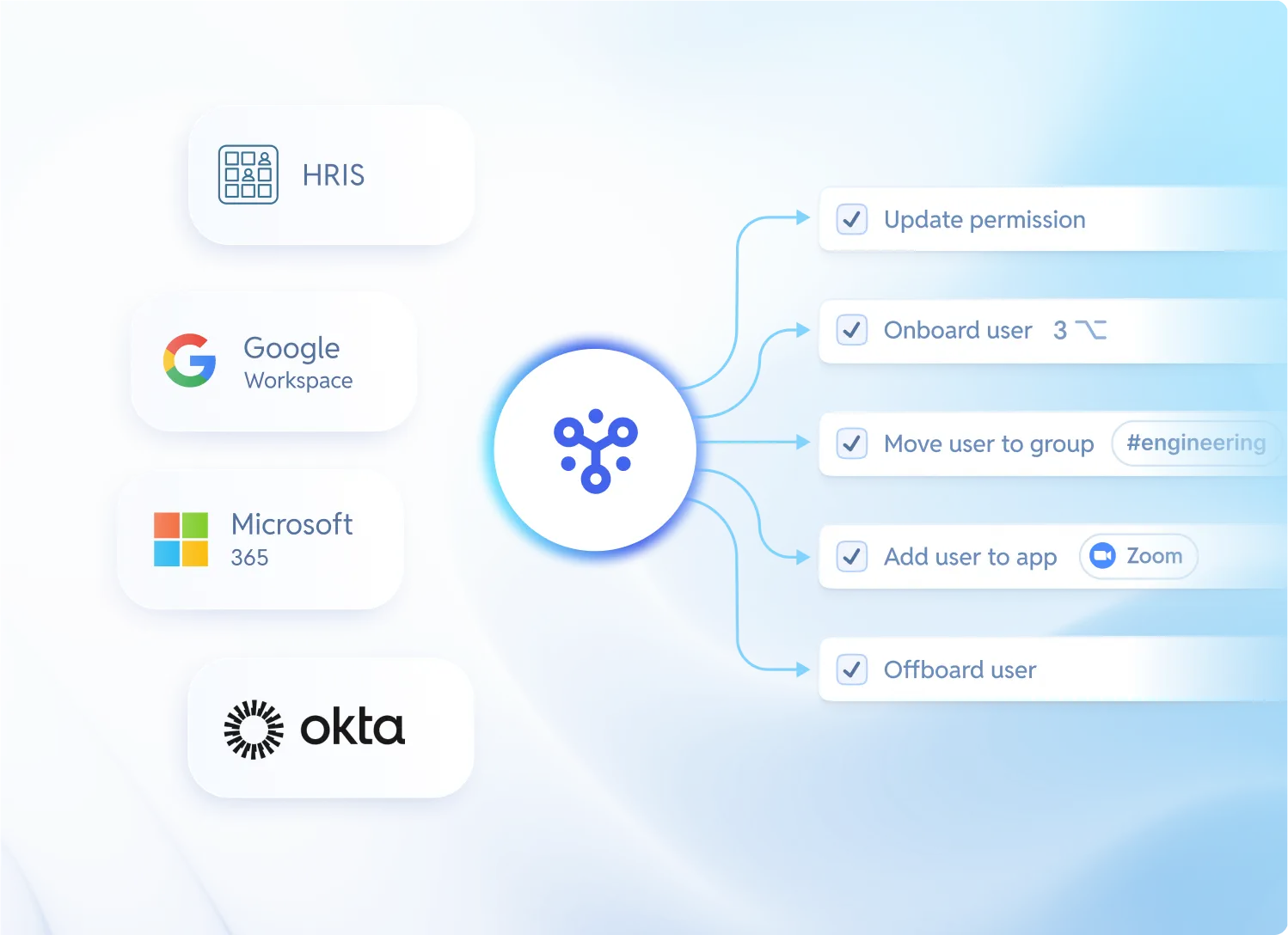
Automated from your actual source of truth(s)

Simple, easy-to-read workflows

Electric Toothbrush with Timer

Smartphone with Advanced Camera Features

Multi-Function Instant Pot

Fitness Tracker with Heart Rate Monitor

High-Performance Blender

Ergonomic Office Chair

Portable Solar Charger

Wireless Earbuds with Noise Cancellation

Smart Home Security System

Innovative Kitchen Gadget
Product Obligatory Blogs

What Makes IAM “AI-Native”? A Definition, Maturity Model, and Why Being the IdP Matters
AI-native IAM isn’t chatbots and ticket automation. It’s continuous access intelligence that can execute policy safely a

One Agent to Run IAM: Why Holistic Context Beats a Fleet of Siloed Bots
IAM teams don’t lack tools, they lack cohesion. Real AI requires one agent with end-to-end identity context across syste

Release Notes: Janurary 2026
Jan Release: Safer automation triggers, new Audit Admin role, and integrations for BambooHR, OpenAI & Zendesk.

IAM or SaaS Management First
IAM vs SaaS Management: why control and action should come before reporting and cost visibility as organizations scale.

RBAC Isn’t Dead: Meet ReBAC
IAM is shifting from roles to relationships as OAuth apps act on your behalf across docs, repos, and workspaces.

NIST Just Opened a Public RFI on Securing AI Agents
NIST Just Opened a Public RFI on Securing AI Agents. IAM Is the Highest‑Stakes Place to Get It Right.

Drift Happens. The Problem Is Everyone Pretends It Doesn’t
Drift is real. Most IAM hides it. YeshID surfaces, explains, and controls drift without breaking your business.
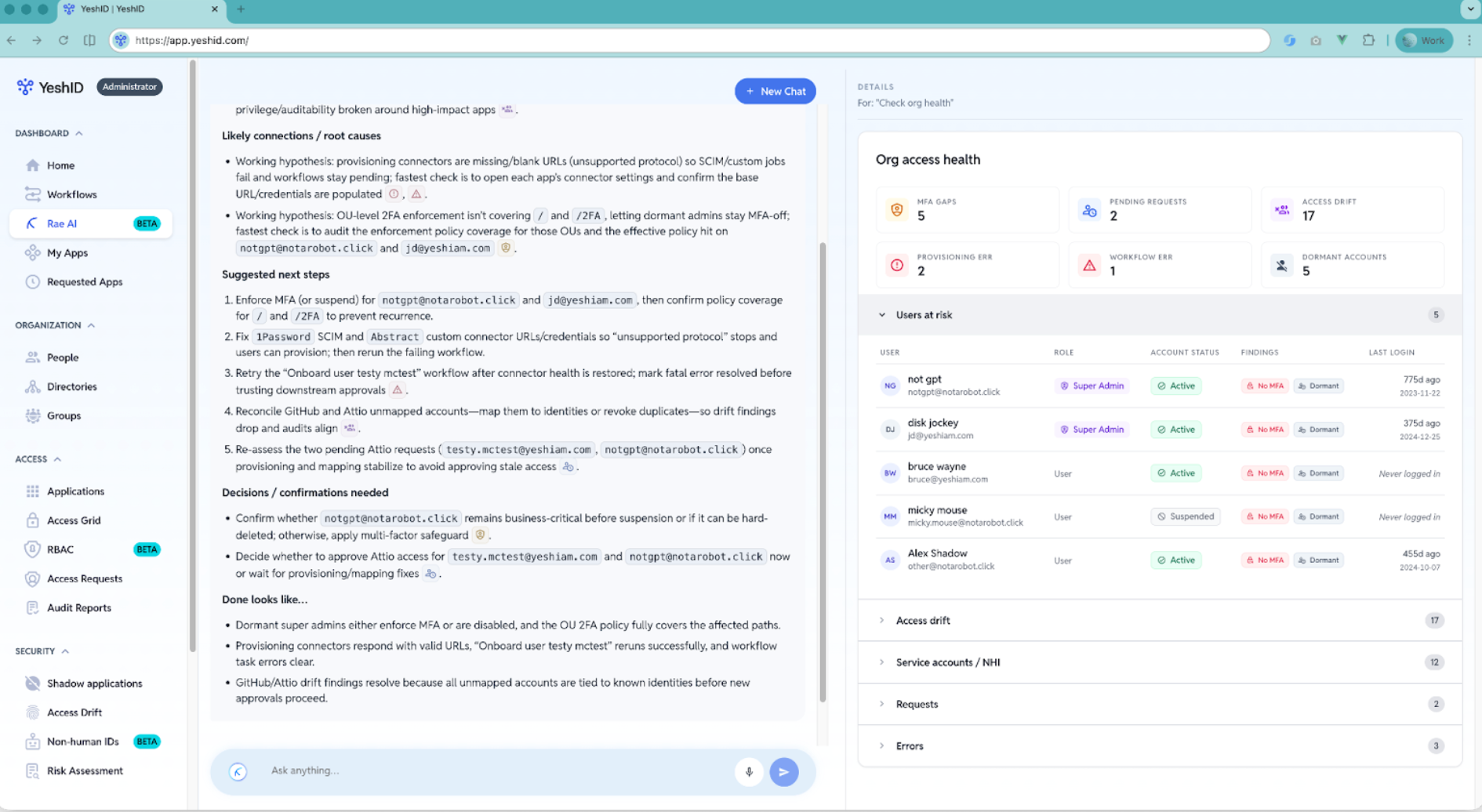
AI for IAM admins: stop bolting chat onto dashboards—build a real colleague
Why adding AI chat to IAM dashboards doesn’t fix the real problem—and what real AI leverage looks like.
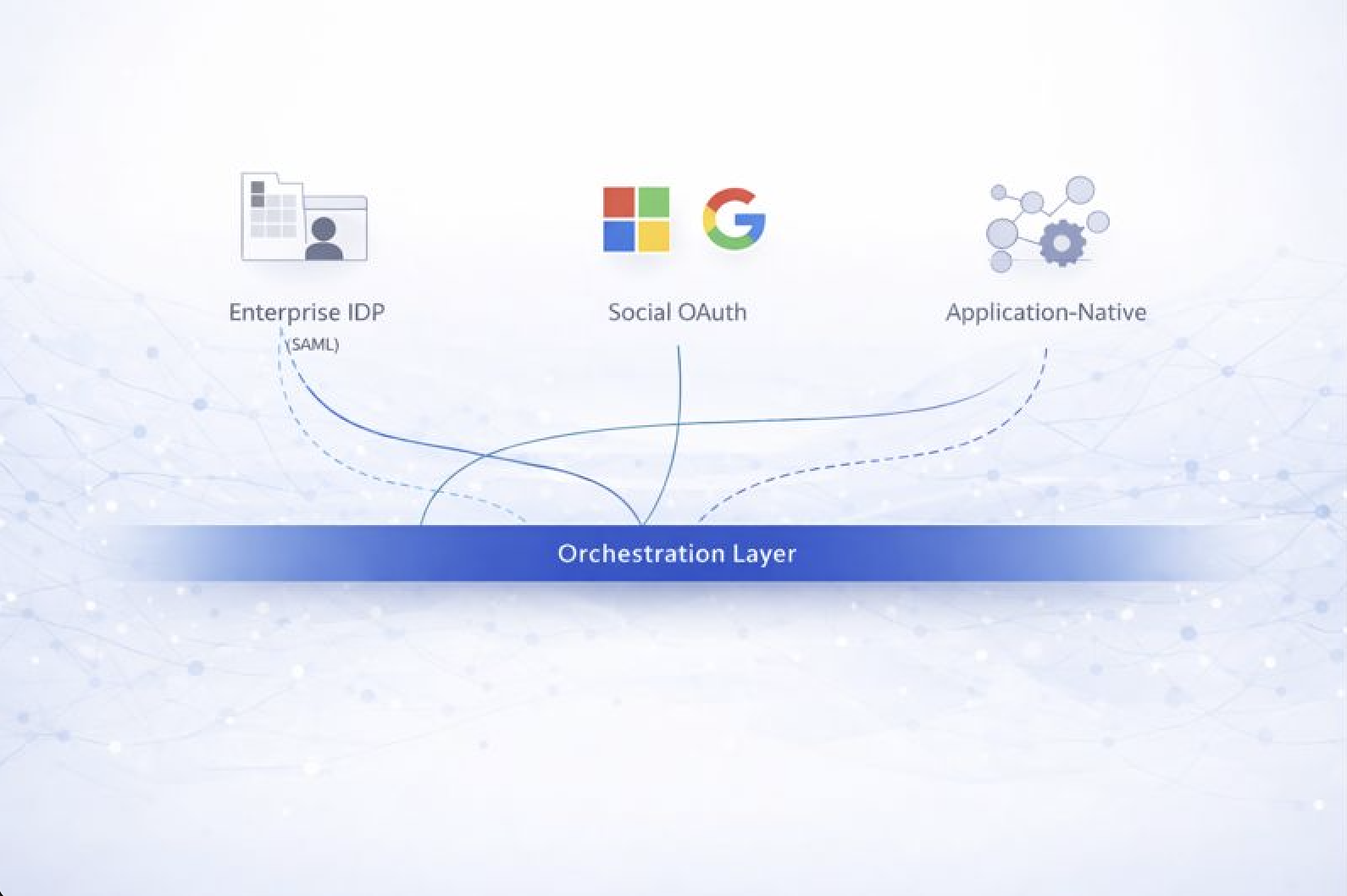
Identity Architecture for the Modern SaaS Stack
Modern identity is no longer one IDP. Learn how CTOs design across SAML, OAuth, apps, and governance layers.
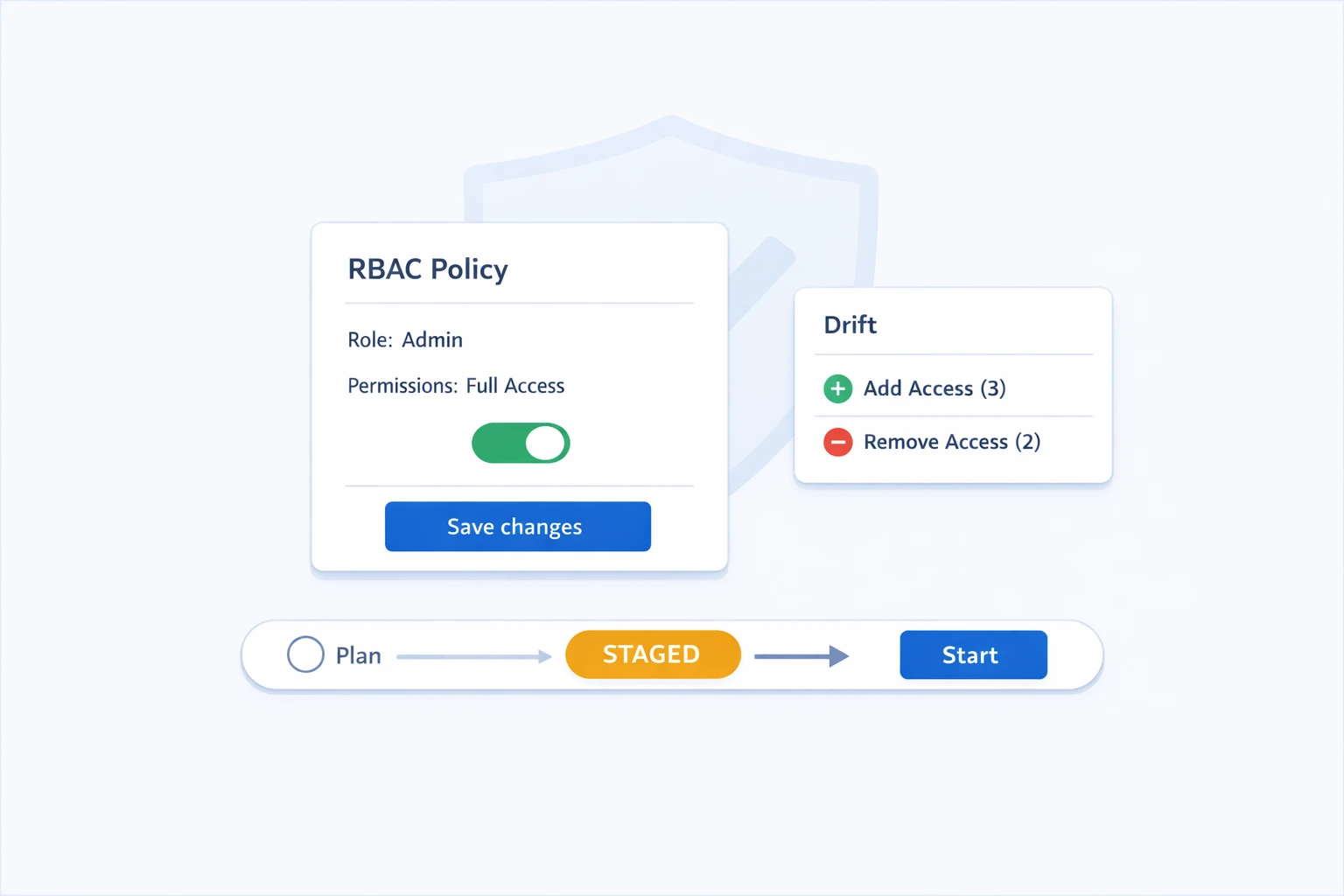
Release note December 2025
Review access changes before they run, fix drift faster, and automate with confidence.
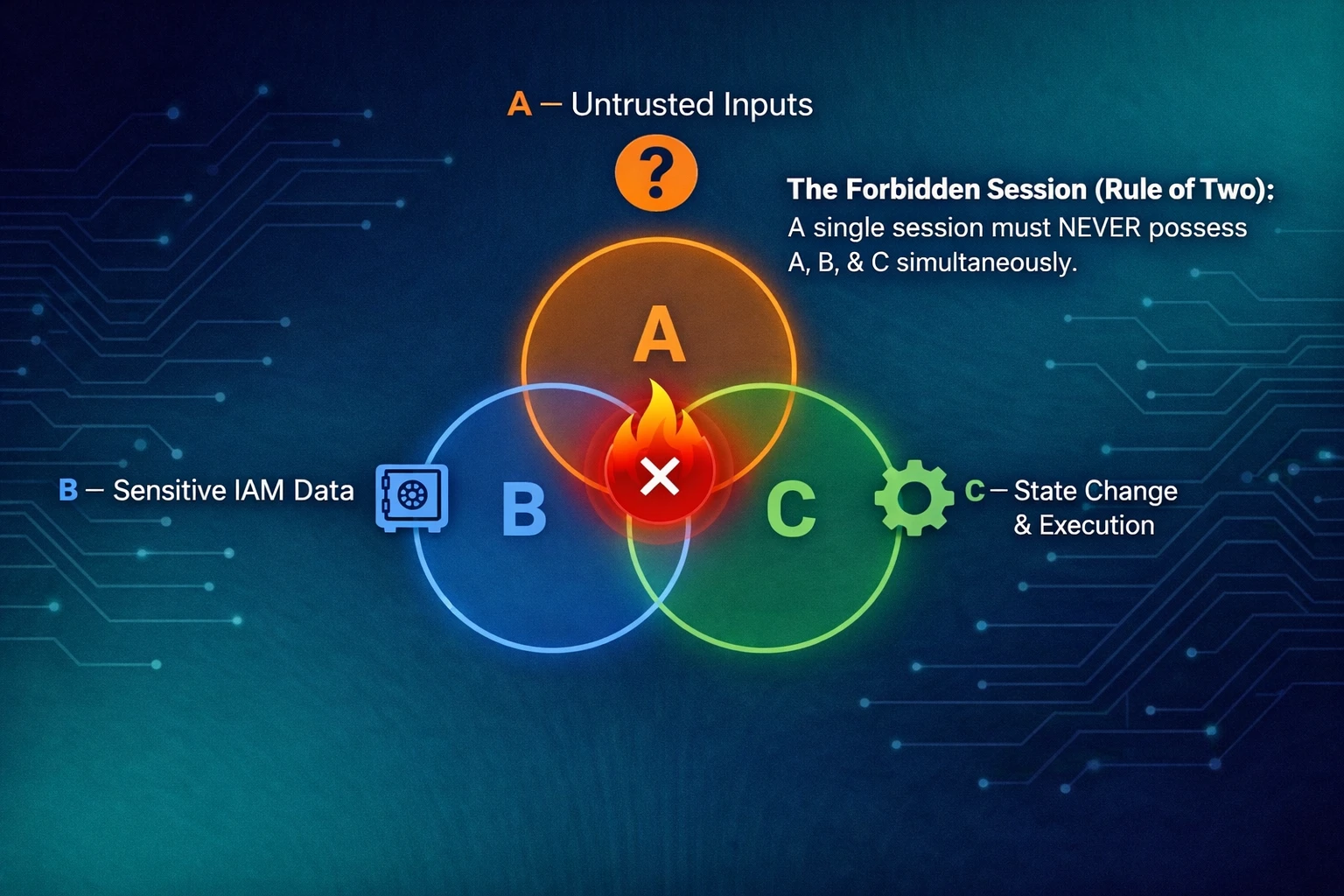
Agentic AI for IAM, Built for Trust
Why prompt injection makes generic AI unsafe for IAM—and how YeshID’s Rae automates access securely.
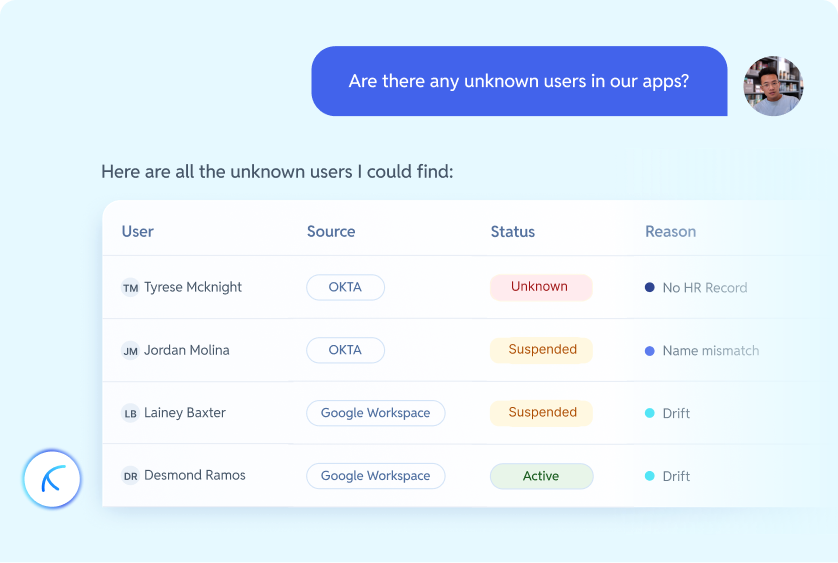
Introducing Rae: Agentic AI Built for Identity and Access Management
Agentic AI built for IAM to detect risk, explain access, and act safely across identities and apps.
The Truth: IDPs Only Govern the Apps They Touch (And That’s Not Enough)
Your IDP secures login, but it cannot govern your full stack. Modern identity needs security orchestration.

How to Talk to Your CFO About Identity & Access — A Practical Budget Script
A guide for talking to CFOs about identity and access using cost, control, efficiency, and ROI as the shared language.

Why People Hate Roles and Groups — And How We’re Doing It Differently
Legacy roles and groups create drift and chaos. YeshID rebuilds RBAC for constant change, visibility, and control.

November 2025 Release Notes
YeshID November 2025 updates: stronger group-based access control, clearer workflows, and smoother IAM integrations
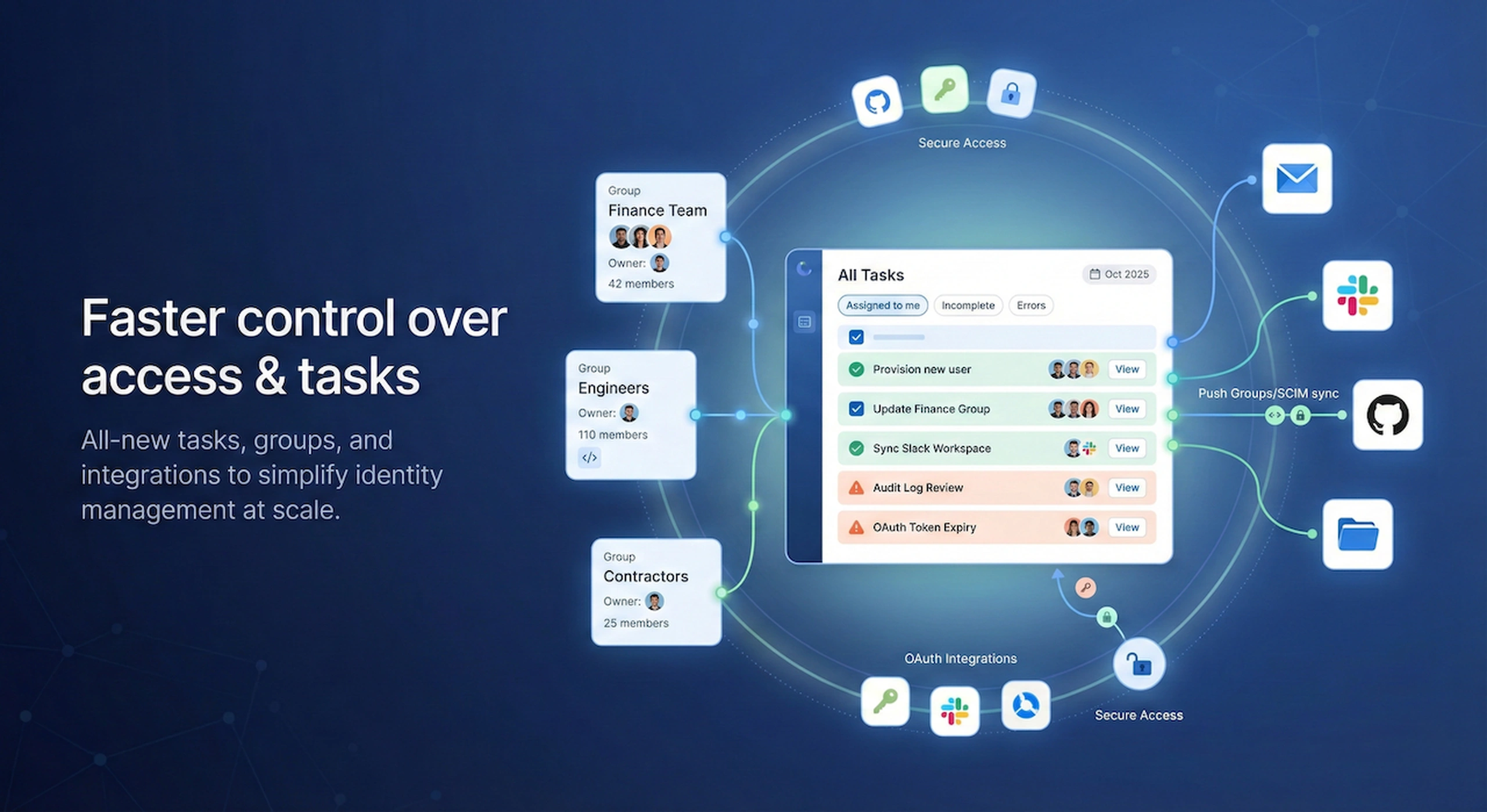
October 2025 Release note
New groups, task management, and integrations to simplify identity management in October 2025

Why ITSM Isn’t IAM, And Why AI Ticketing Tools Don’t Solve Access
Most AI ticketing tools automate requests, not identity. Access needs governance, not another workflow system.

Free Tool: Google Groups Should Not Be a Mystery
Instant, free Google Groups governance that spots real risks, fixes them fast, and runs fully client side.

Starting SOC 2 Without the Burnout: A Practical Guide for Lean Teams
Lean teams can start SOC 2 without burnout: scope small, use simple controls, operate them consistently, and show clear

Identity & Access Management: Stop Chasing Integrations. Start Orchestrating.
Integrations are the 20%. IAM Orchestration is the 80% — where process, security, and compliance actually come to life.

The Real Priorities of an Identity & Access Management Program
Visibility before control. Automate before auth. The real priorities of IAM go beyond locks—they start with logic.

Release Notes October 2025
App requests are clearer, workflows easier to manage, and SCIM provisioning more reliable in October 2025
Introducing Application Workflows: Real-World Automation for Real-World Apps
Automate real-world access changes — not just “add/remove.” YeshID’s Application Workflows handle every step.

The Modern Stack? Or Just the Messy Middle?
The “modern stack” isn’t sleek—it’s a messy middle of trial apps, shadow IT, and duct-taped workflows YeshID fixes.

The SaaS Discovery Buyer’s Guide: What’s Relevant, What’s Noise, and What’s Just Creepy
Not all SaaS discovery is equal: here’s what’s useful, what’s noise, what’s invasive—and where GDPR risk begins.

When the Business Bullies Security & IT (and Wins)
Business teams push AI apps fast—often at IT’s expense. Here’s how to secure the new stack without SSO tax baggage.

Death to the SSO Tax: Why Modern Identity Leaves SAML and SCIM Behind
Legacy SAML/SCIM slows SaaS teams with cost + complexity. YeshID delivers AI-native, no-SSO-tax identity.

YeshID product updates — August 2025
Release notes: August 2025

Scheduled Access — Even When the App Doesn’t Support It
YeshID’s Scheduled Access grants time-boxed privileges—even for manual apps—so nothing slips through the cracks.

Choosing the Right Identity & Access Management Approach for SMBs
IAM paths abound—IDP alone, with MDM, with IGA. YeshID blends them all, adding automation minus the SSO tax.
New in YeshID: HRIS + Triggers and Per-App Approvals
YeshID now supports HRIS + Triggers and per-app approvals—automate onboarding, offboarding, and app access your way.

July 2025: Release note
Why Identity & Access Is the First Project Every New IT Leader Should Tackle
IT team of one? YeshID helps you scale like ten—with AI workflows, real visibility, and no SSO tax.

From Zero to Secure in 5 Minutes: The Fastest Way to Deploy YeshID
Most companies chase full automation—but it’s a myth. With YeshID, you can orchestrate security in just 5 minutes.
Streamlining Identity & Access Management for Dunder Mifflin

How Quivo Cut Onboarding Time in Half (and Stopped Compromising on Security)
A distributed IT team. Dozens of manual steps. YeshID helped Quivo automate onboarding and offboarding internationally.

The Cost of Doing Nothing: Why Manual Access Management Is Risky, Wasteful, and Slowing You Down
Manual access management wastes time, money, and security. Doing nothing is the most expensive choice.

Why Use YeshID Before Migrating Domains
Migrating domains is a high-risk moment for identity and access. It's the perfect time to lay the right foundation, not

Why Modern Schools Need Vsibility, Control, and Simplicity Around IAM
Today’s schools rely on a growing number of apps—email, HR platforms, learning tools, admin systems—all of which require

Review by Role: A Smarter Way to Run Access Reviews
Review by Role: a smarter, cleaner way to manage access reviews in YeshID.

Avoid the SSO Tax: What It Is, Why It’s Dumb, and How We Fixed It
We’ve upgraded ssotax.yeshid.com to make it easier to understand and automate how your team connects to any app.
.png)
June 2025 Highlights at YeshID: Faster Audits, Easier Onboarding, Seamless Integrations
Learn about the features we delivered in June

May 2025 Product Highlights – Easier, Smarter, and More Collaborative IAM!
Learn about the features we delivered in May!
.png)
What I Didn’t Know About MFA—And Why You Don't Need SSO for Compliance

Microsoft 365 Support Is Here - and other product updates!

Why YeshID is Better Than OKTA Workflows
Why YeshID + Okta is the smarter identity stack: faster workflows, broader coverage, and AI-native automation.

Doing More with Less (and 364 SaaS Apps)
“Do more with less” is now the default setting for modern IT teams. The average org is juggling 200 to 400 SaaS apps.

Release Notes: Smarter Workflows, Faster Performance, and Enhanced Security
Boost productivity with AI-driven tasklists, faster workflows, and stronger security in our latest product update! 🚀

Introducing the "SSO Automation Scorecard"
We created a new website that shows you what you can automate for about 200 SaaS apps.
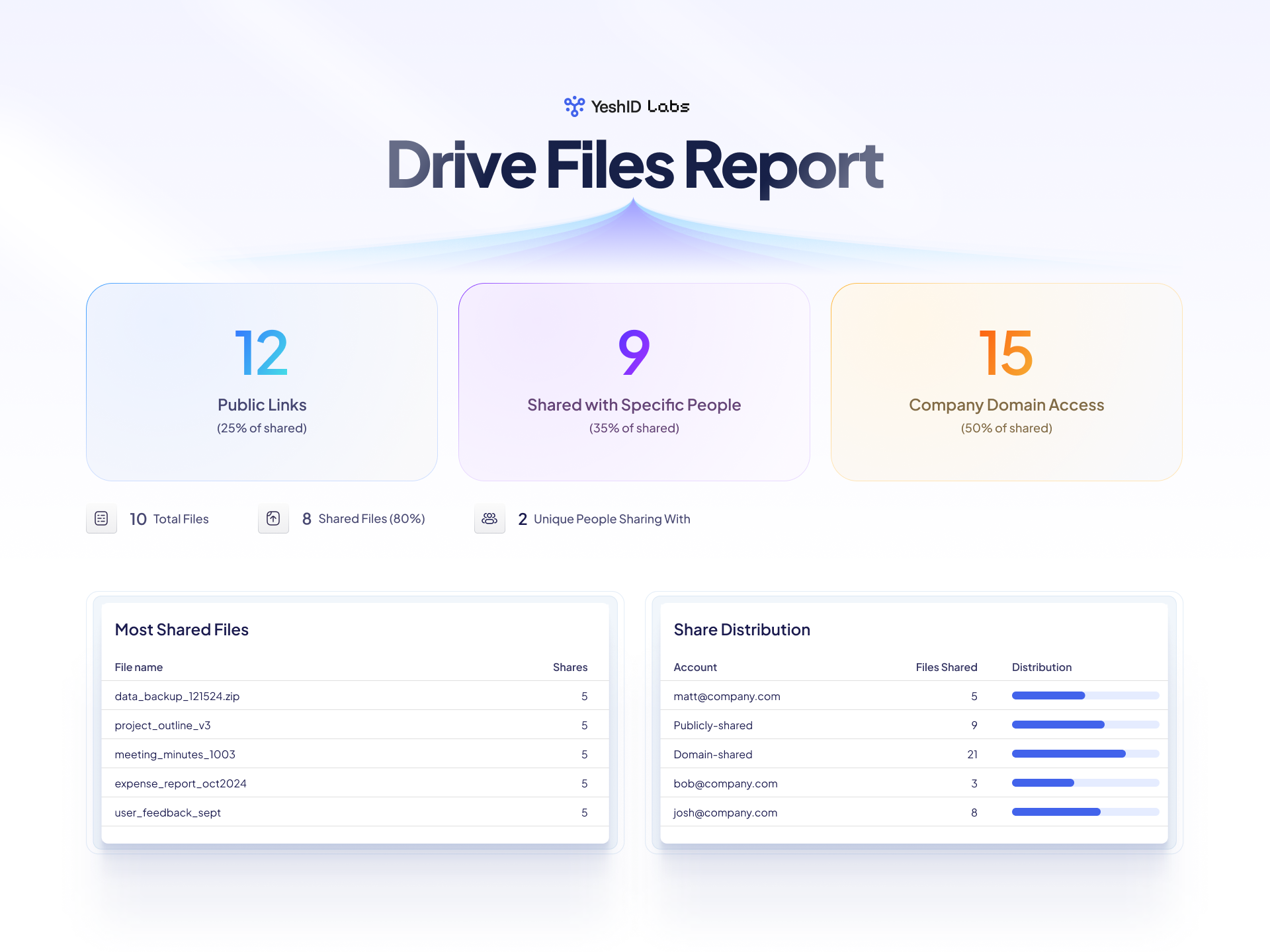
How to Prevent Uncontrolled Google Drive Sharing and Protect Your Sensitive Data
How to Stop Uncontrolled Google Drive Sharing & Secure Your Data

YeshID Monthly Release Notes: December 2024
Enhancements to directory management, incident response, and a new Drive Report (labs) in YeshID's December release

Why We Built the Demo Center: Transparency Over Tradition
Skip the gimmicks, cut through the noise, and let our product speak for itself. Introducing our Demo Center.
.png)
FREE Shadow IT Assessment tool
YeshID offers a free tool to scan your Google Workspace for OAuth Shadow IT.

Free Google Workspace Risk Assessment Tool
Compare your settings against CIS Benchmarks and get expert guidance to strengthen your organization's security posture.
.webp)
YeshID Monthly Release Notes: November 2024
Explore our latest updates: Okta integration, custom app integrations, task UI improvements, and key fixes!

Tired of Manual User List Headaches? Try AppSync
We've heard your frustration: manually extracting user lists from various applications is difficult. Enter AppSync.

YeshID SOC2 Type 2, Round 2
YeshID just completed our second SOC2 audit, covering a full year this round!

Google Workspace: Organize Org Units, Groups, Policies, Devices, and more!
Effectively manage your Google Workspace organization and SaaS applications using Organizational Units, Groups, and RBAC

How to Meet SOC 2 Access Review Requirements - A Startup's Toolkit
Struggling with SOC 2 access management? YeshID simplifies the process for small teams.

YeshID Monthly Release Notes: October 2024
Check out YeshID's October update! New billing system, easier org creation, UI improvements, and better directory manage

Introducing Access Review: Simplify your compliance journey
Access Review is designed to streamline your access management and compliance processes.

🚀 YeshID Monthly Release Notes: : September 2024
This release brings improved audit tracking, real-time sync progress, enhanced user management, and performance boosts.

Balancing SaaS Tools with Security through an Employee Growth Spurt
Chris Hubbard faced significant challenges managing a growing number of SaaS applications across the organization.

YeshID: Free for Small Businesses
YeshID offers free cybersecurity tools for small businesses to protect sensitive data and comply with regulations.

🚀 YeshID Monthly Release Notes: August 2024
Security boosts, task management upgrades, streamlined user imports, and smoother app handling for a stable system.

Manage application access without ever leaving Slack
Request app access directly in Slack with YeshID: streamline workflows, enhance security, and simplify compliance.

🚀 YeshID Monthly Release Notes: July 2024
New YeshID updates: Slack integration, custom fields, improved task management, and performance optimizations.

Got an HRIS? You can streamline your Onboarding Flow with YeshID
We’ve designed YeshID to orchestrate an organization’s onboarding processes.

Access Management Made Easy
Simplify access management with YeshID: automate requests, approvals, and audits, freeing admins and empowering users.

Upgrade your Checklist to a YeshList: Identity & access management done right
YeshID is replacing manual IAM checklists with smart YeshLists, automating tasks for seamless onboarding and offboarding

Simplify SOC 2 Compliance with YeshID
Simplify SOC 2 compliance with YeshID: streamline access management, ensure security, and maintain compliance effortless

Release Notes for May 2024: New Features, Enhancements and Fixes
YeshID May 2024 Update: New AI features, user ledger, improved offboarding, temporary employee support, and more.

The AI Revolution Comes to IAM: Introducing YeshAI
YeshID AI: Simplify SOC2 onboarding/offboarding, save time, reduce risk, and ensure compliance effortlessly.

Centralized IAM Playbooks: The Key to Solving SaaS App Access Management Chaos
Centralize IAM with YeshID: streamline access management, ensure security, and simplify compliance across all SaaS apps.

The Identity Management Struggle: Overpromised, Underdelivered, and How to Fix It
YeshID simplifies IAM with smart YeshLists, automating tasks, enhancing security, and ensuring compliance. Try it free!

Streamlining Employee Management with YeshID
YeshID centralizes and simplifies onboarding/offboarding, integrating HR and IT tools for efficient IAM management.

Easier & more secure employee offboarding for small businesses with YeshID
Offboarding with YeshID: Easily suspend or delete users, reassign data, and deprovision access, ensuring security.

Buyers Remorse in Identity and Access Management: There's no silver bullet
YeshID: Centralize IAM, organize tasks, integrate processes, and avoid automation chaos. Get started for free today.

3 reasons to ditch the access management spreadsheet for YeshID Access Grid
Ditch spreadsheets for Access Grid in YeshID: automate workflows, save time, and enhance security

OAuth oh oh!
Google OAuth flaw lets ex-employees access apps. YeshID is safe. Detect "+" emails, disable domain logins, or use SAML.

IT Efficiency Through Playbooks
YeshID: Centralize IAM, streamline onboarding, audits, and offboarding. Get started for free today.

Navigating the OAuth maze in SMB identity management
YeshID simplifies OAuth management, highlighting app permissions and risks. Ensure security and streamline identity...

Release Notes for January 25, 2024
YeshID 2024 update: Enhanced access grid, improved Google Workspace integration, better UI, and new security measures.

3 identity and access management housekeeping tasks to start 2024
Ah, January! The month of fresh starts, new resolutions, and doubling down on our best behaviors.

YeshID Now Available on Google Workspace Marketplace
YeshID now on Google Workspace Marketplace! Streamline IAM with easy onboarding/offboarding, 2FA, and OAuth management.

YeshID integrations: an easier way to manage app access for SMBs
YeshID replaces spreadsheets for onboarding/offboarding, automating access management for Google Workspace.

New from YeshID: Data visualization for Google Workspace access
YeshID simplifies managing OAuth tokens with new data visualization: identify risks, revoke, or block access easily.

Release notes for November 28, 2023
YeshID updates: better mobile signup, improved task management, event scheduling fixes, Google sync alerts, and new link

A new era of secure IT identity management: YeshID, SOC II, and you
YeshID is SOC II compliant! Enjoy secure, compliant onboarding and offboarding with top data protection standards.

A Non-Technical Guide: How to Streamline Employee Onboarding in Google Workspace
Streamline Google Workspace onboarding with YeshID Onboard. Efficiently set up accounts, grant access, and track.

Stepping Lightly: A Guide to Avoiding Onboarding and Offboarding Missteps
Avoid IAM trip-ups with YeshID: right-sized tools, delegate tasks, adopt best practices early, and focus on both.

YeshID Product Update November 12, 2023
YeshID Update: New AUIDs, improved database migration, simplified UI, better email notifications, and smoother login.

What to look for in an employee onboarding tool for small businesses
YeshID Onboard: Easy, automated onboarding/offboarding for SMBs. Free for first 100 signups. Join now!

A Non-Technical Guide: How to Streamline Employee Onboarding in YeshID
Streamline Google Workspace onboarding with YeshID Onboard. Ensure new employees have access from day one.

Why are we giving YeshID Onboard away for free?
YeshID Onboard is free for the first 100 Google Workspace organizations with 25-250 employees.

Right-sized onboarding and offboarding free for the first 100 signups
Join YeshID's beta for free onboarding/offboarding for the first 100 Google Workspace companies under 250 employees.

Tips for building effective IAM processes at your startup
Manage IAM efficiently with YeshID: simple, flexible processes for onboarding, offboarding, and access management.

The history of SSO and why it’s time for a change
YeshID simplifies SSO for startups and SMBs in Google Workspace. Streamline access, manage tasks, and secure with pass

It’s time to meet YeshID: beta now open for early adopters
Join YeshID's for free! Simplify IAM for Google Workspace: enforce MFA, monitor access, streamline onboarding/offboardin
What Makes IAM “AI-Native”? A Definition, Maturity Model, and Why Being the IdP Matters

At 9:07 a.m. on a Monday, a new hire is ready to work.
They have a laptop. They have an email address. They have a calendar invite titled “Day 1 Kickoff.”
And then:
- They can’t access the code repo.
- They can’t access the ticketing system.
- They can’t access the data warehouse.
- They can’t access the customer support tool.
- Someone in Slack says, “File an access request.”
By lunch, three people have approved the request, two admins have touched four consoles, and one critical permission is still missing—because the app that actually matters isn’t connected to anything.
Offboarding is worse. You disable the user in the IdP, feel relieved, and move on. But weeks later you discover:
- a lingering app-local admin role
- an API token created “temporarily”
- an OAuth delegation that still lets a third-party app pull data
- an app-to-app connection that keeps syncing content long after the human account is gone
This is the uncomfortable truth: identity and access management (IAM) isn’t a product category; it’s the control plane of the company. And as companies become more software-defined (and now agent-enabled), IAM becomes the bottleneck—or the leverage point.
“AI-native IAM” is the attempt to turn IAM from a queue of tickets into an always-on system that understands access, reasons about risk, executes changes, and proves what happened.
This post defines AI-native IAM precisely, lays out a practical maturity model, and briefly covers an important design choice: why an AI-native IAM product can be meaningfully stronger if it’s also the IdP.
The definition: what “AI-native IAM” actually means
An IAM product is AI-native if AI is essential to its core function, not just a UI feature.
Working definition:
AI-native IAM continuously understands access reality, reasons about policy and risk, and safely executes IAM changes end-to-end—at scale—with verifiable outcomes.
There are four non-negotiables embedded in that sentence:
- Continuously understands access reality Not “what the IdP group says,” but what permissions exist in reality across apps, cloud, data, and infrastructure—including non-human access paths like tokens and delegated OAuth grants.
- Reasons about policy and risk Not “approvals as ceremony,” but decisions grounded in least privilege, role intent, separation-of-duties, sensitivity, and blast radius.
- Safely executes changes end-to-end Not “here’s a recommendation,” but actual provisioning, deprovisioning, right-sizing, exception handling, and remediation—with guardrails.
- Verifiable outcomes Not “we think we removed access,” but “we can prove what changed, why it changed, who approved it, and what the system state is now.”
What AI-native IAM is not
A lot of products will use “AI-native” loosely. The common mislabels:
- “AI in the UI”: summaries, chat search, nicer access request forms Helpful, but not AI-native. The operating model hasn’t changed.
- “LLM-driven tickets”: the LLM writes the request, humans do the work Still a queue. Still brittle. Still slow.
- “Static RBAC + AI suggestions”: role advice with no execution path If roles drift (they do), advice without enforcement is just noise.
AI-native IAM isn’t “talk to IAM.” It’s “IAM that can act responsibly.”
Why AI-native IAM is happening now
Legacy IAM broke for two reasons.
1) The surface area exploded
Modern orgs have:
- hundreds of SaaS apps
- multiple clouds
- data tools with fine-grained permissions
- API tokens, service accounts, and non-human identities
- contractors, vendors, and shared operational accounts
- delegated connections (app-to-app, SaaS-to-SaaS, agent-to-app)
Access isn’t a simple “user → group → app” graph anymore. It’s a living ecosystem.
2) Work is becoming agentic
Agents will take actions in tools: creating resources, responding to incidents, onboarding vendors, running finance workflows.
If agents can do work, they must have access. If they have access, access must be governed. If access must be governed, the governance must be continuous and machine-enforceable.
Periodic reviews and ticket workflows don’t fit that world.
Elevator pitch: why build AI-native IAM
AI-native IAM is the control plane for safe autonomy. It makes access decisions faster and safer by continuously understanding real entitlements (including tokens and delegations), reasoning about least privilege and blast radius, executing changes across the long tail of systems, and producing audit-grade evidence by default. It replaces fragile, manual IAM operations with a governed system that can keep up with constant org change—and with agents doing real work.
If you can build that, you’re not making a better form. You’re changing the operating system.
The foundations: what an AI-native IAM product must be built on
Before you talk about “agents,” you need a substrate that makes safe automation possible.
1) An identity + entitlement graph
You need a unified model of:
- identities (employees, contractors, vendors, service accounts, agents)
- groups and roles (IdP groups, app-local roles, cloud roles)
- entitlements (permissions, scopes, resource-level access)
- resources (projects, repos, datasets, customer accounts)
- relationships (who can grant what, who owns what, what is inherited)
- non-human access paths (API tokens, OAuth grants, delegated connections)
If you don’t have the graph, you don’t have ground truth.
2) An integration fabric (read + write)
“Supports SCIM” is table stakes—and insufficient.
AI-native IAM requires connectors that can:
- read entitlements deeply (app-local roles, permissions, resource scope)
- write changes back (provisioning, deprovisioning, role changes)
- handle the long tail via REST APIs, SDKs, and custom integrations
- detect drift when app configurations change
- inventory and control tokens and delegations where the underlying system exposes them
Without write access, you have analytics. Not governance. Still useful!
3) A policy control plane
Policies must be:
- explicit (not tribal knowledge)
- machine-enforceable
- scoped by risk (what can be automated vs what requires approvals)
- mapped to data sensitivity and operational constraints
Policies become guardrails for autonomy.
4) Provenance and auditability by default
Every decision and action needs an evidence trail:
- inputs (what data was used)
- reasoning artifact (why the system decided)
- approvals (who signed off, under what policy)
- actions (what changed, where)
- verification (did the change actually take effect)
If you can’t prove it, you can’t run it in production.
The advantage of also being the IdP
You can build AI-native IAM without being an IdP. Many organizations will also require it, because they already have one. But it’s worth naming why “AI-native IAM + IdP” can be uniquely powerful when done correctly.
Being the IdP gives you a privileged control point for both authentication and delegation.
What that buys you:
- You’re already in the SSO path. If your product is the system that issues SAML/OIDC assertions, you see what apps are actually being used, by whom, and when—without relying solely on periodic app inventories.
- You get first-class control over “who can access what” at login time. SSO policy, step-up authentication, device posture gates, conditional access—these are enforcement levers that don’t require every app to be perfectly integrated.
- You can treat OAuth and API delegation as a first-class IAM problem. The next generation of access isn’t just “human → app.” It’s:
- app → app connections
- agent → app permissions
- delegated OAuth scopes that quietly expand data access
- long-lived tokens that outlive the human who created them
If your product also acts as the authorization server for OIDC/OAuth (or has deep hooks into it), you can often discover, govern, and revoke those delegations with far more precision.
Important nuance: being the IdP doesn’t magically reveal every third-party OAuth grant that lives inside every SaaS ecosystem. For those, you still need deep connectors. But owning (or deeply integrating with) the IdP gives you a clean enforcement and visibility layer for a large and growing set of access paths—and it reduces blind spots that pure “workflow IAM” tends to miss.
Practically, it’s the difference between:
- “We disabled the account” and
- “We revoked the identity, invalidated active sessions, and removed delegated access paths tied to that identity.”
That’s a big deal in a world of app-to-app sync, automation, and agent permissions.
The maturity model: levels of AI-native IAM
“AI-native” isn’t binary. It’s a gradient. Here’s a practical ladder you can use to classify a product—or your internal state.
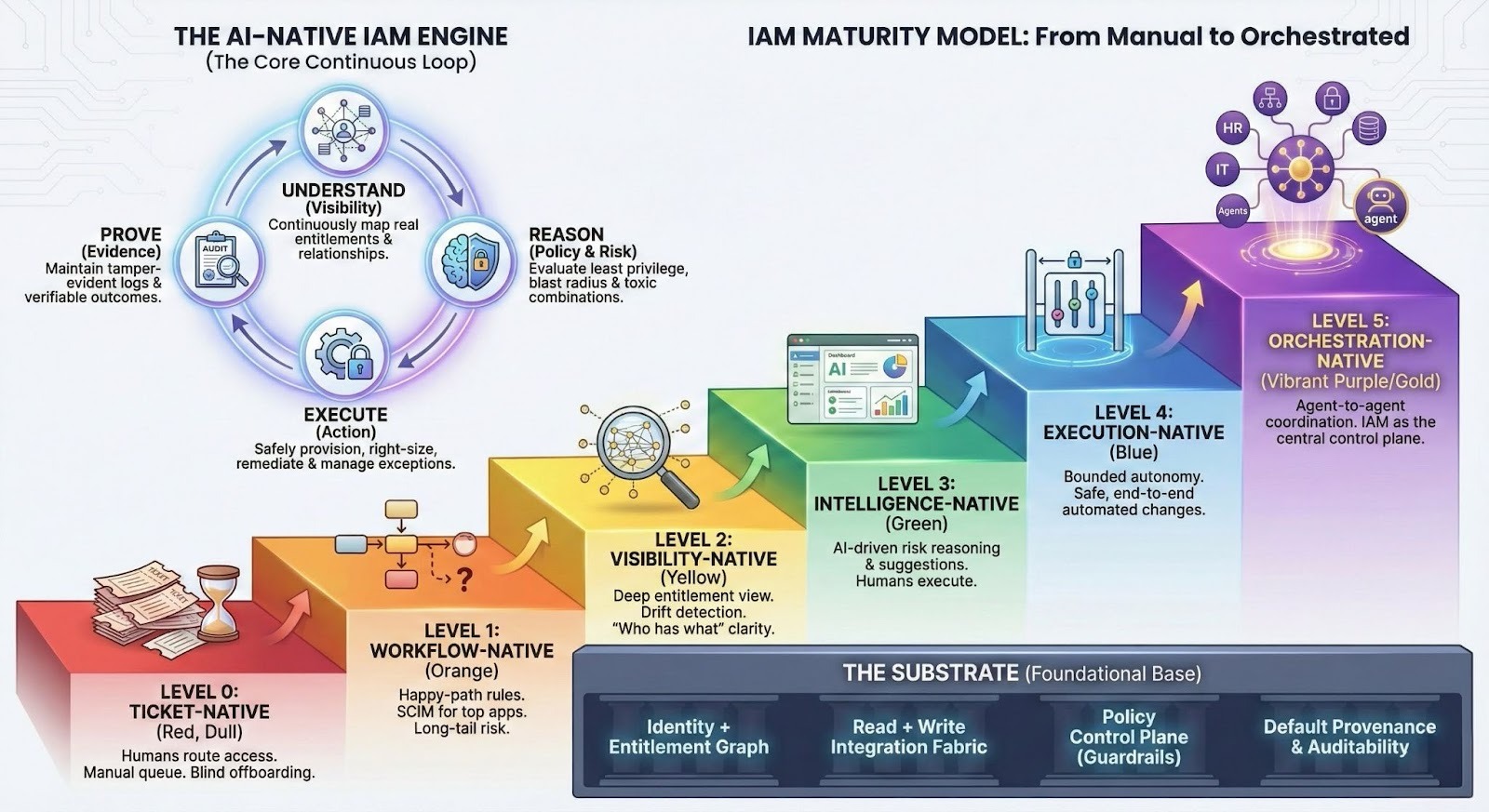
Level 0 — Ticket-native IAM
Operating model: humans route access through tickets and chat.
- Requests are manual.
- Fulfillment is manual in admin consoles.
- Offboarding is best-effort.
- Evidence is assembled during audits (painfully).
Tell-tale sentence: “We disabled the account, but we’re not sure what else still has access.”
Level 1 — Workflow-native IAM
Operating model: rules automate the happy path.
- Joiner/mover/leaver workflows exist.
- Some SCIM provisioning works for top apps.
- Exceptions still require humans.
- RBAC exists, but drifts over time.
What improves: speed and consistency—until reality deviates.
Common failure: the “long tail” of apps stays unmanaged, and that’s where risk accumulates.
Level 2 — Visibility-native IAM
Operating model: entitlement coverage becomes real.
- Deep visibility into app-local roles and resource-level permissions.
- A unified “who has access to what and how.”
- Drift detection: reality vs intended state.
- Visibility expands beyond “accounts and groups” into delegated access paths where possible (tokens, OAuth grants, app-to-app connections).
Key unlock: You can finally govern what you can actually see.
Litmus test: Can you answer this reliably: “Show me every path by which Alex—or Alex’s automations—can reach Customer Data X.”
Level 3 — Intelligence-native IAM
Operating model: AI improves decisions; humans still execute most changes.
AI meaningfully helps with:
- role mining and role suggestions (RBAC hygiene)
- risk-based access reviews (prioritize what matters)
- toxic combinations and separation-of-duties conflicts
- blast radius analysis (what compromise would expose)
- flagging risky delegations (over-broad OAuth scopes, stale tokens, suspicious app-to-app access)
Humans remain the primary operators for remediation and enforcement.
Litmus test: Does AI reduce decision time and review fatigue measurably—or just summarize dashboards?
Level 4 — Execution-native IAM
Operating model: AI executes within guardrails.
The system can perform end-to-end operations safely:
- provisioning/deprovisioning across apps (including non-SCIM via APIs/custom)
- just-in-time access with expiration
- permission right-sizing (least privilege applied where safe)
- automated remediation for certain classes of risk
- exception handling with compensating controls
- revoking delegated access where the system has authority (tokens, sessions, OAuth grants, app-to-app connections)
But it’s not “hands-off.” It’s bounded autonomy:
- approvals required for high-risk actions
- least-privileged agent identity
- change previews and rollback
- tamper-evident logs
Outcome: IAM starts behaving like an always-on team, not a queue.
Level 5 — Orchestration-native IAM (agent-to-agent IAM)
Operating model: IAM becomes a coordinator across systems and owners.
At this level, IAM is no longer a single system acting in isolation. It can coordinate across:
- HR (employment status, org changes)
- IT (device posture, endpoint health)
- security tooling (SIEM/SOAR, detection context)
- data governance (sensitivity, residency, policy constraints)
- application owners (approval and ownership boundaries)
- finance/procurement (vendor onboarding and renewals)
- agent ecosystems (agent identity, delegated permissions, agent-to-app scopes)
Work becomes a structured flow:
Intent → policy evaluation → negotiation → approvals → execution → evidence
Humans stay in the loop for:
- policy changes
- new trust boundaries
- high-risk access
- exceptions that exceed guardrails
Distinctive capability: The product can coordinate multi-step outcomes across multiple owners while remaining auditable and safe.
A quick glossary for the concepts that matter
- Entitlements: the concrete permissions granted inside systems (roles, scopes, resource access), not just group membership.
- Blast radius: what an identity can reach if it’s compromised—directly and indirectly (via escalation paths and delegated access).
- Toxic combinations / SoD: permission pairings that create fraud or high-risk capability when held by the same identity.
- JIT access: permissions granted temporarily for a task, with automatic expiration and logging.
- Delegations: non-human access paths such as OAuth grants, app-to-app connections, and tokens that allow one system to act on behalf of another.
How to evaluate an “AI-native IAM” claim in practice
If you want to classify a product (or your own setup), ask these questions.
Coverage and visibility
- Can it show app-local entitlements and resource-level permissions, not just IdP groups?
- What percentage of apps are integrated for read?
- What percentage are integrated for write (the ability to enforce changes)?
- Can it inventory and reason about tokens and delegated access paths (OAuth grants, app-to-app connections) where those systems expose them?
Decision quality
- Can it explain why access was granted or denied in policy terms?
- Can it quantify risk using blast radius, sensitivity, privilege tiering, and toxic combos?
- Does it understand context (role, team, project, device posture, data sensitivity)?
- Does it recognize that “the user” might be acting through automation, delegation, or an agent?
Execution and safety
- Can it remove access everywhere on offboarding, including app-local admin paths?
- Does it support JIT + expiration + break-glass workflows?
- Can it revoke sessions/tokens/delegations where applicable?
- Does it preview changes and support rollback?
Governance and evidence
- Can you reconstruct an access decision end-to-end months later?
- Are logs tamper-evident and audit-ready?
- Can you prove “policy was enforced,” not just “someone clicked approve”?
If the answers are mostly “no,” it may still be valuable software—but it’s not AI-native IAM.
Three mini-stories that reveal the level immediately
1) Offboarding: “disabled” vs “deprovisioned”
- Ticket/workflow-native: IdP disabled, maybe SCIM deprovisioned in some apps; app-local roles linger.
- Visibility-native: you can see all entitlements; you know what must be removed.
- Execution-native: entitlements are actually removed everywhere, tokens revoked, suspicious delegations flagged, verification recorded.
- Orchestration-native: downstream owners are looped in automatically (transfer ownership, rotate credentials, reassign on-call, revoke agent scopes), and evidence is packaged automatically.
2) Access reviews: spreadsheets vs continuous governance
- Legacy: quarterly spreadsheet of “users in groups,” reviewed with rubber-stamp approvals.
- AI-native: continuous risk-based review:
- focus on high-risk permissions and anomalies
- auto-expire stale exceptions
- propose and execute right-sizing where safe
- treat delegated access (OAuth grants, app-to-app connections) as reviewable access too
- generate evidence without manual compilation
3) Incident response: panic vs containment
- Legacy: scramble to understand what the compromised identity can access.
- AI-native: blast radius is computed immediately:
- prioritize what to revoke first (including delegations)
- enforce step-up auth/JIT where needed
- contain lateral movement paths
- record exactly what was changed and why
In each case, the difference isn’t a better interface. It’s a different operating system.
Common traps and “AI-native” theater
Watch for these patterns:
- Chat-first, integration-last If the product can’t write changes back across systems, it can’t enforce governance.
- Recommendations without remediation “Here’s a risk” is only useful if the system can reduce it safely.
- Automation that breaks auditability If you can’t reproduce why a decision happened, you can’t trust it.
- RBAC as a one-time project Roles drift. Teams change. Apps change. AI-native IAM treats RBAC as a living system.
- Ignoring delegated access paths Disabling accounts but leaving OAuth grants and tokens untouched is the modern version of “we forgot the shared folder.”
What AI-native IAM unlocks
When IAM becomes continuous, intelligent, and executable, a few things happen:
- Onboarding becomes fast without becoming sloppy Access is granted with least-privilege defaults, not “give them everything and fix it later.”
- Offboarding becomes complete and provable You stop carrying invisible risk for months.
- Standing privilege drops More JIT, fewer permanent admin entitlements.
- Delegated access becomes governable OAuth scopes, app-to-app connections, and agent permissions stop being invisible side channels.
- Audits become a byproduct Evidence is generated continuously, not assembled in a fire drill.
- Agents can do real work safely Because access is governed as a first-class system, not an afterthought.
Closing checklist: if you only remember six things
- Entitlements matter more than identities. Groups are not access. Permissions are access.
- Integration depth is destiny. Read + write coverage across the long tail is what makes governance real.
- Policies must be enforceable, not aspirational. PDFs don’t prevent over-privilege.
- Bounded autonomy beats manual heroics. Automate what’s safe. Escalate what’s risky. Log everything.
- Provenance is part of the product. “We can prove it” is the difference between a demo and production.
- Don’t forget delegation. OAuth grants, tokens, app-to-app connections, and agent scopes are access paths too—and they need governance.
AI-native IAM is not “IAM with chat.” It’s IAM that continuously understands, decides, executes, and proves—so the company can move faster without expanding its blast radius. And if you can combine that with the IdP layer (or integrate so deeply it behaves like one), you get a uniquely strong enforcement point for both human and non-human access in an increasingly automated world.
One Agent to Run IAM: Why Holistic Context Beats a Fleet of Siloed Bots

IAM admins don’t suffer from a lack of tools. They suffer from a lack of cohesion.
On any given day you’re juggling identity providers, directories, HR signals, app configurations, provisioning pipelines, approvals, RBAC policies, workflow engines, OAuth sprawl, non‑human identities, and audit obligations. Each subsystem has its own console, its own vocabulary, and its own “source of truth.” The work isn’t hard because any one piece is incomprehensible—it’s hard because the system is fragmented.
That fragmentation has shaped how AI gets applied to IAM so far: a bot for access requests, a bot for RBAC, a bot for audits, a bot for workflow debugging, a bot for OAuth. Each is “smart” inside its sandbox, and mostly blind outside it.
The problem is that IAM failures don’t respect those boundaries.
A single AI agent with a holistic view across IAM—apps, identities, access, workflows, approvals, policy, OAuth, and risk—becomes materially more powerful than a collection of siloed agents. Not because it’s bigger or more complex, but because it can connect the dots the way an experienced IAM operator does.
This post explains why that matters and what it unlocks for an IAM admin.

The core truth: IAM is an end-to-end system, not a set of tickets
Most of the work you care about lives between systems:
- A user can’t access an app. Is it RBAC policy? Group mapping? Provisioning failure? Approval routing? Unlinked account? OAuth vs SAML? Directory identity risk block?
- A leaver is offboarded. Did access actually get removed? Were there exceptions? Did any OAuth grants remain? Did any unlinked accounts survive? What about non-human identities?
- Drift is exploding. Is it a policy modeling issue, a provisioning regression, a mapping gap, or a new onboarding flow?
When you’re doing this manually, you end up performing the same dance every time:
- Start with a symptom.
- Jump across consoles and tables to gather evidence.
- Reconcile contradictions.
- Form a hypothesis.
- Test it.
- Decide on the least risky remediation.
- Verify the fix.
A siloed agent can only help with step 2 in its own domain. A holistic agent can help with the entire loop.
Why “many specialized agents” breaks down in real IAM ops
Siloed agents create three failure modes that IAM admins feel immediately:
1) They can’t see causal chains
A workflow debugging agent might tell you “tasks are failing,” but can’t explain that the root cause is OAuth permissions revoked for the provisioning connector. An access agent might say “user is missing entitlement,” but can’t correlate that the provisioning pipeline has been erroring since yesterday.
In IAM, the right answer is rarely “the one thing that’s broken.” It’s usually the interaction.
2) They force you to be the integrator
When separate agents disagree, you become the arbitration layer. You’re the one reconciling “policy says yes” vs “account doesn’t exist” vs “workflow failed” vs “approval never triggered.”
That’s exactly the cognitive load you were trying to offload.
3) They duplicate effort and miss the “what next?” step
You don’t just need facts. You need sequencing:
- What do I fix first to reduce risk fastest?
- What’s reversible vs irreversible?
- What can I contain immediately while I work on a durable fix?
- How do I verify we’re back in a good state?
Siloed agents tend to output “their” slice of evidence without turning it into a coherent plan.
What a holistic IAM agent can do that siloed agents cannot
A single agent with end-to-end IAM context can operate like a seasoned IAM admin: it starts with intent (“what are we trying to answer?”), then collects the right evidence across systems, then produces a recommendation that accounts for tradeoffs, blast radius, and verification.
Here are the high-value use cases where that difference shows up.
1) Access triage that actually resolves the issue
The classic ticket: “User can’t access GitHub.”
A siloed access agent might check the access request status. A siloed RBAC agent might evaluate policy. A siloed provisioning agent might check connector health.
A holistic agent can do the full diagnosis:
- What does the user have today?
- What should they have per policy?
- Is there a linked account in the target app?
- Did provisioning run? Did it fail? Where?
- Did an approval route correctly, or is routing misconfigured?
- Is there drift (over/underprovision) for this user/app?
- Is this actually an authentication/IdP issue outside IAM provisioning?
Most importantly: it can classify the failure into actionable categories and recommend the least disruptive path to resolution—then provide a verification loop to confirm the fix.
You get “here’s what’s wrong and what to do,” not “here’s a report.”
2) Joiner/Mover/Leaver programs that don’t rely on heroics
JML is where IAM maturity is proven—and where operational reality is brutal.
A holistic agent becomes a JML quality engine because it can validate outcomes end-to-end:
Joiner
- Identity exists, is mapped correctly, meets posture requirements (e.g., MFA).
- Baseline access is granted as expected.
- Accounts are created and linked in target apps.
- Any workflow failures are surfaced with clear next steps.
Mover
- Expected access changes are identified.
- Old access that should have been removed is flagged.
- Exceptions are documented and traceable.
- Provisioning/approval workflows are verified.
Leaver
- Access is actually removed (not just requested).
- Unlinked accounts are detected and escalated.
- OAuth grants and shadow access paths are identified.
- Non-human identities tied to the person/team are included in the offboarding story.
The value isn’t that the agent “automates offboarding.” The value is that it makes offboarding verifiable and repeatable, and it surfaces exceptions before they turn into audit findings.
3) RBAC that is maintainable, not a one-time project
Effective RBAC is time-consuming for one reason: it’s an iterative control system.
You design policy → reality deviates → you investigate → you adjust policy/process → repeat.
A holistic agent accelerates the loop:
- Quantify drift by reason and blast radius.
- Identify top apps contributing to risk.
- Distinguish: policy gaps vs mapping issues vs provisioning regressions vs true exceptions
- Produce a prioritized remediation backlog.
- Support safe rollouts with before/after verification.
This shifts RBAC maintenance from “painful quarterly cleanup” to an ongoing, manageable operational rhythm.
4) OAuth and Shadow IT triage that connects to governance
OAuth risk is not just “look at scary scopes.” The hard part is:
- Who granted it?
- How many users are impacted?
- Is it tied to a managed app we already govern?
- What’s the containment action that won’t break the business?
- What’s the durable alternative?
A holistic agent can connect OAuth findings to the rest of IAM:
- Is the app managed or unmanaged?
- Do we have an approved integration we can migrate to?
- Do we need approval routing changes?
- Do we need policy changes for safer defaults?
It can turn “here’s a risky OAuth app” into “here’s the path to eliminate it.”
5) Audit readiness as a byproduct of operations
Audits punish fragmentation: evidence lives everywhere, narratives are inconsistent, and exceptions are undocumented.
A holistic agent can generate audit-ready outputs naturally from operational workflows:
- Access review packages (per app, per role, per population)
- Approval routing evidence and effective approver mapping
- Drift reports that prove alignment (or quantify misalignment)
- Identity risk posture (MFA, dormancy, mapping quality)
- Workflow execution evidence (what ran, what failed, what was remediated)
The win is not “faster spreadsheets.” The win is a consistent, evidence-driven story of how access is governed—produced on demand.
The real advantage: it produces decisions, not dashboards
IAM admins don’t need another place to look at data.
They need help deciding:
- What is the most likely root cause?
- What is the safest remediation?
- What is the blast radius?
- What can I do now to contain risk?
- What should I do next to make the fix durable?
- How do I verify we’re back to green?
A holistic agent can answer those questions because it can see the full chain: identity → policy → approval → provisioning → access → drift → risk.
Siloed agents can’t do that reliably, because each sees only one link.
How modern agent systems make “one agent, many workflows” practical
You don’t get a holistic agent by stuffing everything into one giant prompt. That becomes noisy, brittle, and hard to maintain.
Modern agentic harnesses typically use a “skills” approach: the agent keeps a stable core behavior, then loads the right domain playbook on demand—access triage, OAuth investigation, drift remediation, workflow debugging, app posture review, directory risk, approvals, NHI inventory, and so on.
To the IAM admin, the important point is simple:
- You interact with one agent.
- It adapts to many IAM intents.
- It stays consistent in how it gathers evidence and recommends action.
- It doesn’t lose context when the problem crosses domains—because it’s designed to cross domains.
What this means for the IAM admins
A holistic IAM agent becomes:
- Your Tier-2/Tier-3 investigator for access and provisioning issues
- Your RBAC maintenance operator that turns drift into a backlog
- Your JML quality enforcer that makes lifecycle outcomes verifiable
- Your OAuth and Shadow IT triage partner that connects risk to governance
- Your audit assistant that produces evidence packages and consistent narratives
And it does all of this without forcing you to be the glue between multiple bots.
Bottom line
IAM work is not a set of independent tasks. It’s a connected system where the highest-cost problems live at the seams.
That’s why one holistic agent—one that can traverse identity posture, access policy, approvals, workflows, provisioning, app accounts, OAuth, and drift—delivers outsized value compared to a fleet of siloed agents.
It doesn’t just answer questions.
It closes loops.
Release Notes: Janurary 2026

Release Notes: Janurary 2026
Over the month, the YeshID team has focused on delivering safer automation, expanding our integration ecosystem, and streamlining access reviews. From a new Audit Admin role to smarter HRIS handling and AI-assisted summaries, here is a consolidated look at the recent updates.
Highlights
Smarter, Safer Automation
- Centralized Trigger Management: We launched a dedicated Triggers page to make finding, adding, and editing automation triggers easier.
- Staged by Default: New triggers now stage workflows by default (applying no changes automatically), allowing you to safely test automation logic before enabling live actions.
- Enhanced HRIS Syncing:
- Change Requests: Directory or HRIS syncs now automatically launch change request workflows when users are modified, creating individual workflows per user to avoid duplicates.
- "Disappearing" User Handling: Offboarding automation is now more robust. If an HRIS simply stops sending a user record (rather than marking them terminated), YeshID can now set an end date to trigger offboarding workflows reliably.
- Script Security: You can now store reusable script settings with script-level properties, including encrypted values masked in the UI, to avoid hardcoding secrets in code-based actions.
Expanded Integrations
We have significantly expanded our catalog and improved how integrations are managed:
- New 1-click Integrations: Connect and manage Calendly, BambooHR, Remote.com, Zendesk, Atlassian (Beta), OpenAI, Chili Piper, and Ashby (Beta).
- Safer Setup & Disconnect: Integration actions cannot be enabled until fully configured and saved. Disconnecting an integration now performs a clean cleanup of provisioning settings and authorization, updating the UI status immediately.
- Atlassian Actions: The Atlassian integration now includes support for "Activate User" actions.
Streamlined Audits & Governance
- New Audit Admin Role: A specialized role allows audit owners to start, run, and complete access reviews without requiring full application admin privileges.
- Improved Workflow Visibility:
- The workflows list now clearly indicates what triggered each run (e.g., specific sync, manual trigger) for better troubleshooting.
- New filtering options allow you to sort by target person, view completed tasks, and bulk-select workflows to delete test runs or start staged items.
- AI-Assisted Administration: The AI chat experience has been redesigned with richer, evidence-linked details. An optional AI-generated weekly admin summary email now provides deep links into organizational health.
Improvements
- Policy Alerts via Teams: Policy alerts can now notify Microsoft Teams. Teams access requests have also been upgraded to support role selection, time-based access, and custom fields.
- Data Visibility: Google Workspace group imports now include nested group members. Additionally, CSV exports across the platform now match the specific filters and sorting you are viewing on screen.
- User & Account Management:
- Drift Analysis: Access drift views now support deep links into specific application and user contexts.
- Manual Imports: The "Import Users" dialog now supports drag-and-drop for CSVs or screenshots with clearer validation.
- App Accounts: You can now edit account names and external IDs for non-integrated applications directly in the UI.
- RBAC Safety: Enabling or disabling RBAC policies no longer risks removing the policy’s principals or app assignments unexpectedly.
Fixes
- Connector Reliability:
- Microsoft: Improved reliability during onboarding by retrying token exchanges if consent hasn’t propagated. Microsoft sign-in now correctly loads user roles (e.g., Auditors see the correct menus immediately).
- Salesforce: SCIM provisioning now allows configuring a profile ID for user creation and uses the correct format for deactivation requests.
- Google: Connections are more stable via improved refresh token handling.
- Workflow Logic:
- Fixed issues where catalog integrations (including Drata) stopped early due to pagination errors.
- Addressed a bug where "remove user" tasks appeared successful even if the removal failed.
- Workflow runs now reconcile missed completions and continue updating even if a single task fails.
- Data Integrity: CSV and screenshot imports now handle commas in numbers and missing IDs more gracefully, with safeguards to prevent accidental mass deactivations during incomplete mappings.
Availability
- Role-Based Access Control (RBAC): Currently in Beta.
- New Integrations: Atlassian and Ashby integrations are currently in Beta.
- AI Features: AI Chat is available on all plans except Free.
IAM or SaaS Management First

How Heads of Technology Should Think About Control, Cost, and Action? As organizations grow past a certain point, technology leaders start seeing the same pattern repeat.
Access decisions are made quickly. Tooling spreads organically. People move roles faster than systems are updated. Nothing is obviously broken, but control feels increasingly indirect.
That’s usually when teams start asking where to invest first: in SaaS management to get organized, or in Identity & Access Management to get control.
They’re often discussed together. They shouldn’t be.
SaaS Management Reports on the Environment
SaaS management platforms, like Torii or Corma, are designed to answer finance-oriented questions.
They surface which applications exist, how many licenses are assigned, who owns each vendor, and where there may be opportunities to reduce spend. For Finance teams, this reporting layer is critical. It creates visibility and predictability around an otherwise fast-moving SaaS footprint.
But by design, SaaS management is largely descriptive.
It shows what exists. It suggests where action might be taken. It does not typically enforce access.
IAM Models Reality and Can Act on It
Identity & Access Management starts from a different premise.
It assumes that understanding the environment isn’t enough. At some point, systems need to act.
IAM systems model who can log in, what permissions they hold, how that access was granted, and how it evolves over time. More importantly, they sit in the path of enforcement.
Modern IAM platforms don’t just tell you that access exists. They allow you to remove it.
That includes:
- Deprovisioning users when they leave or change roles
- Revoking access inside applications
- Removing licenses safely
- Cutting off OAuth tokens, service accounts, and automations
- Enforcing time-bound or policy-driven access
This action is taken from a security and IT perspective, not a financial one. The goal isn’t to save money directly. It’s to ensure that access matches intent and that changes actually take effect.
Platforms like YeshID are built to both understand and act on access, so that lifecycle decisions aren’t just documented, they’re enforced.
Why Acting on Lifecycle Reduces Cost Anyway
One of the quiet benefits of having an IAM layer that can act is that cost reduction stops being a separate initiative.
When access can be safely removed:
- Licenses don’t linger “just in case”
- Over-provisioning becomes unnecessary
- Cleanup doesn’t get deferred
- Teams don’t hold onto tools defensively
Costs go down because uncertainty goes down. This isn’t optimization driven by spreadsheets. It's a reduction driven by confidence. Finance may track the savings. IT makes them possible.
The Difference in Starting Points
If you start with SaaS management, you get better at identifying opportunities. But acting on those opportunities often requires a separate conversation with IT, additional tooling, or manual work.
If you start with IAM, you create the ability to act immediately. Understanding improves over time, but enforcement is available from day one.
That difference compounds.
Over time, organizations that lead with identity find that:
- Offboarding actually removes access
- License cleanup doesn’t break production
- App rationalization sticks
- Security posture improves without slowing teams down
Where This Leaves Heads of Technology
For Heads of Technology and IT, the decision isn’t about choosing between organization and control.
It’s about deciding whether your first system should describe the environment or shape it.
SaaS management helps you understand vendors and spend. IAM helps you understand and enforce how your company actually operates.
Both are necessary. But they solve different problems, and they deliver leverage at different moments.
Starting with IAM gives you the ability to act. Everything else becomes easier after that - including the ability to properly manage spend.
RBAC Isn’t Dead: Meet ReBAC

Enterprise IAM was built for a simpler shape of work: people log into a handful of apps, roles map cleanly to job functions, and permissions change slowly. In that world, RBAC (Role-Based Access Control) scales.
Most organizations today don’t live in that world anymore—even if they don’t have “autonomous agents.”
What they do have is this:
- Users authorizing OAuth access between SaaS products (Slack, Notion, GitHub, Google Workspace, ticketing systems, CRMs).
- “Smart” features and copilots inside each product that can read, summarize, suggest, and sometimes act.
- Automations and integrations that quietly move data across systems once you’ve granted them permission.
So the real access model increasingly looks like:
People authorize apps → apps act on their behalf → actions touch specific objects (docs, repos, channels, tickets) → those objects live inside shared workspaces with shifting relationships.
That’s why IAM is becoming less about “who has what role” and more about “who is related to what object, in what workspace, through what kind of sharing.”
You can call that ReBAC (Relationship-Based Access Control). But the important point for most companies is simpler:
You don’t need a new, centralized “agent platform” to benefit from relationship-based thinking. You need to govern OAuth, and you need object-level guardrails inside the tools you already run.
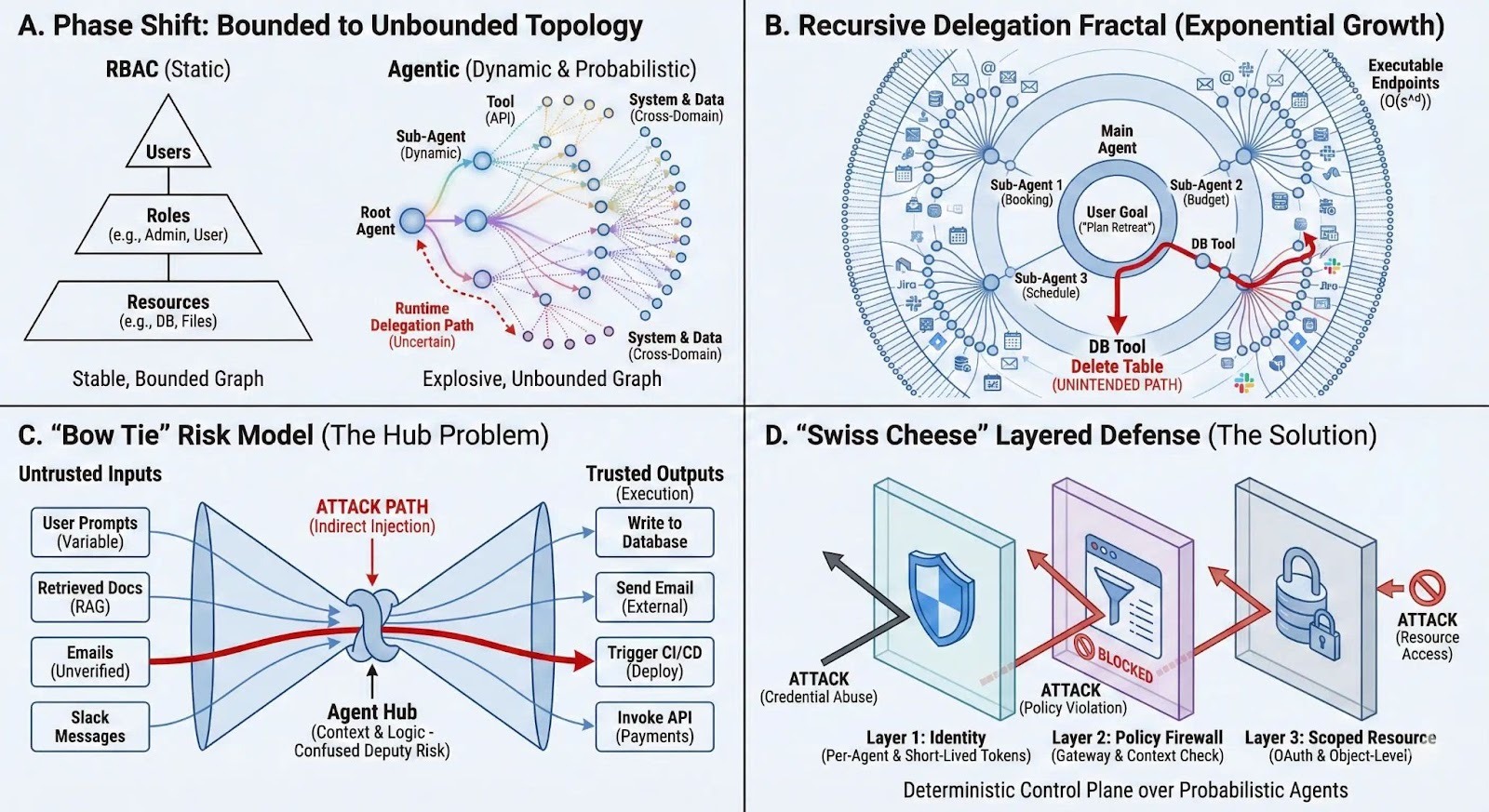
What changed (even without “real agents”)
In most orgs, “agents” are not a separate workforce of autonomous bots. They’re:
- a Slack app that posts and reads messages,
- a Notion integration that can read pages and update databases,
- a GitHub app or token that can open PRs, read code, create issues,
- a Google Workspace connection that can access Drive, Gmail, and Calendar,
- an AI assistant inside those products that can operate across what it can see.
Once OAuth is granted, these tools can behave like a personalized delegate: fast, persistent, and able to chain actions across systems.
This creates two practical realities:
- Authority is increasingly exercised by software acting “as you,” not only by you.
- The true security boundary is often the object (this doc, this repo, this channel), not the app.
Where RBAC breaks down in connected SaaS
RBAC still helps with coarse decisions:
- who can access GitHub at all,
- who can use Google Workspace,
- who can install Slack apps,
- who can be an org admin.
But RBAC strains in the places where modern SaaS work actually happens:
1) The important decisions are object-level
Most incidents and “oops” moments aren’t “someone accessed GitHub.” They’re:
- someone shared a sensitive Drive folder externally,
- a token pushed to the wrong repo,
- an integration read a private Notion space,
- a workflow posted data into the wrong Slack channel.
RBAC answers: “Can you use Drive?” Security needs: “Can you share this folder outside the company?”
2) SaaS permissions are relationship-driven, not role-driven
Access is usually justified by relationships:
- membership in a workspace/team,
- ownership of a project,
- being assigned to a ticket,
- being in a repo team,
- having a doc shared with you.
RBAC can approximate this, but it tends to produce either:
- role explosion (“Repo-Write-Project-A”, “Repo-Write-Project-B”…), or
- over-broad access (“just make it admin so the integration works”).
3) OAuth turns “permission bundles” into durable blast radius
OAuth grants often look like “allow this app to read files” or “access Slack workspace.” Those scopes are frequently broader than people realize, and they persist until revoked.
That’s not a theoretical problem. It’s a day-to-day operational one:
- new apps get authorized during experimentation,
- the app becomes “sticky,”
- nobody remembers it exists,
- and it keeps its access long after the original need is gone.
4) Input manipulation replaces credential theft as a common path
You don’t always need to “hack” an account if you can steer what a delegated tool does:
- a doc someone reads contains instructions the user (or assistant) follows,
- an issue template nudges an automated workflow,
- a page, email, or ticket text shapes what gets summarized or copied.
Even without full automation, steering a legitimate, authorized action is a recurring failure mode in connected workflows.
ReBAC, translated for normal companies
ReBAC can sound like “build a graph database and evaluate relationship paths.” Most orgs won’t do that.
Here’s the practical version that is achievable:
Relationship-based control already exists in your tools—use it deliberately
Your SaaS stack already runs on relationships:
- GitHub: org → team → repo → branch/PR
- Google Drive: domain → shared drive → folder → file → sharing settings
- Slack: workspace → channel → membership → app install permissions
- Notion: workspace → teamspace → page/database → share permissions
The strategy is to standardize how you use those relationship controls, and to treat OAuth connections as privileged.
Think of it as:
- RBAC for “entering the building” (access to the tool, admin vs user)
- relationship/object controls for “what you can touch inside” (which repos/docs/channels, what actions, and what sharing boundaries)
No new grand architecture required to start—just consistent policy patterns, enforced in the systems people actually use.
What to do that’s realistic for most organizations
1) Treat OAuth authorization like granting a new employee access
Most companies are looser with “Authorize app” than they would ever be with adding a new admin.
Minimum viable controls:
- Maintain an inventory of OAuth apps and integrations (first- and third-party).
- Require admin approval for high-risk scopes (or for any third-party app).
- Prefer least-privileged scopes and avoid “full workspace / all files” grants when narrower options exist.
- Periodically review and remove unused apps/tokens.
If you do only one thing: alert on new OAuth grants and new app installs. That alone catches a lot.
2) Put guardrails on the highest-risk actions, not on everything
You don’t need perfect least privilege everywhere. Start with actions that create outsized blast radius:
- external sharing / public links
- exports / bulk downloads
- permission changes (adding collaborators, granting org access)
- writing to production branches / triggering deploys
- creating API keys / tokens / new integrations
Make these actions require either:
- a stronger condition (admin-only, allowlist-only),
- a second step (approval / confirmation),
- or at least a high-signal audit trail and alerting.
3) Standardize “object boundaries” inside each core tool
This is where relationship-based thinking pays off without fancy infrastructure.
Examples of practical boundary patterns:
- Google Drive / Notion: default to teamspaces/shared drives with controlled sharing; restrict external sharing by default; allow exceptions via process.
- GitHub: use teams mapped to repos; enforce branch protections; require reviews for sensitive repos; use CODEOWNERS where appropriate.
- Slack: tighten who can install apps; restrict which apps can access message content; use private channels deliberately for sensitive workflows.
The point is consistency: “where sensitive work lives” should be structurally separated from “where experimentation happens,” so relationships enforce boundaries naturally.
4) Limit “copilot connectors” and AI features to approved data zones
AI assistants become risky when they can read broadly and write freely across systems.
Practical controls most orgs can apply today:
- Allow AI access to specific spaces/drives/repos rather than everything.
- Prefer configurations where AI can suggest but not execute high-impact changes.
- Avoid connecting AI tools to the most sensitive stores until you have confidence in logging and boundaries.
- Make “what data can be indexed / retrieved” an explicit governance choice, not a default.
Even if the assistant is “just summarizing,” summaries can move sensitive data into less-controlled places (like chat). Boundaries still matter.
5) Centralize logs enough to investigate quickly
Most organizations don’t need perfect lineage graphs. They need to be able to answer:
- Which integration did this?
- Acting for which user?
- On which object?
- With what scope?
- When was access granted?
Centralize audit signals where you can, and at minimum monitor:
- new OAuth grants/app installs,
- permission changes,
- external sharing events,
- unusual bulk access.
A pragmatic adoption path (low drama, high impact)
- Pick one domain where RBAC is obviously too coarse Docs (Drive/Notion), code (GitHub), or chat (Slack) are common.
- Define the 5–10 actions you never want to happen silently External share, export, permission grant, prod write, etc.
- Enforce boundaries using the tool’s native relationship model Teamspaces/shared drives, repo/team mappings, channel/app install controls.
- Tighten OAuth around that domain Require approval for high-risk scopes and block unknown apps.
- Iterate with real usage Don’t chase theoretical perfection; reduce the most common and highest-impact failure modes.
Bottom line
You don’t need a future where autonomous agents run everything for this to be true:
Connected SaaS already behaves like delegated automation. OAuth turns those connections into durable authority. And the real security decisions are increasingly object-level and relationship-driven.
So the practical evolution isn’t “replace RBAC with a graph database.” It’s:
- keep RBAC for tool entry and admin boundaries,
- add relationship/object guardrails inside each core platform,
- and govern OAuth + integrations like the privileged access layer it has become.
That combination is achievable for typical organizations—and it maps to how work is actually done in Slack/Notion/GitHub/Google Workspace style environments.
NIST Just Opened a Public RFI on Securing AI Agents

AI agents are moving from “helpful copilots” to systems that can plan, decide, and take action in production. The security industry has been warning for months that this transition changes the threat model: prompt injection, data poisoning, backdoors, and misaligned behavior don’t just distort answers — they can cause real, persistent changes in external systems.
Now the U.S. government is putting formal structure around that reality.
On January 12, 2026, NIST’s Center for AI Standards and Innovation (CAISI) published a Request for Information (RFI) seeking concrete guidance from industry and researchers on how to secure the development and deployment of AI agent systems. (NIST) The RFI was published in the Federal Register on January 8, 2026, and the public comment period closes March 9, 2026 (docket NIST‑2025‑0035). (Federal Register)
This is not a casual “thought leadership” exercise. It’s a standard-setting move — and it’s happening right as enterprises are experimenting with agentic automation in systems that were never designed for an untrusted reasoning loop.
There is no system more sensitive than Identity and Access Management.
What NIST is really doing here
CAISI’s RFI is scoped specifically to AI agent systems capable of taking actions that affect external state — meaning persistent changes outside the agent system itself. (Federal Register) That scope matters, because the security bar changes the moment an agent can:
- modify permissions,
- create credentials,
- rotate keys,
- approve workflows,
- change policies,
- or touch production infrastructure.
NIST is explicitly asking for input on:
- unique threats to agent systems (including indirect prompt injection, data poisoning, backdoors, and failure modes like specification gaming/misaligned objectives), (NIST)
- security practices and controls across model-level, agent system-level, and human oversight categories (including approvals for consequential actions and controls for handling sensitive and untrusted data), (Federal Register)
- how to measure and assess security (methods, evaluation approaches, documentation expectations), (Federal Register)
- how to constrain and monitor deployment environments (what the agent can access, how to monitor, how to implement rollbacks/undoes). (NIST)
NIST also makes it clear that the output of this process is intended to inform “voluntary guidelines and best practices” for agent security — the kind of guidance that quickly becomes a procurement checkbox, an audit expectation, and eventually (in some sectors) a regulatory requirement. (NIST)
Why this is happening now: “agent hijacking” is real, measurable, and still easy
This RFI didn’t appear in a vacuum. CAISI has already been publishing technical work on agent security — including a 2025 technical blog on agent hijacking, describing it as a form of indirect prompt injection where malicious instructions are inserted into data an agent ingests (emails, files, web pages, Slack messages), causing unintended harmful actions. (NIST)
That blog emphasizes a core security reality:
The architecture of many LLM agents requires combining trusted instructions with untrusted data in the same context — and attackers exploit that lack of separation. (NIST)
CAISI’s point is simple: if we can’t reliably prevent injection at the model layer, we must build system-level constraints and evaluation discipline that reduce blast radius and make incidents detectable and recoverable. (NIST)
IAM is the ultimate “external state” environment
If you want a single place where agent security has to be real — not demo-safe — it’s IAM.
IAM is the security layer that gates:
- every SaaS app,
- every cloud console,
- every privileged API,
- every admin action,
- and increasingly, every machine identity and automation identity.
So when an agent operates in IAM, it is operating in the control plane for the business.
That’s why the NIST framing (“agents that affect external state”) maps directly onto identity workflows:
- granting access,
- expiring time-bound entitlements,
- modifying group membership,
- enforcing policy,
- provisioning and deprovisioning accounts,
- rotating secrets,
- and creating/removing privileged identities.
In other words: IAM is where an agent goes from assistant to operator.
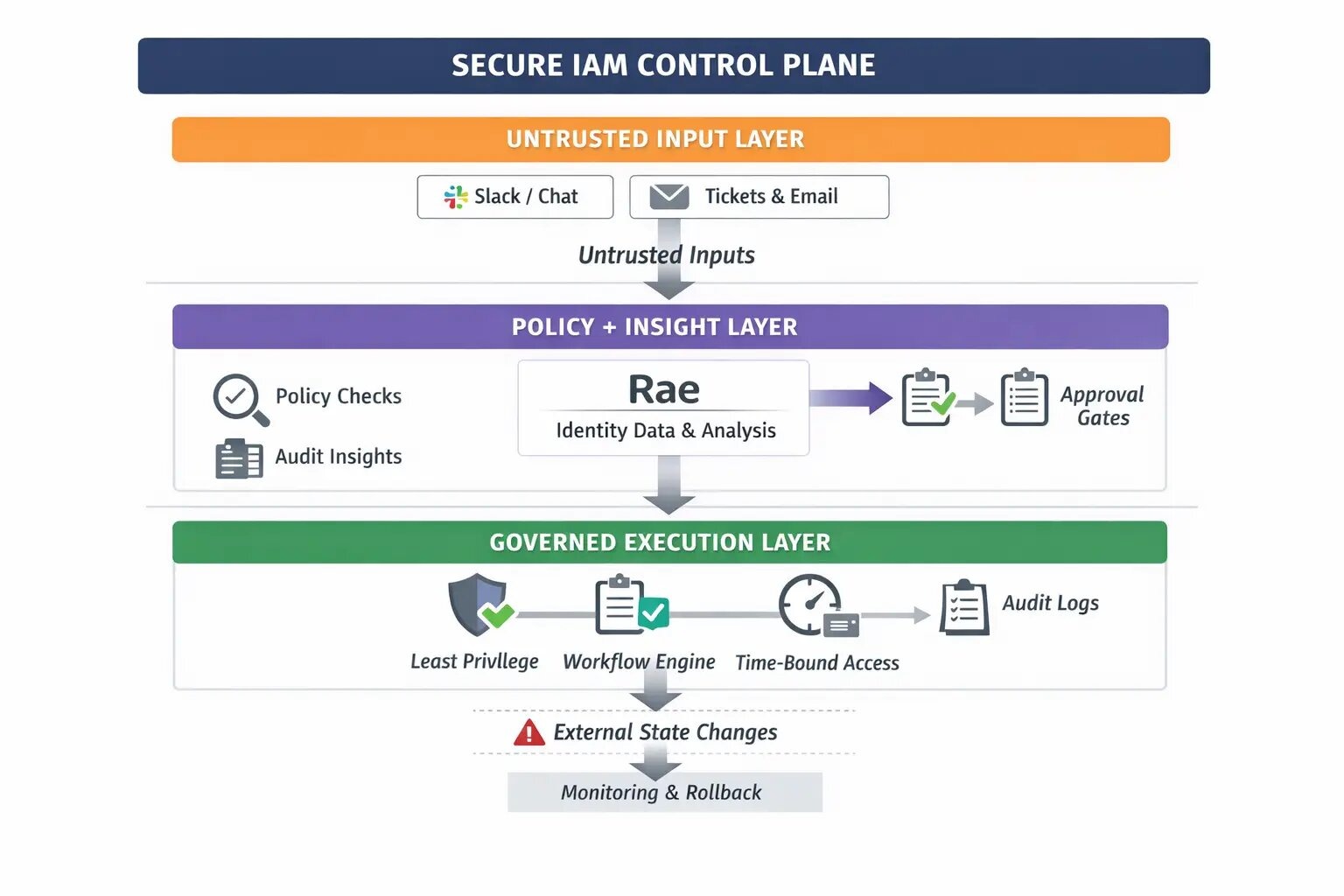
The emerging compliance posture: agents will be judged like safety-critical systems
NIST’s RFI is an early sign of how organizations will soon be expected to justify agent safety. Even before formal regulation lands, enterprise buyers will ask for proof that an agent system:
- Separates untrusted inputs from privileged actions Because if untrusted text can directly steer an execution tool, you have an exploit chain. CAISI explicitly focuses on risks that arise when “model outputs” are combined with software actions, including indirect prompt injection. (NIST)
- Implements least privilege and constrained environments The RFI calls out traditional best practices like least privilege and zero trust as relevant starting points, and asks how to constrain and monitor an agent’s access in its deployment environment. (Federal Register)
- Uses human oversight for consequential actions CAISI explicitly asks for “human oversight controls,” including approvals for consequential actions and network access permissions. (Federal Register)
- Can be evaluated and measured NIST is not just looking for opinions — it’s asking for methods and metrics to assess agent security during development and after deployment. (Federal Register)
- Has monitoring, detection, and rollback paths The RFI asks about monitoring deployment environments and implementing undoes/rollbacks/negations for unwanted action trajectories. (Federal Register)
This is the direction standards are heading: not “did you write a good system prompt,” but how is the system engineered to be safe even when the model fails?
The design constraint that matters in IAM: no “Ask→Read→Write” exploit chains
Security practitioners have converged on a pragmatic architecture lesson for agentic systems: you must prevent a single execution loop from simultaneously being exposed to:
- untrusted inputs,
- sensitive access,
- and the ability to change state.
This is the core of Meta’s widely discussed “Rule of Two” pattern (popularized through industry writeups and analysis): if an agent can read untrusted inputs and also access sensitive data and also act, prompt injection becomes a direct path to impact.
Whether or not you use that exact framing, it aligns tightly with what CAISI is asking for in the RFI:
- tool restrictions,
- approvals,
- permissioning boundaries,
- monitoring,
- and environment constraints. (Federal Register)
IAM is where this matters most, because the “tools” are literally privilege.
Why YeshID is positioned for the next phase of agent security
Most “agentic” product announcements start with a chat interface.
That’s backwards for IAM.
In identity, the interface is not the hard part. The hard part is building a system that can safely turn insight into action, with:
- policy grounding,
- approvals,
- auditability,
- and explicit boundaries between reasoning and execution.
YeshID is built as an AI-native identity control plane — governing authentication, access, and lifecycle across humans, applications, and non-human identities. (YeshID) And Rae (YeshID’s IAM-native agent) is positioned explicitly around the boundary the NIST RFI is pushing the industry toward: separate insight from action, keep actions governed. (YeshID)
1) Clear boundaries between insight and action
YeshID’s Rae messaging is explicit: it “separates understanding from execution,” and any actions follow the same approvals, permissions, and safeguards as other identity operations — “no silent changes” and “no autonomous privilege escalation.” (YeshID)
That’s exactly the kind of control-plane guardrail enterprises will be expected to articulate as agent security standards mature.
2) Answers grounded in real identity data
Rae is described as answering questions using structured identity data across users, apps, groups, permissions, and history — with responses designed to be traceable and explainable. (YeshID)
This matters for two reasons:
- it reduces hallucinated “best guess” outputs, and
- it supports the audit and assessment posture NIST is asking about (what happened, why it happened, what data was used). (Federal Register)
3) Guarded workflows and approvals
YeshID supports access requests directly in Slack or Teams, with in-line approvals and time-based access that expires automatically — a built-in rollback mechanism for access grants. (YeshID)
In a world where agent actions increasingly need to be constrained, reversible, and governed, “time-bound by default” is not a convenience feature — it’s a safety feature.
4) Environment-integrated execution instead of freeform tool calling
NIST is explicitly asking how agents should be constrained in deployment environments and how monitoring/rollback should work. (Federal Register) YeshID’s approach is to put agentic capability inside an IAM control plane, not outside it.
That difference is foundational:
- a generic agent “calls tools,”
- an IAM-native agent operates inside a system designed to enforce policy, approvals, and traceability.
The takeaway: regulated expectations are coming — and IAM will be the test case
NIST’s RFI is the clearest public signal yet that “secure agentic systems” are becoming a defined engineering discipline, with standards, evaluation methods, and best practices on the way. (NIST)
IAM will be the highest-pressure proving ground because identity is the security layer for everything else — and because agents that can change access are, by definition, agents that can change external state. (Federal Register)
YeshID’s bet is aligned to that trajectory: agentic IAM is inevitable, but only systems designed for guardrails, policy grounding, approvals, and auditability will be deployable in the real enterprise.
Rae is built for that reality — not as a chatbot, but as governed identity automation inside an authoritative control plane. (YeshID)
Drift Happens. The Problem Is Everyone Pretends It Doesn’t

Most identity and access tools are built on a comforting assumption: your access model is tidy. Your groups make sense. Nobody bypasses the system. Everyone logs in through the approved IDP. Reality is messier.
Identity and access are always drifting. Someone grants temporary access for a project. An admin adds a contractor directly in Google. A manager shares a folder with an external agency. A team spins up a new SaaS app and just clicks Sign in with Google. None of this respects your perfect RBAC structure. It never has.
The problem is not that drift exists. The problem is that every traditional IAM platform hides it.
The truth nobody wants to say out loud
IDPs only show you drift inside the boundaries they control. If an app uses SAML through Okta, you see it. If it uses OAuth through Google, that drift is invisible. If it uses native roles inside Salesforce, that is invisible. If an admin bypasses the IDP entirely, you only discover it during an audit or after something breaks.
The drift was already there. You just didn’t see it.
The industry assumption that never worked
RBAC and groups were designed for a world that barely moves. The original assumption was a static org chart and predictable access lifecycles. Today, real companies change constantly. Reorgs. Contractors. Agencies. Temporary access. Shadow apps. None of this was part of the model. So the model breaks.
Roles were never the issue. The way we implemented them was.
Groups pick up scar tissue
Every environment eventually has thousands of groups. Google, Entra, Okta, Slack, Atlassian. They accumulate purpose and lose meaning. They route email. They grant access. They map to applications from five years ago. They include external users nobody remembers. They drift silently.
Exceptions are normal
Temporary access is the rule, not the exception. Projects happen. Contractors need privileges. Engineers move teams. Someone needs elevated access for a one time incident. Classic RBAC treats every exception like a violation. So teams either ignore drift or mutate groups until nobody understands them.
Security and IT both lose control
Security wants policy enforcement. IT wants to keep things moving. The tools give them no nuance. Fix the role. Ignore the drift. Create another group. None of these approaches understand why drift happened or how long it should last.
Reviews happen at the wrong time
Most access reviews are tied to compliance cycles, not real events. That means reviews are late, painful, and disconnected from actual risk. The better moment to review is when something changes:
- someone changes departments
- someone moves from contractor to FTE
- someone is offboarded
- a risky group gains new external members
This is when drift matters most.
Introducing Drift as a First Class Identity Concept
YeshID assumes drift exists. We track it and help you manage it. Drift is not corruption. Drift is reality.
The Drift Report
YeshID is introducing a new concept: Drift Reports. They show what changed, why, and whether that change is acceptable. They also distinguish intended drift from accidental drift. Acceptable drift is not a security failure. It is a sign that your business is functioning.
You decide what drift is acceptable
With YeshID, you define:
- allowed drift
- temporary drift
- drift that needs approval
- drift that should auto expire
- drift that should trigger review
- drift that is safe and intentional
You stay in control without pretending the world is static.
Time based overrides
Temporary access rolls off automatically. You do not need a new permanent group or role mutation. The access simply expires.
Reviews triggered by real events
Reviews happen when the world changes, not when compliance forces it.
Groups become Access Sets
In YeshID, a group is not just a bucket of users. It becomes structured identity metadata. It maps to Google, Microsoft, Slack, or any SaaS system. It can be dynamic. It can show drift clearly. You see what changed and why.
Separation of provisioning and enforcement
Legacy IAM assumes the provisioning system should also enforce policy. In YeshID, these are separate:
- Access Sets: what a person should have
- Enforcement: the guardrails
- Workflows: how change happens
- Drift controls: how reality is monitored
IT can operate safely. Security can govern without blocking. Everyone sees the same truth.
The future of RBAC is cleaner roles and safer drift
Roles and groups are not going away. They remain the backbone of access. But the old implementation no longer fits how modern companies operate. YeshID is building an identity system that:
- accepts that things change
- treats drift as normal
- gives teams visibility
- keeps roles healthy
- keeps people productive
- keeps the organization safe
This is identity that matches how real companies work. Not how old systems pretended they worked.
AI for IAM admins: stop bolting chat onto dashboards—build a real colleague

I’m Alex, CTO of YeshID. I spend a lot of time with IAM admins, security teams, and CTOs who are trying to keep organizations safe while the identity surface area keeps expanding: more apps, more identities, more automation, more exceptions, and more ways for access to silently drift into dangerous states.
That’s why I’m skeptical of a big chunk of “AI-native IAM” messaging in the market. Too often it means: a chat box on top of the same dashboards you already have.
AI isn’t the problem. The layer it’s applied to is.
The real opportunity is not making IAM easier to query. It’s making IAM easier to operate by giving admins something they rarely get: a true colleague—a senior, deeply technical IAM/Security/SWE partner who can investigate across systems, connect the dots, prioritize what matters, and help you act safely.
That’s what we’re building at YeshID: Rae.
Why dashboards and rules don’t solve the real IAM job
IAM isn’t hard because UIs are bad. It’s hard because the work is cross-system and investigative:
- Access lives across IdP, directory, IGA, cloud IAM, SaaS admin consoles, CI/CD, secrets managers, and logs.
- Entitlements aren’t “one toggle.” They’re chains: group nesting, role inheritance, policy attachments, SCIM mappings, exceptions, break-glass paths, and shadow admin capabilities.
- The cost of mistakes is asymmetric: miss a privilege path and you get breached; remove the wrong access and you take production down.
Dashboards are good at showing what one system believes right now. Rules are good at enforcing known policy deterministically.
But admins spend their time on the work that doesn’t fit neatly into either:
- reconstructing how access happened,
- understanding blast radius and toxic combinations,
- diagnosing drift and broken provisioning,
- validating offboarding completeness,
- and executing changes without outages.
That’s not a “UI problem.” It’s an insight problem.
The AI trap in IAM
There’s a pattern I keep seeing:
- “Ask AI” summarizes what’s already on the screen.
- It demos well.
- It doesn’t change outcomes.
A quick litmus test:
- If the job is deterministic and auditable (“if X then Y”), a rule/workflow is the right tool.
- If the job requires reconstructing causal chains across systems, dealing with missing context, and making tradeoffs under risk, AI can be transformative.
IAM needs AI for the second category—the parts that take senior judgment and, most importantly, time.
The bar for a real AI colleague in IAM
If you hired a senior IAM/Security/SWE, they wouldn’t add value by reading dashboards back to you. They’d add value by:
- knowing where to look across systems,
- correlating identity facts with activity and change history,
- spotting second-order effects (“this change breaks deploys”),
- producing a plan with options, risks, and rollback,
- preventing catastrophic mistakes,
- and doing the tedious legwork fast.
That’s the bar we hold Rae to.
Not “answers.” Not “summaries.” Operational insight.
What Rae does (today) with the evidence you can actually see
I don’t have long-form public case studies yet. But I can show screenshots of Rae doing the kinds of work IAM teams feel every day—work that normally takes hours of stitching context together across tools.
1) Org-wide health synthesis that tells you what matters this week
Instead of another dashboard tile, Rae produces a prioritized view of the identity program’s health and drift—what changed, what’s risky, what’s broken, and what to look at first.
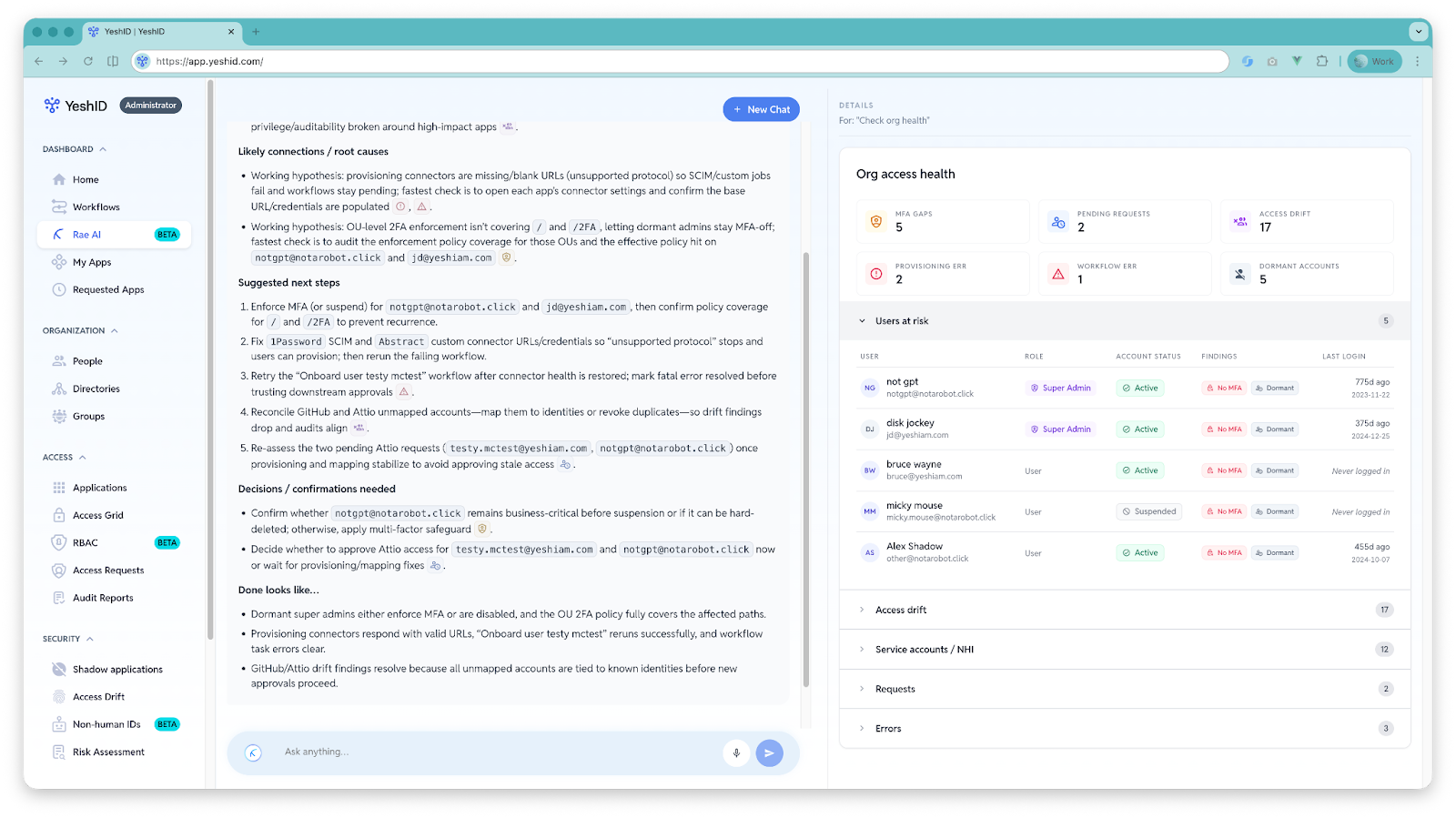
What this is meant to replace is the “I have 20 tabs open and still don’t know where to start” problem.
2) Shadow-IT discovery and access reality, not wishful inventory
Shadow IT isn’t just “apps we don’t like.” It’s unreviewed access paths, unmanaged admin surfaces, and data exposure outside your core controls.
Rae is built to help you identify and reason about:
- what’s actually being used,
- where identities exist outside your expected systems,
- and where access is being granted through side doors.
3) Non-human identity analysis (service accounts, tokens, automation, agents)
Non-human identities are now one of the fastest-growing risk surfaces: service principals, API tokens, CI identities, integrations, ephemeral workloads, and long-lived credentials.
Rae helps you answer questions like:
- Which non-human identities exist, and where?
- Which ones are over-privileged relative to their observed use?
- Which ones are stale, orphaned, or quietly “immortal”?
- Where are the credential and trust boundaries actually weak?
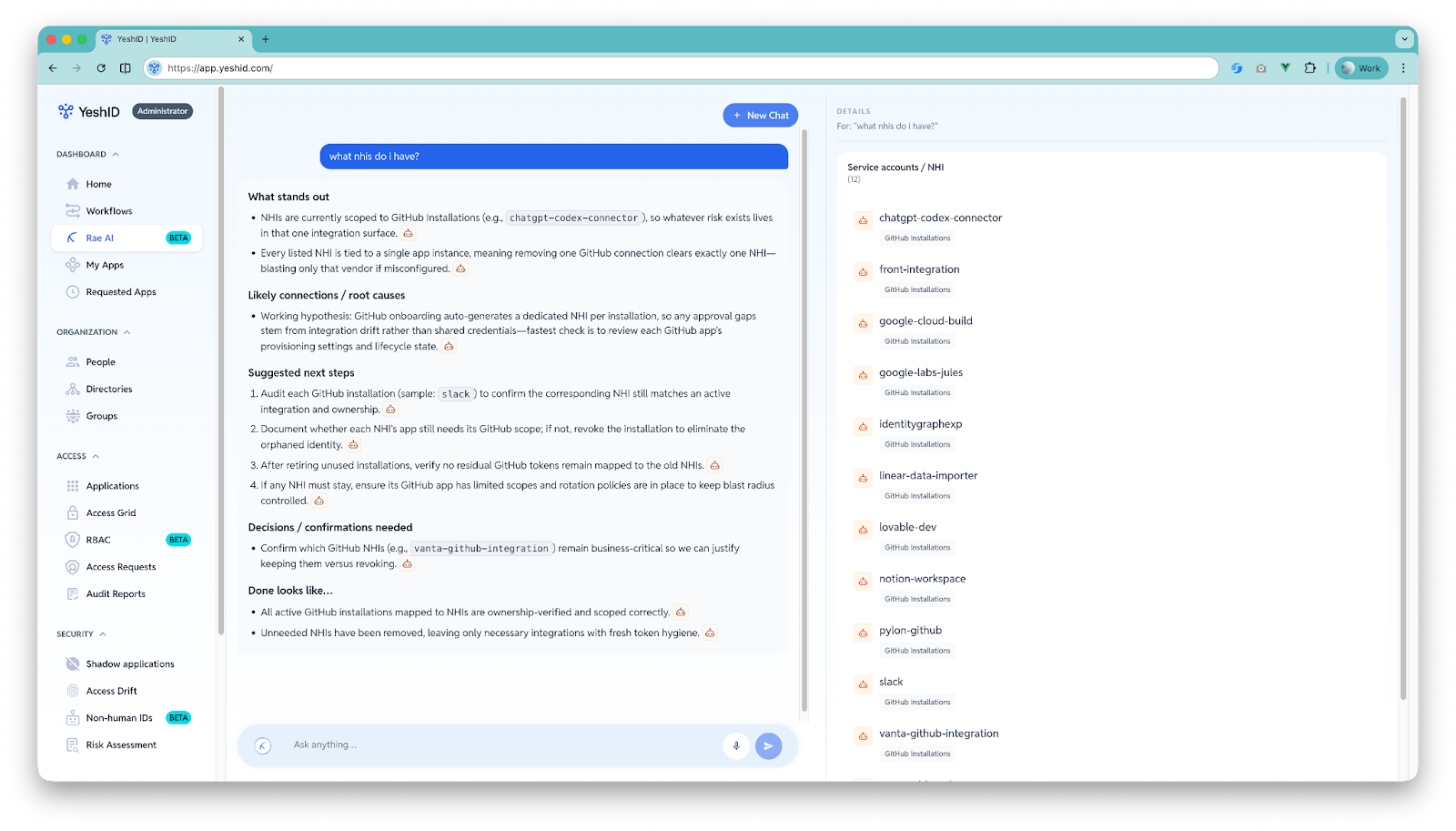
4) Workflow building that turns insight into repeatable operations
In IAM, one-off investigations don’t compound unless they become repeatable workflows: approvals, validations, structured work items, execution steps, documentation.
Rae helps you take “here’s what we found” and convert it into “here’s how we handle this every time.”
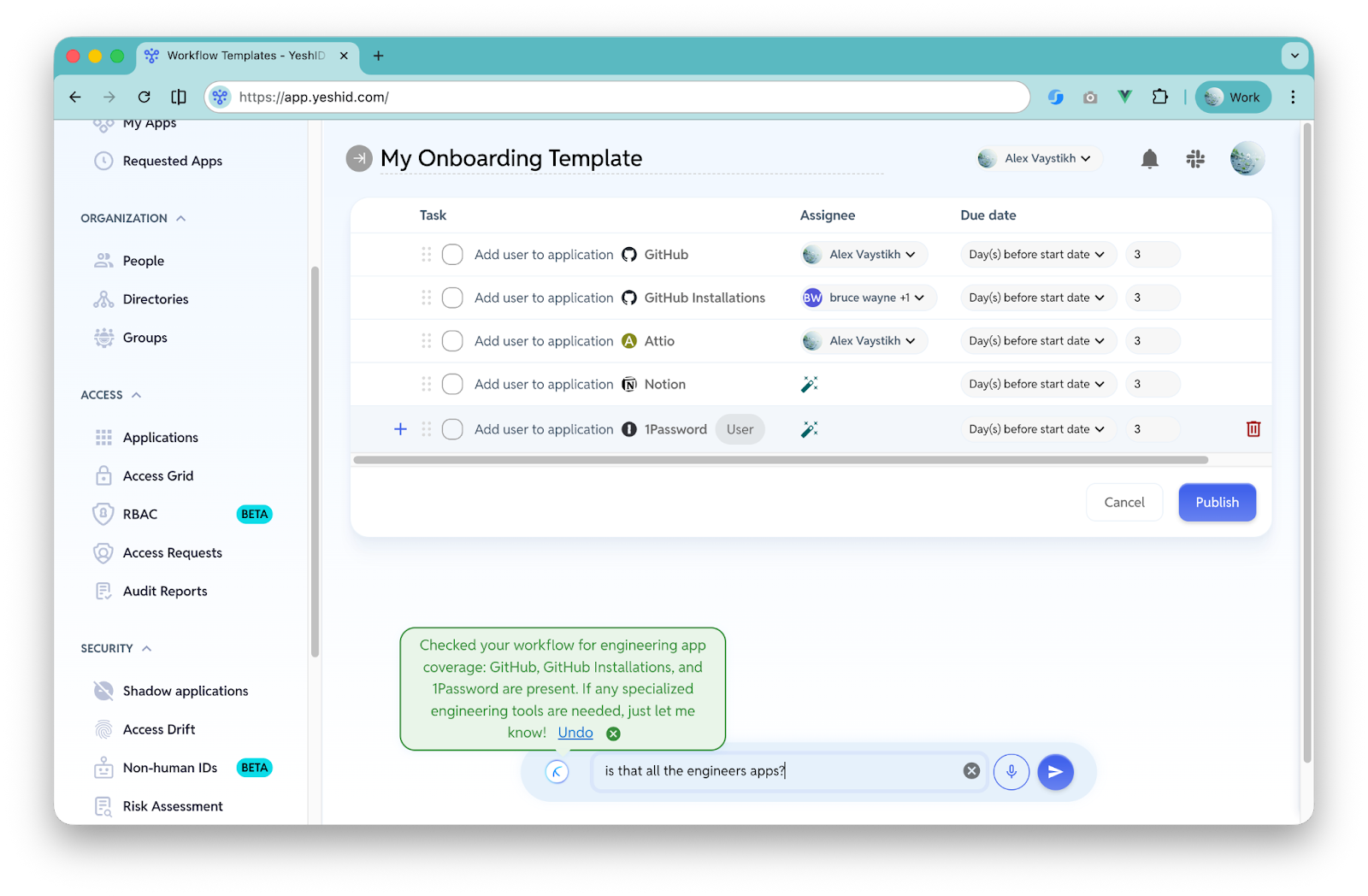
5) Integration building with code for the long tail (especially non‑SCIM apps)
Every IAM team hits the same wall: the long tail of apps that don’t support SCIM cleanly (or at all), plus internal tools and custom platforms.
Rae can write integration code to connect those systems—making it practical to:
- automate provisioning/deprovisioning,
- reconcile entitlements,
- perform targeted access changes,
- and reduce the backlog of “we’ll integrate it someday.”
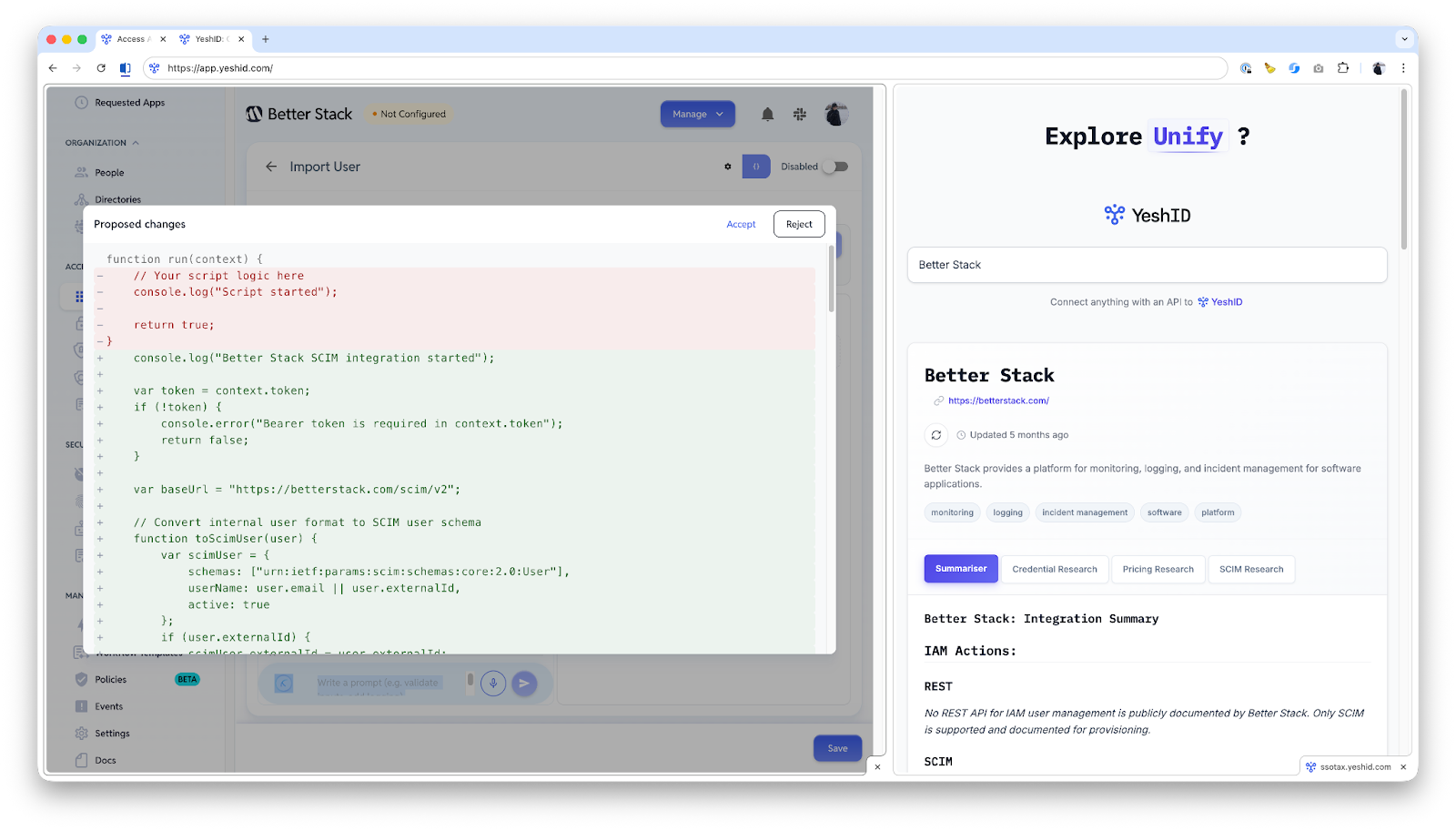
This is not “AI for vibes.” It’s engineering leverage applied directly to the most stubborn part of IAM operations.
“Acts” without autopilot
IAM is too high-stakes for “just let the agent do it.”
A real colleague doesn’t blindly execute. They:
- investigate,
- propose,
- highlight risks and dependencies,
- and help operationalize safely through controlled workflows and review.
Rae is designed to take work off the admin’s plate without taking away responsibility—and to reduce the most expensive failure mode in IAM: a fast, confident mistake.
How to evaluate “AI-native” IAM in 5 questions
Here’s a practical filter:
- Does it create new understanding, or just rephrase existing screens?
- Can it explain “how did this access happen?” with a traceable chain of evidence?
- Does it prioritize what matters, or just generate more output?
- Can it operationalize (workflows, validations, structured execution), not just answer?
- Does it reduce the long-tail integration tax—or does it assume perfect connectors and SCIM everywhere?
If the product can’t do those things, “AI-native” is likely just UI polish.
The point of Rae
Rae is built to be the colleague IAM teams have always needed: deeply technical, cross-system, tireless about investigation, and practical about turning findings into action.
Not to replace how you think—but to give you time back to do what no AI can do for you: decide what matters for your organization, set the tradeoffs, and drive the program forward.
Identity Architecture for the Modern SaaS Stack

1. Executive Summary: The Identity Decision Has Changed
For many years, workforce identity architecture was straightforward. A company maintained a single directory, connected it to a single identity provider (IDP), and integrated most critical applications using SAML (authentication) and SCIM (provisioning). Authentication, provisioning, and access control were largely centralized.
That model no longer reflects reality.
Modern companies operate across multiple identity surfaces. Employees authenticate using different protocols depending on the application. Teams adopt tools independently. Applications manage their own internal permissions. AI systems and integrations exchange credentials without human involvement. As a result, identity is no longer a single control plane—it is a distributed system.
This creates a common point of confusion: organizations believe that selecting the “right” IDP will restore central control. In practice, no single IDP can govern the entire environment. The architectural decision is not which vendor to use, but how to design for consistency across heterogeneous identity systems.
The core question for leadership is no longer:
“Which IDP should we standardize on?”
It is:
“Where do authentication, authorization, lifecycle automation, and governance each belong—and how do they work together?”
2. Identity Surfaces in a Modern Environment
Modern identity architectures consist of several distinct but overlapping surfaces, each optimized for a different purpose.
Enterprise IDPs (e.g. Ping, Okta, JumpCloud)
Enterprise IDPs are designed primarily as authentication control planes. They excel at enforcing login security through MFA, conditional access, device posture, and centralized credential management.
They integrate with applications primarily via:
- SAML
- OIDC
- SCIM (where supported)
When applications fully support these standards, enterprise IDPs provide strong and reliable control. However, their scope is inherently limited to the applications that implement these protocols correctly and completely.
Enterprise-Social IDPs (Microsoft and Google)
Microsoft Entra ID and Google Workspace Identity serve as both directories and OAuth/OIDC providers. In practice, they function as enterprise-social IDPs.
Modern SaaS vendors prioritize these platforms because OAuth:
- Is faster and easier to implement than SAML
- Works equally well for users, services, and integrations
- Aligns with API-first and AI-enabled products
As a result, many new applications support “Sign in with Microsoft” or “Sign in with Google” as a default, sometimes long before they support SAML or SCIM.
Application-Native Identity and Authorization
Every application maintains its own internal authorization model:
- Roles (Admin, Editor, Viewer, etc.)
- Permissions and scopes
- Teams, workspaces, or org structures
This layer determines what users can actually do. It is also the least standardized and the least visible from centralized identity systems.
The Implication
Identity today is not one system. It is a mesh of authentication and authorization layers, each with different capabilities and constraints. Any architecture that assumes a single plane of control will have blind spots.
3. Authentication vs Authorization: The Core Distinction
A key architectural mistake is conflating authentication and authorization.
Authentication answers the question:
“Who are you, and how do you prove it?”
Authorization answers the question:
“What are you allowed to do once inside the system?”
Enterprise IDPs are optimized for authentication. They ensure that users log in securely. They are not systems of record for permissions, roles, or entitlements across applications.
Even when SAML is used:
- Roles are often assigned inside the application
- Permissions evolve independently over time
- OAuth tokens and API keys bypass SSO entirely
This means that centralizing login does not centralize access control. Authorization state remains fragmented across applications, regardless of how consistent authentication appears.
4. Architectural Options and Their Tradeoffs
Option 1: SAML-First Enterprise IDP Architecture
In this model, the organization attempts to route all applications through a SAML-centric enterprise IDP.
Advantages
- Strong, centralized authentication controls
- Familiar governance model for IT and security teams
- Clear login enforcement
Limitations
- Many modern applications are OAuth-first and SAML-later (or never)
- SCIM support is inconsistent and often incomplete
- Authorization still lives inside applications
- Tool adoption slows as teams wait for SAML enablement
This approach often creates a false sense of coverage: authentication is controlled, but authorization visibility remains limited.
Option 2: OAuth-First Enterprise-Social Architecture
Here, applications authenticate directly through Microsoft or Google using OAuth/OIDC.
Advantages
- Low friction for users and teams
- Broad compatibility with modern SaaS
- Faster adoption of new tools
Limitations
- Lifecycle events (onboarding/offboarding) are decentralized
- Shadow onboarding increases
- Access governance becomes reactive rather than policy-driven
Without additional controls, this model trades speed for reduced visibility.
Option 3: Hybrid Architecture (The Common Reality)
Most organizations operate a hybrid model:
- Enterprise IDP for some SAML-based apps
- Microsoft or Google OAuth for many others
- Application-native permissions everywhere
This reflects reality, but it introduces fragmentation:
- Policies are inconsistently enforced
- Offboarding is error-prone
- Audit evidence is scattered
Hybrid architectures require explicit design choices to manage complexity.
5. The SSO and SCIM Tax
Attempting to force consistency by standardizing on SAML and SCIM introduces a significant cost, often referred to as the SSO tax.
This tax includes:
- Paying for enterprise SaaS tiers solely to unlock SAML or SCIM
- Purchasing IDP governance add-ons
- Engineering time to integrate and maintain connectors
- Operational overhead to manage partial implementations
Even after paying this cost:
- Coverage remains incomplete
- OAuth-based apps and integrations remain outside the model
- Internal permissions are still not fully visible
From a CTO perspective, the SSO tax is not just financial—it affects velocity, flexibility, and architectural clarity.
6. The Emerging Identity Architecture Pattern
Modern organizations increasingly separate identity responsibilities across layers:
Authentication Control Plane
- Enterprise IDPs (Okta, JumpCloud, Entra)
- Focused on secure login and access conditions
Enterprise-Social OAuth
- Microsoft and Google as primary adoption paths for SaaS
- Optimized for velocity and compatibility
Applications
- The true source of authorization state
Orchestration and Governance Layer
- Normalizes identities across systems
- Automates lifecycle events across auth types
- Enforces policy consistently
- Provides audit-grade visibility
This layered approach acknowledges that fragmentation is structural, not accidental.
Conclusion
The modern identity challenge is not choosing the right IDP. It is designing an architecture that accepts multiple identity surfaces while maintaining consistency, security, and operational control.
Organizations that succeed do not eliminate fragmentation—they manage it deliberately. They separate authentication from authorization, avoid paying unnecessary SSO tax, and invest in orchestration where centralization is no longer possible.
This is the identity architecture reality modern CTOs must design for.
Release note December 2025

What’s new in December 2025: faster access control in your IAM platform
December focused on reducing admin work in YeshID’s Identity and Access Management (IAM) platform—especially for IT & Security leaders at mid-sized businesses. The theme: safer automation, clearer access visibility, and fewer broken flows.
TL;DR
- ✅ Fix access drift faster with better Role-Based Access Control (RBAC) change previews and remediation workflows (Beta).
- 🧩 Stage workflows before they run so you can review changes and start them in bulk when you’re ready.
- 🔎 Improve access visibility with stronger drift views and better directory group membership handling.
- 🔗 Connect and manage more apps with new integrations (HubSpot, Zoom, Ramp, Asana) and improved SCIM support.
- 🧼 Smoother day-to-day UX: more reliable filters, faster selectors, and clearer workflow emails.
RBAC Policies — preview changes and fix drift faster (Beta)
RBAC Policy updates are now easier to manage in one place. When you edit a policy, changes are batched and saved together, with a preview of the new drift those changes would create.
You can also remediate drift per application using a Fix Drift flow that creates a change request workflow with the right add/remove steps. That makes it faster to turn drift findings into action.
How to try it
- (Access → RBAC) edit a policy, then review and save changes.
- In drift reporting, open an application and choose Fix Drift.
Staged workflows & triggers — safer automation you control
Workflows can now be created in a Staged state, so they don’t run automatically while you’re testing or reviewing changes. You can also bulk select workflows to start staged ones or delete test runs quickly.
Workflows now show what triggered them, so it’s easier to understand why they exist during reviews and audits.
How to try it
- Enable staging when creating a trigger, then review the staged workflows before starting them.
- (Workflows) filter by Staged and use bulk actions.
Security visibility — clearer drift and non-human identity coverage
Access drift views were expanded and cleaned up so you can review drift with more context and fewer confusing edge cases. Application account views can now surface related RBAC Policy context, making access reviews faster.
Non-Human Identities (NHI)—like bots and service accounts—are also easier to review across more sources, and directory group membership handling is more complete when nested groups are used.
Integrations — more apps with stronger provisioning options
You can now connect and manage more of your stack from YeshID:
- New/expanded integrations: HubSpot, Zoom, Ramp, and Asana.
- Improved support for Salesforce provisioning via System for Cross-domain Identity Management (SCIM).
We also improved the connection experience with clearer capability labels and fewer add‑application flow issues. For large Microsoft Teams environments, picking teams and channels now scales better.
Everyday admin UX — smoother filters, selectors, and emails
Several fixes landed to remove friction in common admin workflows. Due Date filtering in task lists is now accurate, filter logic is more reliable, and selection/search controls perform better in larger orgs.
Workflow email tasks are clearer too: admins can send a custom access email even when adding the task to a running workflow, and Google Workspace login guidance now points to accounts.google.com.
Admin tips
- Start new triggers or RBAC changes in Staged mode first, then bulk-start workflows once the preview looks right.
Availability & rollout notes
- RBAC Policy and drift features are marked Beta in the product and require the RBAC/Groups experience to be enabled.
- YeshID’s AI assistant (Rae) is restricted to admin users.
December’s updates are designed to help IT and Security teams keep access accurate with less manual work—while staying in control of when automation runs.
Tell us what would save your team the most time next!
Agentic AI for IAM, Built for Trust

Why AI Agents in IAM Are a Security Breakthrough (and a Security Risk) — and How YeshID Makes Them Trustworthy
Identity and Access Management (IAM) is where enterprise AI gets real.
An AI agent that can answer “why does this person have access?” and then actually fix it—remove an over-privileged role, expire time-bound access, or open the right approval workflow—removes hours of manual work from every joiner/mover/leaver and every audit. It also touches the most sensitive control plane in the company.
That’s why “generic AI assistants” are a non-starter for IAM. The hard problem isn’t whether an LLM can write a nice response. The hard problem is whether an agent can safely operate with:
- untrusted inputs (Slack messages, tickets, email),
- sensitive identity data (entitlements, group membership, access history), and
- the ability to change access.
This is exactly the failure mode security researchers are worried about: prompt injection.
Prompt injection is the reason “AI + IAM” needs new architecture
Prompt injection is a fundamental, unsolved weakness in LLMs: untrusted strings that get into an agent’s context can cause it to ignore developer instructions and take unauthorized actions.
Meta’s “Email-Bot” example illustrates the risk clearly: if an attacker can get a malicious instruction into an email, and the agent reads it, the agent can be hijacked into exfiltrating private data or taking unwanted actions.
Now translate that to IAM:
- The “email” becomes a Slack message, a ticket, or a request form.
- The “private inbox” becomes your directory, entitlements, audit logs, and policies.
- The “send email tool” becomes “add user to group,” “grant role,” “create service principal,” or “rotate keys.”
In IAM, the agent isn’t just summarizing. It’s holding the keys to the kingdom.
The practical framework: Agents Rule of Two
Meta’s proposed framework (inspired by Chromium policy thinking and the “lethal trifecta” concept) is simple and intentionally practical: until we can reliably detect and refuse prompt injection, an agent should satisfy no more than two of three properties within a single session.
Those three properties are:
- [A] Process untrustworthy inputs
- [B] Access sensitive systems or private data
- [C] Change state or communicate externally
If you need all three to complete a request, the guidance is explicit: don’t let the agent run autonomously without a new session boundary and supervision (human approval or another reliable validation method).
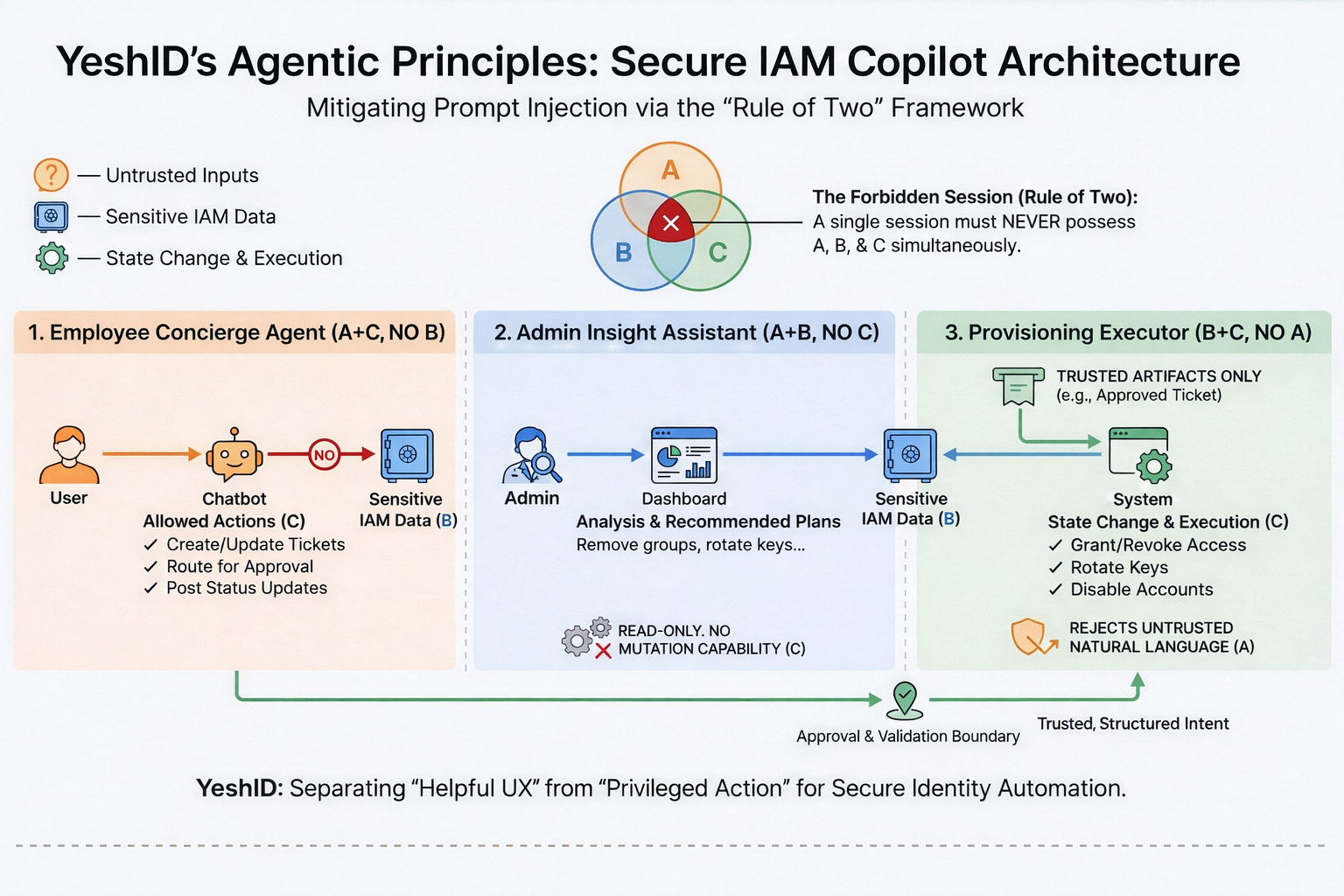
Why this matters more in IAM than almost anywhere else
Most “AI agent” demos outside security involve low-stakes failures: wrong travel suggestions, a missed calendar detail, a sloppy summary.
In IAM, the worst-case failure is catastrophic: privilege escalation, persistence via new credentials, or automated lateral movement—triggered by nothing more than a cleverly crafted request.
So the Rule of Two becomes a design constraint, not a theoretical guideline. It forces you to engineer away the exploit chain: A → B → C.
What an IAM agent looks like when it respects Rule of Two
A useful way to think about an “IAM Copilot” is not as one agent, but as three operating modes (or three cooperating agents), each deliberately missing one of the “dangerous” powers.
1) Employee concierge: (A + C), not B
This is the employee-facing helper in Slack/Teams or a portal.
- It can read untrusted requests (“please give me X”) and messy context (A).
- It can communicate and coordinate: open tickets, ask follow-ups, route to approvers, post status (C).
- It cannot query sensitive IAM data broadly (no B).
This is how you get fast employee UX without turning “chat” into “privilege grant.”
YeshID already supports access requests directly in Slack or Teams, including in-line approvals and time-based access that expires automatically.
2) Admin insight agent: (A + B), not C
This is the “answer the hard question” mode for admins and security teams.
- It can read incident notes/tickets (A).
- It can consult sensitive identity and access data (B).
- It cannot take action (no C).
This is a powerful safety posture: prompt injection might distort reasoning, but it can’t immediately translate into an automated entitlement change.
3) Provisioning executor: (B + C), not A
This is the “do it” engine.
- It can read directory/app state (B).
- It can change access (C).
- It only accepts trusted, structured inputs (no A): approved workflows, policy decisions, validated change plans.
This pattern matches the core Rule of Two idea: you can build incredibly capable systems, but you must prevent any single session from being simultaneously exposed to untrusted inputs, sensitive access, and autonomous action.
Where YeshID is different: we built the infrastructure layer that makes “governed agentic IAM” real
A question we hear often is: “Isn’t everyone just adding a chatbot?”
YeshID’s answer is: the model is not the product. The product is the authoritative IAM control plane that makes safe automation possible.
YeshID is built as “an authoritative IAM infrastructure layer” with a continuously updated source of truth for identities, applications, policies, roles, entitlements, and access changes. And YeshID extends your IdP with visibility, policy, and automation across every human, app, and non-human identity.
That foundation is what enables Rae.
Meet Rae: an IAM-native agent, not a generic assistant
Rae is YeshID’s agentic AI purpose-built for IAM—described as “a senior IAM engineer embedded directly into YeshID.” The key is what Rae is built on:
- Authoritative context (not best guesses): Rae operates on up-to-date identity and policy data from the system of record.
- Explainability anchored to real controls: Rae is designed to explain reasoning and “points back to the underlying data and policies.”
- Governed actions: Rae can take actions within guardrails defined by policies and approvals, and actions are intended to be auditable and explainable.
In other words: Rae isn’t useful because it can chat. Rae is useful because it can operate safely inside a governed IAM system.
What Rae does for employees and admins (in practice)
For employees: fast access without security theater
Employees want one thing: get access quickly, with clarity.
With YeshID, employees can request access in Slack/Teams; managers approve in-line; time-based access is supported and expires automatically.
That’s the employee experience layer. Rae adds the intelligence layer: explain what access means, detect risky patterns, and keep the process aligned to policy—without turning every request into an ad hoc admin intervention.
For admins and security teams: turn IAM from “dashboard work” into decisions and action
Rae is described as doing four things that map directly to modern IAM pain:
- Answer IAM questions in context (and explain why) Examples include: why a user has access, which policies grant an entitlement, and what the impact is if a role is compromised.
- Detect risk and drift proactively Rae looks for unsanctioned apps, over-privileged users/roles, policy drift/misconfiguration, and dormant/risky identities—then explains what changed and what to do.
- Take governed IAM actions Rae can flag/quarantine risky access, open workflows for review, provision/deprovision access, and enforce policy standards—within the guardrails defined in YeshID.
- Turn IAM into a security signal Rae correlates identity data with security signals so investigations can be grounded in “who had access to what, when, and why.”
This is the core shift: IAM becomes an operational system, not a set of spreadsheets and alerts.
Why this is a defensible technical wedge
Most companies trying to add AI into IAM start at the UI layer: “chat with your directory.” That’s easy to demo and hard to trust.
The durable wedge is deeper:
1) Authoritative identity context becomes the agent’s “ground truth”
YeshID’s positioning is explicit: continuously updated source of truth across identities, apps, policies, roles, entitlements, and access changes. That means the AI is not improvising. It’s operating on governed data.
2) Governed action is the only path from insight → outcome
The Rule of Two teaches a practical lesson: if you want agents to take action safely, you must design the system so the agent doesn’t combine untrusted inputs + sensitive access + autonomous action in one session.
YeshID’s Rae is described as being “built for environments where trust, auditability, and explainability matter,” and capable of governed actions aligned to YeshID controls.
3) Real-world IAM requires depth: apps, directories, workflows, and lifecycle automation
YeshID’s platform emphasizes lifecycle management, automation from source-of-truth systems, and provisioning/deprovisioning across apps (SCIM, REST, and even manual). That integration depth is what turns an agent from “answering questions” into “operating the system.”
The bigger point: AI agents will reshape IAM—but only the governed ones will ship
Agentic AI is moving toward plug-and-play tool calling, which increases both capability and risk. Meta’s framework is a reminder that the only safe path is architectural: constrain what an agent can do in one session, require supervision when needed, and build defense in depth (including least privilege).
YeshID’s bet is that the winning IAM agent won’t be the one with the cleverest prompt. It’ll be the one built on:
- authoritative identity context,
- clear policy,
- governed action,
- and auditability from day one.
That’s what makes Rae—and YeshID’s approach to agentic IAM—structurally different.
Introducing Rae: Agentic AI Built for Identity and Access Management

Identity and Access Management is no longer a back office function. It is a primary security control, an audit requirement, and a daily operational challenge.
At the same time, IAM teams are being asked to manage more identities, more applications, more risk, and more scrutiny with fewer experienced practitioners.
That gap is exactly why we built Rae.
The Reality Facing IAM Teams Today
Modern organizations are dealing with an identity environment that changes constantly.
Human users, service accounts, APIs, and AI agents all require access. New SaaS and cloud applications appear weekly. Regulations and audits demand clear answers about who has access to what and why. Identity-based threats continue to rise.
Most IAM tools are still reactive. They surface alerts and dashboards, but they rely on human expertise to interpret risk, write policies, and take action. That expertise is increasingly hard to find and harder to scale.
IAM teams are overloaded, not under-informed.
Why YeshID Took a Different Approach
YeshID was built as an authoritative IAM infrastructure layer.
We maintain a continuously updated source of truth for identities, applications, policies, roles, entitlements, and access changes. That foundation is what allows IAM to be managed as a system, not a collection of disconnected tools.
Rae is built natively on top of that foundation.
Because Rae operates on authoritative identity data, it has real context. It understands your environment as it exists today, not as a static model or best guess. That context is what makes trusted automation possible.
Meet Rae
Rae is an intelligent, agentic AI purpose-built for Identity and Access Management.

Think of Rae as a senior IAM engineer embedded directly into YeshID. Rae advises, monitors, explains, and takes action across the IAM lifecycle.
This is not a generic AI assistant adapted for security. Rae was designed specifically for IAM operations, governance, and security teams.
Rae can assist interactively, work proactively in the background, and perform governed actions based on your policies and approvals.
What Rae Does in Practice
Answers IAM Questions in Context
Rae understands your identities, applications, and policies. You can ask questions like:
- Why does this user have access to this application?
- Which policies grant this entitlement?
- What is the impact if this role is compromised?
Rae does not just answer. It explains its reasoning and points back to the underlying data and policies.
Detects Risk and Drift Proactively
Rae continuously analyzes your IAM environment to identify issues such as:
- Newly discovered or unsanctioned applications
- Over-privileged users or roles
- Policy drift and misconfigurations
- Dormant or risky identities
Instead of reacting to alerts, teams get clear explanations of what changed, why it matters, and what to do next.
Takes Governed IAM Actions
Rae can be configured to act within the guardrails you define.
That can include flagging or quarantining risky access, opening workflows for review, provisioning or deprovisioning access, or enforcing policy standards across applications.
Every action is auditable, explainable, and aligned with YeshID controls.
Turns IAM Into a Security Signal
Rae correlates identity data with security signals to surface identity-driven risk.
Security teams can see threat summaries tied directly to users, applications, and policies. IAM becomes an active participant in security investigations, not just a control to check after the fact.
Teaches and Enables IAM Teams
Rae also acts as a mentor.
It helps teams understand IAM best practices, explains policy trade-offs, and generates policy examples tailored to their environment. This reduces reliance on scarce IAM expertise and helps teams mature faster.
How Rae Is Different
Most AI tools in security are advisory at best. They lack real system context and cannot be trusted to act.
Rae is different because it is IAM-native.
It operates on authoritative identity data, not assumptions. It is designed for action, not just insight. And it is built for environments where trust, auditability, and explainability matter.
Rae is not a chatbot bolted onto IAM. It is an IAM-native agent designed for operational trust.
Who Rae Is Built For
Rae is designed for mid-market and enterprise organizations that are scaling SaaS, cloud, and AI workloads.
It supports security, IAM, and IT operations teams, especially in regulated industries where access governance is critical.
The Business Impact
Organizations using Rae can expect to:
- Reduce identity risk by detecting issues earlier
- Increase efficiency through automation of repetitive tasks
- Close talent gaps by embedding senior-level IAM expertise
- Improve security posture by treating identity as a first-class signal
- Scale IAM operations without linear headcount growth
From System of Record to System of Intelligence
IAM has traditionally been a system of record.
With Rae, it becomes a system of intelligence.
Rae helps organizations move from reactive identity management to proactive identity decision-making, grounded in real data and executed with confidence.
Rae by YeshID is agentic AI for Identity and Access Management, built for trust, scale, and real-world operations.
The Truth: IDPs Only Govern the Apps They Touch (And That’s Not Enough)

Most companies that choose JumpCloud, Okta, or Microsoft Entra believe they have “identity covered.” They picture a single login, a single control plane, and a single place to manage access. That used to be true when every important application supported SAML and SCIM. But that is not the world we live in anymore.
Modern companies now authenticate, approve access, and exchange data across multiple identity surfaces. And the core IDP no longer sees — or governs — most of the stack.
This is why IT and Security teams increasingly add an Identity Orchestration layer like YeshID on top of their IDP. Not to replace JumpCloud or Okta, but to fill the gaps those platforms were never designed to address.
This is the new identity reality.
The Modern Stack No Longer Has One IDP — It Has Three to Five
Five years ago, everything mission-critical ran through a single IDP. Today, an average mid-market company uses multiple login paths:
1. JumpCloud or Okta for SAML apps
Great for enforcing MFA, strong authentication, device trust, and SSO — but only works for the apps that actually support SAML.
2. Google and Microsoft for “social login”
This is how most teams adopt new tools. Marketing, Product, Finance, HR — they all click “Sign in with Google.” New AI companies default to OAuth, not SAML. Startups launching in 2024–2026 often never implement SAML at all.
3. Built-in IDPs for platform ecosystems
AWS, GCP, Atlassian, Salesforce, and others often bring their own identity layers for plugins and internal modules.
4. Apps without any federated login
Contractor systems, point solutions, older tools, niche SaaS — these stay username/password and live entirely outside the IDP perimeter.
Result:
Your IDP governs only the slice of your world that happens to use SAML + SCIM. And for most companies, that’s about 30 percent of the stack.
Everything else is invisible.
Authentication ≠ Access Management
JumpCloud and Okta were built as authentication control planes — not as systems of record for every permission, role, or OAuth grant happening across your environment.
They excel at:
- MFA
- Conditional access
- SSO
- Device trust
- Strong authentication workflows
But they do not manage:
- OAuth-based apps
- “Sign in with Google/Microsoft” adoption (shadow onboarding)
- Internal permission changes inside each app
- App-to-app OAuth connections (MCP, AI agents, integrations)
- SaaS sprawl from non-IT teams
- Drift in permissions after the initial provisioning
- Evidence and audit of who actually has what access across all systems
You can force everything to become a SAML app — but that means:
- Paying the SSO tax everywhere
- Slowing down teams
- Blocking adoption of tools that do not support SAML
- Losing the benefits of modern OAuth ecosystems
- Frustrating business units that want autonomy
Most companies decide not to fight this battle.
So the gap grows.
The Core Problem: Your IDP Only Governs the Apps It Touches
Think about a policy like:
“Only engineers should have access to production tools.”
If 30 percent of those tools authenticate through JumpCloud or Okta and 70 percent authenticate some other way, the IDP can only enforce policy on the 30 percent it sees.
This is the real issue.
You cannot govern what you cannot see. YeshID exists specifically to solve this gap.
Why Identity Orchestration Exists Now (And Didn’t Five Years Ago)
The stack changed faster than the IDPs did.
- OAuth exploded because it is easier for developers, AI tools, and integrations.
- Business units adopt tools directly with social login.
- Most SaaS vendors now ship OAuth first, SAML later, and SCIM maybe never.
- AI tools connect app-to-app through OAuth scopes without human involvement.
- “Strong authentication” layers (Okta, JumpCloud, Entra) remain siloed from the rest of the permissions world.
Identity used to be clean and centralized. Now it is distributed and fragmented.
Identity Orchestration is not a replacement for the IDP — it is the glue.
What an Orchestration Layer Like YeshID Adds
A single place to define access policy across all apps
Not just the apps that support SAML. Not just the ones connected to JumpCloud. Everything.
Visibility across all identity surfaces
- SAML
- OAuth (Google, Microsoft)
- Native app permissions
- AWS/Azure/GCP
- AI agents
- App-to-app token grants
Automated provisioning and deprovisioning for every app
Whether it is SAML, SCIM, OAuth, or API-only.
JumpCloud and Okta provision only what they have connectors for. YeshID provisions whatever the stack actually contains.
Drift detection
If a permission is added directly in Salesforce, Github, Notion, or any OAuth-based app, YeshID detects it and compares it to your policy.
IDPs cannot do this because they do not inspect the app’s internal roles.
Access reviews that actually cover the whole environment
You cannot review what you cannot see. This is where audits fall down when relying only on an IDP.
Workflow and lifecycle automation across different identity systems
Onboarding/offboarding often spans SAML apps, OAuth apps, manual apps, and platform IDPs. YeshID coordinates the entire flow.
AI-native integrations
We connect to applications through APIs — not just standards — so you get coverage without needing vendors to implement SAML/SCIM.
Budget Reality: Why This Does Not Duplicate Cost
Okta and JumpCloud both charge:
- A base cost for authentication
- A premium upcharge for governance, automation, and IGA
Most teams pay for the authentication piece but never fully adopt the governance modules because coverage is limited to SAML-only apps.
Identity Orchestration replaces that part — not the core IDP.
This lets teams:
- Keep JumpCloud or Okta as their strong authentication layer
- Avoid paying for SAML upgrades they don’t need
- Get full-stack governance and automation for every app
- Standardize policy across all login types
- Reduce operational burden on IT
- Improve audit readiness
It is not duplication — it is proper separation of responsibility.
The Simple Mental Model for Identity
JumpCloud/Okta/Ping = Authentication Control Plane
Great for: enforcing MFA, strong login, SSO, device trust.
YeshID = Identity Orchestration & Access Governance
Built for: visibility, provisioning, policy, automation, and reviews across all identity surfaces.
They are complementary layers.
One keeps the front door secure. The other governs what happens inside the building.
Why Companies Adopt YeshID Even When They Already Have an IDP
Here is what we hear from IT Ops and Security teams:
- “Most of our new apps don’t support SAML.”
- “Half our access is happening through Google sign-in and we have no visibility.”
- “Our IDP can’t be our IAM because it can’t touch half the environment.”
- “We need to automate onboarding across apps that don’t have SCIM.”
- “We need policy-based access reviews across everything, not just the SAML slice.”
- “We want governance without forcing the whole company to upgrade to enterprise SAML licenses.”
This is the new normal. Identity changed. IDPs did not. YeshID fills the gap.
Summary
If your company has:
- Multiple ways employees authenticate
- A mix of SAML and OAuth apps
- Teams adopting tools without IT
- Apps that do not support SCIM
- Permissions managed inside each app
- APIs that enable deep automation
- AI tools connecting systems on their own
Then your IDP cannot be your IAM.
IDPs like JumpCloud and Okta remain the strong authentication layer. YeshID becomes the layer that understands who should have access, who actually has access, and how to orchestrate that access across the entire stack. This is why the two layers go together.
How to Talk to Your CFO About Identity & Access — A Practical Budget Script

Mid-market CFOs are pragmatic. They care about clean controls, predictable spend, and not getting blindsided by risk. They do not care about identity jargon, security purism, or why SAML makes you want to cry.
The good news is that identity and access actually map cleanly to the things CFOs already obsess over: cost control, operational efficiency, audit readiness, and business continuity. You just have to frame it in their language.
This is your practical script.
Start With the Business Reason, Not the Tech
CFOs don’t want to hear about provisioning APIs or OAuth token behavior. Start here:
“We have people gaining access, losing access, and changing access every single week. Right now, we track a lot of it manually. That increases risk, slows teams down, and creates audit problems later. Identity and Access is how we keep this manageable, provable, and efficient.”
This translates to:
- We have a moving system of permissions.
- Manual equals expensive.
- Lack of control equals financial risk.
Put the Pain in Real Terms
Identity isn’t an abstract idea. It shows up in real scenarios your CFO recognizes.
Examples they care about:
- Offboarding gaps (contractors, interns, reorg churn) leading to unnecessary app licenses or unrevoked access.
- Shadow IT spend from apps purchased outside procurement.
- Audit remediation hours and external consulting costs because access wasn’t clearly documented.
- Operational drag when IT is stuck fulfilling tickets instead of projects.
Make it practical:
“Every time we have to chase down what someone has access to, it costs time. Every missed offboarding costs money. Every audit gap becomes a fire drill. Identity tools solve these three things.”
Anchor the Problem in Dollars, Not Feelings
This is where CFO attention sharpens.
Give them the simple math:
- Time cost: “We spend X hours per month doing manual provisioning, access reviews, and chasing approvals.”
- License waste: “We routinely uncover unused accounts in SaaS tools. Even small leaks add up annually.”
- Audit cost: “Every unclear access path adds hours to audits. Auditors bill hourly, not emotionally.”
- Risk cost: “One access mistake can cost more than the entire year of good identity hygiene.”
You’re showing the CFO something they love: avoidable spend.
Introduce the Goal: Lean, Auditable Identity
The CFO doesn’t want a massive identity overhaul.
They want:
- predictable access
- clean onboarding/offboarding
- reduced waste
- provable controls
- fewer surprises
Introduce it like this:
“Our goal isn’t to rebuild our entire IAM stack. It’s to get predictable, automated access controls for the systems we use every day. That way we lower risk, reduce manual work, and get audit-ready logs without adding more process.”
This frames identity as an operational efficiency lever, not a cost center.
Position YeshID Clearly and Simply
CFOs want clarity. Use short statements.
“YeshID automates lifecycle management, reduces access drift, cleans up groups and permissions, and gives us audit-ready logs across our SaaS stack.”
“It works with what we already have — Google Workspace, Microsoft, Slack, HRIS — without requiring us to buy SSO upgrades.”
“It cuts down on wasted SaaS licenses because we can actually see who uses what.”
This tells the CFO:
- no massive rip-and-replace
- no surprise SSO tax
- immediate operational value
Explain the Alternative (This Part Matters)
Every CFO wants to know: what if we do nothing? Answer directly.
If we don’t invest in identity:
- IT will continue doing manual access work
- We’ll keep paying for unused SaaS licenses
- We’ll go into audit season without clean evidence
- We have a higher chance of permission drift and access findings
- Small issues will keep turning into expensive emergencies
Identity is one of the few areas where inaction compounds cost.
Give Them the Budget Structure (Script Section)
This is the part CFOs latch onto. Deliver it clean.
The CFO Budget Script
“We’re not asking for an enterprise IAM overhaul. We’re asking for a lightweight, modern identity and access platform that prevents waste and gives us clean access controls. YeshID will reduce manual work, eliminate unnecessary licenses, give us audit-ready logs, and centralize access in a way our current tools can’t.”
“The cost is X. The value shows up in reduced IT hours, reduced audit hours, and reduced license waste. This pays for itself.”
“Identity is the foundation of every access decision in the company. YeshID lets us finally automate it in a modern way, using the stack we already have.”
Show the CFO You’ve Thought About ROI
Use this framing:
Immediate ROI:
- automation of onboarding/offboarding
- clean access reviews
- reduced waste
- fewer audit findings
Long-term ROI:
- sustainable permission controls
- less shadow IT
- less dependency on manual IT knowledge
You’re showing stewardship, not spend.
End With the Close
End simply:
“We can keep using manual processes and patchwork tools, or we can put identity on solid rails. YeshID is the simplest way to do that without taking on an expensive enterprise platform.”
Why People Hate Roles and Groups — And How We’re Doing It Differently

Every IT and security team has the same confession: they secretly hate roles and groups. They won’t always say it out loud, because these systems are supposed to be the backbone of access governance. But the truth is, the way roles and groups have been designed for the last decade makes day-to-day operations harder, not easier.
It isn’t because roles and groups are bad ideas. It’s because the tooling around them froze in time.
Why do people hate roles and groups?
They were built for a world where nothing changed
Most RBAC systems assume a clean, stable org chart and a predictable lifecycle. But today, companies change structure every quarter. Teams spin up, dissolve, reorg, merge, and rename. People move between roles faster. Contractors come and go. Shadow apps appear weekly.
The idea that you can build “the perfect set of roles” and walk away is fiction.
Groups accumulate “scar tissue”
Google Groups. Okta groups. Entra groups. Slack user groups. Atlassian groups. Every environment ends up with thousands of them. And every one of those groups becomes the plumbing of everything else: SAML apps, OAuth scopes, shared folders, email routing, channels, alerts.
Over time:
- owners disappear
- external partners stick around
- group names lose meaning
- app-specific mappings drift
- nobody knows which groups matter and which were created for a launch two years ago
Groups do not age gracefully. They rot silently.
RBAC is treated as law, not intention
RBAC was always supposed to describe an ideal state: “This is who should have access if the world is tidy.” But the world is not tidy.
During real operations, exceptions happen:
- temporary access for a project
- contractor needs three extra permissions
- engineer switched scrum teams
- external agency gets access for a demo
- someone gets an elevated role for an incident
Those exceptions create drift. And drift is not a failure. Drift is real life. But legacy systems treat drift like corruption. So you’re stuck between ignoring reality or endlessly rebuilding the “official” model.
IT and security have no shared control over drift
Security wants policy enforcement. IT wants things to keep moving. Both want visibility. Neither wants to fight over whether a single permission breaks all of RBAC.
Most tools give them the same blunt instruments:
- “Fix the role” (which breaks onboarding)
- “Ignore it” (which causes risk)
- “Add another group” (which just creates more sprawl)
No nuance. No staging. No time-based overrides. No understanding of why drift happened.
Reviews happen at the wrong time
Everyone knows roles and groups should be reviewed. But most tools force reviews only during:
- annual access reviews
- quarterly audits
- compliance cycles
Those reviews are slow, exhausting, and disconnected from reality.
What teams actually want is:
- review when someone changes roles
- review when someone switches departments
- review when a contractor ends
- review when an external partner is added to a risky group
- review when drift exceeds what was intended
These moments matter more than anything an auditor ever schedules.
How YeshID is doing it differently
RBAC as an ideal state, not a rigid system
We treat roles and groups as the baseline—the approved model of how access should work. It’s a starting point, not a prison. You can build your clean structure, but it doesn’t collapse the moment reality deviates.
Drift is first-class
We assume drift will happen.
We track it.
We show it.
We help you control it.
You decide:
- what drift is allowed
- what drift is temporary
- what drift should trigger a review
- what drift should auto-revoke
- what drift needs approval
- what drift is safe and expected
Drift becomes something you manage, not something you fear.
Time-based overrides baked in
Temporary access shouldn’t pollute the role forever. If someone needs elevated access for 48 hours, it should automatically revert without creating a new “special” group or permanently mutating the role.
Reviews that happen at the right time
We let you schedule reviews based on changes in reality, not compliance cycles.
Reviews can trigger when:
- someone changes roles
- someone changes teams
- someone is offboarded
- someone moves from internal to external or vice-versa
- a group suddenly gains more external members
- a group suddenly expands its effective permissions
This is how access should be reviewed: in context, not on a fixed calendar.
Groups become “access sets” with structure
In YeshID, a group isn’t just a bucket of people. It has meaning:
- it can map to Google
- it can map to Microsoft
- it can map to Slack
- it can map to any connected app
- it can be dynamic
- it can show drift clearly
You’re not managing floating objects. You’re managing an identity-driven graph.
Separation of provisioning vs enforcement
One of the biggest flaws in legacy IAM is assuming the thing that provisions access is also the thing that enforces security.
YeshID separates:
- Access Sets: what access someone should get
- Policy Enforcement: internal rules and external triggers
- Workflows: how changes happen
- Drift Controls: how reality gets monitored
IT can operate safely. Security can govern without blocking. Both can see the same truth.
The future: cleaner roles, safer drift, fewer surprises
Roles and groups are not going away. They’re foundational. But the old way of managing them—static RBAC, endless groups, brittle policies—simply doesn’t match how modern companies actually work.
YeshID is building an identity system that:
- accepts that things change
- understands that drift is normal
- gives teams the power to review drift at the right time
- keeps the ideal state healthy
- keeps the real world safe
You get the best parts of RBAC—fast onboarding, predictable provisioning—without the rigidity that made people hate it.
This is identity that works the way companies work today.
November 2025 Release Notes

What’s new in November 2025: simpler access for growing teams
This month’s YeshID product updates focus on giving IT & Security leaders more control with less manual work. We’ve tightened group-based access, made large task and workflow views easier to manage, and improved how user data flows into downstream apps and directories.
TL;DR
- 🧩 Group-first access — manage app access through groups and see where entitlements don’t match expectations.
- 📋 Task & workflow clarity at scale — faster filtering, cleaner views, and better behavior when you’re working through hundreds or thousands of tasks.
- 🧑💼 Manager-aware workflows & email — assign tasks to managers, email multiple stakeholders at once, and keep replies pointed at IT.
- 🔗 Stronger identity integrations — push profile updates to SaaS apps, add UKG HRIS, and support more directory fields and IDs.
- ⚡ Performance & admin upgrades — more custom fields, more technical owners, and faster People/Directory pages for large orgs.
Group-based access — more control, less drift
We’ve made it easier to treat groups as the source of truth for application access, and to see when reality doesn’t match policy.
For applications that should only be accessed via group membership, admins can now mark them as “group-only.” When that’s on, end users will only see those apps in the request catalog if they’re already in an enabled group that grants access. That keeps high-risk or tightly-governed apps from being requested by anyone outside the right groups, without extra manual reviews.
On the Person view, you’ll now see:
- Which YeshID groups a user belongs to.
- For each application, whether access is expected, not expected, or not applicable based on those group rules.
That makes it much easier to spot entitlement drift: for example, when someone has access to a group-managed app but isn’t in any group that should grant it.
In the Audit view, there’s also a new Groups column (for orgs using the Groups feature). This lines up with the application accounts view so you can audit by role and group in the same place.
How to try it
- In an application’s settings, configure which groups grant access and enable group‑managed access where appropriate.
- Open a person’s details to see their group memberships and whether each app’s access is expected.
- Use the Audit view to review group membership alongside application roles.
Tasks & workflows — easier to work big queues
The All Tasks view got a significant usability upgrade aimed at teams that live in YeshID every day.
- A new unified search bar lets you combine filters (assignee, status, due date, application, and more) in one place, with keyboard support and smarter handling of advanced filters.
- Due date filters (like “Today”) now behave correctly, so you don’t see tasks from unrelated dates mixed in.
- Automated tasks are hidden by default, which makes queues less noisy—but you can still surface them when you need to.
- Tasks now clearly indicate when they have approvers attached, helping prevent “complete” actions on tasks that aren’t actually actionable yet.
- There’s a new “skipped” status and icon for tasks that were intentionally skipped (for example, when a user already had access to an application via a group), so automation behavior is more transparent.
Access to the All Tasks view is also smarter: non-admins see only tasks where they’re an assignee, while application admins can still see the broader queue for the apps they manage.
On the Workflows page, we’ve reorganized the table and header so it’s easier to scan:
- Status and workflow type now show as separate pills.
- The “details” column is cleaner and focuses on the essential context (user, app, etc.).
- The workflow run header shows user details, workflow type, and status clearly—even if the user has since been removed.
- Server-side pagination now supports viewing beyond 100 workflows, with a visible total count so you know how big the queue really is.
How to try it
- Go to Tasks → All tasks and start typing in the search bar to mix filters (e.g., app + due date + assignee).
- Use the status and due date options to narrow down what needs attention today.
- Visit Workflows to see the new table layout and run header.
Manager-aware workflows & smarter email
We’ve made it easier to keep managers and other stakeholders in the loop without creating extra manual steps for IT.
First, you can now:
- Assign workflow tasks directly to the user’s manager as a built-in assignee option.
- Target the manager as a recipient in Send custom email tasks, just like the employee themselves.
We also cleaned up how custom emails work:
- The Send custom email task now supports multi-select recipients. For example, you can email the new hire, their manager, and HR all at once.
- Email templating always uses the workflow’s target user as the source of variables, so your templates stay consistent even if you change who receives the email.
- You can set a Reply-To address, including a templated support contact, so replies land in the right shared mailbox instead of personal inboxes.
On the identity side of onboarding, we fixed an issue where recovery/personal emails could be lost when creating Google users. Those values now persist reliably so access emails have a valid personal email to send credentials to.
Finally, from the end-user dashboard, requesting a new application now works as expected even when the app doesn’t exist yet in YeshID. Previously, requests for “new” apps could fail silently after the user clicked Submit.
How to try it
- In a workflow template, add or edit a Send custom email task and choose multiple recipients plus an appropriate Reply-To option.
- In task configuration, select Manager as an assignee for steps that the hiring or line manager should own.
- Test a new app request from the self-service app request flow using a name that’s not yet in your catalog.
Identity & provisioning — richer data, better sync
Several updates this month help keep user profiles and entitlements consistent across your stack.
Push profile updates to SaaS apps
For SCIM-based integrations and other supported apps, YeshID can now push user profile updates downstream when a user is changed in YeshID. Behind the scenes, we fetch the current user record from the app, merge in your updated fields (like name, title, location, or role), and send an update—rather than forcing you to wait for a full re‑provision.
UKG HRIS support via code-based integration
We’ve added a code-backed HRIS connector for UKG that uses UKG’s reporting service to bring employee data into YeshID while still letting you map fields like any other HRIS. This is especially helpful for organizations that rely on UKG but still want consistent field mappings (title, department, location, and more) into directories and downstream apps.
Directory and SCIM improvements
- You can now edit a user’s manager directly from the person edit screen in YeshID and have that change sync back to your primary directory (Google or Microsoft).
- During onboarding, additional Google Workspace fields, including title, are now set correctly on new accounts.
- For admins building custom integrations around Okta, the Okta user ID is now available as a mappable field. That makes it easier to call other APIs that require the Okta ID in the URL.
- Notion SCIM configuration was updated so group imports and related operations work as expected.
We also improved how directory statuses and org units behave:
- Directory identity statuses now support Okta “staged” users, so workflows can trigger accurately before users become fully active.
- Tasks that set a user’s Google org unit now include retry logic, reducing the chance of failures when the org unit update runs just before the account is fully created.
How to try it
- Review a SCIM-connected app’s provisioning settings and confirm which profile fields you want YeshID to own.
- For UKG customers, talk to your YeshID contact about enabling the new UKG HRIS connector and mapping your fields.
- Edit a person’s manager in the People section and verify the update in your directory.
Performance, limits & lab tools
As datasets grow, we spent time making the UI feel faster and more flexible for larger organizations.
Faster People, Directory, and pickers
Profile images were previously included in every /users payload, which added up when you had thousands of identities. We now:
- Skip profile picture imports on the very first Microsoft 365 sync to get you to a usable state faster.
- Serve profile images via a separate URL with long-lived caching instead of embedding them in every user response.
The result: snappier loads for People, Directory, and any user picker components, especially in orgs with 2,000+ identities.
We also fixed a subtle scheduling issue where integrations set to run around the end of the UTC day could occasionally slip by a day. Preferred run times are now handled more predictably.
More room for metadata and owners
Two small but impactful limit increases:
- Custom fields per org increased from 10 → 25, giving you more room for HR or business-specific attributes.
- Technical owners per app increased from 5 → 10, so broader infrastructure teams can be represented without workarounds.
Google Workspace group scanner (lab)
We’ve brought our Google Workspace group scanner into the main app as a lightweight lab experience. It’s a static, read‑only tool that helps you explore how groups are structured in your Google Workspace tenant and spot potential issues faster.
- The experience has been refreshed with a light theme and UI aligned to other YeshID cards.
- We’ve also hardened sign-in so only valid Workspace accounts can use it.
If your environment has the lab enabled, you’ll find it under the Google Workspace group scanner path in your YeshID instance.
Voice input on policy assistant
On the policy page, the built‑in assistant now supports microphone input in supported browsers. That makes it easier to talk through policy changes instead of typing long prompts—handy when you’re drafting or revising security and access policies.
Finally, we’ve made a round of behind‑the‑scenes security and library updates to keep dependencies current.
Admin tips
- For high‑risk applications, consider turning on group‑managed access and using the “Access expected” view on a person’s Applications tab to quickly spot users who shouldn’t have access.
- Use the unified task search bar plus due date filters to build saved “ways of working” (for example, a morning view of “My tasks due today”) and delegate broader queues to app admins.
Availability & rollout
All changes described here have been rolled out to production over the course of November 2025. Some group-related features may depend on your org having Groups enabled; if you don’t see them yet, reach out to your YeshID contact or support team.
Helping IT & Security leaders run lean, secure access programs is the core of what we’re building. November’s updates make YeshID more usable at scale, more aligned with your org structure, and better connected to the HRIS and SaaS tools you already rely on.
We’d love to hear what would save your team the most time next—whether that’s deeper integrations, new workflow types, or reporting. Share feedback with your YeshID contact or support team.
October 2025 Release note

What’s new in October 2025: simpler identity management at scale
This month in YeshID’s IAM platform, we focused on making day‑to‑day identity management easier for IT & Security leaders at mid‑sized businesses. You’ll see big improvements in how you manage workflow tasks, run groups, and stand up integrations—plus a lot of polish on CSVs, emails, and approvals.
TL;DR
- ✅ New All Tasks view with filters and bulk actions to triage work across every workflow.
- 👥 Smarter groups pages with clear owners, static membership, and tighter links to application access.
- 📦 Push Groups & SCIM upgrades so app groups and memberships stay in sync automatically.
- 🔌 Easier integrations, including Google Workspace import and more flexible OAuth headers.
- 📊 Everyday UX fixes for CSVs, access emails, Safari workflows, and approval flows.
All Tasks view — one place to triage every workflow
Work no longer hides inside individual workflows. The new All Tasks view gives you a single list of everything that needs attention across onboarding, offboarding, and access requests.
You can filter by status (incomplete, error, completed), assignee, and more, and the default view focuses on incomplete/error tasks assigned to you so you can clear your queue quickly. We’ve flattened nested tasks for easier scanning, added basic pagination so large orgs don’t bog down the browser, and tuned the backend to fetch tasks and target users in fewer queries.
On top of that, you can now bulk complete, reject, or delete selected tasks, with safeguards so automated tasks only move from “running” to “complete” when it’s safe to do so.
How to try it
- Open the Workflows area in YeshID.
- Look for the new All tasks view in your navigation.
- Use the filters to narrow to your team and status, then try bulk completing a batch of done work.
Note: This view is rolling out behind a feature flag. If you don’t see it yet, reach out to your YeshID contact.
New groups experience — clearer membership and app access
Groups got a major refresh this month to make “who’s in this group and what does it do?” a much easier question to answer.
Group pages now have just two tabs—Members and Access—with Members as the default. At the top, you’ll see an editable card where you can update the group’s name, description, owners, and active status in place. You can set owners when you create a group and manage them later through a dedicated owners table, so there’s always a clear accountable contact.
Membership is now explicit and static, with tools to add or remove people in bulk from the Members tab. Behind the scenes, we record when users enter or leave a group so you have an audit trail for membership changes.
On the Access side, groups now:
- Show which applications and roles the group grants.
- Respect group‑based access when users request an app—if their group already grants that app+role, approvals are automatically bypassed.
- Surface, in application settings, which groups grant access to that app, with visual badges indicating whether those groups are enabled or disabled.
This makes it much easier to explain access in audits: you can see exactly which groups drive access to a given app, and which apps each group actually controls.
How to try it
- Go to Groups and open any existing group.
- On the Members tab, review owners and add/remove members as needed.
- On the Access tab, review which apps and roles the group grants, and adjust as your policies evolve.
- In Applications, open an app’s settings to see which groups are currently granting access.
Push Groups & SCIM — keep app groups aligned automatically
If you manage a lot of SaaS groups (especially via SCIM or Slack), you now have more help keeping them in sync.
For SCIM‑capable applications, YeshID can now import application groups and their memberships, similar to how we already handle HR and directory data. You can configure which fields to bring in and view groups and members directly in the app’s collections view, giving you better visibility into how the app organizes teams and projects.
We also introduced Push Groups support:
- A new “push group” mapping lets you link internal groups or user attributes to specific app groups.
- A new Push Groups task is available in application workflows, which uses those mappings to create or add the user to the right groups in the target app.
- Under the hood, an AddToGroup action uses the app’s SCIM or API configuration so you don’t have to script it yourself.
This is especially useful for tools like Slack and other SCIM‑backed apps where group/space/team membership is the real permission model.
How to try it
- Open an integrated application that supports SCIM or group management.
- In its configuration, define push group mappings from your groups or fields to app‑side groups.
- Add a Push Groups step to the relevant onboarding/offboarding workflows for that app.
- Run a test user through the workflow to confirm they land in the right groups.
Integrations & OAuth — smoother setup, more flexible tokens
We’ve made it easier to connect and manage integrations so you spend less time wrestling with configuration screens.
First, provisioning and integration setup now share a consolidated configuration card with a new Auth & Parameters panel. This panel pulls together:
- Setup instructions for catalog and SCIM integrations,
- Auth inputs (like OAuth 2.0), and
- Global parameters,
with shared validation and a clear sense of whether configuration is “complete” or not. This panel now shows up when you add apps, configure catalog integrations, or manage authentication for existing apps.
We also shipped several integration‑specific improvements:
- Google Workspace as a tier‑1 integration, with support for importing users so you can audit Google more easily in YeshID.
- GitHub and other apps now correctly mark admins based on the right flags, so your access grid and audits reflect real admin status.
- OAuth is more flexible:
- You can supply your own
access_type(for example,offlinefor Google) without YeshID duplicating it. - You can customize the header key and prefix used to send tokens (for example, sending
Zoho-oauthtoken <token>instead of a standardAuthorization: Bearer).
- You can supply your own
And we’ve fixed several edge cases that previously caused offboarding steps to get stuck, accounts to be marked as “running” forever, or deprovisioning to fail when the user had already been removed in the target app. The goal: fewer surprises when you sync, onboard, or offboard.
Everyday UX & reliability — CSVs, emails, Safari, and approvals
A lot of small but important changes landed that you and your team will feel day to day.
Cleaner CSV exports and more helpful imports
Exports from the Access Grid and application accounts now:
- Show full names (not just first names),
- Render role names correctly rather than
[Object], and - Provide more consistent columns for audit and reporting.
On the import side, CSV uploads now run through a preflight check that can:
- Reject Excel‑style UTF‑16 CSVs and files with null bytes with a clear “save as UTF‑8 or ASCII” message,
- Flag missing headers, duplicate column names, and mismatched column counts (with the first row number to inspect), and
- Warn when a file looks truncated or has quoting issues.
That means fewer “mystery” import failures and clearer guidance when something’s off.
Better emails, browsers, and domains
- The “Send custom access email” preview now respects formatting, so what you see in the preview matches what users receive.
- When sending access emails, choosing a different email domain actually updates the address, making it much easier to handle orgs with multiple verified domains.
- Safari users now see complete task lists when viewing workflows; a Safari‑specific loading issue has been fixed.
Access requests, approvals, and audits
We tightened up the access‑request experience:
- Requesters can now add context to their requests by clicking into the application box, and approvers/assignees can reply with comments and choose to share them back with the requester.
- Comments are no longer tied to task state—you can comment even before approvals are cleared.
- A bug where a rejected request sometimes looked approved has been fixed; the system now correctly routes to the rejection path.
- In the access request modal, choosing an app no longer causes the entire app list to re‑appear unexpectedly.
For audits:
- Application audit tasks can now only be assigned to people who actually have access to the application data, avoiding confusing “empty” audit views for non‑admins.
- The audit help text no longer suggests mid‑audit role changes for integrated apps where that isn’t supported, reducing mixed messages for auditors.
Admin tips
- Start in All Tasks: Use the All Tasks view with the default filters (assigned to you + incomplete/error) as your daily homepage. Once you’re comfortable, try bulk completing a group of done tasks.
- Review your key groups: Take a quick pass through your most important groups to confirm the name, description, owners, members, and app access all match how you talk about them internally. It will pay off in your next access review.
Availability & rollout
Most of these updates are live for all customers. Newer experiences like the All Tasks view and some group/access cards may appear first for selected organizations behind feature flags; if you’d like early access, your YeshID contact can help.
Closing & what’s next
October’s work is all about helping IT & Security teams see more, click less, and trust that workflows, groups, and integrations are doing what you expect. Whether you’re managing a handful of workflows or hundreds of thousands of tasks, these changes are designed to save you time and reduce access risk.
We’d love to hear what would make YeshID even more useful for your team—especially around workflows, audits, and integrations. Share feedback with your account team or through in‑product support.
Why ITSM Isn’t IAM, And Why AI Ticketing Tools Don’t Solve Access

The market is shifting fast. SaaS adoption keeps growing. Contractors come and go. Teams add new apps constantly. IT and Security teams receive a steady stream of requests for access, onboarding, offboarding, and permission changes. The work never slows down.
As this pressure builds, many mid-market companies look for something lighter than ServiceNow and more structured than Jira. This has created a new category of AI-driven ticketing tools that advertise themselves as modern ITSM systems. These tools promise cleaner workflows, faster approvals, and an easier way to manage access requests. They often include HR integrations and can provision or deprovision accounts across common SaaS apps.
They improve the first layer of the experience, but they do not solve the deeper access problem.
The difference between ITSM and IAM remains clear
ITSM exists to manage requests, incidents, tasks, and service delivery. Its job is to help teams organize operational work. It focuses on the process.
IAM exists to manage identity, permissions, lifecycle events, and enforcement. Its job is to decide and maintain who should have access and why. It focuses on the system of record.
ITSM decides how a request moves.
IAM decides how access is granted or removed.
These are not competing functions. They are separate domains.
Why new AI tools blur the line
The attraction of these tools is real. They give IT a fast, approachable interface for requests. They make approvals straightforward. They can automate tasks like creating accounts, disabling access, or assigning a set of apps on day one. They generate audit logs and help teams run consistent onboarding checklists.
For many companies, this feels like a breakthrough. It reduces noise and helps teams get organized.
But these tools do not operate as identity systems. They automate actions, but they do not own the identity model or the policies behind those actions.
They do not maintain a unified view of who the user is, what they should have, and what they should not have. They do not evaluate the user’s role, department, location, manager, employment type, or risk posture to determine the correct access. They do not monitor or correct drift when access falls out of alignment with policy. They do not provide continuous governance.
The automation works, but the reasoning behind the automation is missing.
Why this creates problems over time
Companies that adopt these AI ticketing tools often find themselves running two systems. Jira or another service desk continues to handle engineering and IT operations. The new AI tool handles onboarding checklists and access requests. Both systems generate tasks and approvals, but neither maintains a single, authoritative identity layer.
This leads to conflicting views of who has access, inconsistent provisioning rules, manual corrections, and gaps in offboarding. The surface-level workflow looks smooth, but the underlying identity state remains fragmented.
Provisioning alone does not guarantee correct access.
Task automation does not replace governance.
This is where organizations begin to feel the limits of these tools. They solve the intake of requests, but they do not solve the accuracy, consistency, or security of access across the environment.
What real access management requires
Identity and access are not defined by a checklist or a one-time provisioning action. They are defined by a continuous model that ties identity attributes to policy. Real access management needs a system that understands the full lifecycle. It needs a platform that can determine the correct permissions at every stage of a user’s employment, catch drift when it happens, enforce least privilege, and provide a complete audit trail for compliance.
This kind of work requires a dedicated identity layer, not a workflow engine.
Where YeshID is different
YeshID automates onboarding, offboarding, provisioning, and deprovisioning. It integrates with HR. It connects to SaaS tools. It runs workflows. It generates audit trails. But it does all of this with an identity-native foundation.
Access is not just assigned. It is evaluated.
Access is not just removed. It is verified.
Access is not just logged. It is governed.
YeshID maintains a clear identity object for every person. It tracks attribute changes. It manages groups, roles, entitlements, and policies. It detects drift. It cleans up inconsistent access. It ensures that identity and access remain aligned at all times.
Companies can continue using Jira or ServiceNow if they prefer. YeshID integrates cleanly into those systems and performs the identity work underneath. This avoids the problem of adding yet another ticketing tool and creates a single, authoritative layer for the entire access lifecycle.
The mid-market reality
Most growing companies do not need more workflow engines. They need fewer tools that perform more meaningful work. They need identity automation that eliminates manual tasks, closes gaps, and keeps access accurate as the business scales.
The new AI ticketing systems improve the request experience, but they do not replace IAM. They automate tasks, not identity. They streamline workflows, not governance.
YeshID fills the gap by providing a real identity foundation with the automation companies expect. It gives teams a consistent, reliable system of record for who has access and why. It replaces the hidden manual work that continues even after the workflow looks clean from the outside.
Identity determines access. Workflows do not.
- A request system organizes information.
- An identity system enforces the rules.
The new class of AI-driven ticketing tools makes the request experience easier, but it does not solve access management. Only an identity-native platform can do that work. That is what YeshID is built to deliver.
Free Tool: Google Groups Should Not Be a Mystery

Most teams treat Google Groups as a convenience feature. Add people to a group, they get access, done. But over time, that convenience slips into chaos. Groups turn into the plumbing of everything in Gmail, Drive, Calendar, and the pile of SaaS tools connected to your Workspace. They decide who can read sensitive files, who can forward mail, who has access to that shared Dropbox folder from 2019, and who keeps getting alerts from an app no one remembers buying.
And when you finally look under the hood, you see the mess that built up quietly.
We built a free tool that looks directly at the parts of Groups that actually create risk. No setup. No onboarding. You authorize it and it shows you the issues that matter.
This is not a product launch. It is a free utility for admins and security teams who already carry too much operational weight.
What we found when we looked at real environments
When you stare at a few thousand groups, patterns jump out. Ownership disappears. Suspended accounts never get removed. External partners accumulate in places they were never meant to be. Some groups have fifty owners while others have none. Super admins show up inside everyday audiences. OAuth apps with broad scopes are waiting in those same groups.
And everyone assumes someone else cleaned it up.
Groups decide who can read, share, and move data. When they are healthy, least privilege becomes simple. When they sprawl, your blast radius grows. That is the whole reason this tool exists.
What the tool checks
We focused on checks that move the needle. These are the ones that make auditors nervous and give attackers opportunity.
Ownership and accountability
- Groups with no owners
- Groups missing a Manager role
- Leaders hidden from the Directory
Access hygiene
- Suspended accounts still inside groups
- Accounts that never signed in (30 or 90 days)
- Empty groups cluttering everything
- Members without a Gmail mailbox
Privilege and authentication
- Super admins without 2SV
- Groups containing super admins without 2SV
- A direct list of super admins with last sign in and OU
App and data risk
- High risk OAuth app access clustered in groups
Boundary and trust
- External membership that has grown quietly
- Group addresses on unverified or external domains
Scale and visibility
- Largest groups with role breakdown
Every issue comes with two short explanations:
Why this matters. What to do next.
No one wants to dig through documentation or guess how to fix something.
What you get right away
The moment you authorize, you get a ranked, noise-free list of the riskiest group problems. Not a giant spreadsheet. Not a dashboard full of numbers. Just a clean set of issues that deserve attention.
You also get guided fixes. Add two owners. Enroll 2SV. Remove suspended members. Revoke high risk scopes. Move a group to a verified domain. Delete an empty group. Split external audiences. Assign a Manager.
This is the kind of work you can run through in a weekly standup.
And if you ever face an audit, you now have clean evidence showing you are monitoring and correcting group controls.
Who this helps
- Workspace admins relying on groups to define access
- Security and IT teams who want real least-privilege hygiene without more budget
- Orgs that work with partners and need boundaries that do not drift
- Teams rolling out or enforcing 2SV and app governance
If your organization uses Google Groups, this is a fast way to get clarity.
Why we built it
Groups are powerful. They are also invisible until something breaks. Most teams do not have the time or the tools to dig through thousands of memberships, roles, mailbox states, and OAuth relationships.
So we stopped waiting for someone else to solve it and built a simple tool that checks the exact issues we see across hundreds of real environments.
Instant. Free. Useful from day one.
Getting started
Authorize the tool, review your findings, and clean up what matters first. It runs fully client side, costs nothing, and takes minutes. Try it now.
Starting SOC 2 Without the Burnout: A Practical Guide for Lean Teams

If you are kicking off SOC 2, you do not need a rip and replace project or a new alphabet soup of tools. SOC 2 Security (CC1-CC9) can be met with a few low effort controls, operated consistently, and backed by simple evidence.
1) Start here: Scope to win
Define a small, sensible system boundary (for example: Google or Microsoft, HRIS, ticketing, company issued devices, core app components).
Treat platforms run by others as subservice organizations. Get their attestations and write a one page "who does what" matrix.
Keep hard to govern cohorts out of scope at first (for example: personal email field users) or include a small pilot ring where you can enforce basics.
SOC 2 mantra: Say what you do → Do it → Show evidence.
2) Controls that pass (cheap & cheerful)
- MFA everywhere (Google or Microsoft or your IDP).
- Password manager required (and force install the extension through browser management).
- On and offboarding from HR with 24 hour disable on termination.
- Quarterly access reviews by data owners (keep sign offs).
- Device hygiene: full disk encryption, auto lock, monthly patch evidence; built in antivirus (for example: Defender) is fine.
- Browser and OAuth hygiene: manage browsers, block risky extensions, allowlist OAuth apps; do a monthly review.
- Monitoring: enable admin and security alerts; log incidents and changes in your ticketing tool.
- IR tabletop once per year; test one backup and restore flow annually.
Nice to have (not required to pass): org wide SAML cutovers, full EDR or MDM, SIEM or DLP. Use them later where they clearly pay off.
3) Cloud Identity (for Google centric teams)
You can govern users without buying Gmail or Calendar.
Cloud Identity Free $0
Users and groups, SSO, MFA, basic mobile management (passcode plus account wipe)
Cloud Identity Premium per user
Adds context aware access (gate access by device posture or location), advanced device policies, automated app provisioning, SLA and 24x7 support
Practical sizing: start with Free to get managed identities and MFA into cohorts that currently use personal email. Upgrade selectively to Premium for higher risk groups that benefit from context rules or automated provisioning. (Feature sets vary. Always check your edition.)
4) Evidence calendar (copy and paste)
Monthly (about 60 to 90 minutes):
Admin alert export → Patch ticket and OS update logs → Browser extensions report → OAuth allow and deny changes → Five device encryption and lock spot check.
Quarterly:
Access reviews (Google or Microsoft or core apps) with owner sign offs → Risk register and vendor list updates.
Annual:
One hour IR tabletop → Policy re acknowledgments → One backup and restore test.
5) Policy one liners (copy and paste)
MFA: All in scope systems require MFA. Exceptions need executive approval and expire in 30 days.
Provisioning: Accounts are created only upon HR hire and disabled within 24 hours of termination.
Access Reviews: Data owners review access quarterly and record results.
Devices: Only approved, encrypted devices with auto lock may access in scope data.
Patching: OS and browsers are updated monthly. Exceptions require a ticket.
Changes: Production SaaS changes require a ticket with risk and impact and approval. Emergency changes are documented within 24 hours.
Vendors: High risk vendors provide security reports. Subservice responsibilities are documented.
6) What can wait (and why)
Org wide SAML: great for user experience later, not needed to pass.
EDR or MDM everywhere: helpful, but start with platform basics; apply to high risk rings first.
Big bang directory consolidation: tackle gradually. Begin with cohorts where you can enforce MFA and device posture.
7) Optional accelerators (no rip and replace)
If you are on Google Workspace or Microsoft 365 or even Okta, consider tools that automate lifecycle, finish access reviews, and surface Shadow IT (for example: YeshID). The goal is not more dashboards. The goal is governed access with evidence created at the moment of change.
TL;DR
You can pass SOC 2 Security with: MFA + clean lifecycle + basic device hygiene + simple monitoring + real evidence cadence. Keep scope tight, document what you do, and collect proof as you go. Save the big projects (SAML everywhere, EDR or MDM for all) for when they clearly reduce risk or cost.
Identity & Access Management: Stop Chasing Integrations. Start Orchestrating.

Everyone wants the magic “Connect App” button. You click, it spins, and everything just works.
Except it doesn’t. Not in real life.
In reality, integrations are messy. You’re digging through settings to find the right API key, realizing your plan doesn’t include SCIM, begging the budget owner for an upgrade, and deciphering docs last updated in 2019.
That’s not a failure — it’s just how the modern SaaS world works. Everyone wants a seamless experience, but no one really knows their full stack.
The 80/20 Reality
Here’s the truth: integrations are only 20% of the problem.
The other 80% is orchestration — the process that defines what happens when someone joins, moves, or leaves.
And that’s the part most Identity & Access Management (IAM) programs get wrong.
IAM isn’t just about sign-on or authentication. It’s about how identity flows through your organization — how requests, approvals, and removals actually happen in practice. Orchestration is the part that makes security and compliance real. It’s not about writing another policy or checklist — it’s about making the right process the easy process.
When you get orchestration right:
- Access requests go through something familiar and consistent.
- Employees actually feel what good security looks like.
- Approvals, offboarding, and exceptions all flow the same way — no Slack DMs or “can you add them real quick?” chaos.
That’s the first step in building a security and compliance mindset — where following the process isn’t friction; it’s culture.
Why It Matters More Than Automation
Everyone rushes to automate, but automation without orchestration just accelerates mistakes.
When orchestration clicks, your IAM foundation becomes real. It gives you:
- Visibility: Who asked for what, when, and why.
- Consistency: No special rules for special people.
- Auditability: Proof that process was followed, every time.
Once those things exist, automation becomes trustworthy. You’re not just wiring up systems — you’re building confidence.
Build for Flexibility, Not Fragility
Yes, integrations still matter. But APIs break, endpoints move, and “enterprise” features get renamed every quarter.
Your IAM or workflow platform should bend, not break. It should adapt when the SaaS world changes. That’s what orchestration-first design gives you — flexibility that outlasts any integration.
The Real Lesson
Stop chasing integrations like they’re the goal. Start orchestrating like you’re building muscle memory.
When your company learns to follow process — because it’s intuitive, familiar, and efficient — you’ve already won half the security battle.
Orchestration turns “compliance” from a checkbox into a reflex.
And once that mindset takes root, automation and integrations finally have something solid to stand on.
The Real Priorities of an Identity & Access Management Program

Everyone loves to talk about security.
“Did you turn on MFA?”
“Did you enforce SSO?”
“Did you harden your auth for that app no one even uses anymore?”
And don’t get me wrong — those things matter. But they’re not the foundation of a mature Identity & Access Management (IAM) program. They’re the polish on the edges. The shiny locks on a building where half the keys are still unaccounted for.
So what is the right order of operations?
1. Visibility Before Control
You can’t secure what you can’t see. Most companies start reacting to “access sprawl” only when someone asks, “Who still has access to that?” — and no one can answer.
Before you buy another tool, before you spin up another integration, make sure you have a single source of truth for:
- Who your people are (HRIS or directory)
- What systems they can access
- How and why that access was granted
Think of it like building your identity graph — not the marketing kind, the real one that ties humans to entitlements.
This isn’t just opinion. It’s the first pillar in every major framework:
- NIST SP 800-53 starts with Account Management (AC-1 to AC-6) — identification and inventory before any authentication.
- ISO/IEC 27002:2022 outlines Access Control in the same order: define business requirements → manage provisioning → then enforce authentication.
Visibility first. Always.
2. Automate the Mundane
Once you can see it, stop doing it manually.
Manual onboarding, Slack DMs for access, “can you remove this person from Salesforce?” emails — those are all risk vectors. Not because people are bad, but because they’re busy.
Automated provisioning isn’t just convenience. It’s hygiene. It ensures that when someone joins, changes roles, or leaves — the right access flips automatically, and nothing lingers.
The goal: get to zero-touch lifecycle changes. Or as we like to call it, no more “oops, they still had access.”
Both Gartner’s IAM Maturity Model and Forrester’s Zero Trust Framework agree: automation of provisioning and deprovisioning is the second foundational stage. Gartner even calls it “the inflection point where IAM shifts from reactive to governed.”
3. Policy Meets Workflow
Policies sound great on paper:
“Access must be reviewed every 90 days.”
“Only managers can approve new access.”
But in the real world, policy without workflow just creates audit theater.
Your IAM system should enforce the intent of your policy — not just document it. That means building real, operational workflows for:
- Access requests and approvals
- Temporary or just-in-time access
- Periodic reviews and re-attestation
When the process mirrors how your teams actually work, compliance stops feeling like punishment.
According to CIS Critical Security Controls v8, “Account Management” and “Access Control Management” are distinct — and the connective tissue between them is process automation and review cadence.
4. Then — Harden Authentication
Only now should you care about the front door.
Once you’ve got provisioning and workflows in place, go back and harden your authentication surface:
- Enforce MFA everywhere
- Add device or location checks
- Centralize auth with your IdP
At that point, you’re protecting an environment you actually understand. Without that foundation, tightening auth is like putting a fancy alarm system on a house with open windows.
Gartner calls this the “Access Management stage” — valuable, but dependent on strong governance underneath.
5. Continuous Review, Not Point-in-Time Audits
Identity isn’t static — it changes every day. New hires, project access, contractors, mergers. The “state” of access is a moving target.
The best IAM programs don’t just audit annually. They continuously attest to what’s real right now. That’s where AI, smart policies, and automation shine — keeping your environment aligned with intent without constant human babysitting.
The TL;DR
If you’re just starting or rethinking your IAM program:
- Visibility first — know who has access and why.
- Automate provisioning — no more manual adds/removes.
- Enforce through workflow — policy that actually executes.
- Then harden authentication — strong locks on a well-managed house.
- Continuously review — access isn’t static.
These aren’t random steps — they’re the shared backbone across NIST, ISO 27001, CIS, Gartner, and Forrester. Different frameworks, same message: start with identity logic, end with auth polish.
Most companies over-index on locks and underinvest in logic. At YeshID, we help you flip that script — visibility, automation, and control that scale with your stack. Learn how real-world workflows make IAM actually work.
Release Notes October 2025

What’s new in October: YeshID updates for clearer workflows and smoother app requests
This month’s YeshID product updates focus on cutting friction for admins and end users. You’ll see faster, clearer application requests, easier task reassignment, and stronger provisioning with System for Cross‑domain Identity Management (SCIM).
TL;DR
- 🧭 Cleaner app requests — end users see the right custom fields; admins see requestable apps; My Apps still shows apps you already have.
- 👥 Assignee changes that stick — reassign tasks (including virtual and application tasks) without surprises; workflows stay stable when people leave.
- 👀 Clarity for non‑admins — no duplicate dynamic tasks; each task now shows its parent context.
- 🔧 SCIM that “just works” — correct content types, robust ID/role handling, and readable error previews in Test Import.
- ✉️ Alias mapping control (Beta) — optionally disable auto‑mapping to email aliases to prevent cross‑mapping.
App requests & My Apps — fewer tickets, more clarity
End users can now see the custom fields required in application requests, so requests are complete the first time. We also aligned the “Hide from application request” setting with its label: hiding an app from the request list no longer hides it from My Apps if a user already has an account. Finally, admins again see the correct list of requestable apps in the “Request an application” dialog.
How to try it
- Start a request (Access → Request an application) and confirm required custom fields are visible.
- If you hide an app from requests, check My Apps to verify it still shows for users who already have access.
- As an admin, open Request an application and confirm the dropdown populates as expected.
Assignee control in workflows — changes that stick
You can safely reassign workflow tasks, including virtual tasks and application tasks, and expect the update to persist. The product now clearly indicates when updates are allowed and enforces that in the background, reducing confusion and accidental edits. When a person is deactivated or deleted, YeshID automatically cancels pending tasks targeting them and unassigns them from incomplete tasks and templates—preventing “invalid assignee” errors and stuck workflows.
How to try it
- Open a workflow task and change the assignee (works with virtual and application tasks).
- Deactivate a test user and review related workflows to confirm tasks are unassigned or canceled as needed.
Clearer task views for non‑admins — more context, no duplicates
Non‑admin users (like technical owners) now see a clean, de‑duplicated task list. Dynamic container tasks that previously caused duplicate entries are hidden for these users. To preserve context, each sub‑task now includes its parent task name (e.g., “Remove from application — Deactivate user”), so assignees understand the “why” behind their work without extra clicks.
How to try it
- Log in as a non‑admin assigned to tasks.
- Open a workflow with subtasks and confirm there are no duplicates and that each task shows its parent label.
SCIM provisioning & imports — easier debugging, fewer failures
We tightened SCIM (System for Cross‑domain Identity Management) compatibility so integrations are more resilient. YeshID now sends the correct application/scim+json content type where required, skips sending empty role arrays that upset some providers, and better handles large numeric IDs so fields don’t convert to scientific notation. In the Test Import flow, error previews now surface the server’s response context on 4xx/5xx errors—helping you troubleshoot faster without guesswork.
How to try it
- Run Test Import on a SCIM integration and review the error preview on a failing call.
- Verify create/update actions no longer fail with 415 errors on strict providers.
- Confirm user creation updates roles correctly when configured.
Alias mapping control — prevent cross‑mapping (Beta)
Some teams prefer not to auto‑map YeshID people to email aliases (for example, when managers hold aliases for former employees). You can now opt out with a new org setting to disable alias‑based mapping. This helps keep accounts clean and avoids mismatches in environments with many aliases.
How to try it
- Ask Support to enable the alias‑mapping setting for your org.
- Toggle the setting on/off to match your mapping policy.
Admin tips
- Creating a person without onboarding? If you’re not starting a workflow, user creation no longer gets blocked by template validation—just leave the onboarding checkbox off.
- Safer template deletes. Deleting a workflow template now includes a confirmation dialog to prevent accidental removal.
Availability & rollout notes
All updates above are live for all customers unless marked (Beta). The alias mapping control is behind a feature flag and available on request.
We’re focused on helping IT and Security teams move faster with less risk. These YeshID product updates should reduce back‑and‑forth, keep workflows moving, and make integrations more dependable.
Tell us what would save your team the most time next. Share feedback in the comments or reach out to our support team for help getting started.
Introducing Application Workflows: Real-World Automation for Real-World Apps

When people talk about “automating access,” it sounds simple — add a user, remove a user.
But anyone who’s actually done this knows it’s rarely that clean.
Different apps have different quirks. Some need you to drop users into a specific group for SSO. Others require an admin to manually approve or assign licenses. Offboarding often comes with grace periods or transfer steps before you can truly remove access.
That’s why YeshID introduced Application Workflows — a smarter, flexible way to automate the real lifecycle of user access.
What’s an Application Workflow?
An application workflow is a set of steps that define how a user is added to or removed from a specific app — not just at the IDP layer, but all the way through the operational reality.
For example:
When someone requests Slack access, the steps might look like this:
- Add the user to the Okta group application_Slack to enable SSO.
- Create the user in Slack via API.
- Notify the manager or IT admin that access is active.
Or when someone leaves the company, your offboarding flow might:
- Disable the Slack account.
- Wait 30 days to allow message exports or file transfers.
- Fully remove the license and delete the user.
Each step — whether automated or manual — becomes part of one clean, auditable workflow.
Why It Matters
In most companies, onboarding and offboarding are multi-step processes scattered across tools, people, and tickets. Application Workflows bring it all together — so that:
- IT stays in control, even when tasks span multiple systems.
- Managers and HR can safely participate, without being experts in every app.
- Audits become painless, since every access change is tracked.
Even if part of the process is manual — say, checking a box in a vendor portal — YeshID lets you insert that manual step right into the flow. Nothing falls through the cracks.
Built for the Messy Middle
Most IAM tools assume every app supports SCIM or has a perfect API. Reality check: most don’t.
YeshID’s Application Workflows meet you where your stack really lives — in the messy middle of modern SaaS.
You can mix:
- Automated steps (via API, REST, or SCIM).
- Manual steps (with clear instructions and tracking).
- Conditional logic (like approval chains or time delays).
The result? Anyone in your company — from IT to HR — can handle complex onboarding and offboarding without breaking compliance or burning time.
A Simple Idea, a Powerful Shift
Application Workflows turn “add/remove user” into something deeper: a reliable, repeatable process that reflects how work actually happens inside your organization.
It’s not about replacing humans. It’s about making human-in-the-loop automation work — safely, consistently, and at scale.
Because access isn’t one step. It’s a workflow.
The Modern Stack? Or Just the Messy Middle?

Everywhere you look, vendors pitch the “modern stack” like it’s some clean, uniform, well-architected utopia. But let’s be real: most IT environments today look less like a showroom and more like a garage sale.
What the Stack Actually Looks Like
Sure, there are still SAML and SCIM integrations — but only for the handful of apps where you ponied up for the “enterprise package.” For everything else? It’s a hodgepodge of:
- New and amazing apps your team is testing out.
- Trial accounts nobody remembers creating.
- Spreadsheets and email threads driving access changes because the HRIS integration isn’t complete.
- Slack or Teams apps someone clicked “approve” on without a second thought.
It’s not the “classic stack” of on-prem AD and Exchange. It’s not the “AI-stack” we all keep talking about like it already exists. It’s the messy, middle stack.
Why It’s Messy
- You haven’t bought every enterprise license.
- You’re still deciding which apps make the cut.
- SCIM is available, but it’s expensive, so you wait.
- Shadow IT isn’t a theory — it’s the only way teams move fast.
And in that chaos, IT is stuck duct-taping onboarding and offboarding processes together.
The Stakes
This isn’t just cosmetic mess. It creates real problems:
- Dormant accounts that linger for weeks after contractors leave.
- Compliance reviews that eat entire weeks of calendar time.
- Confused managers who don’t know who should get what access, or for how long.
Call It What You Want — We’ve Got You
Whether you want to dress it up as the “modern stack,” admit it’s the “messy stack,” or split the difference and call it the “middle stack,” here’s the point: YeshID supports it.
We don’t force you into a clean enterprise-only world that doesn’t exist. We don’t pretend you can SAML/SCIM your way into bliss. Instead, we:
- Manage all apps regardless of license type — not just the ones with shiny SAML/SCIM connectors.
- Show you what apps your teams are actually playing with, so you can have the right enabling conversations instead of policing after the fact.
- Make onboarding repeatable without endless IT button-pushing.
- Kill dormant accounts the day seasonal workers leave.
- Let HR or managers handle access without needing to become IT admins.
- Keep costs predictable (no SSO tax, no surprise per-seat bloat).
Ready to stop duct-taping the “messy middle” together? Schedule a demo with YeshID and see how we help you manage every app, every user, every workflow — no SSO tax required.
The SaaS Discovery Buyer’s Guide: What’s Relevant, What’s Noise, and What’s Just Creepy

In 2025, every security, IT, and compliance leader is pitched a flavor of “SaaS discovery.” Vendors promise you’ll finally know what apps your employees are using, where your data is going, and how to rein in shadow IT.
But not all SaaS discovery is created equal. Some approaches give you the insights you actually need. Others drown you in noise. And some cross the line into outright privacy invasion.
Here’s how to tell the difference.
What’s Actually Relevant
The goal of SaaS discovery is simple: visibility. You need to know what tools are in play, so you can decide which ones to support, secure, and monitor. Done well, discovery should highlight:
- OAuth Connections – Which apps employees have connected to Google Workspace, Microsoft 365, or Slack. These integrations are where sensitive scopes (calendar, email, contacts, files) can be over-shared.
- Network Integrations – Which sanctioned apps (like Salesforce, Zoom, or Jira) are connected to each other, often via API keys or third-party connectors.
- Expense Data – What’s being billed on corporate credit cards. Finance often sees SaaS spend before IT does.
- SSO Logs – Apps launched from your identity provider. This is the cleanest way to understand what’s officially in use.
- Contracted Apps vs. Actual Usage – Licensing vs. reality. That “500 seats of Box” might be 30 active users and 470 shelfware.
These data points give you an operationally useful view of what to keep, what to rationalize, and where to plug compliance gaps.
What’s Noise
Many vendors mistake “collecting more” for “delivering more value.” The result? Dashboards cluttered with irrelevant or misleading signals, such as:
- Every Chrome Extension Ever Installed – Ninety percent of them are calculators, Grammarly, or Zoom add-ons. Not actionable.
- Random Web Traffic from Personal Browsing – Just because someone hit monday.com on their phone doesn’t mean the company is adopting it.
- Redundant App Detections – Seeing the same tool listed five different ways (“Slack,” “Slack Technologies,” “Slack.com”) isn’t insight — it’s database hygiene failure.
- “Shadow Apps” with No Context – A scary-sounding list of 400 unknowns doesn’t help you prioritize which ones matter.
Noise wastes analyst time and undermines trust in the tool. If you can’t explain to leadership why the data matters, it’s just distraction.
What Crosses the Privacy Line
Here’s where things get dicey. In the rush to promise “total visibility,” some vendors collect more than they should — and that erodes trust with employees:
- Endpoint Keylogging or Full Browser Monitoring – Tracking every URL a user visits or every click they make is surveillance, not discovery.
- Personal Email / Personal Device Scanning – Some tools overreach by inspecting Gmail or iCloud logins, or blending corporate with personal browsing.
- Session Hijacking Techniques – Scraping tokens or injecting agents that can impersonate the user crosses into security risk, not security control.
- Always-On Desktop Agents with No Transparency – Employees should know if a tool is watching their every move. Hiding it in the background kills cultural buy-in.
If a vendor’s approach would make your privacy team squirm, it’s not worth the risk.
The GDPR Factor: Extra Risk in Europe
If your workforce includes employees in the EU, the risks of invasive SaaS discovery aren’t just cultural — they’re legal and financial. Under the General Data Protection Regulation (GDPR), employers must follow strict rules when collecting and processing personal data.
Where discovery tools can go wrong:
- Monitoring Without Legal Basis – Constant endpoint or browser tracking may be considered “surveillance,” which requires a lawful basis (Article 6). “We want visibility” doesn’t cut it.
- Mixing Personal and Business Data – Capturing personal browsing history, personal app installs, or Gmail logins without consent is a GDPR violation.
- No Transparency or Consent – Hidden agents or opaque data collection can trigger challenges from works councils or regulators.
- Data Minimization Violations – GDPR requires you to collect only what’s necessary. Pulling full endpoint activity usually exceeds that bar.
- Cross-Border Data Transfers – Shipping EU employee data to U.S. servers without safeguards (like SCCs or DPF certification) is a compliance risk.
What’s the Actual Risk?
- Employee Pushback – Works councils in Germany, France, and other EU states are aggressive about employee monitoring.
- Regulatory Fines – GDPR penalties can reach €20M or 4% of global turnover. Even if your vendor is sloppy, you’re still on the hook as the data controller.
- Reputation Damage – Trust evaporates quickly if employees feel they’re being secretly surveilled.
Takeaway: If you have EU employees, stick to vendors who emphasize OAuth/API/SSO sources, separate personal vs. business data, and provide EU residency or compliant transfer models.
What to Ask Vendors
When evaluating SaaS discovery solutions, here are the buyer-guide questions that separate responsible discovery from noise and creepiness:
- What are your data sources? (OAuth logs, finance data, SSO logs are clean. Endpoint/browser agents are risky.)
- Can you de-duplicate and normalize app data?
- How do you separate business vs. personal use?
- What privacy guardrails are in place? (Consent, transparency, data minimization.)
- How do you prioritize findings? (Give me risk-ranked insights, not 400-line CSV dumps.)
Final Word
The best SaaS discovery tools should feel like turning on the lights in a messy room: illuminating, not overwhelming.
- Relevant means actionable visibility into sanctioned and unsanctioned SaaS.
- Noise is anything that makes you roll your eyes or wastes cycles.
- Privacy invasion is data collection that crosses ethical or legal lines.
- GDPR risk is the extra reason to demand privacy-by-design.
Choose a vendor that knows the difference — your IT team, your employees, and your auditors will thank you.
At YeshID, we believe discovery should build trust, not break it. That’s why our approach focuses on OAuth scopes, integrations, and real usage signals — not surveillance. If you want to see what relevant SaaS discovery looks like, schedule a demo or try out our FREE SaaS discovery tool (it doesn't capture any of your data - everything executes client-side).
When the Business Bullies Security & IT (and Wins)

For years, IT and Security have been the gatekeeper of the stack. If you wanted to buy a new SaaS app, you braced yourself for the checklist:
- Does it support SAML?
- Does it have SCIM?
- Does it plug into the security team’s identity matrix?
If the answer was no, your business case died before it left the room.
But something’s shifted.
The Business Isn’t Asking Permission Anymore
The AI wave has flipped the power dynamic. Marketing, Sales, HR, Ops—they’re no longer waiting for IT to give them a green checkmark. If the next-gen app that gives them an edge doesn’t have SAML or SCIM, they don’t care. They’ll swipe the corporate card, connect it to Google or Microsoft, and move on.
For the business, the tradeoff is simple:
- Faster access to innovation vs.
- Slower adoption because IT says “no SAML, no go.”
Guess which one wins when revenue’s on the line?
IT’s Old Weapons Don’t Work
The “security requirement” shield—once the ultimate trump card—has cracks. When every new AI tool is API-first and doesn’t bother with enterprise checklists, the old standards look less like security and more like shackles.
SAML and SCIM were designed for a browser-and-HRIS world. But the business lives in a multi-tenant, token-driven, microservice reality. AI agents don’t log in with passwords. They don’t get provisioned through SCIM. And forcing that model means forcing your company into the slow lane.
The Pressure is Real
CISOs and IT leaders are feeling something they’re not used to: pressure from above to bend. Not pressure from regulators. Not pressure from auditors. But from their own peers on the business side saying:
“Stop slowing us down.”
“Don’t keep us stuck on the old stack.”
“Figure out a way to secure this without making us buy enterprise SAML.”
“It’s an AI tool. It launched last week. Of course, it doesn’t support SAML.”
That’s new. And it’s uncomfortable.
A New Bargain
The new bargain is this: IT & Security can no longer play gatekeeper by default. They have to play enabler.
That means:
- Supporting OAuth- and API-first integrations.
- Governing access without demanding legacy SSO tax.
- Meeting the business where the new stack lives.
And guess what? You can. YeshID helps IT teams secure the modern stack without the baggage of SAML, SCIM, or inflated SSO bills. Book a demo and we’ll show you how to keep your colleagues happy and keep your security standards intact, no trade-offs required.
Death to the SSO Tax: Why Modern Identity Leaves SAML and SCIM Behind

If you’ve ever tried to enable SSO or user provisioning in a SaaS product, you’ve likely run into two familiar acronyms: SAML and SCIM. They’re old, clunky, and—if you’re a startup trying to support enterprise customers—expensive.
The so-called "SSO tax" isn’t just about software. It’s about time, implementation effort, and all the awkward handoffs between your app, your customers’ IdPs, and the consultants needed to make everything talk.
And here’s the kicker: it’s not getting easier. But it is getting replaceable.
The Case for Change
SAML and SCIM were built for a different world:
- SAML came out in the early 2000s—designed for browser-based login during a time when “cloud” meant Salesforce and not much else.
- SCIM emerged to automate user provisioning, but only if you stuck to its rigid schemas and limited provider support.
Today’s world looks very different:
- We rely on short-lived tokens, automated agents, and microservices.
- We operate in multi-tenant, API-first environments.
- And our users aren’t always humans—they’re AI co-pilots, scripts, or Slack bots.
So it’s no surprise that modern applications—especially AI-native and cloud-native ones—are turning away from the SAML + SCIM stack. Instead, they’re adopting:
- OAuth 2.0 / OpenID Connect for auth and identity federation
- Public APIs and webhooks for flexible provisioning and deprovisioning
- Event-driven automation and AI agents to handle repetitive identity tasks
This is not just a technical evolution—it’s a financial one. Because every time a vendor tells you “SAML is an enterprise feature,” that’s code for: you’re about to pay a 5-figure premium for something your IdP already supports natively through OAuth.
Why This Matters
For startups and SaaS builders: you don’t need to ship full SAML and SCIM support to offer enterprise-grade access control. If your customers use Google Workspace or Microsoft 365, you can leverage OAuth-based SSO that works out of the box—no consultants required.
For IT and security teams: you can stop paying for brittle integrations and group sync logic that only half works. Modern identity architecture is about API access, not checkbox compliance with legacy standards.
For compliance-minded orgs: just because SCIM is a “standard” doesn’t mean it’s the right standard. Many audits care more about what you do (automated provisioning, auditable offboarding) than how you technically implement it.
How YeshID Makes This Real
At YeshID, we’ve built an identity and access platform that’s designed for how companies actually operate today—not how they used to.
Here’s how we help modern teams leave legacy behind:
AI-Native Integrations (No SAML or SCIM Required)
Instead of forcing every app to support SCIM or SAML, YeshID uses AI agents to intelligently connect with apps via the APIs they actually offer—no matter how non-standard. You get provisioning, deprovisioning, and access management without waiting for a vendor to implement a SCIM endpoint.
OAuth-Based SSO with Google & Microsoft
Most modern orgs already use Google Workspace or Microsoft Entra (formerly Azure AD). Instead of paying extra for “enterprise SAML,” YeshID leverages secure, standards-compliant OAuth SSO that just works. No SSO tax. No XML gymnastics.
Workflow Automation Without the Lock-In
YeshID replaces brittle group-based access with policy-driven automation and reusable workflows, so you can enforce least privilege, onboard faster, and stay compliant—without hiring a dedicated IAM team or paying for hours of custom Okta consulting.
Ready for a Modern Identity Stack?
You don’t need to settle for legacy standards, and you definitely don’t need to pay for them. With YeshID, identity becomes accessible, intelligent, and cost-effective—finally.
YeshID product updates — August 2025

What’s new in August: faster, safer identity management
This month we focused on cutting down clicks, tightening least-privilege, and removing guesswork for IT & Security leaders at mid-sized businesses. You’ll see easier requests, cleaner imports, and clearer status across the product. Identity management should feel simpler—and safer.
TL;DR
- ⏱️ Scheduled access with start time, duration, reminders—now also in Slack—to reduce standing privileges.
- 🤖 AI imports: paste app lists or upload screenshots to generate clean CSVs in minutes.
- 🧭 HRIS improvements: bulk create/remove/unmap, better previews, and auto-refresh after sync.
- ✅ Approvals & audits: Approval Groups, sortable Access Requests, and precise responder tracking.
- 🔗 Integrations & reliability: smoother OAuth, API key auth, stronger pagination, service-account labeling, and branded login fixes.
Time-based access — least-privilege on a schedule
You can now request access for a specific window with a start date, start time, and duration. Approvers are notified at once, with a follow-up reminder if a request is still pending near the scheduled start. When the final approval lands, requesters get a clear confirmation, and task assignees are notified if any step is manual.
Already have access but need a higher role? Request temporary elevation, then we’ll automatically revert you to the original role at the end of the window.
You can also capture these details when users request from Slack. We populate the time zone from Slack (or your org), so schedules land where they should.
Why it matters: Fewer standing privileges, cleaner audits, and less back-and-forth.
How to try it: From an application, enable time-based access in Application settings and then submit a request (in the product or Slack).
AI imports for apps and users — from messy lists to clean CSVs
Add applications faster with AI Paste: drop a plain-text list and we convert it into a strict CSV—sanitized, validated, and ready to import. If the Owners column is blank, we default to your first administrator, and owners are now optional (we’ll still validate any emails you do include).
For users, you can upload screenshots of tables and we’ll OCR them into CSV, map the fields, and show clear, client-side validation with exact row highlights. If a mapping is tricky (think complex APIs), we automatically retry with added context—less tinkering, fewer retries.
Why it matters: Imports that used to take an hour now take minutes, with instant feedback when something’s off.
How to try it:
- Applications → Import and select AI Paste or CSV.
- People → Import and upload a CSV or screenshot.
/ima
HRIS: bulk actions, better previews, and smarter mapping
The HRIS employee table now includes search, sorting, and filters (unmapped, starting soon, leaving soon). You can bulk create, bulk map, bulk remove, and bulk unmap people directly from the table. Sync banners and status messages are clearer, and the table auto-refreshes when a sync completes—no page reloads needed.
We also made mapping smarter: HRIS syncs always map employees to existing users when emails match, even if you haven’t set filters yet. And when HRIS is your people source, we sync core and custom fields regardless of filters to keep records accurate.
Why it matters: Faster clean-up, fewer manual steps, and up-to-date people data.
How to try it: Go to People → Employees (or your HRIS integration) to review, filter, and take bulk actions.
Approvals & audits — clearer groups, quicker triage
Approvals are easier to design and easier to read:
- Approval Groups replace the older owners approach. Mix technical owners, groups, or individuals and drag-and-drop to order them.
- The Access Requests table is sortable again, so you can quickly triage by time, requester, app, or status.
- We’ve improved how we display who responded (including system-run automations) and when, so audits tell a complete story.
- Slack and Teams notifications now try all recipients even if one fails—fewer silent misses.
Why it matters: Faster approvals with less ambiguity and cleaner audit trails.
How to try it: Open any app’s Approvals section to configure; triage in Access → Requests.
Integrations, reliability, and branding — fewer surprises, more polish
We shipped a long list of improvements that reduce friction and make state visible:
- Integration management: A cleaner experience for configuring integrations, with clearer error messages and warnings when switching types. OAuth is more reliable (popup hand-off + timeouts), and there’s a new API Key auth option for services that require
Authorization: ApiKey …. - Pagination that just works: GraphQL cursors, offset/number paginators with repeat-detection, start-page controls, and friendlier limits for services with caps (e.g., when a provider only returns 50 per page). This also hardens SCIM imports that don’t follow specs perfectly.
- Sync visibility: Directory cards now show syncing status and sensible “last sync” times. Provisioning banners are clearer, and tables auto-refresh after imports complete.
- Service accounts: You can label application accounts as non-human (service/bot). This helps identity mapping and reviews focus on real users.
- Branding: Your logo and dark navigation now display correctly on the first visit to your login page.
- Housekeeping: Accepted app invites no longer linger as “pending,” and non-admin assignees on app tasks can view the app details they need to complete their work.
Why it matters: Less setup ambiguity, sturdier syncs, and a UI that reflects reality.
Admin tips
- Separate humans from bots: Mark known service accounts as non-human so reviews and “unmapped” counts stay accurate.
- Use scheduled access for sensitive roles: Require a duration and start time—especially helpful when approvals happen in Slack.
Closing
Our goal is simple: save you time while reducing risk. With scheduled access, AI-assisted imports, bulk HRIS actions, and clearer approvals, YeshID helps you run identity and access with confidence.
Have feedback or want to see a quick demo? Drop us a note—we’d love to hear what would save your team the most time next.
Scheduled Access — Even When the App Doesn’t Support It

In identity and access management, “least privilege” isn’t just a buzzword. It’s a survival strategy. The fewer standing privileges a user has, the less risk there is when something goes wrong. But sometimes users do need escalated access: an engineer debugging production, a finance lead running a one-time export, or a contractor helping with a migration.
That’s where Scheduled Access (sometimes called Just-In-Time (JIT) provisioning) comes in. Instead of handing out permanent admin rights, you grant them for a defined window of time—then they disappear automatically. No more “I’ll remove that later” promises. No more forgotten super-admins lingering in your environment.
Why Scheduled Access Matters
- Temporary privilege elevation: Give access only when needed, for only as long as it’s needed.
- Built-in compliance: Audit trails show who had what and for how long—a must for SOC 2, ISO, SOX, and beyond.
- Reduced attack surface: Time-boxed permissions mean fewer open doors for attackers.
Most platforms stop here: they’ll JIT-provision access to apps that support automatic provisioning and deprovisioning. If the app can’t do it, tough luck. You’re left with a reminder on a sticky note or a Slack message.
YeshID Takes It Further
With YeshID, Scheduled Access works even when the app doesn’t support it.
- For apps with SCIM, APIs, or connectors: we’ll provision and deprovision automatically at the scheduled times.
- For manual apps without automation: YeshID will track the schedule and remind you (via Slack, Teams, or email) to remove that access. We don’t just help with the easy cases—we keep you accountable for the messy ones too.
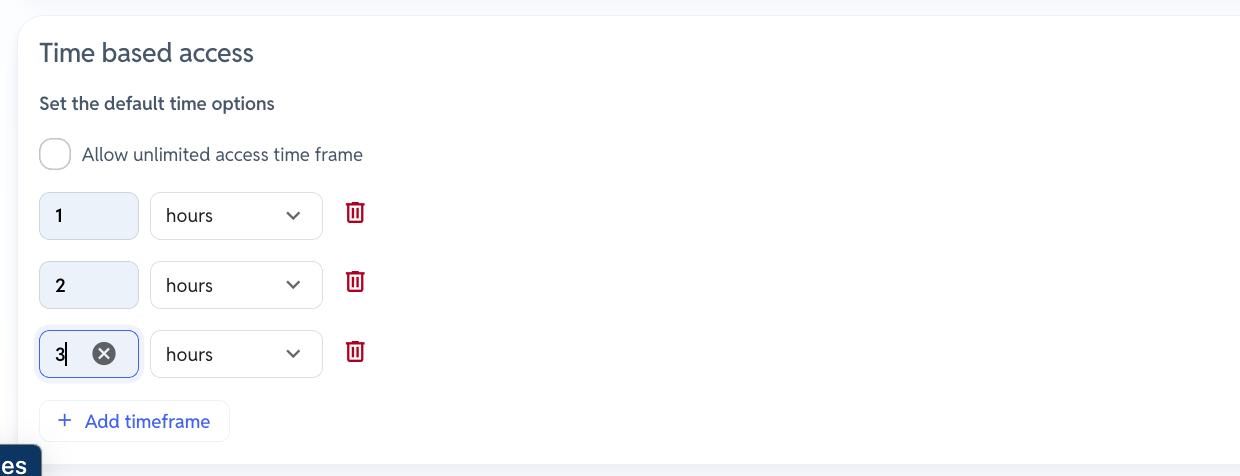
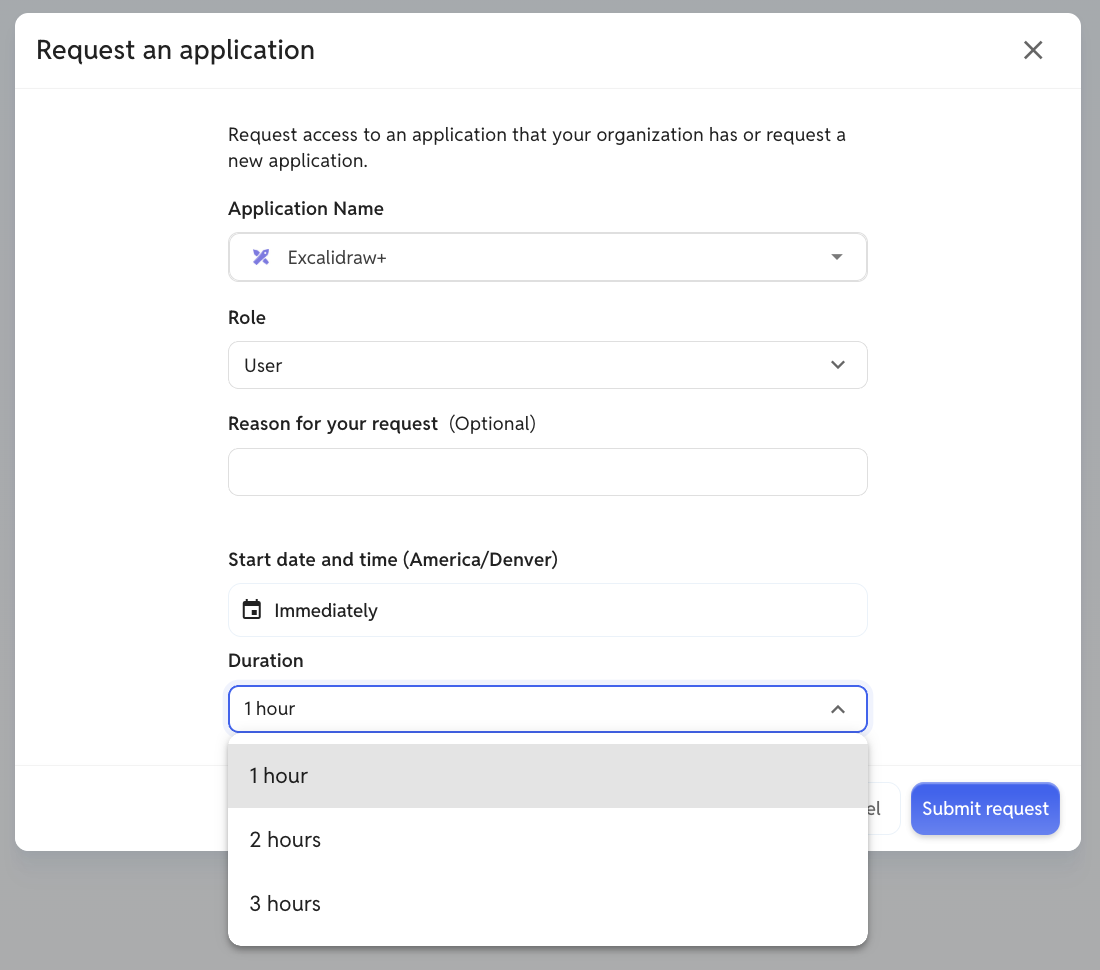
That means your access review is complete, your audit trail is clean, and your IT team doesn’t have to rely on memory or best intentions.
Closing the Gaps
The reality is most companies live in a hybrid state: some apps integrate seamlessly, and others don’t. Scheduled Access with YeshID closes that gap. Whether the app is automated or manual, you’ll always have a consistent, reliable way to:
- Approve temporary access
- Enforce time limits
- Get nudged to clean up when automation isn’t possible
It’s a simple but powerful way to keep privilege creep in check—without slowing your team down.
YeshID Scheduled Access is now in Beta for the YeshID Business package. If you’re tired of relying on sticky notes, calendar reminders, or good intentions to track temporary permissions, we’d love for you to try it.
Choosing the Right Identity & Access Management Approach for SMBs

When you’re running IT and security for a small or mid-sized business, your identity and access management (IAM) strategy will make or break your operational efficiency, security posture, and compliance readiness.
For most SMBs, the starting point is obvious: you’re already on Google Workspace or Microsoft 365. These platforms give you MFA/2FA out of the box, act as your primary login for many SaaS tools, and—if you’ve invested in the right tier—offer basic SAML support. But what happens when you need to go beyond the basics?
The market offers several paths—each with strengths and trade-offs. Let’s break them down.
1. Google or Microsoft Alone
What it is:
Use your existing Google Workspace or Microsoft Entra ID as your only identity provider. MFA/2FA is baked in. SSO via OAuth or limited SAML handles authentication for most apps.
Pros:
- Low to no extra cost—already part of your productivity suite
- Simple setup for small teams
- MFA included, so you’re compliance-ready for many frameworks
Cons:
- Limited automated provisioning and deprovisioning
- No granular, per-app approval workflows
- Weak shadow IT visibility
- Lifecycle management often manual
Best For:
Small orgs (<50 employees) with light SaaS usage, light employee-churn, and minimal compliance burden.
Where YeshID Fits:
By layering YeshID on top of your Google or Microsoft IDP, you keep the simplicity while adding AI-driven automation, access reviews, shadow IT detection, and per-app workflows—without a costly SSO upgrade.
2. Google/Microsoft + MDM-Focused Solution (e.g., JumpCloud)
What it is:
Combine your IDP with an MDM-centric tool like JumpCloud to add device management and an optional directory service.
Why MDM Matters for Security & Compliance:
- Remote lock/wipe of lost or stolen devices
- Device posture checks (OS version, encryption, antivirus)
- Removal of local admin rights
- Enforcing disk encryption for SOC 2 / ISO 27001
Pros:
- Strong endpoint compliance controls
- Single vendor for MDM + directory
- Good for replacing on-prem Active Directory
Cons:
- SaaS lifecycle automation is still limited
- App provisioning is mostly SCIM/SAML-only—API/manual gaps remain
- No built-in access request workflows
Best For:
Orgs prioritizing endpoint security and compliance, especially those migrating away from AD.
Where YeshID Fits:
YeshID pairs with your MDM to handle the SaaS side of the equation—automating provisioning/deprovisioning, managing approvals, and surfacing shadow IT—while MDM keeps devices compliant.
3. IDP + IGA Provider (e.g., Lumos, Nudge, SailPoint, etc.)
What it is:
You keep your IDP (Google, Microsoft, or Okta) and add an Identity Governance & Administration (IGA) platform for access requests, reviews, and some provisioning.
Pros:
- Better user experience for requesting access
- Broad SAML coverage if paired with Okta or a similar IDP
- Strong compliance alignment for regulated industries
Cons:
- Expensive—both in licensing and maintenance
- Complex deployments that often require professional services
- Limited flexibility for OAuth-first or API-based apps without heavy admin work
- Not AI-native—manual upkeep scales poorly
Best For:
Enterprises with large budgets, heavy SAML usage, and dedicated IT staff.
Where YeshID Fits:
YeshID delivers the same governance outcomes—SSO, provisioning, approvals—at lower cost, with faster deployment, and AI-native automation that works across SAML, SCIM, API, and even manual steps.
4. YeshID + Google/Microsoft
What it is:
Pair your existing Google Workspace or Microsoft Entra ID with YeshID’s AI-native IAM platform. Use your preferred MDM for endpoints and let YeshID handle SaaS lifecycle management.
Pros:
- No SSO tax—use OAuth where possible, SAML only when needed
- Works with SCIM, API, and manual provisioning in a single workflow
- Fast deployment—connect IDP and start automating Day 1
- Compliance-friendly audit trails, access reviews, and shadow IT detection
Cons:
- Requires an existing IDP (Google/Microsoft)
Best For:
SMBs with mixed SaaS stacks, compliance requirements, and limited IT headcount who need automation without a full replatform.
Why It Wins:
YeshID combines the compliance-ready MFA/SSO you already have with AI-native orchestration, granular per-app workflows, and lifecycle automation—delivering a modern IAM experience without the legacy complexity or price tag.
For SMBs, IAM isn’t just about logging in—it’s about keeping your people productive, your data secure, and your compliance box checked without drowning in admin work. Whether you start with just Google or Microsoft, pair it with MDM, or layer in a governance tool, the goal is the same: unify identity, control access, and automate as much as possible. YeshID delivers that balance—pairing the MFA and SSO you already have with AI-native automation, per-app workflows, and full SaaS lifecycle visibility—so you get enterprise-grade IAM without enterprise-grade complexity or cost.
New in YeshID: HRIS + Triggers and Per-App Approvals

Orchestrate onboarding, offboarding, and approvals your way — without breaking your existing processes.
If you’ve ever worked in IT, you know the pain:
HR says someone started yesterday, but you never saw the ticket.
A Slack message says “New hire in Marketing!”… but no role, no start date, no nothing.
Or worse — your apps already created the account without telling you.
The truth is, every company moves people data differently:
- Some sync new hires from an HRIS like Rippling straight into Google Workspace.
- Others push everything into Okta first, then out to the rest of the stack.
- Some want HR to send data directly into YeshID.
Until now, that variability often meant extra work (and missed steps). So we built a more flexible, trigger-driven way to connect the dots.
HRIS + Triggers: Your Process, Automated
YeshID now integrates with any HRIS that has a well-documented API — thanks to our AI Integrator — and supports flexible triggers so you can kick off onboarding or offboarding exactly when and how you want.
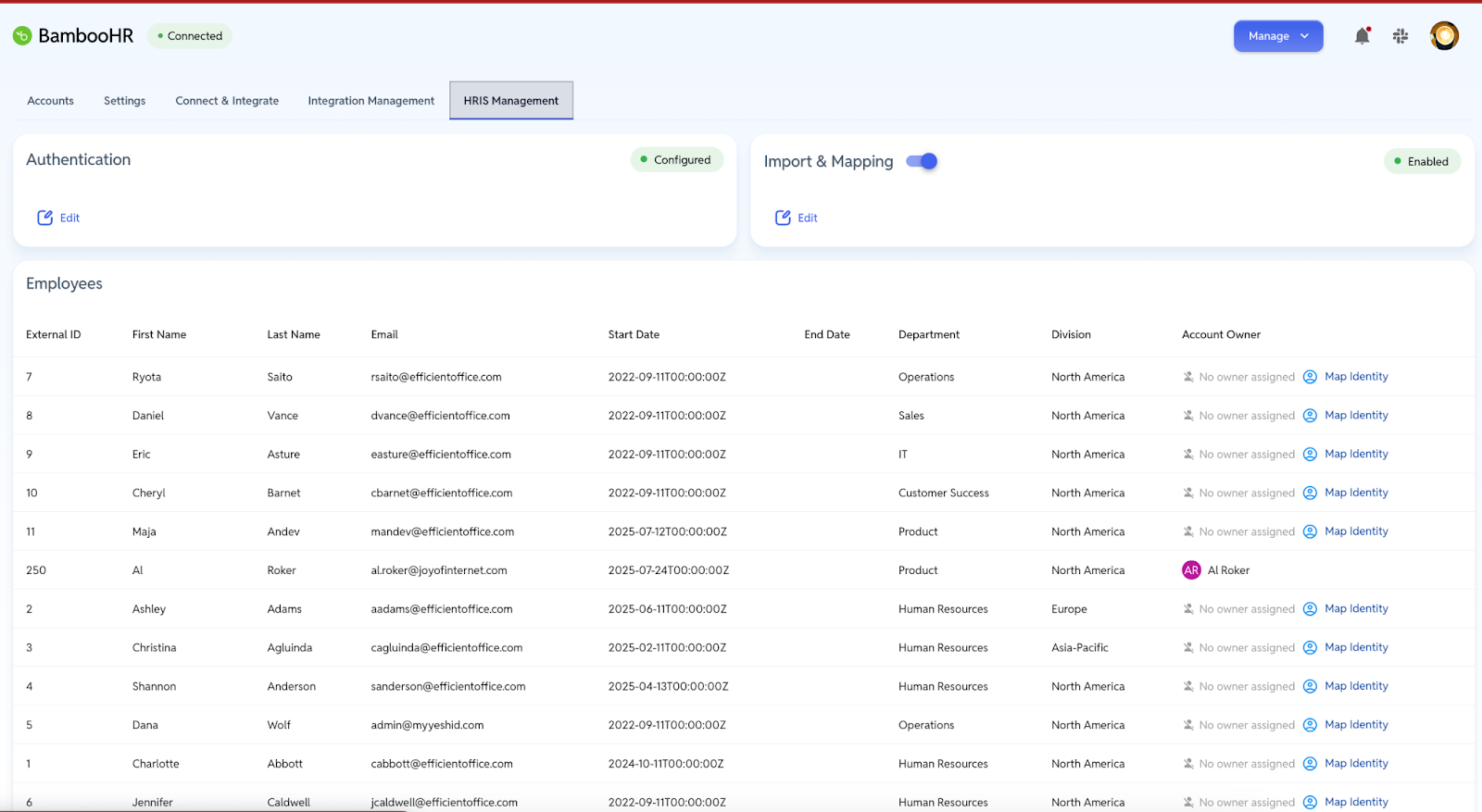
Example:
“When a new active user appears with the Department = Engineering, run the Engineering Onboarding workflow.”
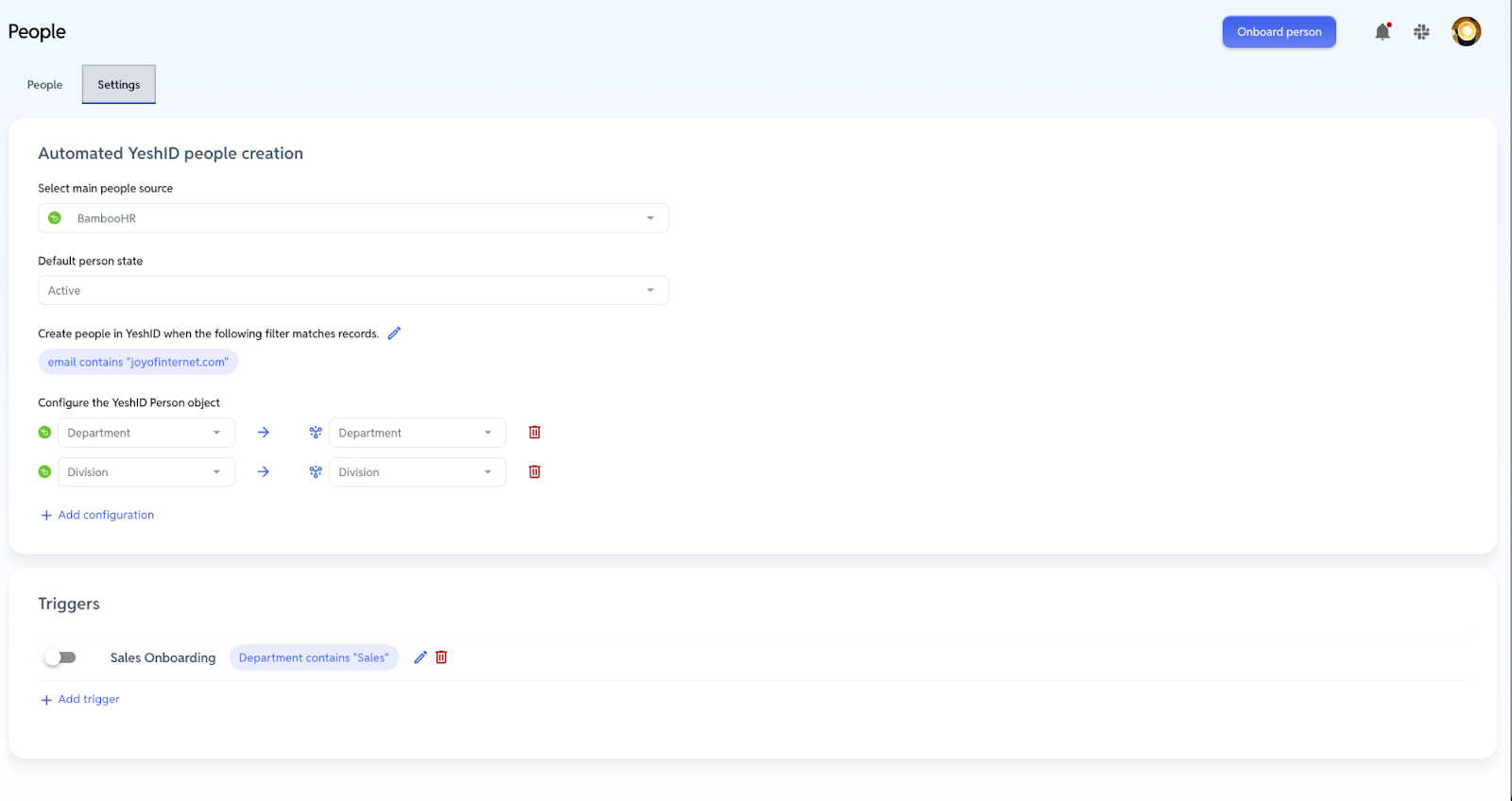
This means:
- No more waiting for the “right” source — we can pull from Okta, Google, Microsoft, or your HRIS directly.
- No more one-size-fits-all logic — your triggers match your org’s maturity and process.
- Onboarding and offboarding stay consistent, visible, and auditable.
HRIS + Triggers is available now in our Business package.
Per-Application Approvals
Not every app can be granted on the spot — some require a manager’s OK, finance sign-off, or a security review before provisioning. Now you can set custom approval lists for each application inside YeshID.
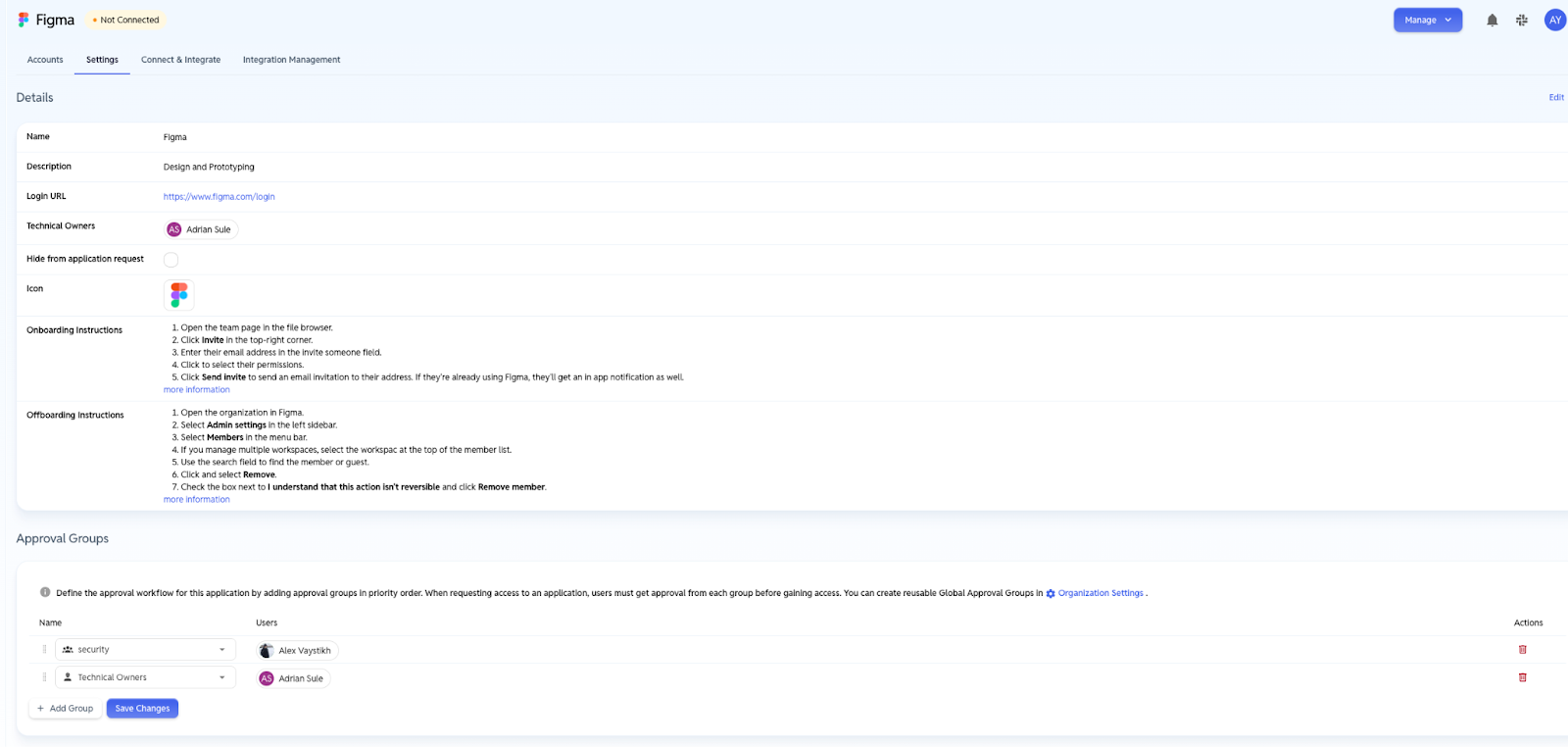
How it works:
- Define who needs to approve a request (per app).
- Users request access via our Slack bot.
- Requests route through the right approvers automatically.
- Provisioning kicks in only when the green light is given.
Approvals are available in both Growth and Business packages.
Why It Matters
With HRIS + Triggers and Per-App Approvals, you can:
- Orchestrate your process your way — no forced replatforming.
- Stay compliant with consistent, auditable workflows.
- Reduce human error by letting automation handle the handoffs.
It’s all about making YeshID fit into the way you already work — while giving you the power to tighten controls, cut noise, and move faster.
Ready to see it in action?
Book a live demo and we’ll connect your HRIS, set up a trigger, and run a workflow — all in one session.
July 2025: Release note

🚀 July 2025 Release Notes – Automate People Ops & Save More
This month we focused on making it effortless to move people in, around, and out of your organization—while giving finance a pleasant surprise. Here’s what’s new for our mid-sized business customers:
- 🏢 HRIS-powered People Automation: Plug in your HR platform to automatically import employees, map fields, and set rules that trigger onboarding or offboarding workflows the moment a status changes—no spreadsheets, no manual hand-offs.
- 🤖 Smarter, Simpler Integrations: A redesigned integration hub lets you visually map fields, auto-generate configs, and preview data before you commit. Bonus: the Slackbot now activates without a separate Slack app install, and new Airtable SCIM & Canva de-provisioning options keep every user in sync.
- 💸 Lower Growth Plan Pricing & Flexible Billing: Growth plan drops to $5 per user/month (or $54 per user/year), and you can disable per-seat billing when you’re invoiced annually—freeing up budget for the things that matter.
- 🔐 One-click Directory Password Resets: Reset and email temporary passwords across Google, Microsoft, and Okta directly from YeshID, slashing recovery time and getting users back to work faster.
- ✉️ Fresh Look, Clearer Alerts: Re-branded email templates, a larger groups selector, and new notification toggles for “user created” and “status change” events keep admins informed—without the clutter.
————————
Which update will save your team the most time?
Stay secure,
The YeshID Team
Why Identity & Access Is the First Project Every New IT Leader Should Tackle

And how YeshID helps the IT department of one scale like a team of ten
So you just became IT.
Maybe you’re the first formal hire. Maybe you were in ops, engineering, or security and got handed the badge. Either way, you’re now the unofficial Department of Everything: onboarding, app access, device setup, compliance prep, procurement, and the constant “Can you add me to X?” Slack pings.
When you're juggling all of that, it’s easy to put off longer-term initiatives. But here’s the thing:
Identity and access is the one project that makes everything else easier.
And YeshID was built for exactly this moment.
The Problem: You Can’t Scale What You Can’t See or Control
In most growing companies, access management looks like this:
- Onboarding via Slack and Notion checklists
- App access tracked in someone’s brain
- Admin rights scattered across teams
- Deprovisioning based on memory and luck
- Former contractors still showing up in Google, GCP, or AWS
This isn’t just inefficient—it’s risky, expensive, and a compliance problem waiting to happen. And if you're the only one holding it all together, you're both the bottleneck and the blast radius.
Why Identity & Access Should Come First
If you’re deciding where to start, here’s why access should be at the top of your list:
- Central control over user access across tools
- Faster onboarding and offboarding without human error
- Visibility into who has access to what, and why
- Audit readiness without last-minute scrambles
- A foundation for device management, security tooling, and app governance
How YeshID Helps the IT Department of One
Most identity tools were built for massive enterprises—with months-long deployments, heavy engineering lift, and a price tag to match.
YeshID is different.
We’re the AI-native identity platform built specifically for lean teams who need to move fast and stay sane. Here's how:
Fast Setup and Immediate Value
YeshID connects to Google Workspace or Microsoft 365 in minutes—no SAML migration required—and automatically maps access across your SaaS stack.
AI-Driven Workflows Without Writing Code
Build custom workflows for onboarding, offboarding, and access requests in minutes. Approvals, app provisioning, Slack notifications—it’s all drag-and-drop, not dev-and-wait.
Real Visibility Into Shadow IT and OAuth Sprawl
Uncover the apps employees are signing into with Google or Microsoft accounts—many of which won’t show up in your SSO. Understand who granted access, what scopes were included, and revoke tokens directly.
Integrations Without the SAML Tax
You don’t have to rewrite your entire app stack to get value. Our AI integration engine lets you connect to apps through APIs, not just SAML or SCIM.
Compliance-Ready Logs and Policies
Access logs, approval trails, and policy enforcement are built-in from day one—so you’re not scrambling come audit season.
You Don’t Need a Big Team. You Need Leverage.
You don’t need to hire five people. You need five hours back every week.
You don’t need hundreds of workflows. You need the three that matter.
You don’t need more admin tools. You need a smarter, AI-native approach to access.
YeshID gives you that leverage—so you can stop being the bottleneck and start being the builder.
Start Here
Identity and access is the root system of your IT stack. Nail it now, and everything else—from security to SaaS management to onboarding—gets easier.
YeshID is here to help you move fast, stay secure, and look like a team of ten—even when you're still a team of one.
From Zero to Secure in 5 Minutes: The Fastest Way to Deploy YeshID

Most companies spend months trying to automate everything. But here’s the truth: if you’re a mid-sized company, full automation is a myth—unless every single one of your apps supports SCIM (and you’re paying for the enterprise tier). Spoiler: they don’t.
That’s why the fastest way to secure your environment isn’t automation. It’s orchestration.
Start by making your core identity workflows—onboarding, offboarding, and access requests—repeatable, visible, and auditable. Then you can optimize the hell out of them.
And with YeshID, you can do that in under 5 minutes.
Step-by-Step: Secure in 5 Minutes Flat
Here’s how you get going—fast.
1. Connect your directory (30 seconds)
Choose Google Workspace or Microsoft 365. One click. Grant permissions.
Boom—you now have full visibility into your users, and (bonus!) a list of apps they’re logging into.
2. Upload your app list (30 seconds)
Grab that Notion doc, spreadsheet, or finance tracker listing the SaaS apps you're paying for.
Drag. Drop. Done.
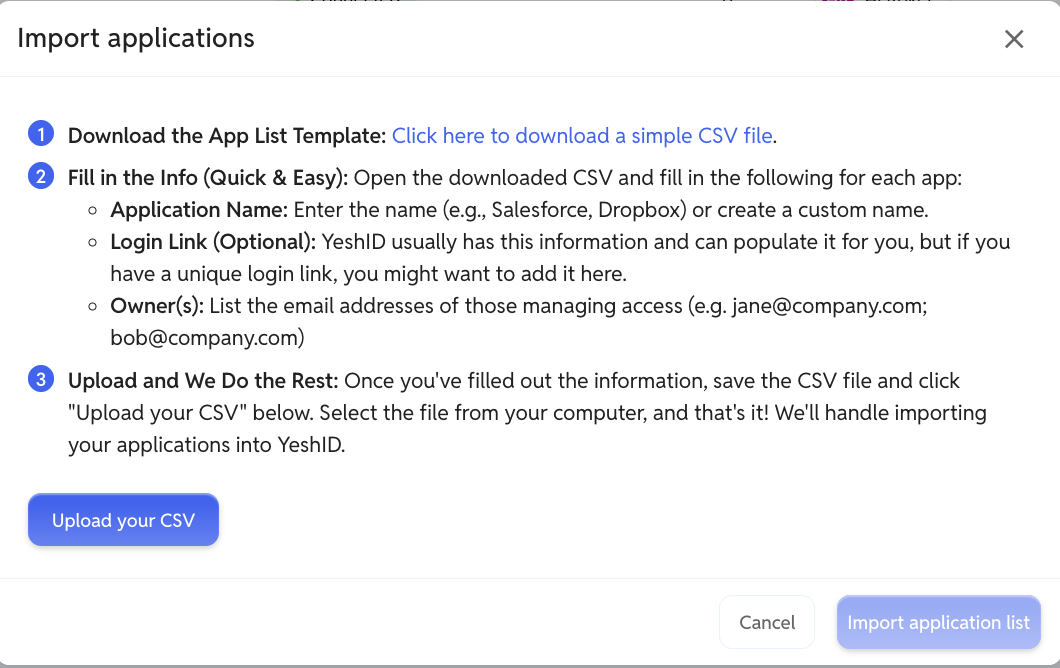
3. Turn your onboarding checklist into a workflow (30 seconds)
Paste your onboarding steps into our AI agent.
We’ll build an orchestrated onboarding flow that actually runs, not just sits in a doc no one follows.
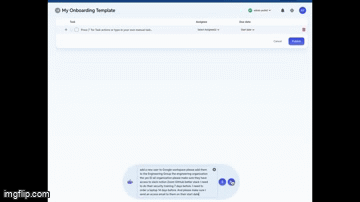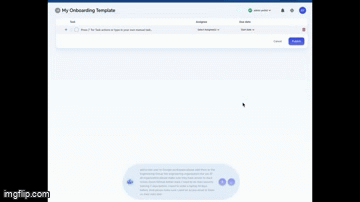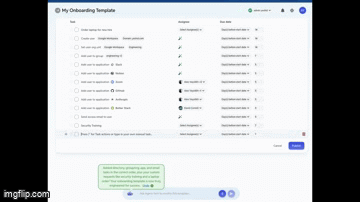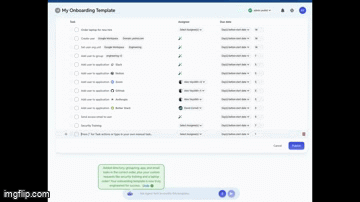
4. Create your offboarding template (30 seconds)
Use ours or customize your own. Either way, you now have a standard, repeatable way to lock things down when someone leaves.
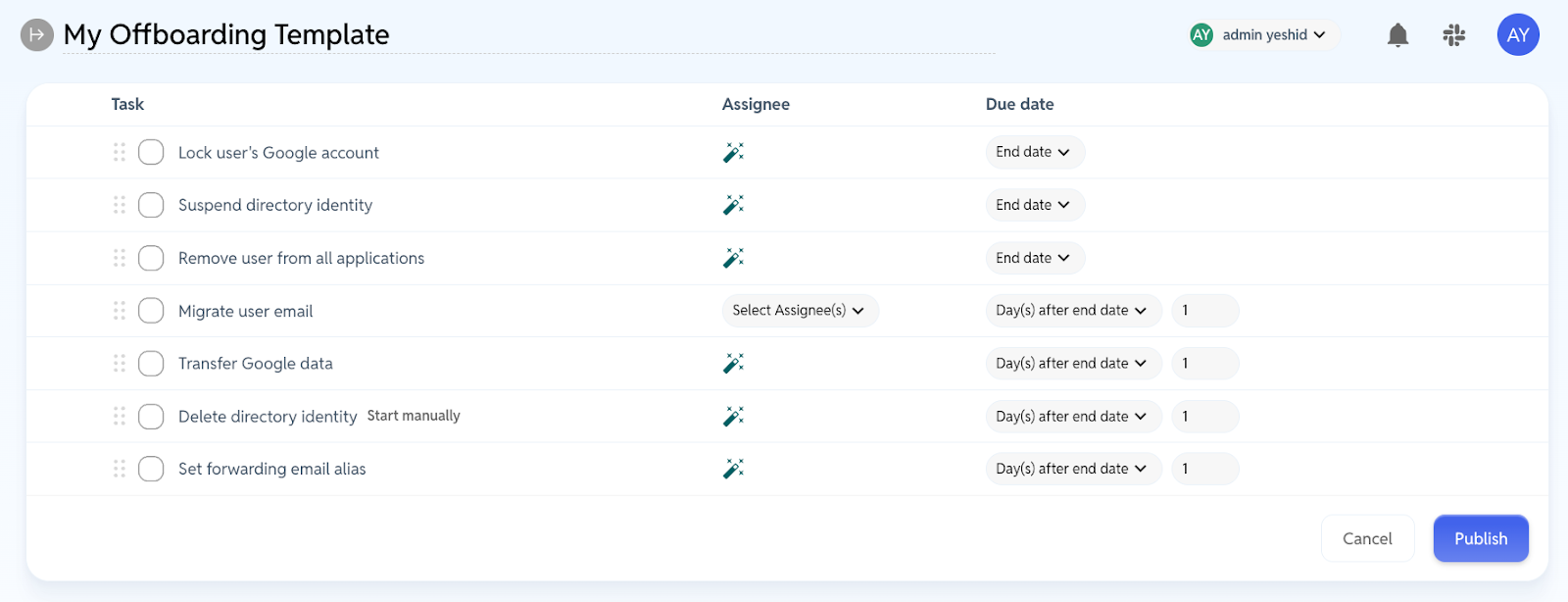
5. Install the Slack (or Teams) app (1 min)
Employees can now request access the right way, every time.
It’s auditable, consistent, and—yes—compliant (hello, SOC 2 and ISO 27001).
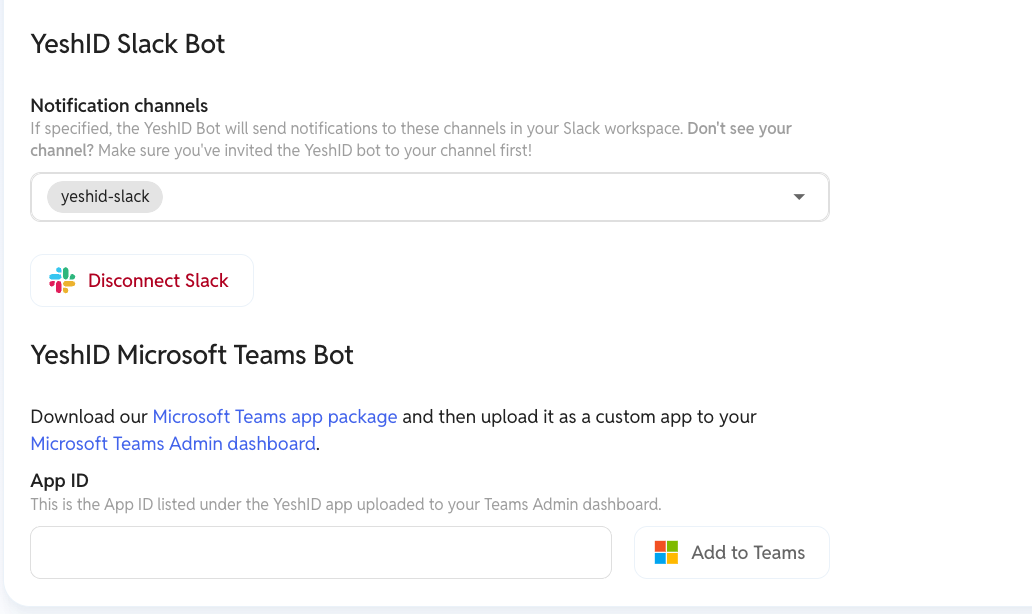
Congratulations, you now have:
✅ All your apps in one place
✅ A consistent onboarding & offboarding process
✅ Logging and visibility
✅ A real access request system (no more “Hey can I get access to X?” in Slack)
This is the foundation. It’s what gets you secure—and keeps your auditors happy.
What About All the Existing Access?
Ah, the fun part: figuring out who already has access to what.
YeshID helps you speed that up too:
- API support? Use our AI-powered integrator to pull in live access lists.
- No API? Upload CSVs—we’ll parse and standardize them with our LLM tools.
- No time? Delegate to the app owner. They can manually confirm who should have access.
TL;DR
Don’t wait six months to get value. In five minutes, you can go from zero to secure:
- Connect your directory
- Upload your app list
- Build repeatable workflows
- Add access request flows
- Start running your org like a real security team
Automation is a journey. But orchestration? That starts today. Try YeshID free → and stop duct-taping your identity process together.
Streamlining Identity & Access Management for Dunder Mifflin

Streamlining Identity & Access Management for Dunder Mifflin
At YeshID, we understand Dunder Mifflin’s focus on enhancing infrastructure efficiency, strengthening security controls, and optimizing operational costs as you continue scaling your fully cloud-native workforce. With a nearly 100% SaaS-based environment and increasing emphasis on strong IT management, our partnership provides a tailored identity and access management solution designed to integrate seamlessly into your existing technology stack. Sitting on top of your Microsoft IDP, YeshID helps you manage lifecycle processes end-to-end, ensuring clear visibility and reliable assurance that offboarding procedures are executed accurately, while also addressing your growing access review needs to maintain SOC 2 compliance.
Here’s how YeshID will directly address your immediate needs and long-term objectives:
1. End-to-End Lifecycle Management & Automation
With approximately 20 onboardings and 15 offboardings per month, we recognize your challenges with limited flexibility and manual effort in your current provisioning processes, especially across your large SaaS ecosystem.
How We’ll Help:
- Automated Onboarding & Offboarding: Seamlessly create, update, and disable accounts across Entra ID and integrated third-party SaaS applications, reducing manual overhead and eliminating risk.
- Direct HRIS Integration: Integrate with your HRIS to trigger provisioning events and streamline employee onboarding automatically.
- AI-Powered App Integration: Automate access management for apps without native SCIM/SAML support, eliminating the need for costly custom development.
- Defined Task Templates & Approvals: Reduce delays and missteps by clearly assigning manual tasks with visibility and accountability via Teams or Slack integrations.
2. Enhanced Visibility & Shadow IT Prevention
With a workforce that heavily relies on SaaS applications, ensuring oversight into unsanctioned app usage and OAuth access is critical.
How We’ll Help:
- Real-Time OAuth Visibility: Gain deep insight into OAuth permissions and usage, proactively identifying risk.
- Natural Language Policy Alerts: Stay on top of identity-related risks with alerts like "notify me if MFA is turned off."
- Centralized Application Oversight: Maintain a full picture of who has access to what, across both approved and unmanaged apps.
3. Robust Access Reviews & Audit Readiness
SOC 2 compliance means you need rigorous access review and offboarding practices that are well-documented and easily verifiable.
How We’ll Help:
- Streamlined Access Reviews: Run flexible, frequent reviews that support CSV imports and detailed ownership tracking.
- Audit-Proof Offboarding: Maintain detailed logs and ensure every identity-related action is traceable.
4. Contractor Lifecycle Management
If you work with contractors or seasonal workers, managing their access often requires pulling attributes from multiple systems.
How We’ll Help:
- Customizable Contractor Workflows: Set up flexible workflows and sync attributes from multiple sources to provision contractors quickly and cleanly.
How Quivo Cut Onboarding Time in Half (and Stopped Compromising on Security)

Before YeshID: Tribal Knowledge and Time-Consuming Tasks
Quivo is a global 3PL logistics provider with operations in six countries and a growing workforce of 300–400 employees. Their IT team is unusually large for a logistics company—30 people strong—due to in-house development of most systems.
But for all that technical depth, onboarding and offboarding were still stuck in manual mode.
“The process was very informal,” said Ian Kyslytsya, IT Infrastructure Team Lead. “It involved a lot of manual steps that only me and Ben—who’ve been here the longest—knew how to do.”
It wasn’t just time-consuming. It was risky.
- Each onboarding had 20+ steps.
- Provisioning access involved writing the same repetitive updates over and over.
- Junior IT staff needed extra guidance to avoid missing something critical.
“It was very exhausting to type everything each time,” added Ben, Senior System Administrator. “Just repetitive toil—and easy to make mistakes.”
After YeshID: Scheduled Starts and Smoother Hand-offs
Quivo adopted YeshID to bring structure and automation to the chaos. With their team already deep in the Google Workspace ecosystem, the default YeshID automations worked immediately—no need for custom integrations.
“YeshID allowed us to formalize our process,” said Ian. “The templates help automate repetitive tasks, and the scheduling feature is critical for us.”
Why? Because Quivo operates across multiple time zones. Previously, they’d often give employees access on Friday—even if they didn’t start until Monday—just to avoid the Monday morning rush. Now, onboarding is scheduled for the right moment, even while IT sleeps.
The Results
✅ 50%+ time savings
“YeshID cuts the time at least in half,” said Ian.
“I’d argue it’s even more,” added Ben. “Automations for Google run in under two minutes.”
✅ Fewer errors, less stress
“There are fewer errors. The work is more efficient. My colleagues have more time for other tasks,” said Ian.
✅ Happier employees (and HR)
A smoother onboarding experience means fewer hiccups—and less fire-fighting on day one.
✅ Easy implementation
“We didn’t have to change our existing workflows,” said Ben. “It fit right into our ticketing system and made life easier.”
What They’d Tell Another IT Team
“It’s a must-have if you’re using Google Workspace as your IDP,” Ian said. “It helps automate and streamline onboarding and offboarding.”
And when asked how they’d describe YeshID at a cocktail hour?
“Simple,” Ian replied. “Less stress. Fewer errors. More sleep.”
The Cost of Doing Nothing: Why Manual Access Management Is Risky, Wasteful, and Slowing You Down

Doing Nothing Isn't Neutral—It's Expensive
When it comes to provisioning and deprovisioning, most companies still rely on:
- Checklists
- Slack messages
- Shared spreadsheets
- Or, worse… hoping someone remembers to “clean things up”
And that’s not just a process issue. It’s a business risk and a budget leak.
Here’s what “doing nothing” really costs you.
Time You Don’t Have
Manual provisioning (setting up accounts and access across apps) and manual deprovisioning (removing that access) takes time—especially if you’re logging into 10–15 different tools per employee.
Let’s say it takes:
- 30 minutes to onboard someone
- 20 minutes to offboard someone
- You’re onboarding/offboarding just 10 people per month
That’s 8+ hours per month—a full workday—gone. And that doesn’t include chasing people for approvals or dealing with forgotten tasks weeks later.
For IT teams of one (or overstretched ops folks), that’s time you could be using to fix issues, improve security, or just breathe.
License Waste (a Silent Budget Killer)
When someone leaves the company, how often are all their licenses actually revoked?
Spoiler: rarely.
Whether it's Figma, Notion, Salesforce, or Slack, orphaned accounts add up fast.
Let’s do a quick napkin math:
- 10 unused licenses at $25/month = $250/month
- That’s $3,000/year, per app
- Multiply that by 3–5 apps? You’re easily leaking $10K–$15K/year in unused SaaS spend
All because someone didn’t get deprovisioned properly.
Compliance Risk You Can't Afford
If you're SOC 2, ISO 27001, or HIPAA-bound, auditors will ask:
- Who had access to what?
- When did they get access?
- Who approved it?
- Was it removed in time?
If you’re managing access by hand, in a spreadsheet or Slack thread, good luck tracking that down quickly.
Doing nothing means scrambling during audit season.
And scrambling means stress, gaps, and potential findings.
MSFT and Google SSO is a great start, but…
It doesn’t manage what access your users have to inside tools. And it definitely doesn’t:
- Automatically grant the right access on day one
- Revoke licenses when someone leaves
- Track approvals and role changes
- Run clean, repeatable offboarding workflows
SSO is just the front door.
You still need to manage the keys to every room inside.
What’s the Alternative?
You don’t need a huge security budget or a heavy-handed IT platform like Okta to fix this.
With tools like YeshID, you can:
- Orchestrate (and automate) your onboarding and offboarding across your apps
- Create reusable approval workflows without building from scratch
- Track who has access to what, and when it was approved
- Save hours every month and thousands in SaaS waste
And yes—it works with Google Workspace and Microsoft 365.
The Real Cost of Doing Nothing
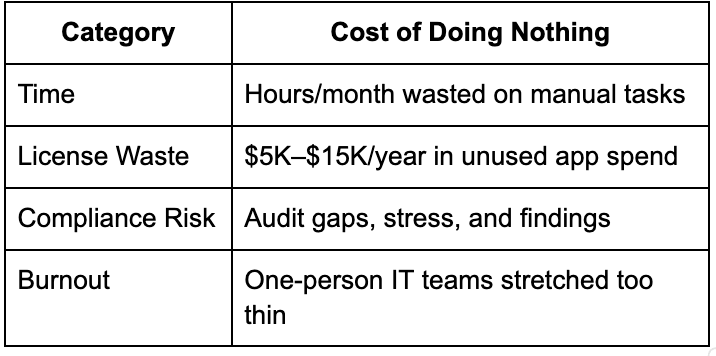
Want to See What It’s Costing You?
Use our ROI Calculator to see how much time and money you could save by automating access with YeshID.
Doing nothing may feel easier in the moment—but over time, it’s the most expensive decision you can make.
Why Use YeshID Before Migrating Domains

Migrating domains is a high-risk moment for identity and access. It's the perfect time to lay the right foundation, not scramble after the fact. Here’s why starting with YeshID before the move is a smart call:
Domain migrations often break identity mappings — leading to failed logins, broken app access, and messy user duplication. With YeshID you get centralized visibility and control across all identities and apps before the domain switch. That means no scrambling after to fix broken access — you’ve already mapped what should exist.
Unified Identity Graph Makes Remapping Easier
- YeshID builds a universal identity graph — linking accounts across apps (including ones tied to old domains).
- When you switch domains, you don’t lose the connection between user → access → resources.
- You maintain continuity and auditability during the transition, with no blind spots.
Pre-Migration Access Reviews Save Pain Later
- Doing an access review before migration lets you clean up dormant accounts, unused permissions, or apps tied to the old domain.
- That makes your domain cutover cleaner, and reduces risk from orphaned or forgotten access.
Workflows Can Smooth the Migration
You can automate the domain switch via YeshID workflows:
- Provision new domain users across apps
- Deprovision old domain users safely
- Send Slack/Email notifications to users
- Trigger verification tasks (e.g. MFA reset)
- No more manual checklists in spreadsheets.
You’ll Never Have More Attention on Identity Than Right Now
A domain change already forces everyone to think about identity and access.
Don’t waste that momentum — use it to adopt a more future-proof, AI-native IAM foundation now.
YeshID turns domain migration from a painful IT cleanup into a secure, structured transformation. Instead of patching things reactively, you take control before the chaos hits.
Why Modern Schools Need Vsibility, Control, and Simplicity Around IAM

The Problem
Today’s schools rely on a growing number of apps—email, HR platforms, learning tools, admin systems—all of which require managing user access. But many schools still rely on spreadsheets, manual processes, or outdated systems to control who gets access to what. This leads to:
- Limited visibility into app usage and access
- Slow onboarding and offboarding of staff and substitutes
- Lingering accounts with access after staff depart
- Wasted costs from unused licenses and over-provisioning
- Over-reliance on IT for routine access changes
Why It Matters
Visibility You Can Trust
Without a clear view, you don’t know which users still have access to critical apps—or whether that access is still appropriate. This is a major security and compliance concern, especially for systems that store sensitive data.
Speed & Simplicity for Admins
Schools often need to grant access quickly—for new teachers, part-time staff, or substitutes. With YeshID, these tasks don’t require IT intervention. School administrators can make changes themselves with an easy-to-use interface and simple workflows.
Cost-Effective Access Management
Every unused license is money wasted. YeshID helps schools stay lean by showing which accounts are active and which aren’t—helping you right-size your software spend.
Why YeshID
YeshID is a modern identity and access platform designed to give schools:
- Clear visibility into who has access to every app, inclusive of shadow applications —no more spreadsheets or guesswork
- Custom workflows to automate onboarding/offboarding for staff, substitutes, and contractors
- Role-based access that reflects how your school is actually structured
- Ease of use, so even non-technical school administrators can manage access confidently
- Cost controls through smarter provisioning, cleanup, and license management
- AI-first design that automates repetitive tasks and flags potential risks before they become problems
Review by Role: A Smarter Way to Run Access Reviews

Access reviews are essential—but let’s be honest: they’re often painful.
Bloated role lists. Confusing UI. Long spreadsheets. Unclear next steps.
Especially when you're reviewing access to SaaS tools that have dozens (sometimes hundreds) of role types—most of which your team never uses.
That’s why we built Review by Role: a smarter, cleaner way to manage access reviews in YeshID.
Smarter Role Definitions = Less Noise
Most SaaS apps don’t curate the roles they expose via API. You might see 80 different roles in an app, even if your team only uses 5 of them.
YeshID now lets you:
- Define which roles matter for your org in each app
- Hide irrelevant roles from access request and review workflows
- Customize what users can request—so employees see only the roles they’re actually allowed to request


Real-Time Access Visibility, Anywhere
Access reviews don’t work without accurate data.
YeshID now supports three flexible ways to fetch access from any app:
- Direct API integrations: If there’s an API, we can connect to it
- AI-powered CSV importer: Point us to a file, and our AI will interpret and structure the user data automatically
- Manual entry: Just want to track a few accounts? You can now update users manually without building out an integration
This means you can run access reviews across all your apps—not just the ones with SAML or SCIM.

Mid-Review Role Changes and Action Tracking
Ever start a review and realize someone needs to be moved from Viewer to Editor?
Now you can:
- Change a user’s role as part of the review
- Track every change you need to make—whether it’s a permission downgrade, a deprovisioning task, or a re-assignment
And YeshID automatically builds a post-review action list, so your IT or Security team knows exactly what needs to happen next.


What This Means for You
With Review by Role, you can:
- Cut through the noise of long role lists
- Run faster, more accurate access reviews
- Reduce reviewer fatigue
- Stay compliant across more apps
- Take action directly from the review screen
It’s a better way to run access reviews—and it’s live now in YeshID.
Want to see it in action? Request a demo and we’ll walk you through it.
Avoid the SSO Tax: What It Is, Why It’s Dumb, and How We Fixed It

Managing access to SaaS applications shouldn’t be a tradeoff between cost, complexity, and security. That’s why we’ve upgraded ssotax.yeshid.com to make it easier than ever to understand—and automate—how your team connects to any app.
The Problem with Traditional IAM Approaches
Most IAM platforms force you to choose between:
- Expensive enterprise SCIM integrations
- Complex, brittle custom development work
This leads to:
- Fragmented user management across systems
- Skyrocketing IT and development costs
- Hidden security risks due to inconsistent access controls
Enter SSOTax: AI-Powered Integration Intelligence
Our new AI-powered SSOTax experience removes these blockers completely.
Just enter the URL of a SaaS application, and our AI gets to work behind the scenes:
- Scans vendor documentation and available APIs
- Detects what level of integration is available based on your subscription tier
- Generates step-by-step instructions for managing user access—without needing custom engineering
Why It Matters
With SSOTax, you get:
- Faster, smarter integrations with any application
- Significant IT and engineering cost savings
- Simpler access management and stronger security
- Time back to focus on high-impact business priorities
This is a major leap forward in our mission to make identity and access simple, flexible, and powerful—for every company, not just the Fortune 500.
Try it for yourself today: ssotax.yeshid.com
Access management doesn’t have to be painful. With YeshID, it isn’t.
June 2025 Highlights at YeshID: Faster Audits, Easier Onboarding, Seamless Integrations
.png)
This month, we're helping you reclaim valuable time and gain clearer insights into who has access—keeping your business secure and efficient.
Here’s what’s new:
Audit Like a Pro
Instantly load audits, track role changes, and complete compliance reviews in one click with our wizard-style Application Access Audit.
Onboard Without Interruptions
Our new minimizable onboarding dialog lets you import users without pausing your workflow, complete with accurate seat counts and smoother login experiences.
Integrate in Seconds
Enjoy copy-and-paste configs, one-click Unsuspend Identity and Unassign License tasks, and preview HRIS data effortlessly. Less setup, more automation.
Instant Insights
Export OAuth applications and user data quickly to CSV, easily see roles per application, and benefit from smarter filtering tools and clear automation visuals.
Smoother Everyday Experience
Faster directory screens, reliable Okta imports, and refined UI tweaks mean YeshID feels faster and more intuitive every day.
We're always striving to simplify IAM for your team. Which update will have the biggest impact for you?
May 2025 Product Highlights – Easier, Smarter, and More Collaborative IAM!

In May, we doubled down on features designed to save admins valuable time, strengthen security, and integrate seamlessly into your team's daily workflow. Here are the top updates you'll love:
- Microsoft Teams Bot (v1) – Approve access, request new apps, and get support without ever leaving Teams. Modern collaboration meets streamlined IAM—ideal for Microsoft 365 users!
- Granular Roles, Everywhere – Easily create and import custom roles via CSV, capturing role assignments directly within Slack and the YeshID console. Cleaner audits, clearer accountability, happier auditors.
- SCIM for Every App – Automatically provision and de-provision users across any application—even those not in our catalog. Keep data accurate, consistent, and effortlessly reduce manual overhead.
- AI-Assisted Setup & Documentation – Our AI-powered workflows now auto-generate integration guides and intelligently map your CSV imports. Less guesswork, more productivity.
- Faster, Smarter On/Offboarding – Standardized tasks, convenient “select-all” shortcuts, and improved scheduling mean quicker transitions with fewer clicks and zero redundancy.
All these enhancements are live now—ready to help your team become more productive and secure today.
Which update will benefit your team the most? Reach out to us in our community and we are happy to help!
What I Didn’t Know About MFA—And Why You Don't Need SSO for Compliance
.png)
What I Didn’t Know About MFA
I was talking to my cofounder recently and said, “Not every company has an Israeli CTO who can argue with auditors about what a compliance requirement really means.” I was joking, but it captures a real problem: auditors often push for “SSO” as a blanket requirement, but that’s not always what’s actually needed for compliance.
Acronym Soup: Understanding MFA, SSO, and SAML
Many customers I talk to say, “We need to do SSO for compliance.” That always catches me off guard, because most companies already have something like “Login with Google” or “Login with Microsoft” in place. Isn’t that enough? It turns out the confusion comes from how these terms are used – often incorrectly. Let’s break it down:
- MFA (Multi-Factor Authentication): A requirement for many compliance standards (e.g., SOC 2, HIPAA, GDPR) that applies to business-critical applications. The key word here is business-critical – not every app needs MFA for compliance.
- SSO (Single Sign-On): An experience where users authenticate once and gain access to multiple applications without needing to re-enter credentials. This idea took off when SaaS apps exploded, and employees got tired of juggling dozens of passwords.
- SAML (Security Assertion Markup Language): An older, XML-based authentication protocol that allows identity providers (IdPs) like Okta, Ping, or Microsoft to handle login for apps. This is often required when using traditional enterprise apps.
- OIDC (OpenID Connect): A newer, JSON-based protocol built on OAuth 2.0, widely used by modern apps like Google Workspace, Microsoft, and most SaaS platforms. It’s faster, more flexible, and supports better user experiences.
The Real Compliance Requirement: MFA for Business-Critical Apps
Here’s the critical point: The compliance requirement is MFA for business-critical apps, not necessarily SSO. There are several ways to implement this:
Option 1: Use Login with Google or Microsoft (Widely Available, Easiest to Implement, Cheapest to Support)
- If the SaaS app supports “Login with Google” or “Login with Microsoft” and you have MFA turned on in those platforms, you’re covered. This approach is the easiest, most cost-effective, and often the quickest to pass an audit, since the identity provider (Google or Microsoft) handles the MFA.
Option 2: Use App-Specific MFA (Limited Availability, Easiest to Implement, Cheap to Support)
- Some apps, like HubSpot or GitHub, have built-in MFA options. This works similarly to consumer apps – you log in with a username, password, and a second factor like a code or app notification. It’s straightforward but relies on each app having solid MFA support.
Option 3: Use SAML with an IDP (Widely Available, Harder to Implement, Higher Ongoing Cost)
- If the app supports SAML ($$ Alert: probably involves you upgrading your app license tier), you can connect it to an IDP like Okta ($$), Ping ($$), or even the free IDPs provided by Google Workspace or Microsoft. This typically involves more upfront setup and ongoing maintenance, including configuring MFA within the IDP and managing complex trust relationships.
My Practical Advice for Getting MFA Right for Compliance Requirements
When I advise companies on MFA, my priority list looks like this:
- Start with Option 1. It’s simple, quick, and effective for most modern SaaS apps.
- Move to Option 2 for apps that don’t support federated login but have solid built-in MFA.
- Consider Option 3 only when you need centralized control over identity and access across a large portfolio of apps, or when an auditor specifically calls for SAML.
You don’t need to over-engineer this. Start with the easiest, most broadly supported methods, and build from there. Most employees are used to different MFA methods from their personal apps and won’t be as thrown off by inconsistency as you might fear.
In short: Don’t let auditors or compliance checklists push you into expensive, over-complicated solutions. Prioritize what’s critical, and don’t be afraid to push back when it makes sense.
Microsoft 365 Support Is Here - and other product updates!

We hear this all the time:
"We bought an identity tool… and then spent nine months trying to make it work."
Or worse:
"We still haven’t finished setting it up."
That’s not how this should work.
At YeshID, our goal has always been simple: help you get value from your identity program in minutes, not months. Whether you're managing users, onboarding and offboarding, or running compliance audits — you should be able to plug in, get visibility, and start automating. Fast.
And as of this week, that experience is now available for Microsoft 365 environments too — not just Google Workspace.
Under 30 minutes from setup to insight
Our install experience is designed to give you real value — fast. Most teams are fully set up and getting useful insight within 30 minutes. You connect your apps, we show you who has access to what, and you can start automating from there.
It doesn’t matter if the apps use SCIM, have public APIs, or need a little manual TLC — we help you manage all of them. So nothing gets left out.
And because we don’t force you to set up SSO for everything, you can avoid the SSO tax until you’re really ready for it.
AI that maps your messy reality into something that works
The truth is, no one has a clean setup. Apps are owned by different teams, processes are half-documented (if at all), and access requests live in Slack threads, Teams chats, or spreadsheets.
YeshID’s AI agent helps make sense of that. It learns from what you’re already doing and maps your existing workflows into clean, repeatable processes. So you don’t have to start from scratch.
Automate what you can. Coordinate what you can’t.
Not everything can be automated — and that’s okay. Sometimes you still need to ask the design team if a contractor should get access to Figma. Or ping HR before removing a departing user from your ATS.
YeshID makes those human moments easier too. Our Slack- or Teams-native workflows let you loop in the right people quickly — so you get approvals and visibility without chaos.
And when automation is possible?
1-click onboarding and offboarding, app provisioning through APIs, and access controls that stay in sync — all ready to go.
Security and compliance without the friction
Apps get added without permission. Access gets shared. Rules get bent. It happens.
But with YeshID, you get guardrails:
- See all your SaaS apps in one place
- Monitor who has access and why
- Get alerts for risky behavior and shadow IT
- Run your quarterly access reviews directly through the platform
All of this now works seamlessly across Google Workspace and Microsoft 365 environments.
So whether your team is all-in on Google, deep in the Microsoft ecosystem, or somewhere in between — we’ve got you covered.
No more waiting for value.
Identity shouldn’t be a six-month project. With YeshID, it’s something you can roll out today — and actually enjoy using tomorrow.
Let’s make identity management work the way your org already works. Slack, Teams, APIs, fast answers, clean reviews. No duct tape. No delays.
Ready to see it? Sign up here.
Why YeshID is Better Than OKTA Workflows

If you’re an organization already using Okta, chances are you’ve made some smart moves. You’ve likely upgraded parts of your stack to SAML, added SCIM support where possible, and chosen Okta to lock down access to business-critical systems. That’s a great foundation.
But here’s the catch: Okta is only part of the puzzle.
Let’s talk about where YeshID fits in—and why it’s the smarter place to invest next.
Okta Isn’t Built for Everything
Most Okta customers we talk to manage 200–400 apps. Some are in Okta, and a surprising large number aren’t. Why?
- SSO.tax - Need I say more?
- Many Newer SaaS apps don’t support SAML or SCIM (AI apps anyone?)
- Others have weak or no Okta integrations.
- And when you need customization, Okta Workflows is the answer—but it’s slow, rigid, and expensive to build and maintain.
So teams are stuck stitching together brittle systems, writing Python code, juggling Jira tickets, and chasing access approvals manually.
That’s where YeshID comes in.
YeshID: Built to Work With Okta (and Eventually Replace It)
YeshID was built to plug into your identity stack today—and help you move beyond it tomorrow. We're not just “simplifying” Okta workflows. We're reimagining them entirely using an AI-native approach that gets you to value faster.
Here’s how:
🧠 Meet Your AI Agent for Identity
At the core of YeshID is an AI Agent that helps with two things:
- AI-Powered Workflow Builder
Just describe what you want—“Onboard a new engineer,” “Deprovision a departing employee,” “Add a contractor for 30 days”—and YeshID builds the workflow for you.
It understands context, systems, and policy, and handles the orchestration automatically. - AI-Powered Integrations
Most identity tools require manual config or SCIM to integrate with apps.
YeshID’s agent can connect to any app with an API. You don’t need to wait for official connectors—just tell the agent what you want to automate, and it will figure it out.
That means you can finally automate identity tasks across the entire SaaS surface area, not just the slice Okta supports.
Why Invest in YeshID Instead of Doubling Down on Workflows?
You could spend the next few months building and debugging flows in Okta Workflows…
Or, you could:
- 💬 Describe the workflow in plain English and let our AI build it
- ⚡️ Automate across tools that don’t support SCIM or SAML
- 🔐 Get real-time visibility into who has access to what, and why
- 📋 Layer access approvals, scheduling, and audits—automatically
It’s faster. Smarter. And way easier to maintain.
TL;DR: Keep Okta (For Now). Add YeshID.
Okta is a solid authentication layer. But YeshID is your AI-native identity platform—built to automate every part of access, from onboarding to deprovisioning to compliance reviews.
We integrate with Okta seamlessly. But over time, we’ll replace the brittle parts:
The workflows. The manual reviews. The access gaps.
So before you spend more money and time building out rigid automations in Okta, invest in something that works with your stack now, and grows beyond it later.
Ready to see what AI-native identity actually feels like?
We’ll have you automating workflows across your entire stack—by the end of the day.
Doing More with Less (and 364 SaaS Apps)

Doing More with Less (and 364 SaaS Apps)
“Do more with less” is now the default setting for modern IT teams.
The average org is juggling 200 to 400 SaaS apps right now. One recent stat puts that at 364 for for enterprises. Now guess how many people are managing all that?
Usually: one. Maybe two.
Meanwhile, teams keep spinning up new tools without flagging IT. According to Productiv, 56% of apps are owned outside of IT. Which means you’re securing apps you didn’t vet, approve, or even know about.
Shadow IT is now just… IT.
It’s chaos.
Automation sounds great in theory…
But when a workflow takes four hours to build and saves you ten minutes a month, it’s not getting prioritized. You’ve got bigger fires to put out.
That’s where the trap is: a lot of “efficiency” solutions are pitched as quick wins but take months to roll out. Some require professional services just to get going. Others pitch “instant value” and still need quarters of runway before they’re remotely useful.
Case in point: Mention Okta in a kickoff meeting and watch the timeline stretch into next fiscal year while you scramble to hire consultants and upgrade your apps to SAML.
YeshID is what happens when IT builds for IT
We built YeshID because we were tired of waiting six months to fix problems we already understood. No more consulting hours. No more praying for SAML. No more “value unlocked in Q3” conversations.
With YeshID, you can be up and running in under an hour. No professional services required. Out of the box, you get:
- A real-time map of who has access to what
- The ability to kill off risky OAuth tokens
- Shadow IT discovery
And then? Our built-in AI Agents kick in to help you go even further:
- Got a messy onboarding checklist in Notion, Google Docs, or Slack? We’ll convert it into an automated, orchestrated workflow with a click.
- Need to integrate with the tools your team is already using? Our agent reads the API docs, generates the integration code, and builds it for you.
It’s like having another engineer or IT ops person on the team—except it doesn’t need PTO.
So, yes… Automate. Secure. Streamline. But do it without the headaches and multi-quarter roadmaps.
👉 Sign up free and automate your first workflow in under an hour.
Release Notes: Smarter Workflows, Faster Performance, and Enhanced Security

A Better, Smoother Experience for Your Team
This latest release brings a mix of powerful new features, key performance improvements, and important fixes to make your workflows more efficient and reliable. Whether you're managing policies, onboarding users, or handling integrations, you'll find smoother automation, better security, and a more intuitive experience. Let’s dive into the details.
🚀 New Features to Supercharge Your Productivity
- AI-Driven Tasklist Views & Smarter Automation – A new chat-style tasklist view makes managing tasks more intuitive, while schema-based prompts improve automated suggestions, helping your team complete tasks more efficiently.
- Enhanced Custom Fields & Directory Selection – User onboarding and tasklists now support more flexible custom fields, and if only one directory exists, it’s selected automatically—saving you time.
- Expanded Slack & Access Control Capabilities – Slackbot users can now request additional roles or access for teammates, keeping permissions in sync with evolving team needs.
- Smarter Policy Management – AI-powered policy generation and violation detection ensure proactive compliance, reducing the risk of policy misconfigurations.
🔧 Fixes & Polishing for a Smoother Experience
- More Reliable Data Handling & Configurations – Issues with missing table references, incorrect parameter storage, and improper decryption checks have been resolved, preventing frustrating UI errors and data inconsistencies.
- Task Management Improvements – Tasklists now allow real-time edits, reassignment, and better drag-and-drop functionality, ensuring a seamless experience when organizing workflows.
- Security & Authentication Enhancements – OAuth and authentication flows have been refined, making login processes more stable while ensuring safer handling of credentials.
- Better Error Handling & Visibility – Error messages and notifications are now clearer across various features, from policy forms to directory integrations, so users can troubleshoot issues more easily.
🔍 Miscellaneous Improvements & Performance Boosts
- Optimized Caching for Faster Performance – Predefined policy prompts now load more quickly, reducing unnecessary external calls and improving overall system responsiveness.
- Cleaner UI & Improved Navigation – A refreshed task layout with side panels, better onboarding/offboarding flows, and refined UI labels make for a more intuitive experience.
- Stronger Integrations Across Platforms – This release introduces enhanced support for Okta, Google Workspace, Atlassian, and BambooHR, ensuring seamless connectivity and fewer sync issues.
- Security & Stability Upgrades – Core dependencies, including Go’s network and crypto libraries, have been updated for improved security, while authentication workflows have been fine-tuned to prevent login and provisioning issues.
Get Started with the Latest Updates
These changes make it easier than ever to automate tasks, manage policies, and keep your organization running smoothly. If you have any questions or feedback, let us know—we’re always working to make your experience better!
Introducing the "SSO Automation Scorecard"

TL;DR - we built a tool that reveals who charges extra for SSO and see exactly what you can automate in 200+ popular applications. Check it out here.
Why Are We Still Doing Manual IT Tasks in 2025?
In a world obsessed with automation, it’s shocking how many IT tasks remain stuck in the Dark Ages. Onboarding, offboarding, access management—these are repetitive, predictable chores that should practically automate themselves. Yet here we are, wrestling with spreadsheets and manual checklists, all thanks to overly complex integration “standards” and a dash of vendor trickery.
“How Much Can I Automate?”
Plenty of identity vendors love to brag about one-click integration and effortless automation. Then you pop the hood and discover layers of complexity that can only be navigated by costly consultants or armies of in-house developers. If you’re an IT pro who wants to replace manual drudgery with real automation, you deserve technology that meets you halfway—but that’s not what most vendors deliver.
The SaaS Integration Nightmare
A huge part of the problem is how SaaS apps approach integrations. Instead of giving us simple, direct APIs for day-to-day needs like provisioning and de-provisioning, they insist on using SAML or SCIM for everything. Sure, those standards have their place, but for basic tasks, they’re often overkill—expensive to implement, hard to maintain, and a giant headache for everyone involved.
A Plea to SaaS Developers: Think of the Implementors
The solution is simple: create a straightforward API.
We don’t need a sprawling, standards-heavy blueprint just to add or remove a user. Give us a straightforward API for these three core functions:
- List Users: So we can see at a glance who’s got access.
- Add User Programmatically: Let us automate provisioning—no more spreadsheets.
- Remove User Programmatically: Because nobody wants to keep paying for unused licenses.
That’s it. With these basic functionalities, we can significantly improve the lives of IT professionals and enable them to automate critical tasks.
The “IT Automation Scorecard”
To help IT teams make informed decisions, we created the SSO Automation Scorecard. It’ll show you who charges extra for SSO and what you can automate in 200+ popular applications. For example:
- SAML Support: Yes/No
- SCIM Support: Yes/No
- List Users: Yes/No
- Add User: Yes/No
- Remove User: Yes/No
- Cost of Automation: Is it free, included, or behind a paywall?
This scorecard would give IT teams the cold, hard truth about a product’s automation capabilities before they sign any contracts.

Conclusion
It’s 2025, and it is unacceptable that basic IT tasks remain manual and time-consuming. At YeshID, we’ll connect with any existing API endpoint your SaaS provider offers—just give us a list-users URL, and we’re off to the races. If your SaaS app can write or delete users via an endpoint, we integrate with that, too.
But we can’t do it alone. We need SaaS providers to step up and provide those basic APIs. They don’t have to follow a massive standard—they just need to exist, and they need to be free. So come on, developers: let’s finally ditch the spreadsheet-driven workflow and make real automation happen.
How to Prevent Uncontrolled Google Drive Sharing and Protect Your Sensitive Data

Google Drive is a powerful, cloud-based collaboration platform that enables seamless teamwork. However, without proper oversight, it can quickly become a security risk. Uncontrolled file sharing, undocumented external access, and lingering permissions for former employees all threaten your sensitive data and brand reputation.
This comprehensive guide will show you how to identify security gaps, establish secure sharing policies, and leverage the free YeshID Labs Drive Files Report tool to regain full control over your Google Drive environment.
Why Does Google Drive File Sharing Spiral Out of Control?
Unconfigured Default Settings:
Out-of-the-box settings can be overly permissive. If you don’t adjust them, files might be visible to entire departments—or even indexed by search engines—after just a couple of careless clicks.
Inadequate Employee Training:
Team members who don’t fully understand Google Drive’s sharing options may inadvertently share links externally. This lack of awareness often leads to unauthorized access and potential data leaks.
Departures and Role Changes:
When employees leave your organization or shift roles, their file access may remain unchanged. This oversight leaves a back door open for future data breaches.
Personal Account Sharing:
In a rush, employees might share files with personal Gmail accounts. This risky behavior takes sensitive files outside your corporate security perimeter, making it harder to track who has access.
Common Risks to Your Sensitive Data
- Publicly Accessible Files: Sensitive documents may be left open to anyone on the internet.
- Over-Sharing with External Parties: Partners, vendors, or contractors may retain access long after projects end.
- Data Governance Failures: Without a systematic approach to managing permissions, your data governance and compliance efforts could falter.
How the YeshID Labs Drive Files Report Tool Restores Visibility
To regain control over your Google Drive sharing, visibility is key. That’s where the YeshID Labs Drive Files Report tool comes in. This free solution provides a clear picture of your file-sharing landscape, helping you identify security gaps before they lead to data breaches.
Key Benefits:
- Instant Clarity: See exactly which files are publicly accessible or shared with outside domains.
- Prioritize Remediation: Focus on the most shared or most sensitive files first.
- Improve Governance: Reinforce your organization’s compliance and data governance policies by ensuring only the right people have access.
Step-by-Step: Using the Drive Files Report Tool
- Visit YeshID Labs:
Go to the YeshID Labs Drive Files Report website and open the tool. - Authorize Access:
Grant secure, read-only permissions to your Google Drive data. Your privacy is safeguarded—everything runs entirely in your browser. The backend only serves static HTML and JavaScript, stores nothing (not even in-memory), and YeshID has zero access to your Drive files or filenames. We use PostHog solely to capture sign-in emails for analytical purposes, and that’s it. (No, really—check the source code!) - Generate Your Report:
In a few moments, receive a detailed, easy-to-understand report outlining your file-sharing environment. - Analyze the Results:
Identify publicly shared files, highlight external sharing risks, and pinpoint “most shared” documents that may require tighter controls.
(Pro Tip: For best results, schedule routine scans to keep tabs on changes in file-sharing behavior.)
Using the Tool After Employee Departures
When an employee leaves your organization, it’s critical to ensure that their Google Drive files remain under proper control. As a Google Workspace administrator, you can:
- Reset the Former Employee’s Password:
Access the departed employee’s account by resetting login through the Google Workspace Admin console. - Sign in with the Reset Account Credentials:
Once signed in as the former employee, run the YeshID Labs Drive Files Report tool. This lets you quickly identify any files that may have been left publicly accessible or shared inappropriately. - Take Immediate Action:
Review and adjust sharing settings, revoke access for external parties, and relocate sensitive files as needed to maintain a secure, compliant environment.
Best Practices to Secure Your Google Drive Sharing
- Configure Default Sharing Settings:
Reduce the risk of accidental oversharing by setting restrictive default options (e.g., “Only me”). - Implement Clear Sharing Policies:
Document and enforce guidelines explaining who can share files, what can be shared externally, and approved methods for secure collaboration. - Regularly Audit and Revoke Access:
Conduct periodic access reviews, especially following employee departures or role changes. Remove outdated permissions to maintain a lean, secure access list. - Provide Targeted Employee Training:
Educate your team on secure file-sharing practices. When employees understand the potential consequences, they’re more likely to follow protocols. - Use Advanced Security Features:
Leverage Google Workspace’s built-in protections such as link expiration, password-protected links, domain restrictions, and classification-based sharing.
Start Taking Action Today
Google Drive security isn’t just an IT concern—it’s a fundamental business priority. By using the free YeshID Labs Drive Files Report tool, you can swiftly identify risky sharing practices and take immediate corrective measures. Combine these insights with solid policies, regular audits, and informed employees to create a resilient, secure, and compliant Google Drive environment.
Ready to regain control? Get started with the YeshID Labs Drive Files Report tool now.
YeshID Monthly Release Notes: December 2024

Release Notes: December 2024
We’ve been working hard to make your YeshID experience smoother, more intuitive, and more powerful. In this release, you’ll find enhanced directory identity management, improved provisioning and notification features, and plenty of behind-the-scenes optimizations. These updates aim to help you manage your applications and user access more efficiently, giving you better control without adding complexity.
New Features
- Streamlined Directory Management: Enhanced identity deletion and easy reconnection of Okta directories, plus a new “in order” task flow for quicker setup.
- Better Incident Response: An integration with PagerDuty lets you respond to critical issues faster and more effectively.
- Labs (Coming Soon): A new Google Workspace Drive Report is in the works to give you deeper insights into drive usage and file activity.
Fixes & Polishing
- Smoother Sync & Provisioning: Improved error handling, more accurate provisioning configurations, and updated task flows ensure reliable day-to-day operations.
- UX Enhancements: Minor interface updates for clarity, cohesive navigation, refined admin notifications, and more precise filtering.
- Cleaned-Up Code: Removal of outdated features and unused code results in a leaner, faster platform.
Miscellaneous
- Pricing Adjustments: Simplified our Pro plan pricing to better align with evolving subscription options.
- Under-the-Hood Improvements: Updates to lock management sessions, small Safari UI tweaks, and other behind-the-scenes optimizations for enhanced stability.
- Greater Flexibility: Optional parameters for organization updates, custom welcome emails, and branded login pages round out the experience.
Why We Built the Demo Center: Transparency Over Tradition

Why We Built It
The traditional software sales process can be... frustrating. You start with a website of buzzwords and vague promises, only to land on a call with someone who’s more concerned about pushing you down a funnel than genuinely solving your problems. It’s time-consuming, and more importantly, it’s not how today’s buyers want to engage.
Transparency matters to us and we believe you deserve better. You shouldn’t have to jump through hoops or schedule a call just to see if a product meets your needs. That's why we built the Demo Center. Our Demo Center isn’t just another “demo page.” It’s a place where we skip the gimmicks, cut through the noise, and let our product speak for itself. No forms, no gatekeeping—just honest content designed to help you understand how YeshID can simplify Identity and Access Management (IAM) for your small business or startup.
By making it easy for you to explore our features at your convenience, we hope to respect your time and enable smarter and more nuanced conversations down the line.
What You’ll Find in the Demo Center
Guided Walkthroughs: Step-by-step videos showing how YeshID tackles everyday IAM challenges.
- Access Grid: Explore our intuitive approach to managing and modifying user roles.
- Onboarding & Offboarding: See how we handle employee transitions seamlessly.
- Access Requests & Approvals: Discover how streamlined workflows make granting or revoking access painless.
- Security & Compliance: Learn about the built-in features that keep your audit requirements in check.
Meet Your Guide: Thilina (“T”)
We wanted to make sure you had a clear and engaging experience, so we enlisted the help of the most cost-effective 'celebrity' we know - our founding customer success engineer, T. He’s not just knowledgeable—he’s engaging, approachable, and committed to helping you find real solutions, not just quick fixes. You might recognize him from some of our more lively videos, like Friday Offboarding Hell or the Bokta Sales Guy.
What’s Next?
The Demo Center is just the beginning. We’ll continue updating it with new videos and resources, ensuring you have the clarity you need as your IAM needs evolve.
Ready to Explore?
Check out our Demo Center and discover how we’re reshaping IAM for small teams. No fluff, no gimmicks—just the answers you deserve. Experience a company that puts you first.
FREE Shadow IT Assessment tool
.png)
All I want for Christmas is visibility into Oauth Apps
Last week while the US was gobbling down turkey our Canadian team decided to build a FREE tool for you to see how your organization is sharing permissions with all those 3rd party sites.
We all know that employees are quick to click through Google’s OAuth consent screen so they can get back to the task they are trying to accomplish, but sometimes the scopes they allow are overly permissive. It’s also really difficult to get a quick overview of the situation with the google admin console. So we decided to build something that makes it all quick and easy.
What is OAuth Shadow IT?
OAuth Shadow IT refers to unauthorized third-party applications that employees have granted access to your organization's sensitive data. These applications can range from productivity tools to niche services, and they often operate under the radar, posing significant security risks.
Why is OAuth Shadow IT a concern?
- Expanded Attack Surface: OAuth-enabled applications can significantly expand your organization's attack surface, making it easier for malicious actors to exploit vulnerabilities and gain unauthorized access to valuable information.
- Cloud-to-Cloud Communication: These applications often communicate directly with cloud providers, bypassing traditional network security controls. This makes them difficult to detect and monitor, creating blind spots for security teams.
- Data Leakage Risk: Unauthorized applications can potentially leak sensitive data outside the organization, either intentionally or unintentionally.
- Vendor Risk: Relying on third-party applications introduces additional vendor risk.
- Compliance Violations: Using unsanctioned applications can lead to violations of data privacy regulations.
Taking Control of Your OAuth Landscape
To combat OAuth Shadow IT, you need visibility into the applications that have been granted access to your organization's data. That's where YeshID comes in.
YeshID's Free OAuth Shadow IT Tool
This is how you can scan your Google Workspace: First, to use this tool you will need to grant us two scopes: the ability to read users and the ability to read the applications that users have granted access to. As a note, we do not store any of this data, everything is done in the browser locally without sending requests through our servers. I’ll also tell you how to remove access at the end.
- Visit our Shadow IT Assessment Tool
- Click Begin Scan
- Authorize YeshID access to list users and their scopes

That’s it! The scan will start immediately. As scan results come in you will see a report similar to this:

From here You can see the applications, number of users who have granted some amount of access to the app, scopes that are common, sensitive scopes and restricted scopes. Clicking on the app will drill down to see which scopes that have been granted and by who. In this example, I can see that Slack has some pretty broad access to some of our employees' files, in particular Slack could delete all of their files. Now in this case I’m not worried because It’s Slack, but if the app is not one I recognize I might dig a bit deeper and maybe recommend to the employee to rethink the access they have granted.

If you want to remove the access you’ve given YeshID, Go to https://myaccount.google.com/, click security on the left side, scroll down and on the right side of the screen you will see a section called third-party apps & services, click see all connections. Then search the list for YeshID and click on it. At the bottom of the screen click “Delete all connections you have with YeshID”. That’s it!
We hope this tool has been helpful. If so you might want to take YeshID for spin with our free trial. We have a much more powerful version of this report that will update daily so you can keep track of all those apps and be alerted when Steve in accounting grants a bit too much access. We’re always looking for feedback and we would love to hear your thoughts in our Slack channel
Free Google Workspace Risk Assessment Tool

At YeshID we are big believers in open source and giving back to the community. That’s why we were thrilled to learn about the beta release of the Google Policy API. Why? Because until now, there's been no automated way to pull settings data from Google Workspace. This meant MSPs and virtual CISOs were manually configuring security settings for their clients – a time-consuming and error-prone process.
We knew there had to be a better way. So, inspired by the amazing support we've received from the IT/Security community, our head of engineering came up with a fantastic idea: a free Risk Assessment tool for Google Workspace!
This tool leverages the Google Policy API to pull your settings data and compare it to YeshID's recommendations for Google Workspace. We were inspired by some of the great work of Google, our MSP friends and also CIS Benchmarks.
Here's what our free Risk Assessment tool does:
- Automates configuration review: No more manual work! Our tool pulls your Google Workspace settings data and compares it to the CIS Benchmarks.
- Provides security insights: The tool highlights areas where your configuration aligns with best practices, and areas where there's room for improvement.
- Offers clear guidance: We don't just tell you there's an issue, we provide guidance on how to address it and improve your security posture.
By following these recommendations, you can significantly improve your overall security posture and protect your sensitive data within Google Workspace.
Ready to take your Google Workspace security to the next level? Check out our free Risk Assessment tool.
P.S. You can also access the full set of CIS Benchmarks for Google Workspace directly on the CIS Security website.
We hope this tool empowers you to secure your Google Workspace environment and shows our appreciation for the fantastic IT/Security community!
YeshID Monthly Release Notes: November 2024
.webp)
Monthly Release Notes: New Features, Enhancements, and Fixes
Say hello to a new era of integrations! This month’s updates bring advanced app integration tools, the ability to connect and manage multiple Google Workspaces, and Okta directory support for enterprise-level user management. These groundbreaking features make syncing users and automating tasks smoother than ever. We’ve also addressed key bugs, improved workflows, and improve a the billing system to give you more control over subscriptions. Let’s explore the full release!
🌟 New Features
Custom Integrations and Integrations Catalog
You can now integrate applications outside our existing catalog! Highlights include:
- Configuring REST API endpoints.
- Authentication handling (e.g., basic auth).
- JSON mapping with jq, pagination, and error handling.
- A dedicated UI for managing custom integrations.
The addition of a catalog of pre-defined integrations simplifies setup by offering templated configurations with user-supplied parameters.

Okta Directory Integration
Added support for Okta as a directory, including:
- Syncing users and groups.
- Creating and deleting identities.
- Seamless integration with applications.
- A user-friendly UI for Okta directory management.
Directory and Identity Management

Create Directory Identity Task
This new task type replaces "Create Google Workspace User," allowing admins to:
- Select directories and domains.
- Make identities primary.
- Update YeshID user records automatically.
Set Directory Identity Org Unit/Group Tasks
Streamline onboarding with tasks that assign organizational units and groups to directory identities.
Directory Sync Settings Page
Admins can now control directory sync settings, enabling or disabling automatic YeshID person creation and deletion based on organizational unit membership.
Policy Analyzer
We’ve introduced the Policy Analyzer, a tool for assessing Google Workspace policies. With features like mobile compatibility, error checking, and tier options, it has been rebranded as "Risk Assessment" for a clearer purpose.
🔧 Enhancements
Application and Task Improvements
Application Audit View
We’ve improved Application Audit functionality by:
- Splitting application and audit views for better navigation.
- Adding a dedicated audit route.
- Showing “Continue Audit” options where applicable.
- Updating instructions for clarity.
Tasks UI Update
Revamped the Tasks UI with a streamlined table layout, clickable rows, and visible assignee tags for better task management.
Improved Identity and Tasklist Management
Directory Identity Editing
Admins can now update directory identity attributes, such as:
- Names, organizational units, groups, and aliases.
Tasklist Parameter Editing
Improved tasklist workflows with:
- Always-editable components.
- Rearranged and quick-access task slots.
CSV Import Enhancements
Enhanced CSV Import features:
- Full name matching for better accuracy.
- User visibility during CSV uploads.
- Admins can now use CSVs to bulk-import users during audits.
Directory Migration
Simplified directory migrations with:
- Integration migration support.
- Streamlined onboarding and identity updates.
- Fixes for onboarding hints.
Overview Stats Updates
Updated stats to provide more relevant insights:
- Added YeshID-specific metrics.
- Moved stats from the home page to the directory view for Google directories.
- Weekly emails now align with updated stats.
Billing System Enhancements
We’ve upgraded the Billing System with features like:
- Improved customer and subscription management.
- Support for payment methods, free/trial/pro plan flows.
- A redesigned billing page with:
- Invoice visibility.
- Plan details.
- Billing information.
Planned updates will include account deletion handling, seat count adjustments, and coupon support. These enhancements ensure a smoother and more transparent billing experience for users.
🐞 Fixes & Polishing
Billing Fixes
- BaseDialog Improvements: Addressed a bug affecting dialog behavior during payment flows, ensuring smoother user interactions.
- Enhanced error handling on the checkout screen.
- Improved compatibility with Stripe test clocks for consistent testing.
Tasklist Fixes
- Resolved visibility issues with tasklists during audits.
- Ensured proper tasklist clearing upon deletion.
- Reset provisioning status when tasklists are deleted to avoid "stuck" states.
Google Integration Fixes
Enhanced reliability in Google integrations by:
- Fixing issues with refresh tokens.
- Adding directory task support for actions like group management and alias settings.
- Addressing bugs with deleted or primary directory users.
Miscellaneous Fixes
- UI Enhancements: Improved button placements, link accuracy, and accessibility across the platform.
- Security Updates: Strengthened CSRF protection for sensitive actions.
- Addressed redirect loops and inconsistencies with error messages.
We hope these updates improve your experience! Stay tuned for more exciting developments next month. As always, we value your feedback—let us know how we can make your journey even better. 🚀
Explore these features and enhancements in your workspace today!
Tired of Manual User List Headaches? Try AppSync

We've heard your frustration: manually extracting user lists from various applications is time-consuming and often costly. Whether it's SCIM fees, non-standard APIs, or tedious manual processes, it's a common pain point.
Introducing AI-Powered Integrations
YeshID's new AppSync feature (now in Beta) is here to streamline the process. By leveraging AppSync AI, you can easily integrate your SaaS applications with YeshID, even if they don't have a standardized SCIM integration.
Key Benefits:
- Cost-Effective: No need for fancy, expensive SCIM integrations.
- Flexible: Works with a wide range of APIs, including non-standardized ones.
- Efficient: Quickly build integrations without extensive coding knowledge.
- Secure and Compliant: Improve security and compliance by automating user management.
How It Works:
- Identify the API: Locate the read-only user list endpoint in your application's API documentation. We can integrate with anything from basic APIs with headers to GraphQL based endpoints!
- Secure Authentication: We support a variety of auth mechanisms required by your applications, including OAuth2. Being security nerds ourselves, we make sure your application’s credentials are stored securely.
- Leverage AI: Use our AppSync AI to generate the integration. We will use the results from the API to determine how to map the results to our user properties. Does the API require pagination? Don’t worry, we’ll figure that out too!
- Customize and Test: We give you the tools to be able to edit the configuration if it happens to be wrong. Fine-tune, test, and verify that the integration has no errors and the results are correct.
- Deploy: Once the test results look correct, clicking save deploys it to your YeshID instance. It’s that easy.

Beyond User Lists
We're excited about the potential of AI-powered integrations. In the future, we aim to support more complex operations like user creation and deletion, making it easier to manage user access across your applications.
Give it a Try!
For those who prefer a hands-off approach, don't worry! We've curated a Global Catalog of pre-built AI Integrations, created and reviewed by our community. These integrations are available to you at no cost.
If you're eager to dive deeper into AI-powered automation, our AppSync feature is currently in beta. Reach out to us to gain early access and start automating your user management tasks today.
YeshID SOC2 Type 2, Round 2

Well, I’m happy that’s over with. Until next time!
YeshID just completed our second SOC2 audit, covering a full year this round! Thankfully, our security-minded team runs a tight ship. Least privilege access? Check. Secure authentication? Check. Encrypted laptops? Check. Tackling supply chain attacks, anomaly detection, vulnerability scans, red teams, pen tests, disaster recovery, and CICD policies that prevent unchecked pushes? Check, check, check, checkmate! Phew. And that’s only scratching the surface…
With the bragging and peacocking about how amazing our team is covered, let me spend some more time bragging and peacocking; I mean—raising awareness!
First, if you think all SOC2 audits are the same, well…

The SOC2 from “How I’ll look in 40 years” is not the same as YeshID’s.
SOC2 Audits 101: What SOC2 Actually Means
In case you’re wondering, SOC2 compliance isn’t just a trendy badge you slap on the homepage. SOC2 stands for System and Organization Controls, a framework for ensuring companies manage customer data securely. There are two main types: Type 1 is a point-in-time snapshot of your security practices, while Type 2 covers the effectiveness of those practices over a sustained period (a year, in our case).
SOC2 is about defining your policies and proving to auditors that you’re following them, all to reassure customers their data is safe with you. For YeshID, this wasn’t just a one-time effort—we’ve baked security into everything we do. But even if you’re doing things right, SOC2 means documenting all of it for an external auditor, with detailed, actionable steps for every process. Now, back to our story…
SOC2, Type 2, Round 1
The first time doing SOC2 can be overwhelming. Even if you’re very mindful of security, and even if, at the core, your practices meet or exceed requirements (we’ll talk more about that later), the fact that it needs to be auditable by an external party means making significant adjustments to how we did things.
For a seed-stage startup, or a Series A or B, process changes are painful and distracting. You want as few policies as possible. When I’m screening early-stage ventures exploring the unknown, nothing screams, “these founders are super creative and open-minded” like having more procedures than that government branch…
But not everything is “exploring the unknown.” Ensuring everyone uses MFA is like wearing a seatbelt—you’re still exploring, but safer.
SOC2 is a bit like a car reminding you to put on a seatbelt—only backward. Normally, if you forget to buckle up, the car beeps until you do, then stops. With SOC2, it’s like the car keeps beeping even after you’ve buckled, and only stops once you open a ticket in your ticketing system saying “buckled up,” then check that ticket each time you get in the car. The kicker? You were already buckled up in both cases—the habit just has to shift to make it easier for an auditor to see.
Am I slightly exaggerating? Sure. There’s a lot of automation around it. Enforcing MFA for each product and user will definitely make it easier, for example. Most aspects are indeed like that, but not all! You still need a ticket for each and every access request, for onboarding and especially for offboarding. You still need a ticket for that access review and incident event. You also need to document your learnings about disaster recovery and the red team you did, and it all should be in one place that’s easy to audit. Each of these is a habit adjustment, and that’s friction.
SOC2 for YeshID was a period of habit adjustments. We were already doing things securely—thanks to the habits of an experienced team—but the infrastructure, logging, and documentation needed to be created.
Start [W]here…?
If this is your first time doing SOC2, here’s the good news! Just go to the official SOC2 website and follow their step-by-step guide: choose which chapter to audit, write each policy (they even provide examples!), implement each policy so it’s audit-ready, and, of course, find yourself an auditor...

SOC2 official website, is…
Yuck.
There’s a lot of paperwork and bureaucracy to navigate when doing SOC2 for the first time. I want to give a shoutout to Vanta. Vanta made it easier for us to start. By having ready-made policies, tests, and reminders, it saved us a lot of time navigating the bureaucracy. Think of it as a specialized TODO app that reminds you to check on your firewall settings, review access permissions, and ensure you’re following your onboarding and offboarding policy.
If this is your first time doing SOC2, either at all or in your current company, I recommend Vanta and similar solutions to set the scaffolding.
One of These Is Not Like the Other: What’s in Scope
The SOC2 certificate logo looks the same for everyone, just like the M.D. certificate on the wall of that dude in the corner selling… My point is—you have to look deeper.
When doing SOC2, you have a lot of freedom in choosing what policies you want to follow and how you want to implement them. Third-party external penetration testing? 🤷♂️ Optional. MFA? Up to you…
YeshID prioritizes customer data and security, so that’s where we started our focus. If you go to trust.yeshid.com and request our SOC2, you’ll see our obsession with keeping you safe and earning your trust.
I strongly recommend you do not assume that all companies with SOC2 are the same. Besides each company having a different bar, the auditor plays a huge role. And like the policies, no two auditors are the same, with some stricter than others.
If you care about your security, ask your vendors for the full report and pay attention to what’s in scope.
.gif)
SOC2 surprise.
SOC2, Type 2, Round 2: A Full Year
The first time you’re doing an audit, you’re fresh on your policies. You and your team just finished defining them and passed the spot-check audit. Congratulations. But can you keep up this healthy lifestyle (don’t call it a diet; don’t make diet analogies)?
Besides the duration, you’re also likely to be working with a new auditor. That means a different way of reading those slightly open-worded policies I wrote a year ago. “All company operating systems encrypted” — are we talking laptops or servers? (Don’t worry; both are encrypted!)
The first time around, it took a few people iterating on the policies and implementation (route all alerts into a single place). The second year was easier, and it only took one person—yours truly—to pass the audit. Before you send me the “CTO of the Year” award, talk is cheap. Thanks to the amazing mindfulness of the team over the year, my job was getting the evidence needed from the places the auditor has no access to.
Besides that, I learned that, like many things, it’s best to divide the responsibility and enforce accountability between people and through systems.
One person cannot be responsible for ensuring all code changes get reviewed by at least two different people, but branch protection in GitHub sure helps. Enforcing least-privilege access is an ongoing job, but a checklist of things a role needs access to, via YeshID templates, saves a lot of time! Ensuring the CEO is accountable for updating the board on the cybersecurity of the company puts the responsibility in the right place, etc. Divide them by focus: HR, IT, Dev—whatever works for you. Someone who will remember to run that periodic disaster recovery exercise, document every incident in a single place, and ensure all employee laptops are compliant.
Make Your Own Policies
Here’s another lesson from a full year in SOC2: you can define any policy you want! The auditor’s job is to read your policy closely and then check that you’re doing exactly what you said you would. So, if your policy is “wash dishes every day,” you’d better have a log for every single day of the year.
An example of a policy I didn’t reword in time was that YeshID does background checks and reference checks for each employee. The problem is, we worked with almost every person in YeshID in past jobs; we know each other well. For those we didn’t, we did extensive reference checks. But… no background check. That’s a ding and one that’s easy to avoid if I just changed an “and” to an “or.”
YeshID and the IAM Struggle: Where We Went Beyond
Going into Year 2 of SOC2 compliance, we aimed for something simpler—especially with Identity and Access Management (IAM) tracking and enforcement. Basic policy definitions and simple automation got us through the first year, but we needed a solution that could scale without piling on complexity. Tracking every IAM change, enforcing roles across services, and automating access rights as duties shifted needed more than just the basics.
We started iterating on the features that would help us meet these needs. YeshID evolved into our source of truth for IAM, automating evidence collection—logging every access change, reviewing every offboarding, and tracking every role adjustment. IAM evidence went from "let’s scrape together what we can" to "ready for audit."
In Summary
Phew! We made it through another SOC 2 audit, and hopefully, we passed on some wisdom that is useful. Remember, not all SOC 2 reports are created equal. Dig deeper, ask questions, and make sure your vendors prioritize security as much as we do at YeshID. For those embarking on their own SOC 2 journey, don't be afraid to leverage tools like Vanta or YeshID to streamline the process. Now, back to work!
Google Workspace: Organize Org Units, Groups, Policies, Devices, and more!

Guide to Google Workspace and SaaS Management: Organizational Units, Groups, and Access Control
Discover how to optimize your Google Workspace and SaaS applications using Organizational Units (OUs) and Groups for enhanced security, compliance, and efficiency.
Table of Contents
- Key Principles of Google Workspace Management
- Organizational Structure for Optimal Management
- Root Organizational Unit (OU) Hierarchy
- Groups Mailing List Structure for Effective Communication
- Security Groups for Access Management
- Implementation Guidelines for Google Workspace and SaaS
- User Account Naming Conventions
- User Provisioning Steps
- Account States Management in Google Workspace
- Account States Organizational Structure
- State Management Guidelines
- Account State Transitions
- Policy Management for Security and Compliance
- Policy Cascade Structure
- Example Policies for Different OUs
- Security Framework: Implementing Role-Based Access Control (RBAC)
- Access Control Matrix for SaaS Applications
- Employee Lifecycle Management in Google Workspace
- Onboarding Process
- Offboarding Process
- Conclusion
Key Principles of Google Workspace Management
- Single OU Membership: Each user or account belongs to only one Organizational Unit (OU), simplifying policy management.
- Multiple Group Memberships: Users can be part of multiple Groups, allowing flexible access across different OUs.
- Policy Inheritance: Policies automatically cascade from parent OUs to child OUs, ensuring consistent enforcement.
- Group-Based Access Control: Utilize Groups to manage cross-OU access for resources and SaaS applications efficiently.
Organizational Structure for Optimal Management
Root Organizational Unit (OU) Hierarchy
Root OU
├── System Accounts
│ ├── Service Accounts
│ └── Admin Accounts
├── Account States
│ ├── Pending
│ └── Suspended
├── Engineering Department
│ ├── FTE (Full-Time Employees)
│ ├── Contractors
│ ├── Drive Management
│ │ ├── Internal
│ │ └── External
├── Sales Department
│ ├── FTE
│ ├── Contractors
│ ├── Drive Management
│ │ ├── Internal
│ │ └── External
└── Marketing Department
├── FTE
├── Contractors
├── Drive Management
├── Internal
└── ExternalGroups Mailing List Structure for Effective Communication
├── Department Groups
│ ├── Engineering Team
│ ├── Sales Team
│ └── Marketing Team
└── Project Groups
├── Project Alpha
└── Project BetaSecurity Groups for Access Management
├── GitHub Access
│ ├── GitHub-Admin
│ ├── GitHub-Developer
│ └── GitHub-Reader
├── Slack Access
│ ├── Slack-Admin
│ ├── Slack-Workspace-Owner
│ └── Slack-Member
├── AWS Access
│ ├── AWS-Admin
│ ├── AWS-Developer
│ └── AWS-ReadOnly
├── Zoom Access
│ ├── Zoom-Admin
│ ├── Zoom-Host
│ └── Zoom-Member
├── Salesforce Access
│ ├── SFDC-Admin
│ ├── SFDC-Manager
│ └── SFDC-User
└── Jira Access
├── Jira-Admin
├── Jira-Project-Admin
└── Jira-UserImplementation Guidelines for Google Workspace and SaaS
User Account Naming Conventions
Standardized naming conventions enhance manageability and consistency across the organization.
- Regular Users:
- Format:
firstName.lastName@domain.com - Examples:
john.smith@company.com,maria.garcia@company.com
- Format:
- System Accounts:
- Service Accounts:
svc-[purpose]-[number]@domain.com- Examples:
svc-backup-01@company.com,svc-integration-01@company.com
- Examples:
- Admin Accounts:
admin-[type]-[firstName.lastName]@domain.com- Examples:
admin-super-john.smith@company.com,admin-help-maria.garcia@company.com
- Examples:
- Service Accounts:
User Provisioning Steps
- Primary OU Assignment: Assign users based on Department and Employment Type.
- Path Example:
Engineering Department → FTE - User Example:
john.smith@company.com → Engineering → FTE
- Path Example:
- Group Assignment:
- Primary Group: Assign to the relevant Department Group.
- Secondary Groups: Add to Project Groups as required.
- Security Groups: Assign based on specific access needs for SaaS applications.
Account States Management in Google Workspace
Account States Organizational Structure
Account States OU
├── Pending
│ └── For employees not yet started
└── Suspended
└── For temporary account suspensionsState Management Guidelines
- Pending Accounts:
- Create accounts in the Pending OU with limited access.
- Move to the appropriate Department OU upon the start date.
- Suspended Accounts:
- Move accounts to the Suspended OU while retaining group memberships.
- Define suspension duration based on organizational policies.
Account State Transitions
Pending → Active Department OU → Suspended → Deleted/Archived- Automated Transitions: Implement automation for onboarding (Pending to Active) and offboarding (Active to Suspended). Schedule account deletion or archiving post-suspension to reduce licensing costs.
Policy Management for Security and Compliance
Policy Cascade Structure
Root OU
└── Department OU
├── Security Baselines
├── Device Management Policies
└── Employment Type OU
├── Access Levels
└── License TypesExample Policies for Different OUs
- Root OU Policies:
- Enforce Multi-Factor Authentication (MFA) for all accounts to enhance security.
- Disable External Sharing to comply with data protection regulations.
- Pending OU Policies:
- Override MFA settings to disabled for minimal access during onboarding preparation.
- Drive Management External OU:
- Enable External Sharing for controlled collaboration with external partners.
Security Framework: Implementing Role-Based Access Control (RBAC)
Access Control Matrix for SaaS Applications

- User Addition & Approval:
- Managers can add or approve users directly in the app or through Security Group Assignment.
- Utilize managers as approvers for access requests to streamline the process.
- Automated Access with RBAC:
- Automate access provisioning based on user roles or departments.
- Implement RBAC to reduce manual provisioning and accelerate onboarding.
Employee Lifecycle Management in Google Workspace
Onboarding Process
- Create User in Pending OU:
- Add new users with restricted access to the Pending OU.
- Move to Appropriate Department OU:
- Schedule the move to the relevant Department OU on the start date.
- Assign to Groups:
- Add users to Department and Project Groups as necessary.
- Configure SaaS Access:
- Set up Single Sign-On (SSO), assign to security groups, and provision licenses.
Offboarding Process
- Account Access:
- Suspend the Google Workspace account.
- Move the account to the Suspended OU.
- Revoke access to all SaaS applications.
- Data Management:
- Transfer ownership of Google Drive files.
- Archive or transfer email data as per compliance requirements.
- Cleanup:
- Remove the user from all Groups.
- Release any assigned resources like licenses or devices.
- Finalize:
- Schedule the account for deletion or archiving to reduce billing and licensing costs.
Conclusion
Efficient management of Google Workspace and SaaS applications is critical for organizational security, compliance, and productivity. By leveraging Organizational Units, Groups, and automated policies, you can streamline employee lifecycle management and enforce robust security measures.
Keywords: Google Workspace management, SaaS applications, Organizational Units, Groups, Access Control, Employee Lifecycle Management, Security Policies, Role-Based Access Control, Onboarding, Offboarding, Policy Management
How to Meet SOC 2 Access Review Requirements - A Startup's Toolkit

Many people I speak with are struggling to understand how to meet SOC 2 access management requirements. If you have a small team of fewer than 30 users, we can simplify this process for you—at no cost. Let’s begin:
Here's a step-by-step guide to streamline your access management process and meet SOC 2 compliance:
1. Connect Your Google Workspace: Seamlessly integrate your existing user base.

2. Import Your Applications: Quickly add your applications, whether it's a manual process or importing from a spreadsheet or Notion doc. (Note: It doesn’t matter which license type you have. We can help you manage any application)

3. Install the Slack Agent: Empower your team to request access directly from Slack using the /Request Application command.


4. Track Access Requests: By using the slack bot, YeshID will quietly behind the scenes not only route the request to the right person to do the task, but also monitor and manage access requests and create an access request report. (SOC 2 Compliance)

5. Create Offboarding Checklists: Create and ensure a smooth offboarding process with customizable checklists. This will help you ensure offboardings are consistent and tasks don’t get missed. (SOC 2 Compliance)

6. Proof of an Offboarding process: Select an offboarding process and let YeshID facilitate (and sometimes automate parts of) the offboarding process. (SOC 2 Compliance)


7. Create and manage access reviews to identify and mitigate potential risks for business critical applications. This will help you facilitate the process across multiple owners and verify that access removals were completed. (SOC 2 Compliance)


8. Produce detailed reports to demonstrate compliance with SOC 2 requirements. (SOC 2 Compliance)

By following these steps and leveraging YeshID's features, you can significantly simplify your access management process and achieve SOC 2 compliance.
Get Started Today
If you're a small team of under 30 users, you can start using YeshID for free. It's a simple, effective way to manage access rights and meet SOC 2 compliance.
Don't Reinvent the Wheel
Let YeshID handle the complexity of access management, so you can focus on running your business. Sign up today and experience the difference.
YeshID Monthly Release Notes: October 2024

We're thrilled to share our latest update, bringing improvements to enhance your overall experience on our platform. This release focuses on the introduction of our new billing system, simplifying user access, and refining many aspects of the user interface.
New Features
Billing System
- We've introduced a new billing system that provides a seamless payment experience, including easy subscription management, secure payments via Stripe, and clear invoicing.
Easy Organization Creation
- Users can now create their own organizations, making it much easier to get started and ensuring smooth, straightforward access to the platform.
Enhancements
Directory Management Updates
- We've streamlined our directory management, leading to better performance and easier navigation.
- Shadow apps are now filtered to focus only on relevant directories, making views cleaner and more efficient.
- Root organization unit information is now filled in for root org units.
Fixes & Polishing
User Interface Improvements
- The task menu has been updated for better usability, fixing issues with automatic closing and element arrangement.
- The formatting of code blocks has been fixed to handle overflow better when pasting complex content.
- The main task view now consistently displays important information at the top, improving visibility.
Security and Performance
- Improvements to system user management help avoid issues with directory operations, resulting in a more stable experience.
We can't wait for you to explore these improvements! As always, your feedback is crucial as we continue to improve our services. Thank you for being part of our journey.
Introducing Access Review: Simplify your compliance journey

For small businesses, achieving and maintaining compliance is challenging. SOC 2 and other regulatory requirements demand meticulous access management, but most of us are still working in spreadsheets and Slack messages. That makes it tricky when compliance reports come due: Spreadsheets become outdated, manual reviews consume time, and quarterly audits are burdensome. We don't think you should have to choose between achieving compliance and running your business efficiently so today we’re releasing another major improvement to YeshID.
Introducing Access Review
Access Review, available now in YeshID customer dashboards, is designed to streamline your access management and compliance processes. It's the tool you've been waiting for to tackle SOC 2 and other regulatory requirements with ease.

Why you’ll love it
If you've ever prepared for a SOC 2 audit, you know the drill: late nights, endless spreadsheets, and frantic emails to application owners. Access Review is here to transform this process. Here's how:
1. Automate the cat herding: Say goodbye to manual data entry. Our customizable templates and automated distribution system handle the heavy lifting. And we'll follow up with application owners so you don't have to chase overdue reviews.
2. Centralized control: No more scattered spreadsheets. Access Review provides a comprehensive view of access rights across your organization.
3. Effortless reporting: When audit time comes, you'll have comprehensive reports ready to go. No last-minute scrambles. Just hit the download button.
Here’s how it works
Access Review simplifies your compliance process:
1. Create review templates with our guided setup
2. YeshID will distribute the access review templates to application owners
3. Access data is auto-populated for integrated apps
4. Application owners can easily import user lists and make access decisions
5. Track pending items with automatic reminders
6. Generate audit-ready reports at the click of a button
Does the world need another Access Review tool?
There’s a growing number of options out there for Access Review and most of them do a pretty good job. But YeshID is focused on solving for the specific workflows that help small businesses more easily and affordably facilitate employee lifecycle management, security, and compliance. That means our Access Review offering is custom-built for teams like yours. We’ve optimized for the things that really count for small businesses:
Simplicity: Intuitive design for ease of use, without the complexity of enterprise solutions like Vanta or Drata.
Flexibility: Compatible with any license type, unlike some competitors that require specific integrations.
Affordability: Access Review doesn’t tack on another X$/user/month fee for you. It’s simply part of YeshID. So you get Enterprise-level security at a small business price point (read: way more affordable than Vanta, Drata, or Torri).
Compliance at the click of a button
Access Review is going to save you a ton of time on the entire compliance process. That means you get to focus on the other stuff that actually helps you grow your business. And because Access Review is deeply integrated with YeshID, it also helps you tighten up security and reduce manual errors.
Access Review isn't just a feature – it's a more efficient approach to managing access and maintaining compliance. Give Access Review a try today and experience how much simpler it is to achieve and maintain compliance.
🚀 YeshID Monthly Release Notes: : September 2024

We’re excited to announce a new release packed with features, enhancements, and fixes to improve your overall experience with YeshID. Here’s a summary of the key updates:
New Features
- Audit Reports: A new audit reports page lets you track and manage audits based on tasklists, helping you monitor audit processes more effectively.
- External Users Tab: We've added a dedicated external users tab on the people page, making it easier to organize and manage internal and external users separately.
- Directory Identity View: You can now view secondary directories and associated groups more clearly, with new APIs for fetching user identities across multiple directories.
- Organizational Unit Visualization: A new organizational unit tree visualization helps you better understand and manage your directory’s structure.
- Real-time Directory Sync Progress: You can now monitor directory synchronization with real-time progress updates, keeping you informed throughout the sync process.
Enhancements
- Improved Application Audit Process: Audit tracking now includes detailed information on account updates, allowing you to track changes and gain better insights over audit periods.
- Multiple Domains Support: Directories now support multiple domains, with an option to set a default domain for better flexibility in managing complex organizational setups.
- Enhanced User Management:some text
- Suspend and unsuspend actions have been moved to more intuitive locations for easier access.
- We’ve improved the process of merging user accounts to handle name changes while preserving external ID integrity.
- Improved Application Management:some text
- Deactivated accounts are now hidden from the default view of application accounts, improving visibility and navigation.
- A new column shows whether applications are managed or unmanaged, helping clarify application states.
- Enhanced Security: We've strengthened protection against CSRF attacks and updated several dependencies to address security vulnerabilities.
Fixes & Polish
- CSV Import Improvement: We've fixed issues with CSV imports to ensure smoother and more reliable processing.
- User List Accuracy: User lists for shadow applications now correctly display users across all grants, improving accuracy.
- Application Accounts Page: Unmapped accounts are now prioritized in the default view, making important information more accessible.
- UI Improvements:some text
- The user side panel now uses a full-page view for consistency with the rest of the application.
- We've replaced the term "user" with "person" throughout the application for better clarity.
- The audit interface has been improved to make it easier to track task progress and completion.
- Task information is now presented in a table layout for better readability.
- Performance Optimization: We’ve optimized database performance, resulting in faster access to events, users, and tasklists.
- Google Workspace Integration: The import process for Google Workspace has been improved, offering better handling of aliases, group memberships, and errors.
Balancing SaaS Tools with Security through an Employee Growth Spurt

Problem: Balancing SaaS Tools with Security through an Employee Growth Spurt
Chris Hubbard, IT Manager at a growing financial services firm, faced significant challenges managing a growing number of SaaS applications across the organization. Coming from larger enterprises like Apple and Yahoo, where resources and teams were abundant, Chris was uniquely positioned to see the difficulty of managing a proliferating SaaS landscape as an IT-team-of-one. "One of the big pain points was the number of SaaS applications and subscriptions that the business relied on," Chris explained. "We were at about 40 applications, which all individually needed to be managed. Keeping track of users' permissions, costs, and securing our environments was becoming increasingly difficult."
The company itself was also growing. Ensuring secure and efficient onboarding and offboarding processes became increasingly complex and time-consuming as the company expanded from 25 to over 120 employees. “We needed a solution to manage employee access gracefully – and ideally all in one place,” Chris said. He hacked what insights he could from Google Workspace but, he explained, “there was no holistic or even snapshot view of every user's application access.” Beyond operational inefficiencies, this opened the door to security risks.
Solution: Implementing YeshID for Unified Application Management and Onboarding
Chris scoured the software landscape for solutions and finally arrived at YeshID. "When I first had a look at YeshID it seemed too good to be true. It ticked all the boxes that I had been looking for," Chris remarked. YeshID provided a holistic view of user application access while streamlining onboarding and offboarding processes, which were critical for his company’s growth trajectory. "YeshID has made onboarding and offboarding so much easier,” Chris emphasized.
YeshID's impact extended beyond just IT efficiencies; it transformed the overall experience for Chris and firm employees. "It's been such a breeze to set users up," Chris noted. "Especially when you're told on a Friday at 4:30 that someone's starting on Monday, that helps. It saves my weekends." That’s because YeshID provides the team with an onboarding checklist, handles all Google Workspace provisioning and group assignments, and can even send a scheduled welcome email on the day they start. The platform's self-service capabilities also allowed employees to request access to specific tools directly, reducing administrative overhead. Employees can even make requests using a simple Slack command. "People have made app.yeshid.com their homepage," Chris explained. "If they need access to a tool, they can just request it and within minutes get rolling."
Results: Improved Efficiency, Enhanced Security, and Enhanced Compliance
Implementing YeshID not only streamlined the firm’s IT operations but also strengthened security and compliance measures. The platform's ability to provide a snapshot view of all users and their respective access rights, including shadow IT activities, was pivotal. "YeshID has just eliminated risks by showing us what's outstanding and immediately actioning people," Chris highlighted. The platform's comprehensive reporting capabilities played a crucial role in meeting regulatory requirements, including Australia’s GS007. "We have to provide a security report quarterly to our executive team," Chris said. "In the past it took weeks to build these reports. Now it takes me 15 minutes." That’s because YeshID keeps an audit trail of access requests and usage for current and past employees.
Furthermore, YeshID enabled Chris and his team to focus on strategic initiatives. "This really allows me to focus more on strategic tasks and managing the team," Chris emphasized. "It takes the grunt work out of onboarding." The platform's automation and centralized management significantly reduced the time and effort spent on manual tasks. "It used to take close to a full day to onboard someone," Chris recalled. "Now it takes about two hours, including setting up the laptop and populating information in YeshID."
Moreover, YeshID's intuitive interface made it accessible across the organization. "Even if we didn't have a support team, I'd be confident that people in the business could run YeshID," Chris noted. "It's perfect for smaller, more nimble, cost-focused companies." The platform's ease of use and robust functionality made it an indispensable tool for the firm’s IT and HR teams alike.
Conclusion
YeshID has proven to be a game-changer for Chris’s company, offering a unified solution for managing SaaS applications, enhancing security, and streamlining onboarding and offboarding processes. As the firm continues to grow and evolve, YeshID remains a critical component of their IT infrastructure, providing confidence in managing application access and ensuring compliance with regulatory standards.
YeshID: Free for Small Businesses

Small businesses are the backbone of our economy, yet they often find themselves at a significant disadvantage when it comes to security and compliance. Complex, expensive tools have historically been the norm, leaving many smaller companies vulnerable to breaches. At YeshID, we believe that every business, regardless of size, deserves security protection.
The Small Business Security Dilemma
It’s a common misconception that security is a luxury reserved for large enterprises. The reality is that even the smallest businesses handle sensitive data that needs protection. From customer information to financial records, the potential consequences of a data breach can be devastating.
We’ve seen countless small business owners try to cobble together their own security solutions using spreadsheets and documentation. While well-intentioned, these methods are often inefficient, error-prone, and leave critical gaps.
YeshID: A Game-Changer for Small Businesses
That’s why we created YeshID. Our mission is to empower small businesses with the tools they need to protect their data and their customers – without the complexity and expense. We’re proud to announce that YeshID is completely free for companies with 30 or fewer employees.
How YeshID Makes a Difference:
- Simplified Employee Management: Say goodbye to complex administration. YeshID makes it easy for anyone to onboard and offboard employees securely.
- Centralized Access Control: Our platform provides a clear, up-to-date view of who has access to what, eliminating the need for outdated spreadsheets and documents.
- Streamlined Compliance: Generate comprehensive compliance reports in minutes, not days.
- User-Friendly Interface: YeshID is designed with simplicity in mind. No need for specialized IT expertise.
Our Commitment to Fair Pricing
For businesses with more than 30 employees, we offer competitive pricing starting at just $2 per user per month. We believe in fair pricing and want to ensure that businesses of all sizes have access to the security they deserve. For comparison, the same solution at Okta will run you a total of $17/user/month (Workflows@ $6/user/month and Identity Governance@ $11/user/month).
We’re committed to making a difference in the cybersecurity landscape for small businesses. Get organized and protect your business with YeshID. Sign up for free today and experience the difference a truly accessible security solution can make.
🚀 YeshID Monthly Release Notes: August 2024

We’re thrilled to share the latest updates that our team has rolled out this month, all aimed at boosting stability, enhancing performance, and squashing those pesky bugs. Here’s a quick rundown of what’s new and improved:
1. Integration Cleanup
We’ve strengthened our system’s security with improvements in 2FA detection, OAuth scope accuracy, and CSP (Content Security Policy) configurations. Plus, we’ve added support for more Google Workspaces and fine-tuned security headers to ensure seamless and secure integrations across the board.
2. Task Management and Workflow
Managing tasks just got a whole lot smoother! We’ve enhanced error handling, task validation, and even added the ability to manage and permanently fail old tasks. New alerts for task queue sizes and fixes for task list creation issues mean your workflows will be running like clockwork.
3. Directory and User Management
Importing users from complex setups is now easier than ever. We’ve upgraded directory and user management with support for additional directory identities, improved alias mapping, and streamlined CSV import functionality. No more headaches when dealing with multiple domains or directories!
4. Application Management
We’ve polished the application management experience with a reorganization of the navigation, fixes for display and alignment issues, and better handling of application accounts. Key updates include support for multi-directory applications and accurate display names, all designed to make managing your apps a breeze.
5. Notifications and Alerts
Your notifications are now more reliable and clearer than ever! We’ve fixed template issues and ensured that alerts, especially in offboarding processes and email tasks, are accurate and properly formatted. No more missed or confusing notifications!
6. Infrastructure and DevOps
Our backend got a thorough cleanup this month with the removal of old workflow tables and the deployment of new application tests. These optimizations keep our database environment lean and mean while ensuring robust performance across the board.
We’re committed to making your experience better with each update, and this month’s focus on stability and performance sets the stage for even more exciting enhancements in the future. Stay tuned for what’s coming next!
Manage application access without ever leaving Slack

I live in Slack. The rest of the team at YeshID does, too. So do a lot of our customers. That’s why we created the Slack integration we wrote about in this other post.
Here, I’m going to tell you how we’ve taken that integration to the next level.
The Problem
Imagine you’re in Slack, discussing some problem. Steve’s the guy who seems to have a handle on what to do. The best way for Steve to take the next step is with an app he doesn’t use all the time. He knows how to use it but doesn’t have access right now. So, let’s just get him access. Easy, right? But according to the customers we’ve been talking to, it’s not.They’ve told us what they have had to do:
- Get out of Slack and send an email (or write a JIRA ticket) to the admin for the app to request access.
- The admin may not be the approver, so the admin has to email the approver.
- When the approver approves, they reply with an email to the admin, who grants access.
- The admin then has to notify the requester.
- However, the requester might not be the person who will use the app, so they have to notify that person.
It's a mess. Or as it’s usually described, it’s a cluster- umm cluster-something.Oh, and compliance? You need an audit trail for compliance. A bunch of emails is not an audit trail. You’ve got to record the decision in an organized way–like in a spreadsheet. Ugh spreadsheets.Of course, some customers have a Slack channel for requests instead of emails. As the organization grows with multiple IT members, they often have a generic channel for access requests (or perhaps you’re just using the general IT team chat). But now you have to hope your request isn’t missed or forgotten in the buffer.And you still need an audit trail for compliance. And a way to make sure things get done
The Solution: YeshID's Access Workflow
We listened to them, and YeshID solved that problem a while ago. Anyone can go to their YeshID console and request an app, and YeshID will manage everything downstream. Anyone who’s clicked on the “Get Started Now” button on the YeshID website, that is.

Hint: click here or on the button to Get Started Now,
If you’ve signed up for YeshID, here's how it works:
- Go to https://app.yeshid.com
- Click on "My Apps"
- Click on "Request an application."
- Pick the application or request a different one if the one you want isn’t on the list
And you're done.Here’s how it looks:

YeshID generates a task and gets it to the right person–approver or admin–depending on how you’ve set things up. YeshIID tracks actions and notifies the requester when the request has been completed.Having YeshID manage the process and provide the artifacts needed for compliance is better than an unmanaged collection (mess) of emails or Slack messages that you have to round up and put into a spreadsheet.
Even Better: Request Directly from Slack
But why even switch focus from Slack to YeshID?With YeshID’s new Slack integration, you make the request right in Slack—no tool switching. And even better, you can request an application for someone else. Here’s how it works.
- Just type
/request - YeshID will pop up a request form in Slack

Here’s what you’ll see if you were part of T’s Tangerine Organization.

And the image below how it would look if you wanted to make a request for Figma on behalf of a guy named Steve Jobs. (Not that Steve Jobs. That one has ceased to be, expired and gone to meet his maker, is bereft of life, rests in peace… see Monty Python Dead Parrot Sketch. This is another Steve Jobs.)

The request goes straight to YeshID and gets forwarded to the right approver or administrator. YeshID monitors the entire process and constructs an audit trail. When approval has been granted, YeshID notifies both the person who has been given access and the person who requested it for them. No loose ends. All loops closed.Ready to Revolutionize Your Access Management?Don't let outdated processes hold you back. Embrace YeshID and experience:
- Increased productivity
- Enhanced security
- Simplified compliance
- Happier employees and IT staff
Start your journey to streamlined access management today with YeshID!
🚀 YeshID Monthly Release Notes: July 2024

📣 What's New This Month
We're excited to share our latest updates to YeshID! This month, we've focused on improving workflows, enhancing performance, and introducing features to make your experience smoother and more efficient.
🌟 New Features
- Slack Integration for Access Management 💬: Request and approve app access directly through Slack, streamlining the access management process.
- Custom User Fields 🏷️: Add organization-specific information to user profiles, such as employee ID or department code.
- Enhanced Email Customization 📧: Add your company logo to YeshID emails and send tailored messages for different workflows.
- Improved Google Workspace Integration 🔄: View and edit email aliases directly within YeshID for better Google Workspace management.
- Task Management Improvements ✅: Use new features like expandable subtasks and in-task discussions to improve team coordination.


💪 Enhancements
- Performance Optimization 🏎️: We've reduced the loading time of the Application view by 86%, significantly improving responsiveness.
- User Management Refinements 👥:
- Streamlined user creation process with improved email validation
- Enhanced invite link functionality to work seamlessly for already active users
- Added a check to prevent creation of users with email addresses that are aliases of existing users
- Workflow Enhancements 🔧:
- Improved task completion tracking with clearer indications of who completed or rejected a task
- Enhanced notifications for task rejections in onboarding and offboarding processes
- Added a text input for providing reasons when responding to access requests
- UI Improvements 🎨:
- Added spacing between task status and assignments for better readability
- Improved navigation with direct links from ledger items to related tasklists
- Introduced filters in the Google user directory for easier user lookup
🛠️ Fixes and Polish
We've addressed several issues to ensure smoother operation:
- Resolved an issue where the completed state display was not showing correctly
- Fixed group reset functionality when cancelling certain operations
- Improved error handling in various workflows, particularly in task validation processes
————————
We hope these updates make your YeshID experience even better. As always, we value your feedback and look forward to hearing how these changes improve your day-to-day operations. Thank you for being a part of the YeshID community!
Got an HRIS? You can streamline your Onboarding Flow with YeshID

We’ve designed YeshID to orchestrate an organization’s onboarding processes. From the moment you tell YeshID that a user will be onboarded to the moment onboarding is complete, YeshID tracks progress and takes action. YeshID expects that one of the first steps in your YeshID onboarding template is something like Create a new Google account for user.Seems a logical place to start.But in recent conversations, we have learned that lots of onboarding journeys start with a HRIS. I know, a HRIS sounds like it might be the Egyptian god of onboarding, and for all I know, it might be. But I meant it as an acronym for Human Resources Information System. It’s another one of those things I learned sitting next to an IT system admin. When onboarding starts with an HRIS - it’s the HRIS that creates the Google Account for the user.Let’s look at two different onboarding flows for “T’s Tangerines,” a company I invented to show you what the flows look like. First, here’s what the workflow would look like if T’s Tangerines had the IT Admin create the new user’s account (using YeshID, of course.)

Now here’s what it looks like if the HRIS creates the user’s account:

Let’s look into the HRIS-creates-accounts scenario a little more closely.Since YeshID always monitors your Google Workspace account all your YeshID admins are notified whenever anyone (or anything) creates a new account. If you’re an admin and HR creates a new account, you’ll get an email like this one:

Clicking Onboard on the email will lead you to the screen to fill out user information.

After filling the particulars for the detected user, you choose an onboarding template. In this case, you’d choose one that picks up after the creation of the Google user. One like this

2. When you want to run an Onboarding Template on an existing user.
You don’t have to click emails to onboard people your HRIS system has created. You can navigate to your People page and click on the ... next to their entry and onboard them from there.

You’ll get an option Onboard user

Clicking Onboard User on the previous screen will lead you to the screen to fill out user information.

After auto-filling the particulars of the detected user, you can go ahead and choose an onboarding template that simply picks up after the creation of the Google user.

Conclusion
If you’re creating Google Users with your HRIS, you can keep right on doing what you are doing. YeshID will help you control your onboarding process for a Google User created by your HRIS. And remember, YeshID will keep records of the process to help you Simplify SOC2 Compliance.
Access Management Made Easy

Editor’s note: Thanks to our Customer Success Engineer, Thilina, for authoring this week’s post on the woes (and the solution!) for access management.I used to sit next to the IT SysAdmin of a small but rapidly expanding organization. I love to people-watch, and one of the things I would see them do–always accompanied by grumbling– (I used to people-listen, too) was handling access requests.One day after a particularly loud and animated grumble, I asked:“An access request again hey? What is it this time?”“Oi! Can’t get enough of my work, eh mate??” (They were British, so they said “Oi” not “Oy.”)“But yes..it’s another access request for [they mentioned a sensitive system], and it’s the fifth one today - I swear if they ask again…” Eventually, the profanity stopped, and I understood why it was so upsetting.
- The company had a list of applications that required access to be granted (or revoked) in a recorded and auditable way. Auditable is key here.
- My Admin friend was the admin of all the applications because managing them required tech skills. But the admin was not always not the “owner” or “approver,” the key decision maker who is supposed to vet requests.
- As a result, when someone wanted access, the admin couldn’t just grant it. They had to pass the request (via email or chat message) to the approver.
- And then wait. And sometimes, wait. And then wait some more. And nag the approver. And get nagged by the user.
- And when you get the approval back, they needed to record it to make sure the spreadsheets were up to date for that quarterly compliance nonsense.
- No fun!
It is the second decade of the 21st century, and people are still doing this. There’s got to be a better way.And with YeshID - there is!
1. Enter Your Applications & Their Owners
With YeshID you can add your applications and specify the application administrators – the owners or approvers I talked about earlier.When someone wants access or is onboarded or offboarded, or there’s any other activity that concerns the owner’s applications, YeshID notifies them. This means less shoulder tapping on the admin and notifications going to the right place at the right time. And there’s an audit trail for compliance.To get started quickly with your applications, YeshID provides two ways to add the admin (and login URL):

If you have a lot of apps that you’d like to get imported into YeshID, you can use a CSV file that has your list of apps and their owners.

And upload them to YeshID to quickly import your applications.

Or you can enter them one by one or edit them this way:

2. Update the Access Grid for your Apps
Once your applications are added, you can check out the Access Grid to see the current record of app-to-user memberships.From here, you can go in and quickly check off boxes to mark which users already have access to which apps.

An even quicker way to update an app's access, especially if you have many users, is to import a CSV of users per app.

When you click into an app, you can import a CSV of email addresses and Yesh will take care of the rest.

YeshID will finish by showing you the differences so you can review the changes being made.

3. Let your Users and App Owners take care of their own Access Requests.
Now, since you’ve already done the hard work of:
- Letting YeshID know of your Apps; and
- Updating the access for your Apps
You and your users are now able to do the following:
My-Applications
Since YeshID is integrated into your Google Workspace, any of your users can navigate to app.yeshid.com/my-applications where they will see a grid of applications they already have access to. (No more wondering: “Wait, which URL was it again?”)

Request Access
Now, when one of your users requires access to one of your organization’s apps, they can navigate to “All Managed Apps” and Request Access to their app of choice. They can fill in details to provide reasons for their request.

After they submit the request, YeshID will notify the Application Owner about a pending request.

If you’re an Application Owner, you’ll be notified with a link to a page where you can see the request and choose to either Confirm or Reject.If you confirm, YeshID will generate a task will be generated for the admin, and once granted, the user will see the newly granted application the next time they click on their My-Applications grid.

And just like that, a world of shoulder tapping, lost conversations, and requests falling off the side of a desk is avoided through the use of smart technology and engineering by your friends at YeshID.
4. Use Yesh to Ace your Access Audits
With YeshID ingrained into your employee lifecycle, audits and Quarterly Access Reviews (QAR’s) become a breeze.Simply go to your Access Grid and click on “Download Quarterly Report,” which will produce a spreadsheet created for access audits.


Review the details (there’s a sheet per app!), fill in any additional comments, and just like that - your Quarterly Access Review is done.
Conclusion
Ready to reclaim your sanity? By automating access requests and approvals, YeshID empowers admins and users. Users gain self-service access requests, and admins are freed from the time-consuming manual process of nagging app owers and updating spreadsheets.Sign up for a free YeshID trial today and see how easy access management can be.
Upgrade your Checklist to a YeshList: Identity & access management done right

For the past month, we have been working closely with ten customers who have been helping us build something that solves their Identity & Access Management (IAM) problems. We call them our Lighthouse customers.
These are smart folks at companies who are either “Unexpected Google Admin”, Solo-IT team, and/or HR. We have been working with them to figure out how they can move away from manual checklists and spreadsheets that manage their: onboarding, offboarding (or provisioning, de-provisioning), and access requests.
(If this sounds like you, you might qualify to climb into the next Lighthouse group.)
We’re working with them to replace their checklists and spreadsheets with something smarter - YeshLists.
A YeshList template is a pattern for a smart checklist. It’s kind of like a task template--the kind that you might create in Asana, Notion, or Google Sheets, but smarter. It does some of the automation and orchestration of getting the task list done for you.
You make a Yesh template by listing the steps for an activity--say onboarding or offboarding, YeshID can automate tasks within Google Workspaces like ”Create a new Google Account” or “Lock Workspace.” Or they can be automated outside Google Workspaces, like “Send welcome email.” Or they can be delegated, like “Have the Slack Admin set this person up for the Slack channels needed for a new hire in marketing.” Or manual like “Order a Yubikey” or “Send them a welcome swag box.”
Here’s an example of an Onboarding template. Notice that the YeshID template is smart enough to make the dates relative to the start date.
Here’s what a YeshList template looks like:

Once you’ve got a template customized to your organization--or even to a particular department--and someone is ready to start you put in the person’s name, start date, and some other information, and YeshID will create a YeshList from a template.
And then, it will RUN the template for you. If a task is automated (like some of the Google tasks we mentioned above), YeshID will make it happen when it’s supposed to happen. So think “I don’t need to sit in front of the computer at exactly 5 pm and suspend Joe from Google Workspace.” You can trust that YeshID will do it for you.
If we cannot automate a task--like reclaiming a license or de-provisioning--we route the request to the person responsible for the task and ask them to respond when it is completed. And when they respond, we mark it as done.

But wait, there’s more! In addition to helping you ensure someone is offboarded or onboarded properly, we will automatically update our access grid so that you can use it for compliance purposes.

Finally, we have an end-user view that lets your employees see what applications they have access to and request access to apps they don’t have. This will help you track access for compliance purposes and make sure they are properly offboarded from the apps they have access to upon departure from the company.

We are looking for anyone who:
- Uses Google Workspace
- Works at a company between 10-400 employees
- Holds the responsibility of IT, Security, HR, compliance (or some combination thereof) in their job description
- (not requirement, but bonus) Have SOC2 or other compliance requirements
..to work with us to setup YeshID in your environment. We'd love to show you how you can be more efficient, secure, and compliant with us!If you are interested, please reach out to support@yeshid.com. Of course, you are always welcome to sign up in your own time here.
Simplify SOC 2 Compliance with YeshID

Navigating the complexities of SOC 2 compliance is daunting. Said more simply: getting SOC 2 certified sucks. It will always suck some, but it won’t suck quite as much if you’re using YeshID.Certification is important and becoming vital. Certification assures others that your systems are secure, their data will be protected, and your processes align with stringent regulatory standards. More and more companies will refuse to do business with you if you aren’t SOC 2-certified. You may be familiar with companies like Vanta, Drata&Secureframe that help with certification. We’ve gotten SOC 2 certified with their help.SOC 2 certification requires well-defined access management protocols and evidence that the protocols are being followed. The first part is “relatively” easy: anyone can design a protocol. The second part is hard, and it’s where YeshID helps big-time. YeshID simplifies and streamlines identity & access management (instead of cobbling together checklists, spreadsheets, and ticketing systems). And YeshID keeps track of what you do. YeshID helps you get SOC 2 (and stay SOC 2) with more SOCcess.Let’s see how it works.
CC and SOC 2
Almost everyone knows that CC stands for the Common Criteria for Information Technology Security Evaluation and that it’s an international standard (ISO/IEC 15408) for computer security certification. (Wikipedia, CC website)Almost everyone knows that SOC 2, or Service Organization Control Type 2, is a cybersecurity framework developed by the American Institute of Certified Public Accountants (AICPA) in 2010.And almost everyone knows the relationship between SOC 2 and the Common Criteria. But for the one or two readers who don’t know, we’ve spelled out some of the connections and how YeshID helps.
Logical and Physical Access Controls
SOC 2 compliance ensures that only authorized personnel can access your systems and data. YeshID excels in managing access controls:
- Production Deployment Access Control (CC 6.1): YeshID restricts access to production deployments by controlling who can modify application access. This ensures that only authorized personnel can deploy changes to production environments.
- Access Reviews (CC 6.2, CC 6.3, CC 6.4): Conducting quarterly access reviews is a crucial part of maintaining SOC 2 compliance. YeshID facilitates these reviews by providing comprehensive information on user access rights, helping you ensure that access is appropriately restricted and any required changes are tracked to completion.
- Restricted Database and Network Access (CC 6.1): YeshID helps restrict privileged access to production databases and networks to authorized users with a business need. By controlling application-level permissions, YeshID indirectly restricts access to critical systems.
- Remote Access MFA (CC 6.6): YeshID integrates with Multi-Factor Authentication (MFA) solutions to enforce MFA for remote access, ensuring that only authorized employees can access production systems remotely.
Enhancing Processing Integrity and System Operations
Maintaining the integrity of your data processing and monitoring system operations are vital components of SOC 2 compliance. YeshID supports these areas through:
- Change Management (CC 8.1, CC 5.3, CC 7.1): YeshID enforces change management procedures by requiring approvals and tracking changes in access rights. This ensures all changes are authorized, documented, tested, and reviewed before implementation.
- Log Management (CC 2.1): YeshID generates logs for actions such as account provisioning, deprovisioning, and access modifications, which are essential for auditing and reviewing system changes.
Supporting Control Environment and Communication
A robust control environment and effective communication are essential for SOC 2 compliance. YeshID helps in these areas by:
- Code of Conduct and Confidentiality Agreements (CC 1.1): YeshID can require employees to acknowledge the company’s code of conduct and sign confidentiality agreements during onboarding, ensuring a commitment to integrity and ethical values.
- Security Awareness Training (CC 1.4, CC 2.2): YeshID ensures employees complete security awareness training during onboarding and annually thereafter, helping maintain a high level of security awareness across the organization.
- Roles and Responsibilities (CC 1.3, CC 1.4, CC 1.5): YeshID specifies the roles and responsibilities of employees for various systems and applications, ensuring that everyone is aware of their internal control responsibilities.
- System Changes Communication (CC 2.2): YeshID logs changes to access rights, effectively communicating system changes to authorized internal users.
Seamless Onboarding and Offboarding
Managing employee access throughout their lifecycle is a critical aspect of SOC 2 compliance. YeshID excels in:
- Onboarding New Users (CC 6.2): YeshID simplifies the registration and authorization of new internal and external users, ensuring that only authorized users are granted system access.
- Revoking Access Upon Termination (CC 6.3, CC 6.5): YeshID facilitates the offboarding process by revoking access for terminated employees, ensuring compliance with termination policies and reducing the risk of unauthorized access.
- Unique Account Authentication (CC 6.1): YeshID integrates with authentication systems to enforce unique account authentication, ensuring each user has a unique username and password or authorized SSH keys.
Conclusion
With YeshID, you can streamline your IAM processes, enhance security, and ensure compliance. Our robust features help you manage employee access, conduct thorough access reviews, enforce change management procedures, and maintain a secure control environment.Get SOC 2 certified and stay SOC 2 certified with YeshID. Let us help you simplify the complexities of managing employee access and achieve SOCcess. Try for free now!
Release Notes for May 2024: New Features, Enhancements and Fixes

May 2024 YeshID Update: New Features, Enhancements, and Fixes
Greetings YeshID Community!
We're excited to share the latest updates from May, designed to enhance your YeshID experience with new features, improvements, and fixes for a smoother and more efficient digital workspace.
🚀 New Features to Boost Your Workflow
- Agent Yesh AI: Use AI to generate onboarding and offboarding workflows, saving you time and effort.
- Comprehensive User Ledger: Gain complete visibility into user actions with our new comprehensive user ledger, tracking all activities and events, including suspensions, un-suspensions, additions, and removals, all in one place. Manual event addition is also supported.
- Enhanced Offboarding Process: Streamline offboarding with new tasks for archiving users, removing them from all applications and Google Groups, and disabling 2FA.
- Support for Temporary Employees: Add optional end dates during onboarding to manage contract employees effectively.
- Nudge Button: Prompt task owners to complete tasks with notifications via email and Slack.
- App Requests: Users can now request apps from the entire YeshID catalog or custom apps, expanding your toolset.
- Custom Onboarding Emails: Admins can schedule personalized emails to be sent to employee inboxes during onboarding.
✨ Enhancements for a Better Experience
- Task List Improvements: Enjoy clearer communication, easier management, and consistent scheduling with green indicators for successful tasks, required messages for task rejections, a default timezone setting, and delete buttons.
- Improved Notifications: Admins will stop receiving notifications if they have zero tasks, reducing unnecessary alerts.
🔧 Fixes to Smooth Out Your Operations
- Optimized Performance and Integration: Enhanced Access Grid performance, improved error reporting and form validation, better Slack channel settings and invite links, and increased timezone support.
- Email Notifications: Optimized notifications, removed daily task reminder emails, and updated weekly email format.
- Task List Templates and Off-boarding: Automatically updated templates when applications are deleted, and comprehensive off-boarding tasks included in default templates.
- UI and Messaging Improvements: Various UI tweaks, improved task rejection messaging, and better error messages.
Try YeshID today and tell us what you think by joining our Slack community — link in the admin view after signup.Your insights help us shape the future of YeshID!
The AI Revolution Comes to IAM: Introducing YeshAI

YeshID’s mission is to deliver identity & access solutions that are simple, secure, and trustworthy. Today, we’re releasing our first AI agent. It’s designed to simplify onboarding and offboarding workflows. Why onboarding and offboarding? These workflows are mandatory for SOC2 compliance. Crafting playbooks for specific roles often becomes a major source of IAM admin friction and frustration.In our YeshList blog post, we discussed how we tackled this problem when we created task templates. The first templates we made were for onboarding and offboarding. Introducing AI takes it a step further and makes it even easier.Simply describe the type of playbook you need, and our AI will suggest a workflow optimized to meet SOC2 standards. This gives you a solid foundation, making editing and customization faster than starting from scratch.Why this matters to you:
- Save time: Focus on the strategic aspects of IAM, not repetitive tasks.
- Reduce risk: Get AI-driven help to craft comprehensive playbooks, minimizing errors.
- Gain confidence: Every action is transparent and auditable, building trust in the process.
Experience YeshID LLM by visiting task templates in YeshID and learn how it can enhance your employee onboarding workflows. (Coming soon--support for offboarding and the messy middle.)
The Power of AI, Guided by Our Principles
We’ve been experimenting with LLMs for a while. We saw their potential to revolutionize identity and access management. Incorporating LLM reasoning capabilities will be a productivity multiplier, resulting in a better, more secure, and seamless experience for IAM managers and employees alike. We have a lot planned, and our plans are rooted in our core principles:
- Simple: We believe technology should make your life easier, not harder.
- Secure: Protecting your data is our utmost priority.
- Trustworthy: We build on a firm foundation of transparency and reliability.
Responsible AI: Balancing Innovation with Caution
AI can reason and use tools to intelligently evaluate and automate access requests, enforce security policies, perform audits, handle employee onboarding and offboarding, resolve integration issues, provide real-time support, optimize spending, and more. Much more. It's a powerful tool that can work 24/7, reduce human error, and provide invaluable insights.But, as we have all learned, there are problems. AIs can hallucinate, be tricked, and create disaster at scale. That's why we will only ship AI-powered features when we're confident they are secure, reliable, and work as you expect them to.
AI as Your Trusted Partner
We believe in a future where AI empowers IAM managers to be more effective and secure. It's a future where routine tasks are handled seamlessly, and you can focus on what matters most. Our commitment to our principles means we'll bring you these innovations quickly and responsibly, ensuring your experience with YeshID remains simple, secure, and trustworthy. We move fast, and much more is coming soon.If you'd like to see how YeshAI can help you make better onboarding decisions, check out the bot on our website here. However, if you are ready to experience the power, security, and compliance of an AI-enhanced IAM, then signup to get started with YeshID for free.
Centralized IAM Playbooks: The Key to Solving SaaS App Access Management Chaos

If you're an IAM (Identity and Access Management) manager in a small or medium-sized business, you know the challenge of trying to secure a growing ecosystem of SaaS (Software as a Service) applications. Every day, there’s a new app that one of your employees must have, and it's your job to ensure access is granted quickly, consistently, and securely. But with each new app, the risks of inconsistent access management grows. Is there a way to solve this challenge? Of course, there is. Why else would I be writing this and you reading it?Read on.Many apps can't be easily integrated into your IAM system. The apps might support SAML (Security Assertion Markup Language) for single sign-on (SSO), but that's often locked behind an expensive “Enterprise” tier. And even if you can afford it, automated provisioning requires SCIM (System for Cross-domain Identity Management), which is even less commonly supported. SCIM is an open standard that defines a schema for exchanging user identity information between systems. It allows IAM systems to automate the provisioning, de-provisioning, and management of user accounts in SaaS apps, ensuring that access is always in sync with the user's current role and employment status.

Without SCIM, IAM managers are forced to rely on manual processes and custom integrations to manage SaaS app access. As your team and SaaS portfolio grow, these manual processes become increasingly unsustainable and error-prone.
The Challenge: SaaS App Sprawl and Access Management Complexity
So what do you do? Many fall back on spreadsheets and a patchwork of playbooks to try to keep up. But this approach has serious risks – and the risks get worse as you add more apps and more people with varying access needs and roles. This perfect storm of complexity spirals out of control, leading to inconsistencies, security risks, and compliance issues.
The Risks of Inconsistent Access Management
When onboarding and offboarding processes vary from app to app, it's easy for things to fall through the cracks.Imagine a new sales rep who starts work excited to dive in and close some deals, only to find they can't access the CRM because their account hasn't been provisioned. Or consider the IT team that thinks they've completed an employee's offboarding, only to discover weeks later that the ex-employee still has access to sensitive data in a cloud storage app. These inconsistencies not only frustrate employees and waste time they also create serious security risks that compound with each new app.
The Dangers of Access Creep
Then there's the access creep. As employees move between roles, their permissions don't always keep up. “Ex-engineer Al Sutton revealed that despite quitting 18 months ago he still retained access to Twitter's central file store on GitHub, a website used by software developers to store source code.” — The TelegraphConsider a tech startup that uses GitHub Teams to manage their code repositories. When an engineer leaves the company, their GitHub account isn't always immediately deprovisioned from the company's GitHub organization. If the IT team is busy or forgets to follow up, the ex-employee could retain access to critical codebases, infrastructure-as-code templates, and other sensitive IP long after they've left. This lingering access is a major security risk even if the engineer has no malicious intent. Why?If the engineer’s personal GitHub account is ever compromised, hackers could then gain access to the company's crucial assets. As your company grows and more employees cycle through, the risk of this happening increases.
The Danger of Poor Visibility
Perhaps most concerning is the lack of visibility into user permissions across SaaS apps. Even with an IAM system in place, the lack of automation makes it impossible to fully track and manage access across all SaaS apps. Consider an auditor who asks to see a report of everyone who has admin access to your financial systems. If those permissions are managed in a spreadsheet or worse, in someone's head, you're going to have a tough time pulling that report together. And if you can't confidently prove who has access to what, you risk failing the audit and losing out on big deals with security-conscious customers. Achieving SOC2 compliance with inconsistent access management is a daunting task that only gets harder as your SaaS ecosystem expands. And even if you're not pursuing SOC2 compliance, put yourself in your customers' shoes: would you buy a product from a company that can't even track something as basic as what their employees have access to?The longer you wait to address these issues, the more entrenched and intractable they become. That's why it's critical to implement a solution now, before your SaaS environment grows too complex to manage.
The Solution: Centralized IAM Playbooks
By bringing all your access management processes together in one place - including manual steps, automated workflows, and everything in between - you can ensure consistent, timely execution of access changes across all your apps, now and in the future. You gain a single pane of glass to monitor and manage permissions. And you can easily generate the reports you need to breeze through your next compliance audit, no matter how many SaaS apps you've added to your stack.
Why Legacy IAM Falls Short
But not all IAM solutions are up to this task. Legacy IAM systems often lack the flexibility and extensibility needed to implement truly centralized playbooks. They might handle the basics of single sign-on and provisioning, yet struggle to accommodate the custom workflows and manual steps that are a reality of life with SaaS apps, especially as your app portfolio diversifies.
Introducing YeshID: Your Centralized IAM Playbook Platform
This is where YeshID comes in. Our platform is designed from the ground up to enable seamless, centralized playbook implementation. YeshID is the connective tissue between your IAM system and all your SaaS apps, no matter their native capabilities. With YeshID, you can define and automate access management playbooks that work across your entire app ecosystem. You can quickly onboard and offboard users, keep permissions in sync with job roles, and always know who has access to what – even as your SaaS landscape evolves.Looking for a centralized IAM playbook creation guide? YeshID has you covered. Our platform makes it easy to create automated IAM playbooks that solve inconsistent onboarding and offboarding, help you manage access creep, and improve your compliance audits. We've compiled the best practices for SaaS access management playbooks into our intuitive interface, so you can get started quickly and confidently.Best of all, YeshID doesn't require you to upgrade all your SaaS subscriptions to the most expensive enterprise tier. Our platform works with the tools you already have, filling in the gaps and bringing everything together under one roof.
Take Control of Your SaaS Access Management with YeshID
If you're tired of juggling multiple access management playbooks, losing sleep over compliance audits, and constantly worrying about the security risks lurking in your SaaS shadows, it's time to take a look at YeshID. With our platform, you can finally close the loop on IAM and focus on the high-value projects that really matter.Access management in the age of SaaS sprawl is a big challenge, but it's not an impossible one. By embracing centralized playbooks and a tool like YeshID, you can tame the access management chaos, stay secure and compliant, and prove the strategic value of IAM to your organization. The future of identity and access management is here – and the risks of inaction are too high to ignore. Are you ready to seize control of your identity & access management? Get YeshID Onboard for free and start today.
The Identity Management Struggle: Overpromised, Underdelivered, and How to Fix It

In the world of identity management, the struggle is real. Identity management involves controlling and managing user identities, access rights, and privileges within an organization. At YeshID, we've seen it all: from Google App Scripts built inside Sheets to Notion databases, full of outdated and fragmented documentation. We’ve seen people who have unexpectedly inherited the identity management job and people spending all their time reacting to HR onboarding and offboarding surprises. We’ve seen managed service providers with creative solutions that too often fall short. And we’ve seen IAM vendors overpromising integration and seamless system management and delivering upgrade prices and uncontrolled manual processes.It's like a tangled web of issues that can leave you feeling trapped and overwhelmed. The result? A complex set of challenges that can hinder productivity, security, and growth:
- Workflow Issues
- Redundant Workflows: You have workflows dedicated to verifying automation, manually handling unautomatable tasks, and fine-tuning access in each app, including sending requests and reminders to app owners and the time-consuming quarterly access reviews.
- Workflow Dependencies: Intertwined workflows make it hard to untangle them, leading to a domino effect when changes are made.
- Bottlenecks and Delays: Manual steps and the need to chase approvals slow down processes, causing frustration and reduced efficiency.
- Data Management and Accuracy
- Data Inconsistency: Manual intervention and multiple workflows increase the likelihood of data inconsistencies, such as discrepancies in user information across different systems, leading to confusion and potential security risks.
- Email Address Standardization: Maintaining a consistent email address format (e.g., firstName.lastName@) can help with organization, but ensuring conventions are followed can be complex, especially as the organization grows..
- Security
- Secure Access: Enforcing secure access practices is non-negotiable, but it's an uphill battle, including:
- MFA: Multi-Factor Authentication adds protection against compromised credentials, but getting everyone to comply can be a challenge.
- Secure Recovery Paths: Ensuring account recovery methods aren't easily exploitable is crucial, but often overlooked, leaving potential gaps in security..
- Principle of Least Privilege: Limiting user permissions to only what's necessary for their roles is a best practice, but permissions can creep up over time, leading to excessive access rights and failing compliance audits.
- Regular Updates and Patching: Keeping systems updated and patched is essential to address vulnerabilities and maintain a secure environment.
- Secure Access: Enforcing secure access practices is non-negotiable, but it's an uphill battle, including:
- Compliance
- Compliance Concerns: Meticulously designing workflows to collect evidence that satisfies compliance and regulatory requirements is time-consuming and often confusing.
- Operational and Growth Challenges
- Knowledge Silos: Manual processes mean knowledge is held by a few individuals, creating vulnerabilities and making it hard for others to step in when needed, hindering business continuity.
- Audit Difficulties: A mix of automated and manual workflows without proper documentation makes audits challenging and prone to errors, increasing the risk of non-compliance.
- Difficulty Scaling: As the organization grows, the complexity of fragmented processes hinders growth potential, making it difficult to onboard new employees and manage access rights efficiently.
- Complex Offboarding: Workflows must ensure proper, gradual account removal to balance security, archiving, business continuity, and legal compliance concerns.
- Mandatory Training: Tracking mandatory training like security awareness within the first month of employment is an ongoing struggle.
- Group and OU Assignments: Correctly placing users in groups and organizational units is key for managing permissions, but automating this requires careful alignment between automation rules and the company's organizational structure, which can be challenging to maintain.
Recommendations: Untangling the Web
YeshID’s YeshList gives you a way to untangle the process web organizing centrally, distributing the workload, and coordinating actions.
- Implement Company-Wide Accountability
- Establish a regular cadence for an access review campaign to ensure permissions are regularly reviewed and updated.
- Create a simple form for managers to review access for their team members, making it easy for them to participate in the process.
- Use a ticketing system or workflow tool to track requests and ensure accountability, providing visibility into the status of each request.
- Embrace Role-Based Access Control (RBAC)
- Design granular roles based on common job functions to streamline access granting, reducing the need for individual access requests.
- Track roles in a spreadsheet, including Role Name, Description, Permissions Included, and Role Owner, to maintain a clear overview of available roles and their associated permissions.
- Upgrade to Google Groups for decentralized role ownership, employee-initiated join requests, and automation possibilities, empowering teams to manage their own access needs.
- Use RBAC to speed up audits by shifting focus from individual permissions to role appropriateness, simplifying the audit process.
- Tool Examples: Google Workspace allows custom roles, but other identity management solutions may offer more robust RBAC capabilities.
- Conduct Regular Application-Level Access Reviews
- Periodically review user access within each critical application to close potential security gaps and ensure that access rights align with job requirements.
- Restrict access to applications using your company's domain to improve security and prevent unauthorized access from external accounts.
- Utilize tools like Steampipe or CloudQuery to automate the integration of application access lists with your employee directory, enabling regular comparisons and alerts for discrepancies, saving time and reducing manual effort.
- Invest in Centralized Workflow Management
- Consolidate Workflows: Map existing processes, find overlaps, and merge them within a centralized tool.
- Prioritize High-Impact Automation First: Target repetitive, time-consuming tasks to get the most value.
- Prioritize Data Standardization and Integrity
- Define clear rules for email addresses, naming, and data entry, and enforce them during account creation to maintain data consistency across systems.
- Implement input validation to catch inconsistencies early, preventing data quality issues from propagating throughout the organization.
- Schedule data hygiene checks to identify and correct discrepancies between systems.
- Use a tool or script for account creation to ensure consistency.
- Strengthen Security with Key Enhancements
- Mandate MFA for all accounts.
- Review Recovery Methods: Favor authenticator apps or hardware keys over less secure methods.
- Regularly review user access levels and enforce least privilege principles.
- Use your company's Identity Provider (IdP) for authentication whenever possible to centralize access control and simplify user management.
- Make Compliance a Focus, Not an Afterthought
- Document Workflows Thoroughly: Include decision points and rationale for auditing purposes.
- Build requirements for proof of compliance directly into your automated workflows.
- Tackle Operational Challenges Head-On
- Reduce errors with in-workflow guidance, providing clear instructions and prompts to guide users through complex processes.
- Cross-train IT team members to reduce single points of failure.
- Develop templates for recurring processes to streamline efforts and ensure consistency.
- Democratize Identity Management
- Empower employees and managers to resolve access requests whenever possible through:
- Automated Approval Workflows: Set up workflows with pre-defined rules to grant access based on criteria.
- Manager Approvals: Delegate access request approvals to direct managers for their teams.
- Self-Service Access Management: Consider a self-service portal for employees to request and manage basic access needs.
- Empowered Employees and Managers: Enable employees and managers to add or remove employee accounts for specific apps as needed.
- Empower employees and managers to resolve access requests whenever possible through:
The Light at the End of the Tunnel
As you evaluate solutions, keep these factors in mind:
- Cost-Effectiveness: Prioritize solutions with free tiers or flexible pricing models.
- Ease of Use: Choose tools with intuitive interfaces to encourage adoption.
- Scalability: Ensure solutions can grow with your company.
Identity management is a critical aspect of any organization's security and operational efficiency. By recognizing the common challenges and implementing the recommendations outlined in this post, you can untangle the web of identity management struggles and create a more streamlined, secure, and efficient process.YeshID Orchestration is here to help you on this journey, bringing Identity and Automation closer together for a more dedicated, consolidated, and simple solution. Don't let identity management hold you back any longer – take control and unlock the full potential of your organization today. Try for free today!
Streamlining Employee Management with YeshID

Is your company using a patchwork approach to employee onboarding and offboarding? Or is everything in one place? Are you relying on a combination of HR tools, IT tools, spreadsheets, checklists, and communication across email and Slack?YeshID gives you a simple, clean way to manage centralized and distributed Identity and Access Management (IAM). It’s centralized (everything in one place) and decentralized (workload doesn’t land on one set of shoulders). YeshID integrates with your existing HR and IT processes, regardless of complexity.
YeshID Simplifies Onboarding
When your new hire shows up, bright-eyed and ready to rock, the last thing you want to do is drain that enthusiasm. OK, it’s not the last thing. But never mind. You don’t want it to happen. Good news. You can use YeshID to create a smooth onboarding experience for new hires.
Scenario 1: No HR or Limited IT Integration
YeshID acts as your one-stop shop for managing both HR and IT tasks during onboarding. YeshID lets you create playbooks that include manual steps like ordering a laptop, sending company swag, compliance training, along with automated tasks like user provisioning in Google Workspace, assigning them to groups and departments, and coordinating access to other applications.By centralizing the orchestration process in YeshID, you ensure a streamlined and organized onboarding experience for your new hires. By decentralizing--assigning tasks to people other than your unexpected IT person--you can get the work done faster and better.
Scenario 2: Existing HR Tool with Partial IT Provisioning
Maybe you’ve got an HR or IT tool that handles some basic IT provisioning. You probably know that it falls short if you don’t have the fancy enterprise license for all of your applications. And so you are back to a spreadsheet or document to handle the rest of your IT process.But don’t worry! YeshID will seamlessly integrate with your existing process and will handle provisioning coordination (with the application owners) of the lower license tier applications that don’t have SAML/SCIM support.If an HR tool creates a new user in Google Workspace, YeshID will send an alert to ensure that the rest of the onboarding takes place. You can then assign a pre-built playbook to coordinate the remaining tasks on your checklist.
YeshID: The Advantages
- Simple Setup: Get started with YeshID in minutes, not days or weeks.
- Flexible Workflows: YeshID adapts to your existing processes, allowing you to handle manual and automated tasks regardless of license type.
- Effortless Compliance: YeshID simplifies compliance by centralizing access requests and approvals, ensuring a clear audit trail.
- Enhanced Security: YeshID reduces human error and improves security by tracking identity life cycles and permissions so that offboarding is mistake-free.
- Happy Teams: YeshID empowers your team with clear processes, reduces busy work, and frees them to focus on strategic tasks.
Ready to Streamline Your Onboarding Process?
YeshID is the key to a smoother, more secure, and more efficient employee onboarding experience. Get started today and see the difference YeshID can make for your organization.
Easier & more secure employee offboarding for small businesses with YeshID

When people talk about onboarding and offboarding, onboarding gets all the attention. We talk about how to make a seamless onboarding experience and get your new employee to work fast. How to provide them with the birthright apps they need to do their job. But we don’t talk about what happens when it’s time to part ways with an employee and what needs to be done then. Ensuring proper offboarding is a huge concern for small businesses. When you part ways with an employee, there’s a lot you can forget that can leave you vulnerable:
- If the recovery email and phone number aren’t reset, the user might be able to regain access to their account.
- If you forget to forward the user’s email, you might miss out on important communication from your customers.
- If you don’t promptly deprovision the user’s accounts from third-party applications, you might be paying more in license costs than you need.
Luckily, it’s not all up to you to remember every step. Here’s how you can handle employee offboarding in YeshID.
Easier employee offboarding in YeshID
To offboard someone in YeshID, select that person from your Organization, and in the side car that opens, click ‘Offboard.’ From here, you can choose:
- What action you wish to perform (suspending vs deleting)
- Who, if anyone, to assign access to the employee’s Google Docs/Drive, Calendar, etc. data
- Who, if anyone, should receive new email sent to the old address
- When you would like the process initiated
As long as you are managing application access in YeshID, we will also create subtasks for applications which need to be deprovisioned. This is a big differentiator from how you can manage this process in the Google Workspace console. Offboarding directly in the console only turns off “sign in with Google” accounts for the user. But what about accounts that use a work email and password? YeshID helps you track all application access to make sure the user is offboarded from any company applications they had access to.
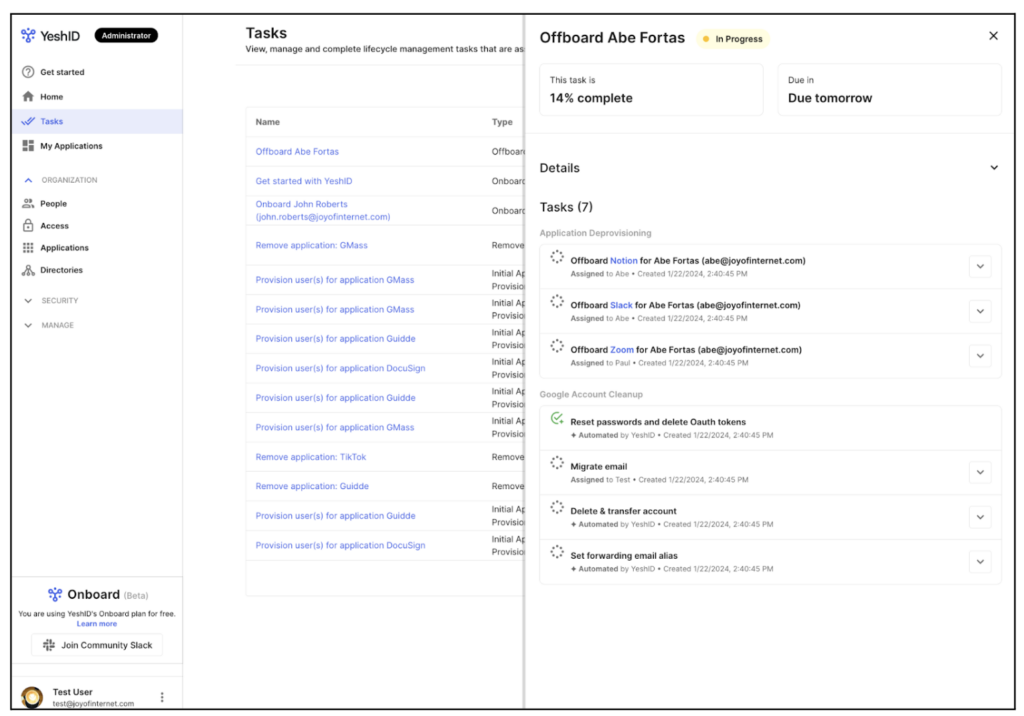
Now let’s dive into each option.
Offboarding with the intention to suspend
This is a good option if you want to remove access for a user but don’t want to completely delete them. For example, maybe the user was privy to critical business data that you don’t want to risk losing, or maybe it’s a seasonal contractor that you plan to reinstate later in the year. Here’s what happens when you suspend a user in YeshID:
- The user's data will be kept, but they won't receive emails, calendar invitations, or files as long as they're suspended (note: this does require you to maintain a Google Workspace license for the user).
- Once you specify that the user is suspended, you will be prompted to create a task list to offboard the user from the applications they have access to.
- Emails are sent to the application administrators, prompting them to remove access for the user at specified time.
- You can “unsuspend” a user at any time, as long as they're not deleted.

Offboarding with the intention to delete
This is a good option if you know that you want to remove the user entirely. When you delete a user, YeshID will:
- Reset the Google Workspace password, which will revoke any application-specific passwords tied to the user’s account
- Log the user out of every Google session across all of their devices by invalidating their session cookies
- Delete the user’s account recovery email and phone numbers
- Revoke all OAuth grants associated with the user’s account
- Prompt you to create a task list to offboard the user from the applications they have access to
- Send emails to application administrators, prompting them to remove access for the user at the specified time.
When you delete a user, YeshID will also create a list of tasks that an admin must manually complete. While the above steps will happen automatically, these steps require confirmation from the admin to continue:
- Confirm that they have transferred all email from the account they wish to save, by using the Google Data Migration Service.
- Initiate any data transfers that were configured in the YeshID offboarding dialog (Google Docs/Drive, Calendar, etc.).
- Delete the account in Google Workspace.
- Set the old email address as an alias on another account so you can continue receiving new email for the old account.
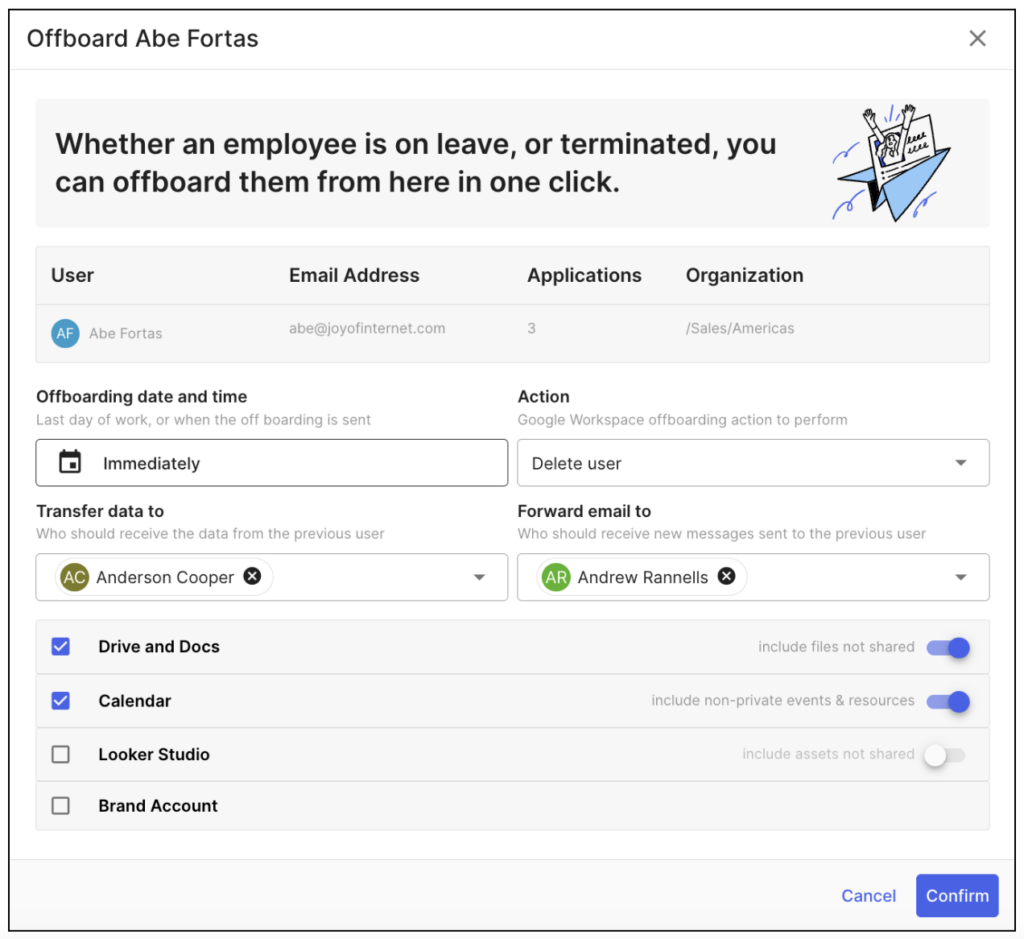
It’s worth noting that the last step here, creating an alias, can’t be done until you delete the user. Then you have to remember to come back to create the alias. It’s an easy step to forget — thankfully you have that task reminder in YeshID. 😉
Easier offboarding with technology
The task of offboarding a user contains many distinct steps, each of which can lead to issues if forgotten. Why take the risk? YeshID uses ready-made procedures that ensure you follow offboarding best practices and keep your environment safe and running smoothly. See how easy it can be.
Buyers Remorse in Identity and Access Management: There's no silver bullet

Suppose you’re a growing company. Then you’ve got a growing Identity & Access Management (IAM) problem--because that happens when you grow. You’ve probably been using a combination of spreadsheets, emails, checklists, and half-remembered procedures to handle onboarding, offboarding, and compliance audits. Then along comes an IAM vendor who pitches their shiny identity provider service: a vision of IAM nirvana with automated provisioning, de-provisioning, and access requests. All you have to do is sign up and push a couple of buttons. (After you pay them, of course.) Here’s what the IAM vision looks like:
- One Platform, Seamless Control: Manage all your SaaS applications' identities and access in a single, centralized IAM platform. No more jumping between different tools or spreadsheets.
- Automated Efficiency: Streamline user access with automated provisioning and de-provisioning across all connected applications. Forget manual tasks and ensure instant access when needed.
- Cost-Effective Security: Secure your SaaS environment without breaking the bank. Expect transparent pricing for essential IAM features like SCIM/SAML support.
Great vision. But according to the customers we’ve talked to, it’s a mirage.Here’s what IAM reality looked like once they encountered it:
- Fragmented Landscape: Many IAM tools only manage a limited subset of SaaS applications, leaving you with a patchwork of tools and manual processes for the rest.
- Paywalled Integrations: Access to crucial features like SCIM/SAML often requires upgrading to more expensive tiers with your SaaS providers.
- Inconsistent Implementation: Even when available, SCIM/SAML implementations can vary significantly between SaaS providers, causing compatibility issues and integration headaches.
- Manual Mayhem: Unsupported applications force admins to resort to manual workarounds, relying on static documentation and informal communication (emails, Slack, spreadsheets) to manage access, leading to inefficiency and security risks.
So they experience IAMBM - an acronym I just made up for Identity and Access Management Buyer’s Remorse. Automating a chaotic, uncontrolled, disorderly process does not make it harmonious, controlled, or orderly. You replace a messy manual mess with a messy automated mess.Bill Gates said it right: “The first rule of any technology used in a business is that automation applied to an efficient operation will magnify the efficiency. The second is that automation applied to an inefficient operation will magnify the inefficiency.”
Shifting the Paradigm
Consider orchestration before automation. YeshID’s orchestration lets you capture and organize your tasks in playbooks. As you organize your activities--in one place, with a single source of truth--you can automate when it’s cost-effective, convenient, and technically feasible. You can integrate manual processes, partly automated processes, and completely automated processes using a single interface. Orchestration lets you delegate tasks, follow up, and distribute work without losing visibility and control. Orchestration will make your IAM activities transparent, orderly, distributed, and more secure. IAM is about people, not just technology. Don't fall into the automation trap. By empowering your team and focusing on clear, trackable processes, you can achieve secure and efficient access management without the "buyer's remorse" hangover.
Try YeshID
Let YeshID be your partner in keeping your identity and access management realm simple, effective, and secure. Get YeshID Onboard for free and start today.
3 reasons to ditch the access management spreadsheet for YeshID Access Grid

The age old method of keeping track of who has access to different applications is typically a spreadsheet. People on the left, and apps on the top. A new person comes or goes, and you update the spreadsheet. Easy enough, right? Except that your head of engineering gave Jira access to someone and forgot to tell you.And then there was that time that you were on vacation and didn’t get to personally handle offboarding, so who knows what did or didn’t get deprovisioned. Oh, and of course, there’s that one contractor who just needs access to a few things — wait, are they still doing work for you?Suddenly what you’re calling access management doesn’t feel reliable. In 2024, it’s time to ditch the spreadsheet in favor of technology that makes your life simpler. Today, we’re excited to introduce Access Grid for YeshID, the only identity and access management platform purpose-built for companies running in Google Workspace.Access Grid might look like what you’re used to, but it’s much more powerful and easier to maintain. By reducing the orchestration of access management, we make it easier to be efficient and compliant. Here are three reasons to ditch your spreadsheet this year.
- A spreadsheet is static.
Your spreadsheet is just that — a spreadsheet. It’s simply a list you have to maintain. Your spreadsheet doesn’t automatically send an email or remind someone of a provisioning task. Updating a field in Access Grid, on the other hand, kicks off a workflow, allowing you to track access as it’s being granted or revoked. When you check a box to indicate that a user should have access to an app, a task is automatically created and assigned to the administrator of the app. Access Grid shows a grayed box, indicating that it’s still to be provisioned. Once the administrator confirms that they’ve granted access, Access Grid is automatically updated.

- A spreadsheet is manual.
Unlike with your spreadsheet, Access Grid has the ability to automatically identify users for commonly used applications that YeshID is integrated with. That means you don’t have to manually input who has access to your organization’s instances of Slack, Notion, and Hubspot. Depending on the size of your organization, this can save tons of time.

- A spreadsheet is “all you.”
Access Grid’s centralized workflow makes your spreadsheet a living access table — and that means it’s not solely on you to ensure it’s always current. Once you kick off that workflow, you can set, forget, and let Access Grid handle the rest. By automating requests to your internal application owners, you can take yourself out of being the middleman.

Ditch your access management spreadsheet
The spreadsheet method had its day, but you can see how it might prevent SMBs from leveling up and even unintentionally add operational, technical, and security debt to take care of later. What’s more, access management isn’t just about ensuring internal accuracy. It presents a security and compliance risk as well. If you’re ready to ditch the spreadsheet for a more streamlined way to onboard/offboard and a more secure way to manage app access, look no further. YeshID is SOC II compliant, in the Google Workspace Marketplace, and has a big ol’ DELETE button if you decide it’s not for you. Learn more!
OAuth oh oh!

What happened?
On December 16th Truffle Security disclosed a Google OAuth vulnerability that allows employees, even after leaving a company, to retain access to applications like Slack and Zoom. The vulnerability arises from the ability to create Google accounts where the email address has the domain of the corporate organization but does not actually belong to that organization. This poses a risk to organizations, service providers like Zoom and Slack, and Google itself.
How does it work?
1. First, the user must have an account in your corporate Google workspace, such as user@example.com2. Then the user creates a new personal Google account, using their existing email, but they add “+something” to the user name part of the email, eg. user+something@example.com. Because Google will essentially ignore anything after the + in an email address, the user will be able to receive all the verification emails in their corporate inbox. (They need to do this in advance of leaving the organization.)

User must click “Use your existing email” and use the alias user+something@example.com

3. Now the user can use this google account to sign into 3rd party apps under the corporate domain. This is possible because many of these 3rd party apps only verify that the domain part of the email used when logging into the account is a known corporate account. (user+something@example.com ⇒ domain = example.com)

Was YeshID Affected?
No, users attempting to use this technique to log into YeshID would not be successful.
Recommendations
Detection
- If your organization has tools to perform an email search (such as the Security Center Investigation Tool in Google Workspace), look for emails sent to addresses containing your domain and a “+” symbol to detect these shadow account creations.
- Review the user lists in the applications your organization uses to look for accounts with email addresses containing a “+” symbol to detect users who may have exploited this vulnerability.
Prevention
- If your organization uses applications that allow any user to sign in as long as they are from your domain, consider disabling that feature. For example, in Slack: https://slack.com/help/articles/115004856503-Manage-how-people-join-your-workspace
- Switch the application to use SAML for SSO if possible
Regular auditing of your user environment is important and YeshID can help. Out-of-domain accounts are visible through our integration functionality. Try Onboard for free today.
IT Efficiency Through Playbooks

Startups build ad-hoc IAM systems, a tangled mess of spreadsheets, emails, and memory traces in the brains of the team members. As organizations grow, the tangles grow. Think about it:
- When a new hire joins, how easy is it to get them productive? How long does it take until they’ve been given access to everything they need?
- When it’s time for a compliance audit, do you need to sweat over spreadsheets, check multiple app interfaces, and comb through email chains, hoping you don't miss something?
- Is "Shadow IT" growing? When well-meaning employees start using convenient new apps, are they bypassing IT? Or does IT maintain visibility and control without bureaucracy?
- Is offboarding easy? When someone leaves, can you quickly cut access to all the apps they used while retaining access to the data they created?
Cheer up! Things will get worse.As your company grows and your tech stack gets more complex, whatever chaos you had will get worse. Why?
- You're juggling multiple playbooks. One spreadsheet for onboarding, a checklist for audits, a half-remembered process for software requests.
- Time becomes essential. Onboarding tasks, regular access reviews, or even handling forgotten password resets shouldn't rely on your memory.
- Your processes aren't static. New apps get adopted, rules change, one-off issues reveal cracks in your workflows. Updating your playbooks becomes a time-consuming chore.
- Your organization changes. New groups appear. Old groups merge. Consultants, temps, and suppliers need access
- Collaboration is a nightmare. Chasing down other teams to get tasks done, sending reminders, consolidating responses, and hoping they update the results in the right place… it turns your attempted efficiency into another massive time suck.
The YeshID Difference: One Playbook, Total ControlNow imagine this:
- Effortless orchestration: A new employee begins, and your centralized YeshID playbook spins into action. Accounts are created, exploiting the best available integrations. For anything without an integration, YeshID creates tasks with clear owners and deadlines. Task reminders? Automatically sent to the right department. You get progress reports, not a growing sense of dread.
- Compliance is no sweat: Audit looming? YeshID pulls who has access to what and current settings across every supported app, then surveys users and managers to verify who truly needs what access. Reports become accurate and stress-free.
- Offboarding without the panic: Employee departs, and your playbook cuts off access to integrated apps instantly. It also generates tasks with clear owners for everything else, ensuring no security holes slip through the cracks.
- A playbook that evolves with you: YeshID is your adaptable IT brain. It leverages your IAM, automates manual steps, sends timely reminders, and handles approvals across teams. Change a process? Update the playbook, and everyone instantly follows the latest version.
Sound too good to be true? Let YeshID be your partner in keeping your identity and access management realm simple, effective, and secure. Get YeshID Onboard for free and start today.
Navigating the OAuth maze in SMB identity management

Today's interconnected digital landscape, where applications seamlessly integrate to enhance productivity, is both a blessing and a curse. On the one hand, information is more accessible than ever, requiring switching between apps and services, ostensibly increasing productivity. On the other hand, the importance of robust identity management cannot be overstated, and if you’re not careful you can lose track of who, what, and where you’ve authorized permissions — and with companies under 2,000 employees averaging more than 73 SaaS app integrations in 2020, it’s clearly a growing problem. It's crucial to recognize the potential risks associated with OAuth (Open Authorization) grants and how they impact your organization's data security. In this blog post, we'll delve into the intricacies of OAuth and shed light on the vulnerabilities that may lurk beneath the surface.
Broad OAuth access can mean identity sprawl
Many applications today build on top of each other, using the data from one to power the other. A common example is Google. Google is not one thing; it’s Gmail, Drive, Calendar, etc. And for each of these services, Google has a fine-grained API that engineers can use (usually read-only or read-write) to integrate with their products. OAuth is the standard authorization technology across services and is part of what makes an “interconnected” internet experience possible. For example, YeshID Onboard leverages OAuth APIs from Google, Slack, Zoom, and other platforms to streamline identity management for your organization. However, the devil is in the details when it comes to OAuth scopes, which are the permissions granted to applications. An alarming aspect is the breadth of these scopes. Some vendors offer OAuth APIs in an all-or-nothing approach, which hampers the ability to employ least-privilege access principles. This contrasts with providers like Google Workspace, known for their granular scopes, allowing for more specific permissions like manipulating mailbox settings, accessing sensitive files, and even user impersonation. However, granularity does not inherently mean restraint; vendors may still request more permissions than necessary, increasing potential risks.Complicating matters, the risk of data exposure and account takeover is substantial if an OAuth-integrated application is compromised. This situation is akin to any custodian acting on our behalf; the extent of the compromise is proportional to the level of trust and access we’ve granted. So understanding the granularity and necessity of OAuth scopes is crucial in safeguarding your organization's sensitive information. It's imperative to assess not just what permissions are possible, but also what permissions are truly necessary for the task at hand
OAuth can introduce unintentional vulnerabilities
One of the major risks lies in users granting OAuth access without fully comprehending the implications, which can lead to unintended vulnerabilities. Consider the scenario of a vulnerability in a Single Sign-On (SSO) mechanism that allowed unauthorized access using Google credentials. Users, in their quest for convenience, might inadvertently expose sensitive company data by granting access without due diligence.The accidental use of work credentials in personal applications further exacerbates the problem. This unintentional mingling of professional and personal spheres can result in a breach of company data, underscoring the need for user education on OAuth access and permissions. Here’s an example of what you might wind up with.
Navigating OAuth security concerns
Enhancing the security of your accounts can be achieved by clearly understanding the difference between “session length” and “grant validity period.” In OAuth, permissions granted to applications often allow extended, but not indefinite, access to company data, raising potential security concerns. This issue becomes particularly critical when applications with extensive permissions retain this access for prolonged periods. To mitigate risks like unauthorized access, data exposure, and account takeover, it's essential for leaders to proactively manage and monitor these OAuth grants. Regular reviews and audits of the grant validity periods are key practices in ensuring these permissions are necessary and relevant, and in maintaining the overall security and integrity of your organization’s data. Here’s a look at the OAuth request lifecycle to illustrate the issue:

One way to do this is by using your Google Workspace console and navigating the following path: Security > Access and Data > API Controls > Manage third party app access > View list. There, you can view apps with access, revoke access if needed, and just get a general view of what’s going on in your app environment. Check out the video below, where I walk you through it.[embed]https://www.youtube.com/watch?v=lbjWs_NL1qs[/embed]On the other hand, you can also easily track this information with YeshID. Our intuitive dashboards present a comprehensive overview of app licenses, showcasing the interconnected web of permissions across different applications. This helps leaders easily identify which apps or services have broad access to sensitive data and understand the potential risks associated with each OAuth grant.As leaders in the SMB space, it's imperative to understand the intricacies of OAuth and its potential risks. By educating users, understanding OAuth scopes, and implementing security measures, SMBs can fortify their identity management practices, ensuring a robust defense against the evolving landscape of digital threats. YeshID is your partner in this effort, showcasing the identity sprawl within your organization and aiding in the vigilant management of OAuth access. Want to learn more about how we can keep your identity and access management realm simple, effective, and secure? Get YeshID Onboard for free and start today.
Release Notes for January 25, 2024

Howdy YeshID Community!New year, New updates to YeshID! We're coming in hot for the first release of 2024 with a lot of amazing updates that are, as always, designed to make managing your digital workspace easier, more intuitive and more efficient.Here's what we just dropped:
- 🗒️ Access Grid Enhancements:
- Sorting and Visibility Improvements: Integrated apps are now prioritized in the access grid, improving navigation and usability. Additionally, new hover and resize behaviors for the access grid’s shadow enhance user experience.
- Column Reordering: This feature enables users to rearrange columns in the access grid, allowing for a more customized and efficient workspace.
- ⚙️ Application Management and Integration:
- Application Deletion and Addition: The logic for deleting applications has been improved and moved for better accessibility. There’s also a new flow for adding applications requiring OAuth.
- Google Workspace Integration: Fixes and improvements in the integration with Google Workspace ensure more reliable and accurate synchronization.
- User and Admin Syncing: Enhancements in syncing admin roles and user identities, including syncing with Google, streamline user management.
- Manual Application Addition: Resolved issues related to adding non-integrated applications manually.
- ✨ User Interface and Usability Improvements:
- UI Enhancements: Various tweaks, like minimum bar width adjustments and added spacing in forms, improve the overall user interface.
- State Visibility: Improvements in showing the correct state in different modes, like preselected app mode, enhance user clarity.
- 🏗️ Organizational Structure Visualization:
- Org Tree Visualization: Fixes and enhancements in the organizational tree visualization, especially for empty organizations, improve clarity and user interaction.
- 🔐 Identity and Access Management:
- Account Mapping and Reporting: Better handling of identity mappings and integrated application reports, ensuring accurate tracking and reporting.
- Group Membership Bugs: Fixes in group membership management enhance reliability in user access control.
- New Status Indicators: Introduction of an invited status tooltip for better user status tracking.
- 📧 Email and Notification System:
- Email Template Updates: Changes in the email templates for different scenarios, like user onboarding and access requests, for clearer communication.
- Trigger Emails for User Changes: Automatic email notifications for user additions, deletions, or suspensions outside of YeshID.
- 🤝 Security and Compliance:
- Secret Property Handling: Enhanced security measures to prevent the return of secret properties in integrations.
- File Type Restrictions: Restricted certain uploads to PNG files only to bolster security.
- 📋 Task Management and Navigation:
- Task View Splitting: The tasks view has been split by completion status for better task management.
- Navigation Enhancements for Admins: Improved navigation options for admins, especially those who are new or in the process of being onboarded.
- 🕺 Miscellaneous:
- Year Update in Templates: Updated the year to 2024 in email templates.
- General Bug Fixes and Improvements: Various other fixes and improvements, including time display issues and testing adjustments.
3 identity and access management housekeeping tasks to start 2024

Ah, January! The month of fresh starts, new resolutions, and doubling down on our best behaviors. This is the perfect time for Google Workspace Super Admins to do a check to ensure they’re following best practices when it comes to identity and access management.Unsure where to start? Here are three things you can do today.
1. Audit all apps and limit scopes where needed
OAuth is a widely used protocol for granting access to resources. OAuth also represents one of the largest surface areas for data to be unknowingly leaked is through an unmanaged application through OAuth in Google Workspace. When a user grants an application access to their Google Workspace data through OAuth, they may not be fully aware of the scope of access they are giving to the application, and the application may have access to more data than the user intended. This issue becomes particularly critical when applications with extensive permissions retain this access for prolonged periods.To mitigate risks like unauthorized access, data exposure, and account takeover, it’s essential for leaders to proactively manage and monitor these OAuth grants. Regular reviews and audits of the grant validity periods are key practices in ensuring these permissions are necessary and relevant, and in maintaining the overall security and integrity of your organization’s data.One way to do this is by using your Google Workspace console and navigating the following path: Security > Access and Data > API Controls > Manage third party app access > View list. There, you can view apps with access, revoke access if needed, and just get a general view of what’s going on in your app environment. Check out the video below, where I walk you through it.[embed]https://youtu.be/lbjWs_NL1qs[/embed]On the other hand, you can also easily track this information with YeshID. Our intuitive dashboards present a comprehensive overview of app licenses, showcasing the interconnected web of permissions across different applications. This helps leaders easily identify which apps or services have broad access to sensitive data and understand the potential risks associated with each OAuth grant.
2. Review your authentication settings
Reviewing your authentication settings to ensure they align with internal policies is paramount. We recommend you use one of these two approaches:
The traditional 2FA and strong password approach
First, enforce strong passwords that contain a combination of uppercase and lowercase letters, numbers, and special characters, and are at least 12 characters long. Using a unique password for each account is important because if a hacker gains access to one password, they will not be able to use it to access your other accounts. You can do this through Google Workspace Admin console here. Second, turn on two-factor authentication (2FA) to add an extra layer of security to your online accounts by requiring a second form of verification in addition to your password (usually a code sent to your phone, a biometric scan, or a physical token). 2FA makes it much harder for someone to gain unauthorized access to your accounts: Even if they have your password, they also need to have access to your second form of authentication in order to log in. You can do this through Google Workspace Admin console here.
The more modern passwordless approach
A more secure (and easier to use) choice is to adopt the passwordless setting. It has several benefits:
- You stop using the vulnerable password
- You handle the two-factor requirement with a simpler user experience
Turn on Google’s passwordless beta or try YeshID’s simple passwordless approach.
3. Streamline your onboarding/offboarding process
If you’re still onboarding new users manually in Google Workspace the old way, it might be time to think about updating your process. Fortunately, that doesn’t have to mean putting weeks into procuring a tool or hiring an employee. By augmenting Workspace’s hard-to-navigate console with a user-friendly dashboard and enhanced controls, YeshID makes streamlining onboarding and offboarding a breeze. Scheduled workflows, flexible controls, and customizable templates help automate onboarding/offboarding and provisioning tasks, ensuring the right users have the right access at the right time.
- Schedule onboarding: YeshID allows you to schedule onboarding tasks. An email is automatically sent to the user on their start date, and their account is provisioned immediately to kickstart the application license process.
- Create templates for departments: Create templates for different departments to automate the assignment of groups and orgs, reducing manual work.
- Manage application provisioning: Manage the application provisioning process through YeshID’s task management system. Assign administrators for each application, and they’ll receive notifications for when to provision access.
- Compliance management: YeshID serves as a central source of truth for access management, making it easy to demonstrate compliance when needed.
It’s your year!
Let YeshID be your partner in keeping your identity and access management realm simple, effective, and secure. Get YeshID Onboard for free and start today.
YeshID Now Available on Google Workspace Marketplace

YeshID is the all-in-one identity management tool for growing organizations and the only identity and access management tool built specifically for Google Workspace. And now, we’re thrilled to announce that YeshID is now available on the Google Workspace Marketplace! 🎉
A milestone for YeshID
Why is this such a milestone for us? By integrating YeshID into the Google Workspaces ecosystem, we're bringing you a unified experience that seamlessly blends the power of identity management with the collaborative prowess of Google's suite of productivity tools. Having an app available for download on the Google Workspace Marketplace provides several benefits including increased visibility, easier access for users, and an additional layer of trust and security (= peace of mind for our users). Super admins can easily find and enroll in YeshID directly from the Marketplace, streamlining the deployment process and making it more convenient for them to access the app. (just press the easy button!)Every publicly available app in the Google Workspace Marketplace is reviewed by Google's Marketplace team, which adds a layer of trust and security for you. Also, we’re already SOC II compliant and you have a big ol’ DELETE button if you decide it’s not for you.
Benefits at a glance
Multi-factor authentication simplicity: Passkey-powered two-factor authentication means no more passwords, and puts access at your fingertips — literally.Streamline life cycle managerment: Templatize and schedule onboarding and offboarding tasks to set up a repeatable process for ease and speed. Onboarding new team members has never been smoother. YeshID automates user provisioning, ensuring that your team members have the right access from day one. No more tedious manual setup – just efficient and error-free user management.Effortless access management: Empower employees to initiate requests for new application access that are automatically routed to the proper application administrator.Security Visibility: Easily manage OAuth scopes to Google Workspace. Get a high level view that lets you navigate OAuth scopes with less complexity and easier oversight. Act confidently and quickly to revoke, block, or manage suspicious applications.
How to get started
Getting started with YeshID on Google Workspaces Marketplace is a breeze. Simply visit the Marketplace, locate YeshID, and click 'Install.' (note: you’ll need to have super admin privileges). The setup wizard will guide you through the process, and in no time, you'll be experiencing the benefits of seamless identity management in 5 minutes, no IT or security experience required — because futzing around in Google Workspace’s admin console isn’t what you had in mind when you started a company.
YeshID integrations: an easier way to manage app access for SMBs

Onboarding and offboarding employees includes managing which SaaS applications they need access to and which they need to be removed from. Many small- and medium-sized businesses (SMBs) do this with something lovingly (or not so lovingly) called The SpreadsheetTM.A new employee joins the company? Update The Spreadsheet. An employee left the company? Update The Spreadsheet. An employee changed their name? Update The Spreadsheet. Then, when the annual access review comes along, everyone asks: How accurate is The Spreadsheet? And as your company grows, the more employees you have, the more applications you use, the more digitally connected you are — the more complicated The Spreadsheet gets.The spreadsheet method had its day, but you can see how it might prevent SMBs from leveling up and even unintentionally add operational, technical, and security debt to take care of later. It is possible to automate granting and revoking access and permissions by using APIs for many applications. But there are some substantial barriers:It’s nobody’s job (yet). Small companies are often strapped, and maybe you don’t have a dedicated headcount that can own the process of updating employee application access.The app doesn’t have an API. With some applications, the only way to update permissions is in the app itself. The expensive SSO tax gets in the way. Using automation software like Okta, for example, forces you to implement technological protocols you just don’t need yet. It’s expensive and can be disruptive to users.
A better way to automate IT permissions
Because it’s so easy to implement, more modern application vendors have adopted “Sign in with Google,” and they don’t charge for it. This means that if you use Google Workspace, the need for SAML-based SSO (like Okta) is nearly obsolete. And get this — 70% of startups and SMBs already operate on Google Workspace to begin with!YeshID helps Google Super Admins create a streamlined, repeatable, efficient, and compliant way to manage identities and applications. Using templates, you can automate creating a Google user and putting them in the proper organization and groups. This also triggers the creation of a task list of apps they need access to and automatically sends requests for provisioning to the proper admins. And now, we’re testing an even easier way to do this: If the application offers the ability to read the list of users on lower subscription tiers, we’ll actually keep the list up to date for you. And soon, we’ll have the ability to add the user for you too (if that capability exists in lower subscription tiers). To start, we have integrations with Slack, Notion, and Hubspot. Once enabled, syncing users from those applications to YeshID can be done with a click of a button.
Give it a go
YeshID is in beta and looking for folks who sit in that sweet spot where you want to ditch The Spreadsheet but don’t want to go all in on Okta. If this is you, learn more! We’re already SOC II compliant, we’re in the Google Workspace Marketplace, and you have a big ol’ DELETE button if you decide it’s not for you.
New from YeshID: Data visualization for Google Workspace access

Last week, we talked about the risks that come with granting OAuth tokens without restraint across your organization and mentioned two ways to manage this process:
- You can periodically check your Google admin console to see what permissions are authorized and manually revoke access where needed.
- Or you can also easily track this information with YeshID.
Our intuitive dashboards present a comprehensive overview of access to your Google Workspace, showcasing the interconnected web of permissions granted to third-party applications. This helps leaders easily identify which apps or services have broad access to sensitive data and understand the potential risks associated with each OAuth grant. And today, we’re making it even easier to gather those insights and take immediate action with new data visualization capabilities in YeshID. Let's explore how data visualization can play a pivotal role in mitigating risks like data exposure and unintentional oversharing of permissions. We’ll introduce you to our new visualization tool along the way.
Our risk representation of OAuth scopes
Humans are really good at pattern recognition, and seeing things drawn or color-coded can help us quickly grasp a concept. In this case, we can use data visualization to provide a granular representation of OAuth scopes (the permissions granted to applications), breaking them down into easily digestible components and allowing you to pinpoint areas of high risk. This clarity enables informed decision-making when it comes to understanding exposure from connected applications and adjusting permissions to align with organizational security policies. YeshID’s data visualization breaks OAuth scopes into a digestible color-coded graph so you can easily pinpoint areas of risk. We use Google’s sensitive/restricted scope classification system to categorize granted scopes on a green, yellow, red basis. Find an anomaly? We also make it easy to revoke or block access.
Not just a pretty picture
Once you have an idea of what looks suspicious, YeshID makes it easy to act with options to revoke, block, or manage applications.
- Revoking a third-party application’s access essentially invalidates the access that your users have granted to an application. However, this is temporary and your user could grant permissions again. We allow you to mark it as ‘Forbidden,’ and we will highlight it if access has been regranted.
- Blocking an OAuth token goes a step further by preventing the associated application from requesting access to the user's Google Workspace data altogether — a cumbersome process when done through the Admin Console.
Here it is in action.[embed]https://youtu.be/oqzbDfTrObg[/embed]
Try YeshID now
Data visualization within YeshID transforms the complexity of app access management into a visual narrative that’s easier to grasp at a glance. By harnessing the power of visualizations, you can navigate the challenges of OAuth tokens, enhance security measures, and foster a culture of awareness and responsibility among users. Learn more.
Release notes for November 28, 2023

Enhanced Mobile Experience and Onboarding
- Mobile UI Improvement for Signup
- We've improved the mobile interface for a smoother signup experience. Now, our signup page is fully optimized for mobile devices, ensuring easy access and navigation.
Task Management and Email Notifications
- Improved Task Interactions and New Task States
- Enhancements in task interactions, including the addition of "Completed" and "Cancelled" status options, allow for more precise task management and tracking.
- Automated Task Email Setup
- To streamline your workflow, task-related emails are now automatically set up when a new user registers and disabled upon account deletion.
Event Scheduling and Management Enhancements
- Scheduled Events Fix
- We've introduced a feature for scheduling events to be published at a later date, along with fixes for updating user enrollment states in sync with scheduled event emails.
Google Integration and System Notifications
- Google Sync Failure Notification
- A new system banner will alert you if the daily Google import fails, providing hints to resolve the issue quickly and efficiently.
Usability Improvements
- External Links in Markdown Now Open in New Tab
- To enhance user experience and prevent loss of progress in our app, external links in markdown now open in a new tab.
A new era of secure IT identity management: YeshID, SOC II, and you

YeshID is now SOC II compliant! 🎉 Not sure why this is important? In an increasingly digital world, safeguarding sensitive information, especially during employee IT onboarding and offboarding, is of critical importance. SOC II compliance represents a major commitment to data security and privacy. We want to share this news with you for two reasons:
- To help deepen your trust in YeshID as your tool of choice for secure onboarding and offboarding.
- You might want to achieve SOC II compliance for your growing company one day too! We’re hoping our journey can help you with yours.
In this blog post, we'll explore what SOC II compliance means, its significance for YeshID, and how it benefits your organization.
What is SOC II compliance?
SOC II, or Service Organization Control 2, is a rigorous auditing process that evaluates a company’s controls relevant to security, availability, processing integrity, confidentiality, and privacy of customer data. Achieving SOC II compliance demonstrates that YeshID has undergone thorough assessments and meets high industry standards in data security.

SOC II compliance is usually conducted by a third-party assessor that measures the following:
- Security: Assesses measures in place to protect the organization's systems, data centers, networks, access controls, and more from unauthorized access, physical and otherwise
- Availability: Examines downtime, disaster recovery, and business continuity planning to assess the reliability of systems and services as agreed upon with customers
- Processing integrity: Evaluates if data is processed accurately, completely, and in a timely manner
- Confidentiality: Assesses access controls, encryption, and data privacy measures to focus on the protection of sensitive data from unauthorized access or disclosure
- Privacy: Assesses the management of personal information and its compliance with relevant data privacy regulations
There are companies that help you achieve SOC II compliance. For example, YeshID worked with Vanta to help automate the SOC II process and find a vetted third-party auditor.
Why does SOC II compliance matter?
SOC II compliance ensures that any company undergoing the process has implemented robust security measures to protect sensitive information. This is particularly essential for YeshID because during employee onboarding and offboarding, personal and confidential data is frequently exchanged. Achieving SOC II compliance shows our strong commitment to data security and privacy.SOC II compliance helps reduce potential risks and vulnerabilities in your data management processes. It safeguards your organization against data breaches and regulatory fines. It also sends a signal to your customers, investors, partners, and stakeholders that data privacy and access management is a top priority for your company.
SOC II-compliant IT onboarding and offboarding with YeshID
SOC II compliance is a milestone that strengthens our commitment to data security and privacy. By choosing YeshID, you can trust that your sensitive information is in safe hands during employee onboarding and offboarding processes and that you are complying with the highest data protection standards. This means that you are that much closer to achieving SOC II compliance by using a SOC II-compliant onboarding and offboarding provider.In an age where data breaches and privacy concerns are ever-present, SOC II compliance is your assurance that YeshID is dedicated to maintaining the utmost standards of data security. Let us help you unlock a new era of security and efficiency in your organization's processes.
A Non-Technical Guide: How to Streamline Employee Onboarding in Google Workspace

Although it can seem overwhelming — especially for those of us at small companies where identity and access management is just one of the many hats we wear — employee onboarding in Google Workspace can be a breeze, even if you're not a tech guru. The key is knowing where to start.In this guide, we’ll walk you through the step-by-step process of setting up new employee accounts, configuring email, and granting access to essential apps within Google Workspace. We'll also cover common challenges and provide tips for simplifying the process, including how to leverage tools like YeshID to make things even smoother.
Step 1: Set Up a New Employee Account
The first step in onboarding a new employee is to set up a new employee account in Google Workspace. It’s worth noting here that we are assuming you have Google Super Admin access, which is a prerequisite for completing the tasks below.

It's a good idea to do this a couple of days before the employee's start date to ensure that other applications can be provisioned smoothly. Here are some things to keep in mind:
- Email address: By creating a Google Workspace account, you're giving the employee an identity within your company, which is centered around their email address.
- Password management: You'll need to create a password for them, which you should send them and save so they can access their account on the first day.
- Security: To enhance security, force the new employee to change their password upon the first login and strongly consider enabling two-factor authentication (2FA). This will grant them access to Google systems like Calendar, Mail, and more.
Step 2: Grant Access to Google Groups and Organizations
Next, ensure that the new employee has access to the right email groups and is placed in the appropriate organizational units, or orgs, within Google Workspace. While this process may be manual, you can often use the profile of another user with a similar role as a reference to determine which groups and orgs to assign.

Step 3: Provide Access to Birthright Apps
Birthright apps are the applications that every employee should have access to, such as Slack, documentation systems (e.g., Notion or Confluence), and HR applications. To grant access to these apps:
- Go into each application and provide access to the new email address you created for the employee.
- Sometimes, you may need to coordinate with other departments to ensure access is granted appropriately.
Step 4: Track Access and Compliance
Whether you handle app provisioning yourself or someone else does it, it's crucial to keep track of the apps you've granted access to for three key reasons:
- Offboarding: When an employee leaves the company, you can easily revoke their access to applications.
- Cost control: Tracking app access helps you manage licenses efficiently, saving your company money.
- Compliance: Compliance requirements often demand proof of access, so having a record is essential.
Many companies without a full HR or IT department might track this information in a spreadsheet or company wiki that needs to be manually updated and kept private. It’s a lot to manage, but by implementing these best practices today, you set yourself up for success tomorrow.
Simplify Onboarding with YeshID
There are options that don’t involve doing all of this manually: GAM, Bettercloud, Okta, and Ping are a few. The problem though is that for most small businesses, these products are overkill. They are expensive and time-consuming to implement — especially when what you really need is just to get people to work using solid best practices, not advanced technology. YeshID Onboard provides an option for smaller companies that have embarked on their identity and access management journeys but aren’t in a place yet where they need a very technical (or expensive) solution. We provide a quick and easy way to streamline onboarding today while setting up the foundational best practices we outlined in this guide. Benefits include:
- Schedule onboarding: YeshID allows you to schedule onboarding tasks. An email is automatically sent to the user on their start date, and their account is provisioned immediately to kickstart the application license process.
- Create templates for departments: Create templates for different departments to automate the assignment of groups and orgs, reducing manual work.
- Implement passwordless security: Enhance security by utilizing YeshID's passwordless authentication method.
- Manage application provisioning: Manage the application provisioning process through YeshID's task management system. Assign administrators for each application, and they'll receive notifications for when to provision access.
- Compliance management: YeshID serves as a central source of truth for access management, making it easy to demonstrate compliance when needed.
Streamlining employee onboarding in Google Workspace doesn't have to be a daunting task. With the right approach and tools like YeshID Onboard, you can efficiently manage the process and ensure that new employees have the access they need from day one.Try Onboard. The first 100 people to join will get access to better onboarding and offboarding for free today and early access to future product updates.
Stepping Lightly: A Guide to Avoiding Onboarding and Offboarding Missteps

Onboarding and offboarding employees to your IT systems is like an intricate dance
It can either be a graceful waltz or an out-of-sync electric slide. In this post, we’ll talk about four potential trip-ups when thinking about employee access management. We’ll also show you practical steps you can take today to streamline onboarding and offboarding. Let’s take it for a spin!
Using a tool that’s too big (or too small)
The misstep
Imagine trying to dance the tango in tap shoes or attempting a waltz in hiking boots. Similarly, using tools that are either too complex or too basic can throw off the entire rhythm of your onboarding and offboarding dance.
With advanced providers like Okta, for example, you have to configure SAML, SCIM, and JIT to authenticate and manage users. This is known as the SSO tax and can mean a lot of work on technology that you might not really need yet. On the other hand, people who try to manage the process with Jira tickets or Notion/Docs, often forget to track and update things.
The right step
Find a tool that's your perfect dance partner — one that adapts to your rhythm by helping you accomplish what you need to get done today and grows with you. Instead of taking an over-comprehensive approach to SSO that may overwhelm customers and inflate costs, focus on the tasks you face today — the stuff you just need to work and to be secure. And with the right tool, you can actually set yourself up for success by creating good processes from the beginning, which will help you scale as your business expands.
YeshID Onboard provides an option for smaller companies that have embarked on their identity and access management journeys but aren’t in a place yet where they need a very technical (or expensive) solution. It’s also free for now (find out why).
Trying to do it all yourself
The misstep
Picture a solo dancer trying to cover the entire stage – it might look impressive, but the risk of exhaustion and missteps is high. If you’re the Google Admin for your small startup or company, odds are you’re an overachiever, but stretching yourself too thin can have negative effects on your work and your health.
The right step
Enter your dance ensemble – your application administrators. Delegating tasks during the onboarding and offboarding performance lightens the load and ensures a smoother routine. With Onboard, you can assign an admin to each app your company uses, then automatically route requests for provisioning to the proper admins. We also help you empower employees to initiate requests for new application access, which can also be routed to the proper application administrator.
In this way, automation becomes your dance partner, stepping in to handle repetitive tasks while you take center stage. Things like customizable templates, task assignments, and email notification not only help you save time but also minimize the chances of errors.
Putting off best practices until “later”
The misstep
Delaying the incorporation of best practices is akin to attempting a complicated dance routine without rehearsal – it leads to chaos and missteps. Maybe it’s too expensive to manage right now — time or budget wise — but what you end up with is a messy company footprint and opening yourself to security risks.
Onboarding and offboarding tools have overlooked the middle of the market. There are plenty of smaller businesses that want to easily manage their processes now while setting up good practices for tomorrow.
The right step
We created YeshID Onboard because we saw that gap. Specifically for 50-250 people, Onboard provides an option for smaller companies that have embarked on their identity and access management journeys but aren’t in a place yet where they need a very technical (or expensive) solution. We provide a quick and easy way to accomplish your checklist today while setting up the foundational best practices that will help you grow in the future.
Only focusing on onboarding, not offboarding
The misstep
Different industries have specific compliance and regulatory requirements that must be met during onboarding and offboarding. Handling third-party data can be scary and requires robust security measures. And focusing solely on onboarding is like nailing the first half of a dance and forgetting the finale. Onboarding is about efficiency, but offboarding is both a security and compliance requirement.
The right step
Your onboarding solution should comply with data protection regulations and keep your data safe. Ideally, you should be able to track provisioning/deprovisioning in a single dashboard to offboard a user with confidence while maintaining compliance and reducing license costs. This is another area where your Product Administrators can play back-up dancers, ensuring a seamless transition.
Let’s dance
In the dance of onboarding and offboarding, perfecting each step is essential for a harmonious performance. Choose tools that dance to your rhythm, build a team of Product Administrators as your dance ensemble, kick off best practices from the first note, and never forget the importance of the grand finale – offboarding. YeshID Onboard is your dance instructor for small to medium-sized businesses, offering a strategic approach to identity and access management. Users also get access to an exclusive Slack community of small business hustlers and heroes just like you so we can share, support, and celebrate together. Sign up today.
YeshID Product Update November 12, 2023

YeshID Product Update November 12, 2023
Hello YeshID Community!
I’m thrilled to announce the latest updates to YeshID, all designed to make managing your digital workspace easier, more intuitive, and more efficient. Here’s what’s new:
Enhanced Application Management
- Introducing AUID: We’ve added a new ‘Application Unique Identifier’ (AUID) for each application. This simplifies identifying applications across environments… More about that in the coming weeks
- Database Migration Improved: To ensure smoother operations, we’ve fixed issues with duplicate applications in our database migration process. Your data’s integrity and consistency are always our top priority.
User Interface Improvements
- Role Renaming: We’ve renamed ‘superadmins’ to ‘admins’. This change is part of our commitment to simplicity and clarity in role definitions.
- Streamlined UI: We’ve removed unused elements like the old landing page, focusing on a cleaner, more efficient user interface.
Email Notifications and Task Management
- Email Scheduling Perfected: We’ve fixed issues with the daily and weekly task emails. Now, they’ll arrive precisely when you need them - at Monday UTC midnight for weekly and UTC midnight for daily updates.
- Task Reminder Emails: Stay on top of your admin tasks with our new daily reminder emails. Opt in or out as you prefer - we’re all about giving you control.
- Weekly Admin Updates: Our new weekly admin emails will keep you informed and help you stay ahead of the curve.
User Experience and Access Control
- Smooth Login Experience: We’ve resolved the issue where admin users were redirected to the onboarding page and getting stuck. Your seamless access is crucial to us.
This update is a reflection of our commitment to constantly evolve and improve. We believe these enhancements will make your YeshID experience even more rewarding. As always, we’re eager to hear your feedback.
Thank you for being a part of our journey!
What to look for in an employee onboarding tool for small businesses

Small businesses face special challenges in managing their employee onboarding and offboarding processes with limited resources. Without a fully staffed IT or HR department, there’s often just one person covering “operations” for the whole organization. And in some companies, someone with a totally unrelated job ends up running these functions.We’re like that, actually. As a startup, YeshID has a small staff. In addition to my founder duties, I’m the one to handle IT employee onboarding and offboarding for our team. And that’s the way we want it for now — we’re keeping overhead low so we can concentrate on building the best product. But that doesn’t mean we want to skimp on laying a good foundation for tomorrow.In a situation like this, efficiency and simplicity are so important. It’s not just about providing an email address for new employees. You have to add them to the correct organizations and groups in your Google Workspace; keep track of who has permissions for what applications; track the number and cost of app and software licenses, keep up with which teams own which services, and the list goes on. Technology can help you streamline, templatize, and automate your user onboarding and offboarding procedures. In this post, I’ll talk about what to look for in a tool.
User-friendly IT onboarding and offboarding
The first thing you should consider when evaluating an onboarding solution is its user-friendliness. You need a tool that is easy for both administrators (aka you) and users to navigate. The last thing you want on your already overloaded calendar is extensive training for a complicated system. Look for a solution with an intuitive interface and a straightforward setup process.One of the most significant advantages of a user-friendly onboarding solution is its ability to templatize and automate repetitive tasks. Look for a solution that offers customizable templates, task assignments, and email notifications. This not only saves time but also minimizes the chances of errors. You’ll also want to make sure the tool lets your employees request access to the apps they need — and that access is routed to the appropriate approver.
A secure and compliant employee onboarding and offboarding tool
Handling third-party data can be scary and requires robust security measures. Your onboarding solution should comply with data protection regulations and keep your data safe. Look for features like passwordless encryption and access controls to protect sensitive information. Different industries have specific compliance and regulatory requirements that must be met during onboarding and offboarding. Ensure that the onboarding solution aligns with these requirements. Ideally, you should be able to track provisioning/deprovisioning in a single dashboard to offboard a user with confidence while maintaining compliance and reducing license costs.
New employee onboarding and offboarding that grows with you
Your business may be small today, but tomorrow’s looking bright! Consider whether the onboarding solution can grow with you. It should be able to accommodate a growing number of users without significant disruptions. Scalability ensures that you won't outgrow your onboarding tool as your business expands. And with the right tools, you can actually set yourself up for success by creating good processes from the beginning. Beware the SSO tax on this one though. Some access management solutions require you to advance your engineering practices far beyond what most small- to medium-sized businesses need. Don’t settle for a solution that requires you to jump over unnecessary hurdles.
Cost-effective IT onboarding solutions
Until someone invents the money tree, it's essential to consider the overall cost of the tool in relation to the value it provides. This includes licensing fees, implementation costs, and ongoing maintenance. Make sure you're getting the features and support you need without breaking your budget. A cost-effective solution should offer a good balance between functionality and affordability.The flip side of this one is to make sure you’re not signing up for a solution that you’ll have to grow into fast. Many of the options in this space are overkill. They are expensive and time-consuming to implement — especially when what you really need is just to get people to work using solid best practices, not advanced technology.
The best onboarding and offboarding for small businesses
Identity and access management in the 21st century means digital onboarding, provisioning of the hundred-and-one software apps your org uses, plus traditional hardware setup. It’s become complex (and often frustrating) for both managers and employees. Finding the right onboarding solution for your small business can significantly improve the efficiency and effectiveness of your onboarding and offboarding processes.YeshID Onboard provides an option for smaller companies that have embarked on their identity and access management journeys but aren’t in a place yet where they need a very technical (or expensive) solution. We provide a quick and easy way to accomplish your checklist today while setting up the foundational best practices that will help you grow in the future.
- Templatize and schedule onboarding and offboarding tasks to set up a repeatable process for ease and speed.
- Assign application administrator(s) then automatically route requests for provisioning to the proper owners.
- Track provisioning/de-provisioning in a single dashboard to offboard a user with confidence while maintaining compliance and reducing license costs.
- Empower employees to initiate requests for new application access that are automatically routed to the proper application administrator.
- And because it’s in beta, YeshID Onboard is free (yes, like free free) for the first 100 companies to sign up (must be in Google Workspace and have 50-250 employees).
Start streamlining your onboarding and offboarding processes without the need for budget approval or credit card information. You’ll also get access to an exclusive Slack community of small business hustlers and heroes just like you so we can share, support, and celebrate together. Take something off your never-ending to-do list and sign up today.
A Non-Technical Guide: How to Streamline Employee Onboarding in YeshID

Last week, we published a blog post called "A Non-Technical Guide to Streamlining Employee Onboarding in Google Workspace." In that post, we walked you through the step-by-step process of setting up new employee accounts, configuring email, and granting access to essential apps within Google Workspace.
This week, I'll share tips for simplifying the onboarding process using YeshID Onboard. YeshID Onboard is a free tool that helps you efficiently manage employee onboarding and ensures that new employees have the access they need from day one.
Why are we giving YeshID Onboard away for free?

Earlier this month, we announced that our onboarding tool YeshID Onboard is now in beta and that we’re providing it free to the first 100 organizations of 25-250 employees working in Google Workspace to sign up. We’ve onboarded more than 20 companies since we put that message out, and we’re thrilled with the success those teams are experiencing with Onboard. But we’ve also noticed there are some questions around why we would give YeshID Onboard away for free, and that’s what I want to talk about today.
Ship, learn, improve
YeshID is a startup. Alex and I founded the company, and now we’re a small team with experience from tech heavy hitters like Meta, Microsoft, OpenDNS/Cisco, and RSA. We’re what you call a seed stage startup: we’re in the initial phase of developing our product and are focused on turning an innovative idea into a viable business. Seed startups are known for their potential to bring disruptive solutions to the market. They often challenge the status quo and aim to break into existing industries with new and creative approaches — and that’s just what we’re doing. We’re developing a tool that will disrupt the identity and access management world for smaller companies, which right now spans too big (like Okta) or too minimal (like spreadsheets). That means that we’re doing a lot of research, a lot of testing and iterating, and a lot of proving out concepts — and here’s the thing: we can’t do any of that without you. So, we’re giving our product away. Simple as that. Will that always be the case? Hopefully not! We are starting a business after all, but rest assured that if you join on a free plan, your plan will stay free, even if we start charging new customers for it.
Join us
Onboarding and offboarding are so fundamental to companies of all kinds, yet solutions have either lagged behind business needs or leap-frogged over a whole market size. This feels like the perfect entry point for YeshID and for companies looking to take the next step in their identity and access management journey. Onboard is purpose-built for small businesses using Google Workspace. We help you knock out the operational tasks that need to get done today while laying a solid foundation for tomorrow.
- Save time onboarding and offboarding team members with consolidated user controls
- Manage application requests and keep track of IT licenses and costs all in one place
- Skip the login screen and move effortlessly between approved applications
Plus, after you sign up, you’ll also get access to an exclusive Slack community of small business hustlers and heroes just like you so we can share, support, and celebrate together. And you’ll be helping us learn even more about the small business needs that have been overlooked until now. Head to our website to learn more.
Right-sized onboarding and offboarding free for the first 100 signups

This summer, we kicked off the beta program for YeshID, the all-in-one identity management tool for growing organizations. We invited participants to help us build the future of identity, access, and application management for small- and medium-sized businesses. But there was a catch — you had to talk with us. We realized this was a bump in the process and potentially scary because you might think we were going to sell something to you.We’ve onboarded more than 20 companies to the beta, ranging from faith-based nonprofits to financial technology companies. The only stipulation to join is that they run on Google Workspace and have fewer than 250 employees. Our beta members do vastly different things and are different sizes, but we’ve discovered that they all have three things in common:
- The people who are running Google Workspace access to the apps their companies use are strapped, and this isn’t their only responsibility. We’ve found they’re split into two camps. There’s the one-person IT team that’s bogged down with a million and one tasks. Or there’s someone (like me at my company!) who just got saddled with the task because someone has to do it.
- The biggest obstacle these folks currently face is onboarding/offboarding. Solutions are either too rudimentary, like tracking data in a spreadsheet, or too advanced, like biting off more than you need with Okta. There’s no good middle ground, and these IT teams of one, or Unexpected Google Admins, as we like to call them, are left to figure it all out on their own.
- Everyone we’ve talked to so far has said they need the same things out of their onboarding and offboarding tool: They need to be able to get people to work ASAP, they need a smart process default for setting up access, and they need it to be available at a low cost or for free.
With the needs around onboarding and offboarding being so great (and purse strings being so tight), we’ve decided to offer Onboard, our beta onboarding and offboarding functionality, for free to the first 100 customers who join the beta. And now you don’t even need to talk to us. You can simply sign up and get immediate access.
The Goldilocks of onboarding and offboarding
Running a startup ourselves, we understand the need to get employees started yesterday because the team is lean and we need those hands. We want to save ourselves time and money, too, because those are two things any business leader is short on. It’s true that there are other options in this space: GAM, Bettercloud, Okta, and Ping, to name a few. The problem though is that for most small businesses, these products are overkill. They are expensive and time-consuming to implement — especially when what you really need is just to get people to work using solid best practices, not advanced technology. YeshID Onboard provides an option for smaller companies that have embarked on their identity and access management journeys but aren’t in a place yet where they need a very technical (or expensive) solution. We provide a quick and easy way to accomplish your checklist today while setting up the foundational best practices that will help you grow in the future.Especially when it comes to “birthright apps,” or those that are automatically granted to every new employee (think: Slack, Zoom, etc.), YeshID helps you save tons of time.
- Templatize and schedule onboarding and offboarding tasks to set up a repeatable process for ease and speed.
- Assign application administrator(s) then automatically route requests for provisioning to the proper owners.
- Track provisioning/de-provisioning in a single dashboard to offboard a user with confidence while maintaining compliance and reducing license costs.
- Empower employees to initiate requests for new application access that are automatically routed to the proper application administrator.
Let’s grow together
Onboarding and offboarding are so fundamental to companies of all kinds, yet solutions have either lagged behind business needs or leap-frogged over a whole market size. This feels like the perfect entry point for YeshID and for companies looking to take the next step in their identity and access management journey. So get Onboard! The first 100 people to join will get access to better onboarding and offboarding for free today and early access to future product updates. And you’ll be helping us learn even more about the small business needs that have been overlooked until now.
Tips for building effective IAM processes at your startup

Processes are important for any organization, but they're especially important for startups. Smaller companies don't have the luxury of having a lot of people to handle different tasks. Everyone wears multiple hats, and that means that processes need to be in place to ensure that things get done correctly and efficiently — especially when you’re talking about securing access to your accounts, customer data, and workspace privileges. But how do you set up secure but flexible employee lifecycle processes when you're just starting out (and you don’t have a head of IT or HR yet, and you have four other jobs to do, and you still want to have a life)? The key is to start lightweight. Don't try to create a complex system right away. Instead, focus on the most important processes and build them out over time.In this blog post, I’ll give you some tips for implementing and managing identity and access management (IAM) processes at your organization — and let you in on how we make the most of our own limited startup founder time.
Tips for managing IAM processes at your startup
Creating and maintaining any process requires effort. A process should act like a microculture: aligning everyone involved without getting in their way. It can be tricky to strike a balance. YeshID helps small- and medium-sized businesses automate processes, reduce risk, and improve compliance around identity management and account access. And we’re also a small business ourselves. Our mentality around process at this point in our growth story is to focus on effective processes from the outset — but keep them to a minimum. After all, effective process management provides a smoother experience, but it shouldn’t get in the way of building and growing our product or business. Here are a few things we’ve learned along the way.
Be basic
What are the essential tasks that need to be done in your business? Once you know what those are, you can start to develop processes for them. For example, you might need to create processes for onboarding new employees, granting access to systems and data, and deprovisioning employees when they leave the company. The next time you onboard a new employee, keep track of everything you do as a way to get a list of needed processes started. Then build them out from there.
Be informative
Document your processes and make them available to all your employees. This will help ensure that everyone is using the same processes and that there is no confusion about who has access to what.Another way to ensure your processes are understood is to make them easy to follow. Use clear and concise language, and avoid jargon.
Be open
Things will change as your business grows, so your processes need to be flexible enough to adapt. Once you have some processes in place, get feedback from your team and make changes as needed. This will help you ensure that your processes are effective and efficient.At YeshID, we continuously identify and improve processes that don't serve us well by using feedback cycles. Our strongest processes have short feedback cycles, like unit tests in code that quickly signal any issues. On the other hand, the processes tested less often, like planning an off-site, tend to be less efficient.
Be protective of your time
Finally, as promised: the most meaningful move we’ve made as startup founders is to lay claim over our time. To take one thing off the endless founder to-do list, we tap into experts whenever possible. We know that we can’t do it all ourselves. For example, we have a finance advisor, Shane; and we use an Employee of Record (EOR) to hire people globally. These ready-made processes save us time and what could be costly mistakes.And at this point in the vast technical landscape, why bother building and maintaining any functionality outside of your core business goals? There are a lot of people, tools, and software available that can help you create repeatable processes and execute them to save your time and to help avoid errors.
Who’s building your IAM processes?
We built YeshID to meet the need to manage the growing complexity of your employees’ digital footprint. Identity and access management in the 21st century means digital onboarding, provisioning of the hundred-and-one software apps your org uses, plus traditional hardware setup. It’s become complex (and often frustrating) for both managers and employees.Hopefully, these tips will help in your own process creation. Alternatively, you could use a ready-to-implement solution like YeshID that suits your current needs, offering comprehensive management of onboarding, offboarding, apps, costs, and access, and empowers employees to manage their digital footprint easily.Take something off your never-ending to-do list. Make managing identity and access management easier for your small company with YeshID. Get access to beta now.
The history of SSO and why it’s time for a change

In a world where “Sign in with Google” rules, it feels almost unbelievable that we used to have to remember usernames and passwords for every account or application we touched online. That reality was even more cumbersome for HR and IT administrators, who had to keep a whole company’s worth of usernames, license numbers, passwords, and the like up to date.
The introduction of SSO changed all of that. But times have changed again, and beneath the promise of seamless identity and access management lies a complicated reality many startups and small businesses aren’t ready for.
In this blog post, I’ll talk you through how SSO has changed over the years to now encompass much more than many businesses need and why it’s time for an alternative.
SSO historically: a lifesaver
The value of SSO is undeniable and it was met with open arms: Employers could reduce help desk requests about forgotten passwords, saving everyone time. SSO created a strong access point that reduced vulnerabilities by consolidating login credentials and improving overall security. Password fatigue became a thing of the past, ostensibly boosting productivity.
Various SSO providers, like Okta, used a bookmark-like system to locally save passwords for easier logins. This approach, while user-friendly, had terrible inherent security risks. Over time, as technology evolved, application vendors started configuring SSO instances using Security Assertion Markup Language (SAML), an XML-based standard for exchanging authentication and authorization information between different systems. You can think of SAML as basically an additional layer of authentication on top of SSO.
Then Google Workspace and OAuth came along and changed all of that. OAuth, short for Open Authorization, is a standard for access delegation adopted by companies like Google, Amazon, Facebook — anywhere you can “Sign in with ___.” For example, when you use “Sign in with Google,” you are giving Google permission to handle credentials for you without you needing to enter additional credentials or passwords.
SSO today: more than you need
Because it’s so easy to implement, more modern application vendors have adopted “Sign in with Google,” and they don’t charge for it. This has made the need for SAML-based SSO nearly obsolete — especially for startups and SMBs, 70% of which operate on Google Workspace to begin with.
So IAM providers have bucketed functionality like provisioning/deprovisioning and lifecycle workflow into the SSO definition. There’s SAML support, but then you also need Life Cycle Management, API Access Management, Workflows, etc. And the more features, the higher the price tag.
The problem is that these protocols are often intertwined, forcing you to configure SAML, SCIM, and JIT to authenticate and manage users That’s fine for enterprise-level operations where there are resources to implement and manage all of this (and maybe other reasons for using those standards) but when it comes to startups and SMBs, it’s simply overkill. One of the issues is that IAM providers currently focus on providing a blanket of capability across everything you could do, instead of focusing on everything you need to do now. And, of course, you have to build it all yourself.
It’s time for a new approach to SSO: There has to be an option that sits between either tracking permissions and credentials in a spreadsheet or going all in with an expensive enterprise-level solution.
SSO tomorrow: a task-centric approach
YeshID is a new identity and access management tool built specifically for startups and SMBs working in Google Workspace. Instead of taking an over-comprehensive approach to SSO that may overwhelm customers and inflate costs, we focus on the real tasks that startups and SMBs face today — the stuff you just need to work and to be secure.
We believe in starting with the task in mind and tailoring solutions to meet those specific needs while using foundational best practices that pave the way for scalable and secure operations management as you grow.
- A single dashboard allows you to monitor access requests and IT licenses, and the management of onboard and offboard tasks across all your apps.
- Access levels you can configure by department or function make onboarding and offboarding a breeze.
- Passkeys, based on FIDO standards, offer a secure and streamlined sign-in alternative to passwords. They're phishing-resistant, simplify account registration, and are compatible across multiple devices, including those in close proximity.
- Transparent pricing means no hidden costs or surprise upsells.
We provide smart defaults that ensure you don’t have to start from scratch or spend valuable resources on re-engineering the digital identity processes. This not only saves time but also ensures companies adopt best practices early, without having to be experts in digital identity.
SSO and you: join us
The SSO landscape isn’t keeping up with the needs of startups and SMBs today. It's time to move away from complex and costly solutions and embrace simplicity and efficiency. If this vision of streamlined, low-overhead identity and access management, we invite you to join our Beta. You get early access to YeshID and your experience will help us shape the future of SSO for small businesses. Get more info, and join us today.
It’s time to meet YeshID: beta now open for early adopters

We’re guessing futzing around in Google Workspace’s admin console isn’t what you had in mind when you started a company. But like so many of the jobs done by the heroes and hustlers who lead small companies and growing startups, it has to get done and you’re the one to do it.Well, we want to help. YeshID empowers companies of 11 to 250 employees to be more safe, compliant, and efficient in 5 minutes with the only identity and access management tool built specifically for Google Workspace. And today, we’re ready to pull back the curtain and show you what we’ve been working on.
YeshID early beta is here (and free)
We invite you to be among the first people in the world to try YeshID as part of our early beta program. You get free lifecycle management, financial license oversight, and unphishable authentication, and we get the opportunity to learn from your feedback and experience. It’s a win-win. As a member of the early beta program, you’ll discover how YeshID helps you:
- Enforce multi-factor authentication (MFA) for all users and devices
- Monitor access requests and IT licenses, and onboard and offboard employees across all your apps from one dashboard
- Skip the login screen and move effortlessly between approved applications with unphishable authentication
In return, you’ll lend your expertise as an overworked small company admin to inform our folks in product, design, and engineering. Our goal is to build something that solves your problems, so we’ll want to talk to you plenty.
Join us
Want to hear more? Let us know and we’ll reach out. We’re excited to have you join us on the frontlines of making identity and access management simple for small companies.
YeshID Labs - Free tools for IT and Security teams.
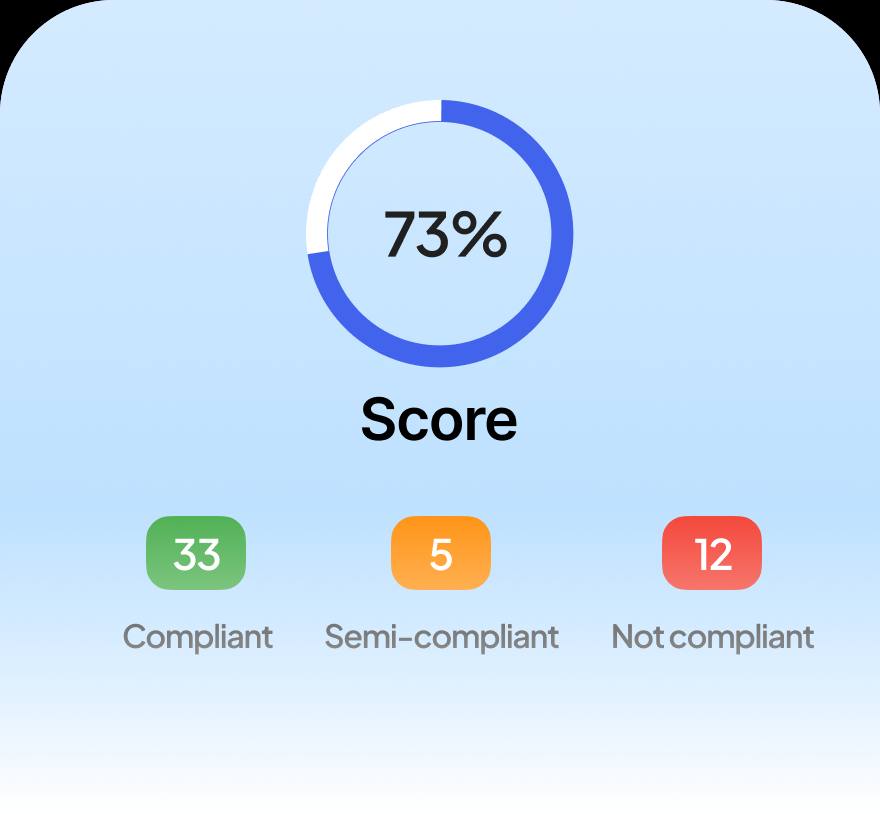
Policy Checker
Free tool to analyze and assess your Google Workspace policies for security best practices.
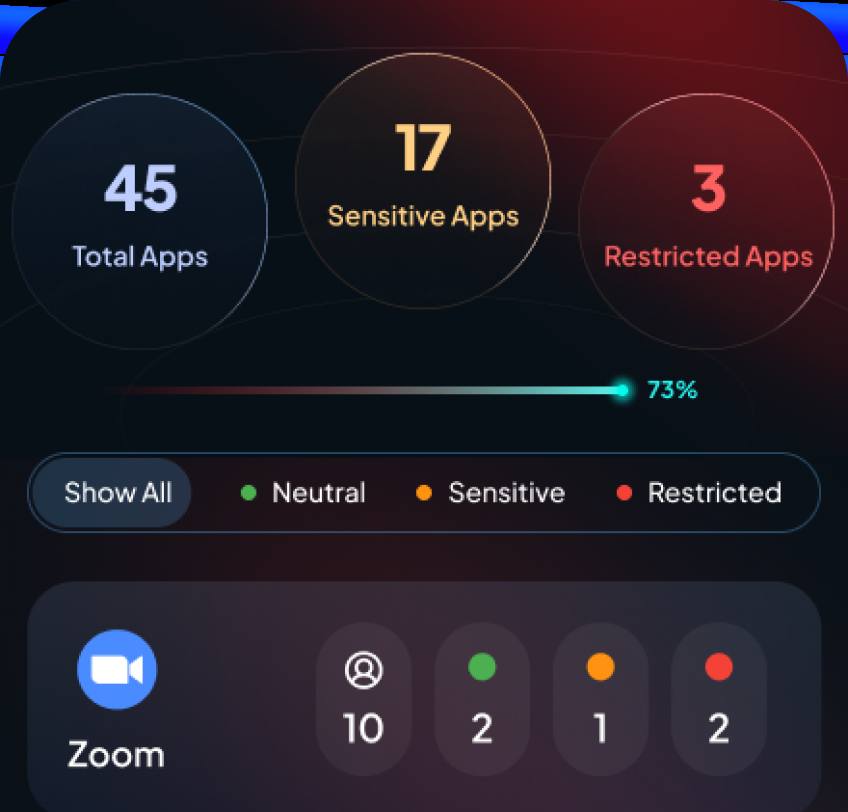
Shadow IT Assessment
Discover unauthorized applications and OAuth access in your Google Workspace environment.
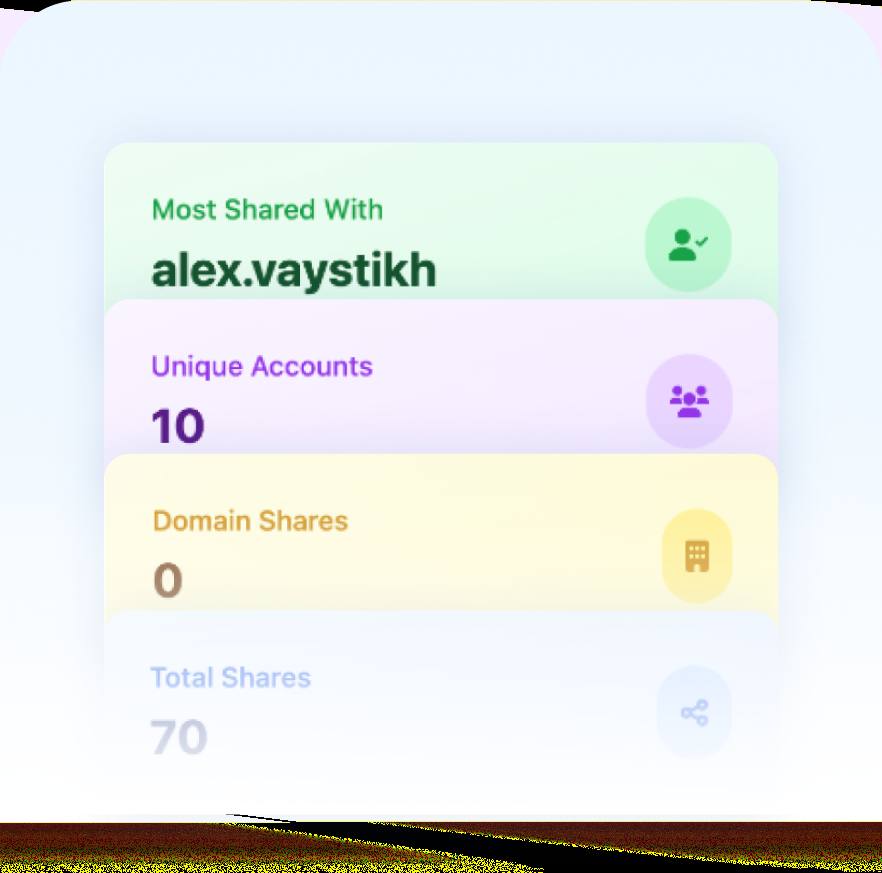
Drive Reports
Generate comprehensive reports on Google Drive usage, sharing, and security settings.
